Welcome back, my fledgling hackers!
In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.
In this article, we'll take a look at the world's best Wi-Fi hacking software, aircrack-ng, which we previously used to bump your annoying neighbor off their own Wi-Fi network. We'll be using aircrack-ng in nearly all of the subsequent hacks, so I think it's wise to start with some basics on what is included and how to use everything.
For this to work, we'll need to use a compatible wireless network adapter. Check out our 2017 list of Kali Linux and Backtrack compatible wireless network adapters in the link above, or you can grab our most popular adapter for beginners here.

First of all, aircrack-ng is not a single tool, but rather a suite of tools for manipulating and cracking Wi-Fi networks. Within this suite, there is a tool called aircrack for cracking passwords, but to get to the cracking we need to do several steps using other tools. In addition, aircrack-ng is capable of doing DOS attacks as well rogue access points, caffe latte, evil twin, and many others.
So, let's get started with the aircrack-ng suite!
Quick Note
The ng stands for new generation, as aircrack-ng replaces an older suite called aircrack that is no longer supported.
Step 1: Iwconfig
Before we get started with aircrcak-ng, we need to make certain that BackTrack recognizes your wireless adapter. We can do this within any Linux system by typing:
- bt > iwconfig
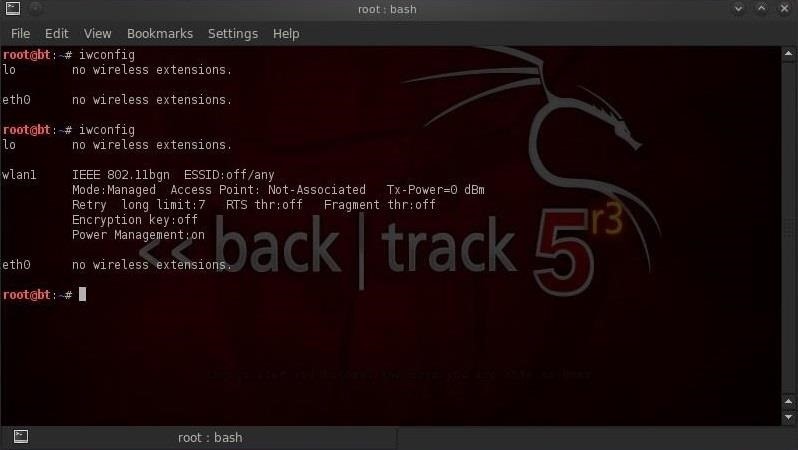
We can see here that BackTrack recognizes my USB wireless card, and it tells me that it's capable of 802.11bgn, that the ESSID is off, that the mode is managed, etc.
Okay, now we're ready to start using aircrack-ng.
Step 2: Airmon-Ng
The first tool we will look at and need in nearly ever WiFi hack is airmon-ng, which converts our wireless card into a promiscuous mode wireless card. Yes, that means that our wireless card will hookup with anyone!
Well, that's almost correct. When our network card is in promiscuous mode, it means that it can see and receive all network traffic. Generally, network cards will only receive packets intended for them (as determined by the MAC address of the NIC), but with airmon-ng, it will receive all wireless traffic intended for us or not.
We can start this tool by typing airmon-ng, the action (start/stop), and then the interface (mon0):
- bt > airmon-ng start wlan1
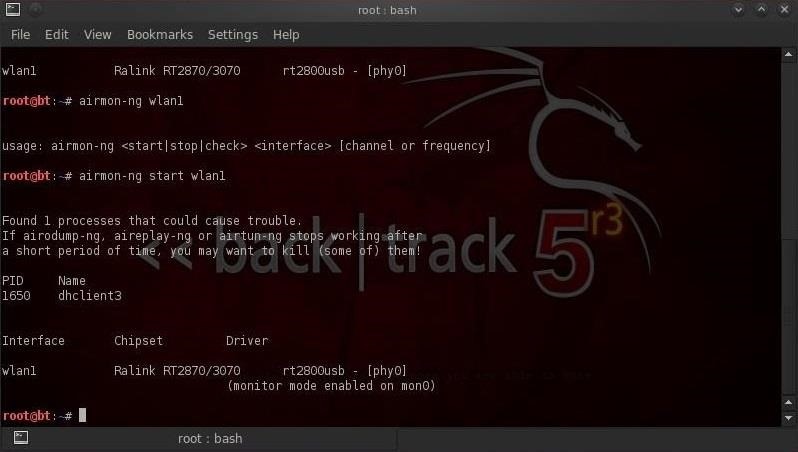
Airmon-ng responds with some key information on our wireless adapter including the chipset and driver. Most importantly, note that it has changed the designation for our wireless adapter from wlan1 to mon0.
Step 3: Airodump-Ng
The next tool in the aircrack-ng suite that we will need is airodump-ng, which enables us to capture packets of our specification. It's particularly useful in password cracking.
We activate this tool by typing the airodump-ng command and the renamed monitor interface (mon0):
- bt >airodump-ng mon0
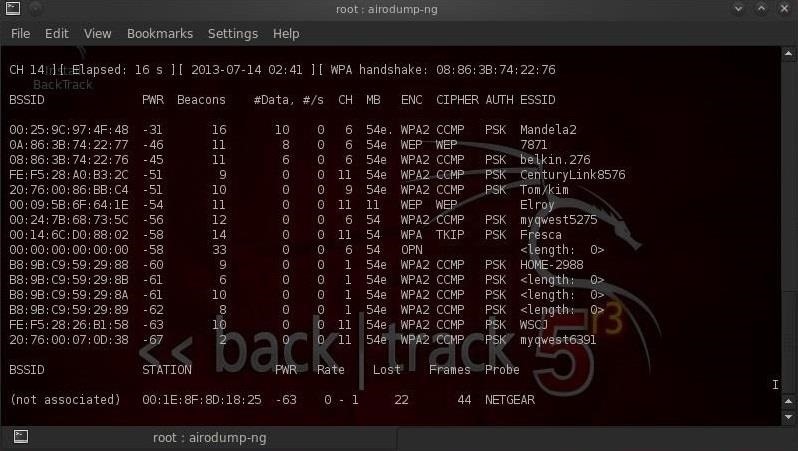
As we can see in the screenshot above, airodump-ng displays all of the APs (access points) within range with their BSSID (MAC address), their power, the number of beacon frames, the number of data packets, the channel, the speed, the encryption method, the type of cipher used, the authentication method used, and finally, the ESSID.
For our purposes of hacking WiFi, the most important fields will be the BSSID and the channel.
Step 4: Aircrack-Ng
Aircrack-ng is the primary application with the aircrack-ng suite, which is used for password cracking. It's capable of using statistical techniques to crack WEP and dictionary cracks for WPA and WPA2 after capturing the WPA handshake.
Step 5: Aireplay-Ng
Aireplay-ng is another powerful tool in our aircrack-ng arsenal, and it can be used to generate or accelerate traffic on the AP. This can be especially useful in attacks like a deauth attack that bumps everyone off the access point, WEP and WPA2 password attacks, as well as ARP injection and replay attacks.
Aireplay-ng can obtain packets from two sources:
- A live stream of packets, or
- A pre-captured pcap file
The pcap file is the standard file type associated with packet capture tools like libpcap and winpcap. If you've ever used Wireshark, you've most likely worked with pcap files.
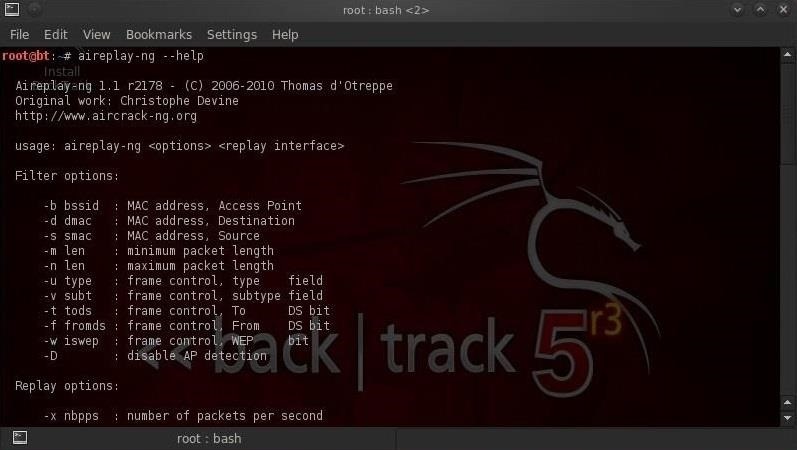
We can see in the screenshot above of the first half of the aireplay-ng help screen, that aireplay can filter by the BSSID of the access point, the MAC address of either source or destination, the minimum and maximum packet length, etc. If we scroll down the help screen, we can see some of the attack options using aireplay-ng:
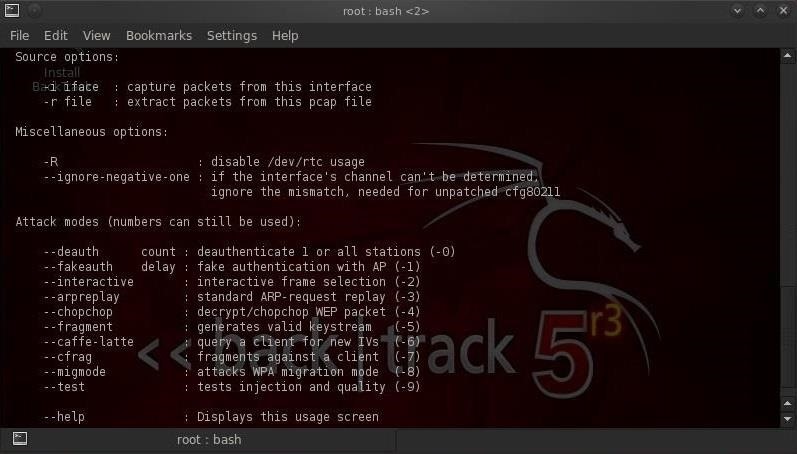
These include deauth, fake deauth, interactive, arpreplay (necessary for fast WEP cracking), chopchop (a form of statistical technique for WEP packet decrypting without cracking the password), fragment, caffe latte (attacking the client side), and others.
These four tools in the aircrack-ng suite are our Wi-Fi hacking work horses. We'll use each of these in nearly every Wi-Fi hack. Some of our more hack-specific tools include airdecap-ng, airtun-ng, airolib-ng and airbase-ng. Let's take a brief look at each of these.
Step 6: Airdecap-Ng
Airdecap-ng enables us to decrypt wireless traffic once we have cracked the key. In other words, once we have the key on the wireless access point, not only can we use the bandwidth on the access point, but with airdecap-ng we can decrypt everyone's traffic on the AP and watch everything they're doing (the key is used for both access and for encryption).
Step 7: Airtun-Ng
Airtun-ng is a virtual tunnel interface creator. We can use airtun-ng to set up an IDS on the wireless traffic to detect malicious or other traffic on the wireless access point. So, if we're looking to get an alert of a particular type of traffic (see my tutorial on creating a PRISM-like spy tool), we can use airtun-ng to set up a virtual tunnel that connects to an IDS like Snort to send us alerts.
Step 8: Airolib-Ng
Airolib-ng stores or manages ESSID's (the name of the access point) and password lists that will help speed up WPA/WPA2 password cracking.
Step 9: Airbase-Ng
Airbase-ng enables us to turn our laptop and wireless card into an AP. This can be especially useful when doing a rogue access point or evil twin attacks. Basically, airbase-ng allows us to attack the clients, rather than the AP, and encourages the clients to associate with us rather than the real AP.
That's It for Now
These are the primary tools in the aircrack-ng suite that we'll be using as we explore Wi-F hacking. There are other tools, but these are the ones we'll be focusing on. If you're looking for a cheap, handy platform to get started working with aircrack, check out our Kali Linux Raspberry Pi build using the $35 Raspberry Pi.

In our next guide, we'll start our exploration of wireless hacking techniques with creating a evil twin access point, so make sure to keep coming back. If you have any questions, please comment below or start a discussion in the Null Byte forum and we'll try to help you out.
Just updated your iPhone to iOS 18? You'll find a ton of hot new features for some of your most-used Apple apps. Dive in and see for yourself:





















107 Comments
Ty so much,
I' following u and hope this guide will make me more haky :-)
Now i'm a lamer and i'd like to know something new and maybe better then only wifi hacking in the future.
Before my wireless card wasn't recognized by backtrack so i bought the adapter u told about and it works fine.
Well, i say u thanks and hope , like before, that u'll teach us more things :-)
Ps.
Sorry for my bad english but i hadn't time to use google translator :-)
when i type airmon-ng nothing show to me :/ whats wrong can u tell me pls ? or gimme your email and i send you message ..
You may not have wlan interface try downloading drivers compact wireless from google. better to search for version dated 26 june 2010 :)
hope it will work
Ma:
Did you check to see whether your wireless card is up and running?
Also, the command requires the start command with the name of the interface.
OTW
When I used the command ( airmon-ng start wlan1) the designation for my wireless adapter does not change from wlan1 to mon0 so im unable to proceed from there i do not get that part of thae reading at all
Andwele:
When you type iwconfig, what is your wireless adapter?
OTW
i am on wlan0 instead of wlan1 but when i use the command (airodump-ng start mon0) i keep getting "airodump-ng --help" for help.
i cannot proceed further than here because of this ...help plz !
Andwele:
First, you must put wlan0 in monitor mode.
airmon-ng start wlan0
Then, airodump-ng mon0
OTW
yeah thats exactly what i did and i keep getting --> "airodump-ng --help" for help
Andwele:
Are you using an aircrack-ng compatible wireless adapter?
OTW
Will this work on windows 8? And from where can I get the software.. I dont want any virus to sweep into my system...
I know I am talking very naive but this is the first time I am doing anything like this..
Thanks in advance!
Annanna:
This software is all on BackTrack. Its a Linux distribution with hacking and security tools. You can get it directly from here.
I have several tutorials on Null Byte on how to install and use it.
Welcome to Null Byte!
OTW
Thank you so much,
You will be seeing me more often now.
Command Airmon-Ng not find me and iwconfig command not act
There Efe origin afflicting thou shalt not work for me why?
DKTR:
Welcome to Null Byte!
What error messages are you getting?
OTW
I do not get an error message right to you it opens a table with full wifi
This opens a table but there are no where WIFI.
DKTR:
iwconfig should list your wifi interfaces. Then you need to put your wifi adapter into monitor mode with airmon-ng. After putting it into monitor mode, you then use airodump-ng to see all the AP's.
OTW
How do I do this??
Are you using BackTrack?
Yes I am using BackTrack
What happens when you type iwconfig?
It always
iwconfig
lo no wireless extensions.
eth1 no wireless extensions
No matter how many times I do it always
Are you running in a VM?
yes
When running BackTrack in a VM, you must have an external wireless adapter such as a USB wireless adapter. Otherwise, you will need to run BackTrack directly on the hardware to use your built in wifi.
OTW
Thanks,,,
Can I Dual Boot Kali Linux And Windows 8.1 To hack wifi password, I am using a laptop core i 3 ???
You need to run the tracks directly on your use hardware built in WiFi
How do I do this?
DKTR:
I suggest buying an ALFA card for hacking wifi. You will need one to do all my hacks.
You can also install BT as a dual boot system.
OTW
I have a wireless card D-Link How do I get ALFA card??
You can also install a dual boot system BT
How do I install BT?
DKTR:
The Alfa card is available from nearly all the electronic retailers.
I have a tutorial here on how to install Backtrack.
OTW
But I did not understand how I run Backtrack directly on hardware for your use built in WiFi
VM software
DKTR:
Did you read the tutorial?
Download BackTrack, burn it to a disk and then install on your hard drive. BackTrack will prompt you to make a dual boot system.
OTW
Disc DVD + R that good?
It can burn the Maya Attribute infest?
And I apologize with I load too much of you just did not get the manual ....
Airmon-NG is showing zero results. I'm assuming it's possible that one of the running processes air mon warned me about could be interfering. Would spoofing my MAC address have any effect on the dump? I'm also not connected to the Internet, but I really didn't think that would matter. I'm playing with it, but was just curious what your thoughts would be. Thanks otw
Are running in a vm?
Yes, took me a little while to get the adapter up and running, so I may have configured something wrong.
AWUS036NH
Bridged the adapter in virtual box
USB is active
And promiscuous mode is set to allow vms
What happend at iwconfig?
It looks exactly like the screenshot from the lesson. Only difference is my tx-power=20 dB.
Good. How about airmon-ng?
Showing mon0 and wlan0 with the same chipset and driver. Ralink RT2870/3070 rt2800usb - phy0
Also worth noting I'm running Kali on a 64 bit Debian vm
Woooow, detached USB, plugged it back in... Problem solved. I should know better than that. Thanks for the quick response and help OTW.
Dear master otw
Can you please add me on facebook, so you can give me some quick response, my name is sebastian nielsen with the squirrel picture to the left.
Ps. Im your biggest fan!!!
Sebastian:
Welcome to Null Byte! I'm glad you are enjoying my tutorials.
As you can imagine, I need to maintain my anonymity so I can only communicate with you through Null Byte. Sorry.
OTW
Dear Master otw
what I thought was that you could make a fake facebook account. where you could get a lot of friends who have questions about your "block" that you could give quick response to. and of course you need to write fake things down about yourself. So you can stay anonymous.
Why becouse i dont like to try the tutorial out and wait for you answer my quistions after some hours.
I hope you understand and might have changed my mind.
Sorry for my bad english xD
Sebastian;
I don't see how a Facebook page would get you a faster response. The limiting factor is me.
OTW
I would of said time, as you don't seem very limited lol
Okay master otw
Master OTW
For this tutorial would it be wise for me to disconnect myself from the internet before attempting it?
Hey Gumskull, not sure what OTW will say, but I've been successful using a cable LAN connection for my internet connection and then using the aircracking suite on wireless that way you can still read the tutorials, look up things etc.
Hope this helps
I agree with Existing Me.
My problem here is that my router is downstairs and my computer is upstairs and I don't have an ethernet cable long enough to reach upstairs without demolishing the house. Would it still work if I were to use a wireless connection?
You don't HAVE to be connected to the lan, you could always just download/ print out the tutorial
You make an excellent point there. My mind doesn't work the easy way around. Thank you.
So...we have all so painfully learned.
hey sebastian i think ur looking for a private tutor.........After reading all these comments ,i'd just like to say THANK U to OTW for your time and patients....hey guys u ever played 100 games of chess at once.......exactly
hi can tell me whats happening here thanks
root@kali:~# aireplay-ng --deauth 100 -a 58:#:35:#:50:C8 mon0
19:00:50 Waiting for beacon frame (BSSID: #:98:#:23:#:C8) on channel -1
19:00:50
Couldn't determine current channel for mon0,
you should either force the operation with --ignore-negative-one or apply a kernel patch
Please specify an ESSID (-e).
try dropping the - out of your channel switch
Also i Don't know if you HAVE to, but i always specify the ESSID
Try aireplay-ng --help, but mostly i think it's because your using "channel -1" instead of "channel 1"
Nice Article, but i am just curious to know that is it really necessary to switch wlan into mon mode ?
Because at one time , i used airodump-ng with mon mode enabled and the other time with mon mode disabled ( I used airodump-ng -c 1 -w "data file name" --bssid 00:16:*:B4:*:* wlan0 )
I couldn't observe any certain difference in the console terminals. Both the processes seemed same to me.
Bharat:
If you don't put the wlan into mon mode, you will be limited in what packets you can pick up and send.
OTW
Wow... Perfect and simply guide!
Hi OTW,
I have a problem with Aircrack ....my channel is always fixated on -1 even when i try to change it to a specific channel
Evil:
Check out this post on how to fix this issue.
https://forums.kali.org/showthread.php?20582-HOW-TO-FIX-Airodump-ng-fixed-channel-1-Kali-kernel-3-12-also-on-rt2870-3070usb
OTW
Evil,
At the end of your code use "--ignore-negative-one"
That is what worked for me.
Do i need all of these tools or i should jst have one of them
You need all these tools and they are all built into Kali.
can i just use wireless card built in? atheros ar9285. I use lenovo G480. I stuck at airodump. please help me
Usually not. It must
It must be aircrack compatible.
So my wireless adapter (ALFA AWUS036NH) arrived and on the command:iwconfig,it detects my wireless adapter.Then I typed airmon-ng start wlan0 and was assigned to monitor mode mon0,but when I typed in airodump-ng mon0,I do not receive any clients on the network.Any ideas OTW?
Peace.
Here is a blast from the past because I figured this...
"1 week ago
Oh, OK.. Ø
Plug & Play on that card not 100%
For your next set of questions maybe: https://www.google.com/search?q=AWUS036NH+linux+issues "
Thanks CH.
Frank:
Attach some screenshots so we can see what's going on and diagnose the issue.
OTW
Hello Sir,
I'm using Kali 2.0 in a Virtual machine. I've followed your tutorials. It's really great. But now I'm facing some problems.
I've attached a screenshot when I'm using this command below:
#airodump-ng wlan0mon
So, what's the problem here??? why I'm not getting any "BSSID", "CH" here???
Thanks
ME
Screenshot from iwconfig:
Screenshot from airmon-ng start wlan0:
Screenshot from airodump-ng mon0
Here's the problem,no wireless clients returned.
Thanks for your Help :)
Peace.
About 17 steps and it's as good as fixed.. (`)
CH:
And what are those 17 steps you're talking about?
even I have the same problem no clients in the list even after I killed the processes
Hi, I have one question, I have done access point mapping using airodump-ng, so i have collected so many aps, with different encryption some of are open aps. Is there any tools or web services are available for visualization ?
I found this website http://bit.ly/1Nbfgm6 but is there any other sources are available ?
Thanks!
Is there any software for windows 7? thx :)
what's the name of the very first terminal you open ?
Hello Sir,
One question: when i execute airdump, what does the part under the Aap list represent? The one with STATION column? Thank you.
That represents the MAC address of the client.
Which client? I see about 3-4 macs there and I'm not connected to any network. Clients of which network?
The BSSID is the AP and the station is the client.
Awfully sorry for bothering you this much, but what does the Probe column represent? Sometimes there are up to 10 probes on 1 client
I have a problem OTW. First of all I'm using kali Linux 2.0 on virtual box and the second I don't have a wireless card but I downloaded compat wirless 2010-09-01-p so I when I use a iwconfig I can see that there is a wireless card named wlan0.
now the problem > I followed your steps correctly I even killed the processes after turning the W.A to monitor mode but after I use airodump-ng wlan0mon I don't get anything except a terminal showing only bssid and other stuff but no clients can you plz give me a solution I desperately need a answer ........
hi pls help me im always getting this prb : got no data target network !! and then aircrack-ng quite the operation
so pls any solution !! and thank u
https://scontent.xx.fbcdn.net/hphotos-xpf1/v/l/t34.0-0/p206x206/11949786_681537258649516_29077981_n.jpg?oh=6d7a0719addbbf3b318fa16fd6c3bac4&oe=55E8B839
Hello!
After entering airmong-ng start wlan0 my wireless adapter won't change to monitor mode (mon0)..also i get a lot more output, for example encryption key, ESSID, access point etc..
So when i try airodump-ng mon0 the output is:
Interface mon0:
ioctl(SIOCGIFINDEX) failed: No such device
I tried some other commands, but nothing worked.
I'm running the Realtek Semiconductor Corp. RTL8191SU 802.11n chipset.
After some research I guess this chipset isn't compatible to aricrack-ng??
Please help me out.. i just want to be sure before buying a new adapter.
Thanks in advance.
If you are using Kali 2 , the monitor interface is named wlan0mon. If not, before you execute airmon start wlan, first execute airmon-ng check kill
and then airmon-ng start wlan0, to eliminate any interfering processes that might cause this. -ne py
airodump-ng mon0 not showing anything plz help.. searching for solution from 2 days still got nothing to fix this ...
Did you happen to read the week old comment right above yours?
Hello, I've been trying to get this to work, but it's not. I'm running Kali Linux 2.0 on a live persistent USB. Below is a screenshot of when I type iwconfig and airmon-ng start wlan0.
I have tried airmon-ng check kill btw.
Note that in the error message it references wlan0mon. The new version of aircarck-ng using that designation for the monitor interface. Try running airmon-ng start wlan0mon.
I've now tried that, and it doesn't show any errors with the airmon-ng start wlan0mon. But when I try airodump-ng mon0, or anything other than airodump-ng wlan0, it says that device is not found.
However when I try airodump-ng wlan0 is show the following:
ioctl(SIOCSIWMODE) failed: Operation not supported
ARP linktype is set to 1 (Ethernet) - expected ARPHRDIEEE80211,
ARPHRDIEEE80211FULL or ARPHRDIEEE80211PRISM instead. Make
sure RFMON is enabled: run 'airmon-ng start wlan0 <#>'
Sysfs injection support was not found either.
"But when I try airodump-ng mon0 or anything other than airodump-ng wlan0, it says that device is not found."
"anything other than airodump-ng wlan0" includes wlan0mon. The ones I tried are:
It is getting complicated when it shouldn't. Have you ever packet injected or put that card into monitor mode?
This would help some if you could take the interfaces down and up and set modes manually. I am going to sleep if they have not helped you I will look at this again in few hours.
I have never packet injected or put this card into monitor mode. This is my first time ever trying aircrack-ng.
As for taking the interfaces down and up and setting them manually, I'm not sure what you mean. I've never heard about that before. But just take your time, or tell me if this is getting too annoying to help with.
Could my chipset have something to do with it? I think it's BCM43142. This is what I get when lspci -nn | grep Network:
07:00.0 Network controller 0280: Broadcom Corporation BCM43142 802.11b/g/n 14e4:4365 (rev 01)
Well broadcom is not the best chipset to start with. I am really sick ATM so Im having a hard time visualizing this issue. Pretty sure if you can not start a monitor interface then the card is not gonna work. I maybe wrong tho...
Okay. Thanks for you help and get well soon :)
If you are running persistent then reboot the machine type : init 6 <-- not reboot
When the machine comes back up try again w/o killing all the processes. Then let us know if that helped.
This card is compatible with aircrack-ng and packet injection yes?
Sadly that did not help. I don't know if it's compatible with aircrack-ng and packet injection. Where do I check that? Sorry, I have only been working with Linux for a few weeks, so I'm still a newbie.
I have a problem OTW. First of all I'm using kali Linux 2.0 on virtual box and the second I don't have a wireless card but I downloaded compat wirless 2010-09-01-p so I when I use a iwconfig I can see that there is a wireless card named wlan0.
now the problem > I followed your steps correctly I even killed the processes after turning the W.A to monitor mode but after I use airodump-ng wlan0mon I don't get anything except a terminal showing only bssid and other stuff but no clients can you plz give me a solution I desperately need a answer ........
A dictionary attack? ROFL. Is it really worth it to hack into grammies router with the password "cookies"? HAHAHAHA!!!
OTW,
I'm using kali 2017.2 live persistence and I have a wireless adapter TPLink T2U aside from my laptop internal wireless card. I tried to use the tplink wireless adapter (interface ra0) and it can capture wpa handshakes on my network however, it can not inject packets by using aireplay-ng and can not deauth my target AP's. Using wlan0 on monitor mode, everything is normal. The reason why I purchased this TPLink is to have a longer range in capturing AP's... Here is my screenshot...
Can you help me with this problem?
Thank you...
Hi
Am using linux mint on my HP laptop . When I run airmon-ng start wlani
It's say it found 4 processes that cause trouble
PID Name
848 NetworkManager
849 avahi-daemon
996 avahi-daemon
1096 wpa-supplicant ........
Pls help to fix this ??
Does it say that causes or may cause? Its different.
You can use it without kill any process, but if you encounter any try to kill them.
Share Your Thoughts