Welcome back, my tenderfoot hackers!
I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.
With this guide, I'm starting a sequential and cumulative series for learning and using Metasploit. This first part will cover the very basics of Metasploit for those of you who are new to Null Byte, and as a refresher for those of you who are not. With that in mind, this will be quick and dirty first lesson on using one of the most powerful hacking platforms on planet Earth.
Metasploit Background & Installation
Metasploit was developed by HD Moore as an open source project in 2003. Originally written in Perl, Metasploit was completely rewritten in Ruby in 2007. In 2009, it was purchased by Rapid7, an IT security company that also produces the vulnerability scanner Nexpose.
Metasploit is now in version 4.9.3, which is included in our Kali Linux. It's also built into BackTrack. For those of you using some other version of Linux or Unix (including Mac OS), you can download Metasploit from Rapid7's website.
For those of you using Windows, you can also grab it from Rapid7, but I do not recommend running Metasploit in Windows. Although you can download and install it, some of the capabilities of this hacking framework do not translate over to the Windows operating system, and many of my hacks here on Null Byte will not work on the Windows platform.
Metasploit now has multiple products, including Metasploit Pro (the full commercial version) and the Community edition that is built into Kali and remains free. We will focus all of our efforts on the Community edition, as I am well aware that most of you will not be buying the $30,000 Pro edition.
Ways to Use Metasploit
Metasploit can be accessed or used in multiple ways. The most common method, and the one I use, is the interactive Metasploit console. This is the one that is activated by typing msfconsole at the command line in Kali. There are several other methods as well.
Msfcli
First, you can use Metasploit from the command line, or in msfcli mode. Although it appears that when we are in the console that we are using the command line, we are actually using an interactive console with special keywords and commands. From the msfcli, we ARE actually using a Linux command line.
We can get the help screen for msfcli by typing:
kali > msfcli -h
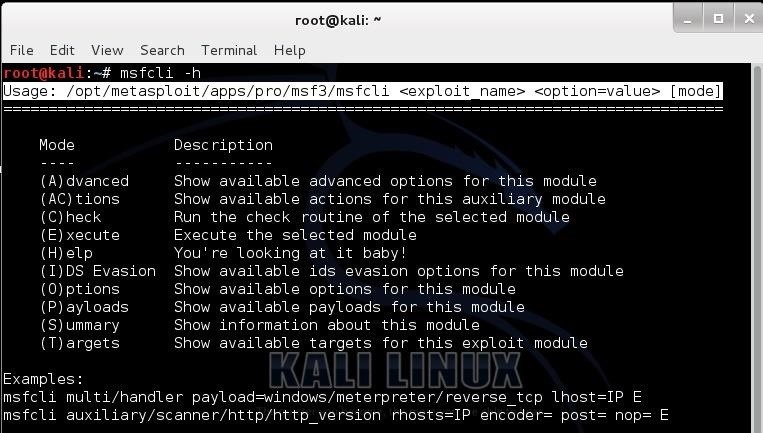
Now to execute an exploit from the msfcli, the syntax is simply:
kali > msfcli <the exploit> payload = <the payload> rhost = <IP> lhost = <IP> E
Where E is short for execute.
In my tutorial on creating payloads to evade AV software, we are using the msfencode and msfpayload command in the command line (msfcli) mode.
The drawback to using the msfcli is that it is not as well-supported as the msfconsole, and you are limited to a single shell, making some of the more complex exploits impossible.
Armitage
If you want to use Metasploit with a GUI (graphical user interface), at least a couple of options are available. First, Raphael Mudge has developed the Armitage (presumably a reference to a primary character in the seminal cyberhacking science fiction work, Neuromancer—a must read for any hacker with a taste for science fiction).
To start Armitage in Kali, simply type:
kali > armitage
If Armitage fails to connect, try these alternative commands:
kali > service start postgresql
kali > service start metasploit
kali > service stop metasploit
Armitage is a GUI overlay on Metasploit that operates in a client/server architecture. You start Metasploit as a server and Armitage becomes the client, thereby giving you full access to Metasploit's features through a full featured—thought not completely intuitive—GUI. If you really need a GUI to feel comfortable, I don't want to discourage you from using Armitage, but mastering the command line is a necessity for any self-respecting hacker.
Modules
Metasploit has six different types of modules. These are:
- payloads
- exploits
- post
- nops
- auxiliary
- encoders
Payloads are the code that we will leave behind on the hacked system. Some people call these listeners, rootkits, etc. In Metasploit, they are referred to as payloads. These payloads include command shells, Meterpreter, etc. The payloads can be staged, inline, NoNX (bypasses the No execute feature in some modern CPUs), PassiveX (bypasses restricted outbound firewall rules), and IPv6, among others.
Exploits are the shellcode that takes advantage of a vulnerability or flaw in the system. These are operating system specific and many times, service pack (SP) specific, service specific, port specific, and even application specific. They are classified by operating system, so a Windows exploit will not work in a Linux operating system and vice versa.
Post are modules that we can use post exploitation of the system.
Nops are short for No OPerationS. In x86 CPUs, it is usually indicated by the hex 0x90. It simply means "do nothing". This can be crucial in creating a buffer overflow. We can view the nops modules by using the show command.
msf > show nops
Auxiliary includes numerous modules (695) that don't fit into any of the other categories. These include such things are fuzzers, scanners, denial of service attacks, and more. Check out my article on auxiliary modules for more in-depth information for this module.
Encoders are modules that enable us to encode our payloads in various ways to get past AV an other security devices. We can see the encoders by typing:
msf > show encoders
As you can see, there are numerous encoders built into Metasploit. Once of my favorites is shikata_ga_nai, which allows us to to XOR the payload to help in making it undetectable by AV software and security devices.
Searching
Ever since Metasploit 4 was released, Metasploit has added search capabilities. Previously, you had to use the msfcli and grep to find the modules you were looking, but now Rapid7 has added the search keyword and features. The addition of the search capability was timely as Metasploit has grown dramatically, and simple eyeball searches and grep searches were inadequate to search over 1,400 exploits, for instance.
The search keyword enables us to do simple keyword searches, but it also allows us to be a bit more refined in our search as well. For instance, we can define what type of module we are searching for by using the type keyword.
msf > search type:exploit

When we do so, Metasploit comes back with all 1,295 exploits. Not real useful.
If we know we want to attack a Sun Microsystems machine running Solaris (Sun's UNIX), we may want may to refine our search to only solaris exploits, we can then use platform keyword.
msf > search type:exploit platform:solaris
Now we have narrowed our search down to only those exploits that will work against a Solaris operating system.
To further refine our search, let's assume we want to attack the Solaris RPC (sunrpc) and we want to see only those exploits attacking that particular service. We can add the keyword "sunrpc" to our serach like below:
msf > search type:exploit platform:solaris sunrpc
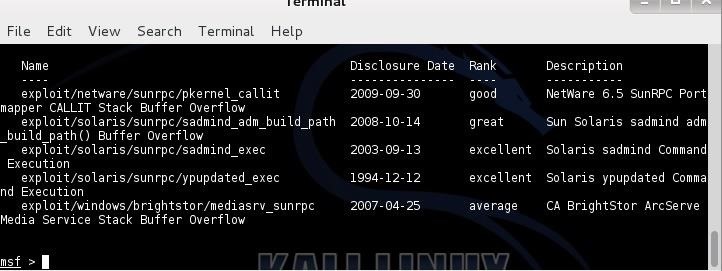
As you can see, this narrows are results down to just five exploit modules!
Metasploit has many capabilities that are still untapped by us, so I will continue this Metasploit series to explore the simplest to the most complex. In the meantime, try some of my Metasploit hacks outlined in many Null Byte posts and keep coming back to this series on Metasploit to learn to hack like a pro!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















26 Comments
very well explain
I would like to see a tutorial about FB hacking, remotely.
Not in local Wifi, and not a simple phising page via kali LINUX.
thanks bro !
Nice!, I find this very helpful for my virtual running Kali on my android, MSF always freaks out when I try to open the msf command line, the kali > msfcli -h function will be very helpful!, thanks. I'm looking forward to the rest of these series!
Bart
Sir OTW,
For some reasons, i had to uninstall metasploit and reinstall it again.
i downloaded it and i have done the instructions to install it.
the metasploit-framework folder is located in /root (myusername)
it works when i double-click on the ruby script, but it gives the following error when i type "msfconsole" in Terminal:
root@kali:~# msfconsole
/usr/lib/ruby/1.9.1/rubygems/customrequire.rb:36:in `require': cannot load such file -- /usr/local/bin/config/boot (LoadError)
from /usr/lib/ruby/1.9.1/rubygems/customrequire.rb:36:in `require'
from /usr/local/bin/msfconsole:45:in `<main>'
root@kali:~#
i NEED metasploit to launch when i type "msfconsole". (im not lazy, but i need it for some reasons).
What should i do?? (im sorry to bother you with this long article).
probably the gems need updating.
run...
apt-get upgrade && bundler update && bundle update
Matt:
Metasploit is built into Kali. No need to install.
OTW
I already know that sir, but i deleted the metasploit files completely and
is=nstalled it again.
You might find it easier to simply re-install Kali.
Btw, why did you uninstall Metasploit in the first place?
No matter, i fixed metasploit files manually.
cannot start because of error.
https://bugs.kali.org/print_all_bug_page_word.php?search=&sort=&dir=DESC&type_page=html&export=-1&show_flag=0
Are you running it on Kali?
Yes OTW. Just find your posts, thx so much for the tutorials.
root@kali:~# uname -a
Linux kali 3.18.0-kali3-amd64 #1 SMP Debian 3.18.6-1~kali2 (2015-03-02) x8664 GNU/Linux
Have you tried running msfupdate?
yes, did the update.
Temp fix:
root@kali:~# msfconsole.framework
* Starting the Metasploit Framework console...-
######## #
################# #
###################### #
######################### #
############################
##############################
###############################
###############################
##############################
# ######## #
## ### #### ##
### ###
#### ###
#### ########## ####
####################### ####
#################### ####
################## ####
############ ##
######## ###
######### #####
############ ######
######## #########
##### ########
### #########
###### ############
#######################
# # ### # # ##
########################
## ## ## ##
http://metasploit.pro
Save 45% of your time on large engagements with Metasploit Pro
Learn more on http://rapid7.com/metasploit
= metasploit v4.11.3-2015061001 [core:4.11.3.pre.2015061001 api:1.0.0]
msf >
very Informative Answered literally all my questions in one read through
When I tried to use the 'msfcli' command I was approached with this error.
root@Kali:~# msfcli -h
bash: msfcli: command not found
msfcli has been discontinued.
Yeah just found that out and was about to delete my comment. Thanks anyway.
Just wondering, what are your opinions on the removal of msfcli?
I honestly am unsure how this comes into effect.
It doesn't impact me at all. I use msfconsole
So I'm not missing much?
Thanks for the help.
How would i be able to create a listener that a will use to a pc that we are in different networks...
My ip address keeps changing every time i restart my modem
Hey i am a newbie both to metasploit and null byte. I just created a file with metasploit (trying in case i dont know his ip) to send to my friend (just for testing , he knows it), but then accidently closed terminal .So after he has opened the file , how can i know .And how to open that session ?(if he has open and if he has not open , both)
HELP any msf command besides msfconsole does not work! (i.e. msfpayload, msfencode, or msfcli) I can see the details of the command via the man pages, however, if I were to type in a command like "msfencode -h" I get a command not found error. Someone please help!
Thanks
When I type the command msfcli inthe kali console it just says " bash: msfcli: command not found ". What should I do?
Well now for any newcomer the msfcli has been removed from the metasploit framework but one way to obtain a real linux command for the msf through msfconsole is to run
msfconsole -x
this command will provide us a real linux command line not just an interactive console that has it's own keywords and commands which by no means related to the CLI
Share Your Thoughts