Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

We had a blast during last week's social engineering calls. One of our attending social engineers was so clever that she convinced several people on Craigslist that lost items were hers, even if it seemed she couldn't be trusted. But females are better social engineers, naturally. Some say that females have a special knack for manipulating men, but I think that's preposterous. I can't see why that would be true in a million years (note my sarcasm).

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

I felt our community would benefit from this article. Social engineering is a big part of what we do, so it's something you should all become familiar with.

Last week's social engineering phone calls were a blast. We made some friends, and even some enemies. We scored cheap food for some buddies, made some phone bills disappear, and even got a few people some free pizzas. So overall, it was a very successful night. In light of its success, I figured we'd all do another one!

This is the first official announcement for a new weekly activity on Null Byte for the community to participate in. Starting next week, depending on how much traffic we get doing it, we are going to start doing live social engineering calls via Skype. I've made a list below so that you can get a feel for some of things we'll try to accomplish in these calls.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Just showing off the successful social engineering results. Make sure that if you used the guide, post back here with a picture of whatever you bought!

This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

When it comes to social engineering, Null Byte is here to show you how it's done. Social engineering is the key fundamental to unlocking tons of possibilities and opportunities in your everyday life. So, what is social engineering? Social engineering can be called many things. It's taking nothing and turning it into something. It's taking the bad and making it good. Above everything else, it's the art of manipulating the world and people around you—coercing that salesman into giving you a low...

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

Code execution in Microsoft Word is easier than ever, thanks to recent research done by Etienne Stalmans and Saif El-Sherei. Executing code in MS Word can be complicated, in some cases requiring the use of Macros or memory corruption. Fortunately, Microsoft has a built in a feature that we can abuse to have the same effect. The best part, it does so without raising any User Account Control security warnings. Let's look at how it's done.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

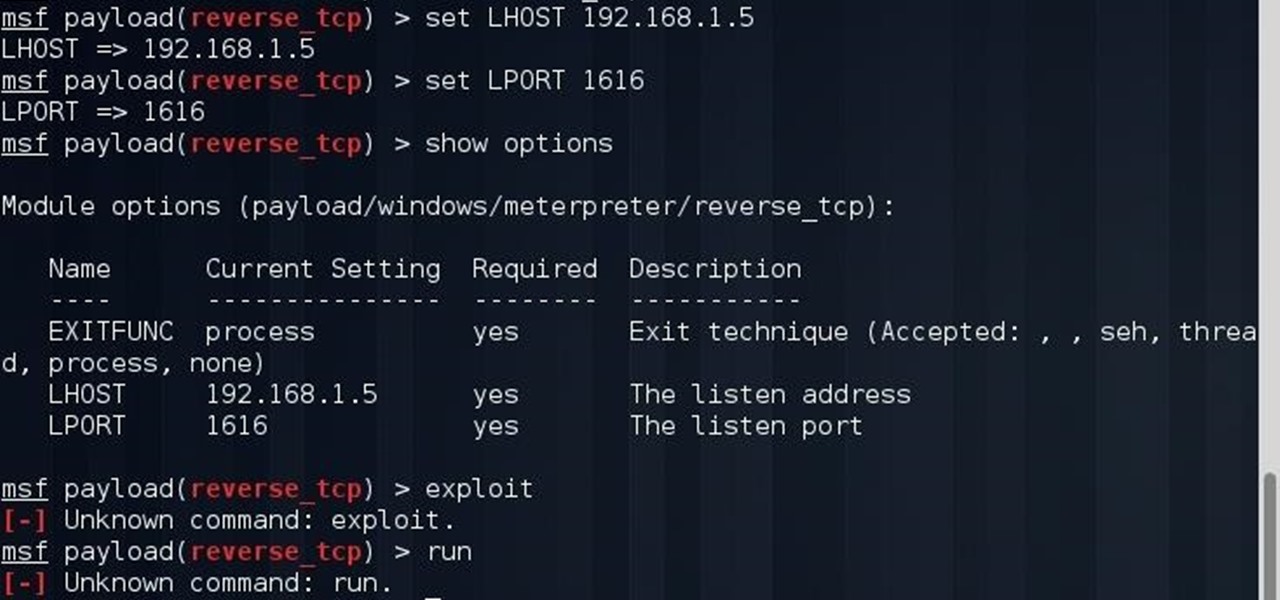
Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit of mind-kung fu.

hey everyone i wish that u can help me so ! i was trying this exploit

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

It's no secret that more and more talented computer science gurus and programmers are turning toward high-paying careers in engineering. Today's engineers stand at the forefront of some of the world's most important and exciting technological innovations — ranging from self-driving cars and surgical robots to large-scale construction projects and even space exploration—and our reliance on these talented data-driven professionals is only going to grow in the coming years.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Hello friends. This is actually my first how to.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

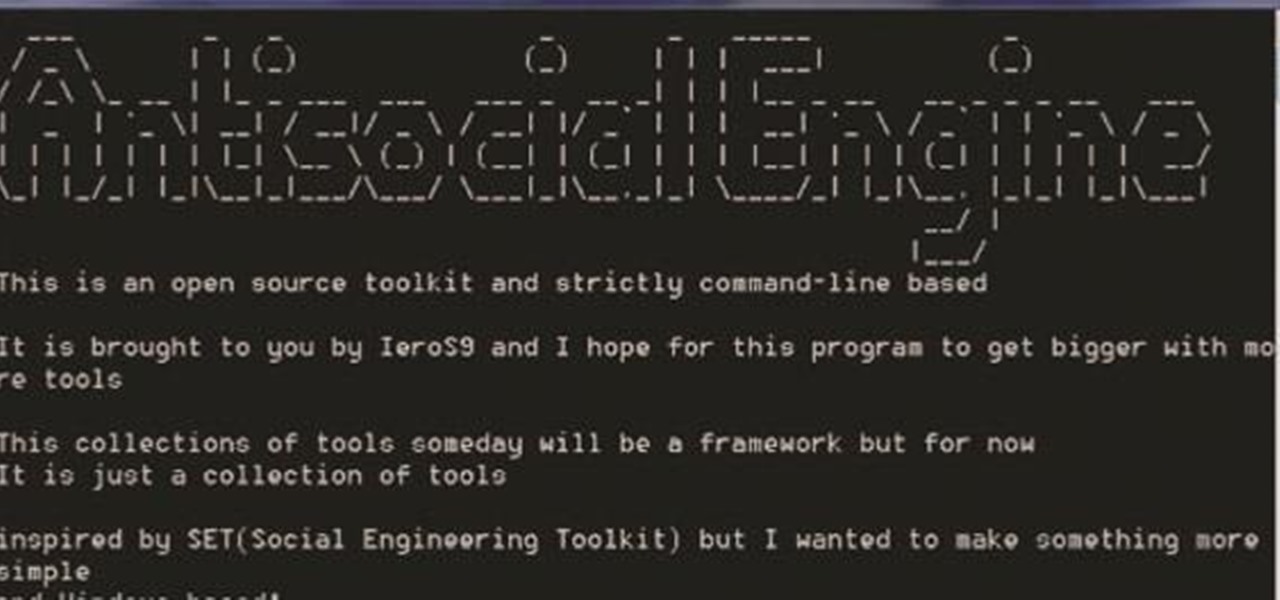
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

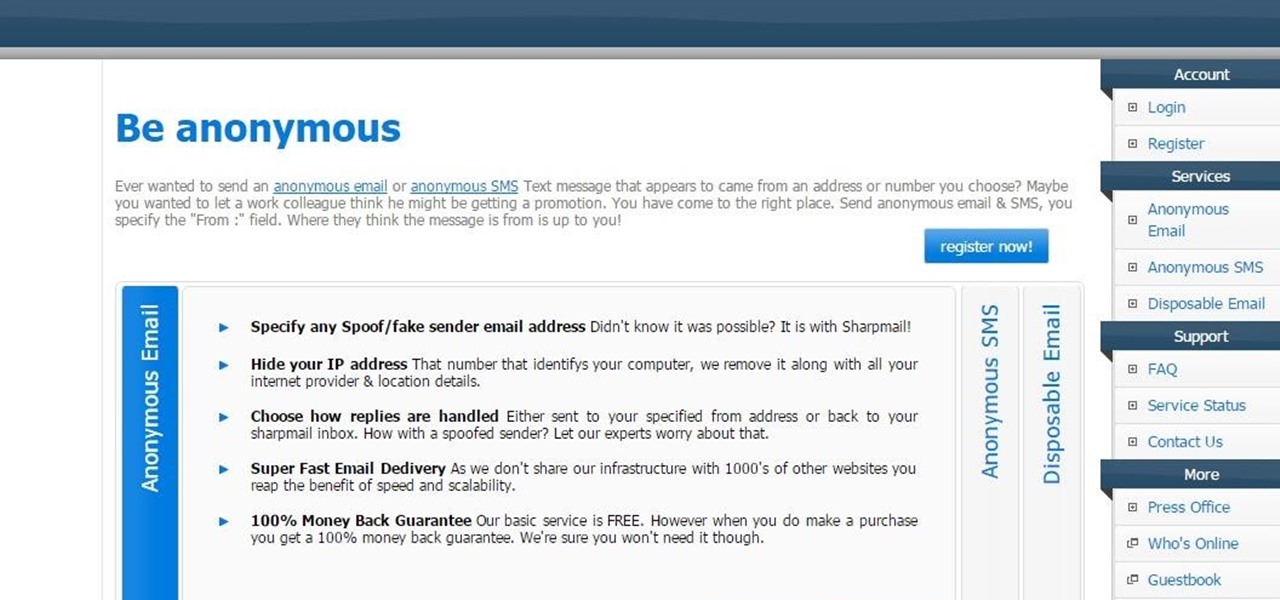
Welcome, The Geeks!! This is my first article on email spoofing and hope everyone likes it.