Everything Else


How to Program in C# : Introduction to the Basics (Part 1)
Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

How To: Keeping Your Hacking Identity Secret: How to Become a Ghost Hacker #3
I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.


IRC Guide: Universal NickName
Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

Networking Foundations: Basic IP Addressing (Part 2)
Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.
How To: VIM, Using the Normal Mode Part 2
Hello there Nullbyters, Last tutorial we discussed navigating and setting some options.
How To: VIM, Using the Normal Mode Part 1
Hello there Nullbytes, In my previous tutorial found here,

IRC Guide: Making a Bot
Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

How To: Set Up a Pentesting Lab Using XAMPP to Practice Hacking Common Web Applications
Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!
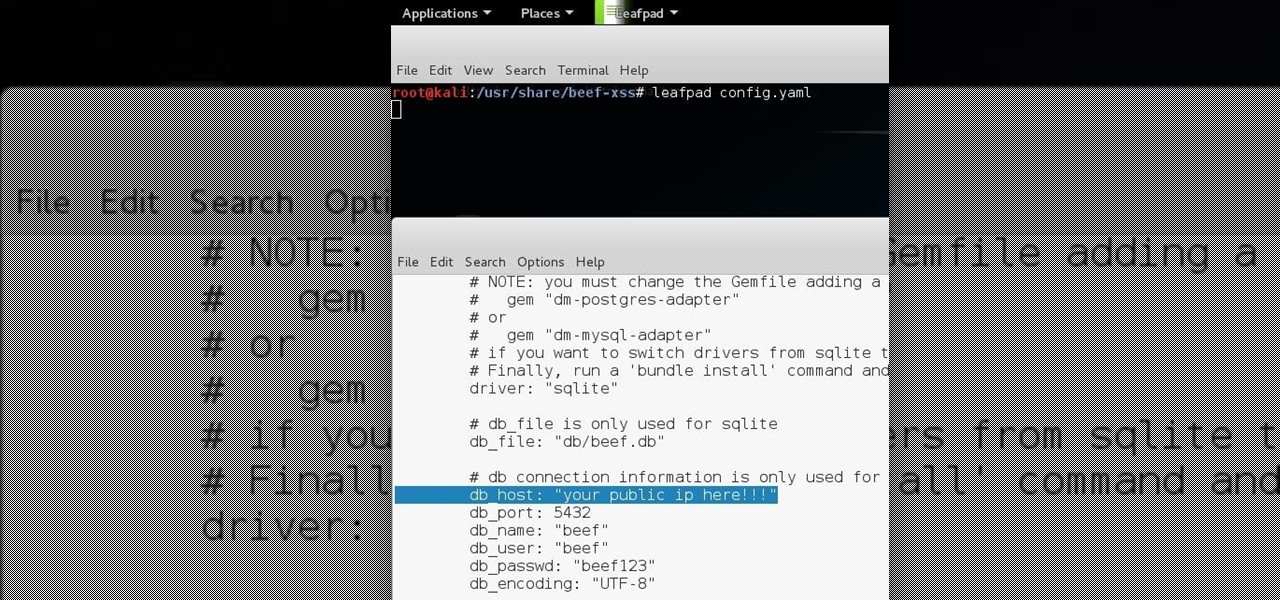
How To: BeEF - the Browser Exploitation Framework Project OVER WAN
Hello all Just thought id share how ive managed to get beef working over the internet.

How To: VIM, as Ugly as It Is Fast
Hello there Nullbyte users! This will be my first article here.

Tutorial: DNS Spoofing
Greetings my fellow hackers.

How To: The Five Phases of Hacking
Five Phases of Hacking:- The five phases of Hacking are as follow:

How To: Build a Really Small Hacking
removed!

Guide: Wi-Fi Cards and Chipsets
Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

How To: This LastPass Phishing Hack Can Steal All Your Passwords—Here's How to Prevent It
If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

How To: Add Proxies to Your ProxyChains Config File the Lazy Way ;)
Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

How to Meterpreter: Obtaining User Credentials with PowerShell
In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Hack Like a Pro: How to Hack Like the NSA (Using Quantum Insert)
Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

How To: Write a Java Based Backdoor(RAT)
Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

How To: Create & Obfuscate a Virus Inside of a Microsoft Word Document
When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

How to Java: E2 (DataTypes and TypeCasting)
Welcome back Java programmers! In this tutorial we'll being going over Variables/DataTypes and Type-casting

How To: Gathering Sensitive Information: How a Hacker Doesn't Get DoXed
before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

How To: Exploit Development-Everything You Need to Know
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Guide: Privacy Matters
Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

How To: Gathering Sensitive Information: Basics & Fundamentals of DoXing
I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

TypoGuy Explaining Anonymity: Staying Hidden from the NSA
We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

How To: Creating Unique and Safe Passwords, Part 1 Using Wordlists
Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

Rasberry Pi: Introduction
Most of you probably heard about Rasberry Pi and if you haven't; what is wrong with you? But nothing less a Rasberry Pi is a computer a very small computer. Despite these size limitations, the Rasberry Pi is to not be underestimated. Not only can it do anything like a normal laptop or desktop, but, in my opinion on of the coolest features is that it boots off a Micro SD card. It can do anything that you want, but it's built to be played with. A hacker heaven.

How To: Bypass Antivirus Using Powershell and Metasploit (Kali Tutorial)
So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

How To: Keeping Your Hacking Identity Secret - #2
My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

How To: Using BASH for Computer Forensics
Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

How To: Successfully Hack a Website in 2016!
Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

How To: Program Your Own Little RAT (Part 2) Getting the Client Working
OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

How To: Use BeEF and JavaScript for Reconnaissance
Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

How To: Program Your Own Little RAT (Part 1) Getting the Server Working
I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

How To: READ THIS Before Posting to Null Byte (Update 10-Jan-2016)
After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"

How To: Bind Dendroid Apk with Another Apk
I recently posted a Tutorial about setting up Dendroid: http://null-byte.wonderhowto.com/how-to/setup-dendroid-android-rat-0167299/. I have worked the last 5 days on getting the Dendroid Binder, given with the Dendroid Source, working. This solution only works on Windows systems!
How To: Web Development 05 - More Styling
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!







