The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.
You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

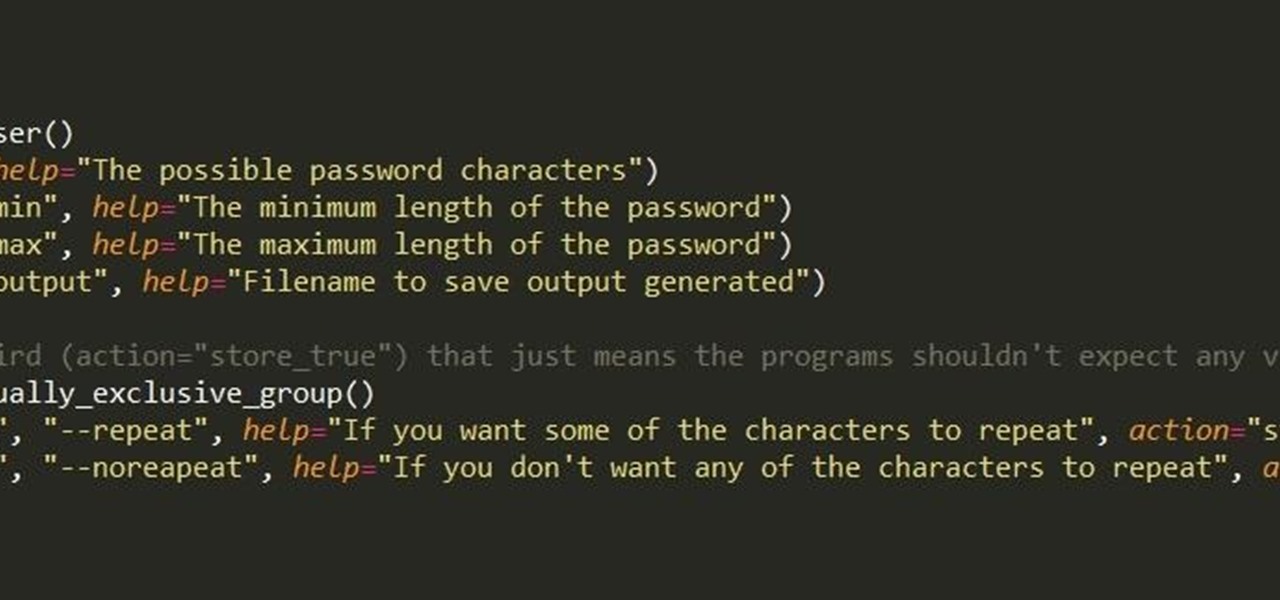
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...

Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected.

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

So, how does someone keep their hacking life completely secret? What This Is:

Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global financial markets crashed as well, but that's another story.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...