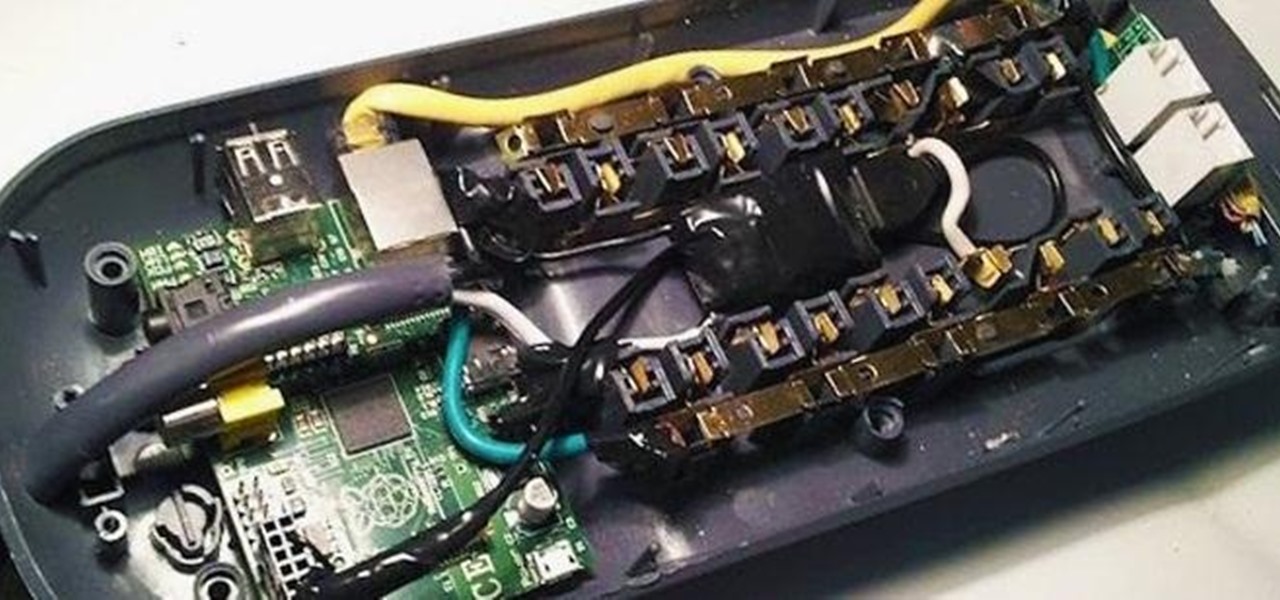
Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.
Welcome back Hackers\Newbies!

Yes, you read the title correctly. GameStop has problems, and if you're lax in morals, you can take advantage of them for free games and cash. I'm bringing you all yet another exclusive Null Byte that falls into the fascinating category of life hacking.

You might be sitting there thinking that I'm crazy, but the truth is you're only partially right. You can get free text messaging for life, all for a cheap, one-time fee. But, how can that be possible? An exploit in AT&T's prepaid GoPhones is the culprit behind this sweet, oh-so rare opportunity for exploitation. The exploit grants a lifetime of free texting, assuming that the company stays afloat from now until the end of time.

Null Byte is looking for moderators! In today's Null Byte, we're hacking Netflix. As most of you know, Netflix is a subscription service that streams movies and TV shows to your devices over the internet. A common stance amongst my Xbox Live friends is that Netflix isn't worth the cost. The instant movies predominantly consist of old titles, and new movies aren't added often enough.
i "found" a debit card that had the sticker on with activating instructions, how can i see if it is activated and if it is not, then how can i activate it and if it is how can i use it with out getting caught...

Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and the aircrack-ng software suite, the software has become unusable.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.

Bitcoin is a new currency built off "Satoshi Nakamoto's" (alias) 2008 Bitcoin white-paper. Bitcoin provides its users with a way to make peer-to-peer (P2P) transactions without having to use a bank as a mediator. There is no middle man, no corporation backing it, and no one has access to your money, except you. It's decentralized from government, run by the people, for the people.

Anonymity is very important to many internet users. By having your "e-identity" exposed online, you can be stuck with a number of unwanted issues, such as:

With the purchase of my latest computer, installing Linux turned into a nightmare from Hell. The graphics drivers are probably the biggest issue that anyone with a newer computer will run into when installing Linux. AMD and NVIDIA are the dominant ones on the market, both of which have awful support.

Users of the latest AMD 6xxx series graphics cards may have noticed that when they are playing Skyrim, their framerate isn't anywhere near what it is supposed to be with dual GPUs in Crossfire. AMD is working on releasing drivers with these issues fixed, but it has been too long since Skyrim has come out to just sit and wait.

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

Remember the Power Pwn, the clever little hacking tool disguised as a power strip? It's great in theory, but with a $1,295 price tag, it definitely doesn't fit into most people's budgets.

Overclocking is quite an awesome thing. When computer components are designed, they are made to run at a certain speed, otherwise known as their clock and bus speeds. These limits are not actually limits. You can overclock components, which essentially makes them go faster than their set limitations. This can save you a lot of cash when newer components come out and you don't have enough money to upgrade. However, when you overclock components, you must be careful and make sure that the machi...

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

Having bills to pay is one of the worst parts of life, especially around the holidays. And if you're extremely unlucky, you might also have to pay some hefty medical bills. This can put a heavy damper on plans, wants and needs. What's worse? The people that you owe money to are pushy and always bother you to pay in a more timely fashion, or worse, pay bigger premiums.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

This is a followup from my recent series on XSS exploitation, giving a few extra attacks/tricks to try.

As many of you Null Byters may know, I was planning on writing this article a week or two ago. Better late than never! So, let's get right to it then—choosing the right Linux distro for your needs.

Google is great. They provide us with tons of free services and open source APIs that we can code fun tools for, one of which I don't think gets enough credit: Google Voice.

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.

Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

Welcome to another Community Byte announcement from Null Byte! The goal of the Community Bytes is to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you, so that is exactly what we do! In our sessions, we have started to both code and complete HTS missions. This means that there is something for everyone here, so make sure you join us.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

Amazingly, a lot of people I know haven't even heard of SOPA or PIPA. Now, every English-reading person with an internet connection will finally have those two four-letter acronyms emblazoned in their minds. For the entire day today, Wikipedia's English-language site will be in total blackout in protest against the proposed legislation in the United States. And that's not all. MoveOn, Reddit, BoingBoing, Mozilla, WordPress, TwitPic and other popular websites are down today in protest.

When you buy computer parts, it can be a tough decision where you want to put all of your hard earned dollars into. Not only that, but when you buy a top of the line component, 3 months later (at most), your hardware will likely be outdated. This puts consumers like us in a bit of a pickle when it comes to purchasing, especially on a tight budget.

Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, even if the disk dies out, someone will probably be able to fix it and get it back to working order—at least long enough for you to back up your data. Hard drives are a bit more forgiving. As you can guess, due to the unpr...

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

If you're on a tight budget for food, whether you're in college, or someone just starting out living on their own, you're probably low on money and sick of ramen noodles. Don't get me wrong, ramen can be tasty and filling, and there is almost nothing cheaper.

Laptops are almost a necessity in today's society. It doesn't help that a laptop that can actually increase your work productivity will put at least a $1,500 dent in your wallet. I'm sure you have searched around to try to find factory direct deals, or (shiver) even looked at used laptops, but that isn't the way to go. You need something that actually has a warranty, and good performance, but at the same time, doesn't require you to sell a kidney. This can cause quite a dilemma, as it can tak...