Null Byte: Page 21







forum
Piping Crunch into Hydra 


























forum
VPN Specific Location? 








forum
Need Help as a Beginner 







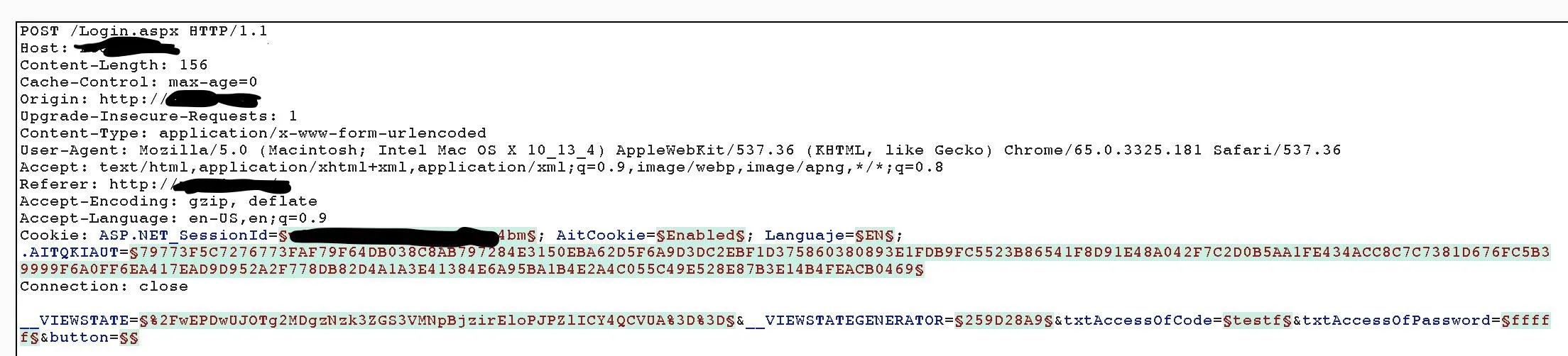









forum
THC Hydra Doesn't Work!! 










forum
Introduction: Cffe