Hot Null Byte How-Tos


How To: Reverse Shell Using Python
Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.
Basics of Ruby: Part Two (Loops)
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

How To: OpenSSL Unique Encryption/Decryption Scripts
In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

Hack Like a Pro: How to Install & Use a Secure IRC Client with OTR
Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Basics of Ruby: Part 1 (Data Types/Data Storage)
Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.
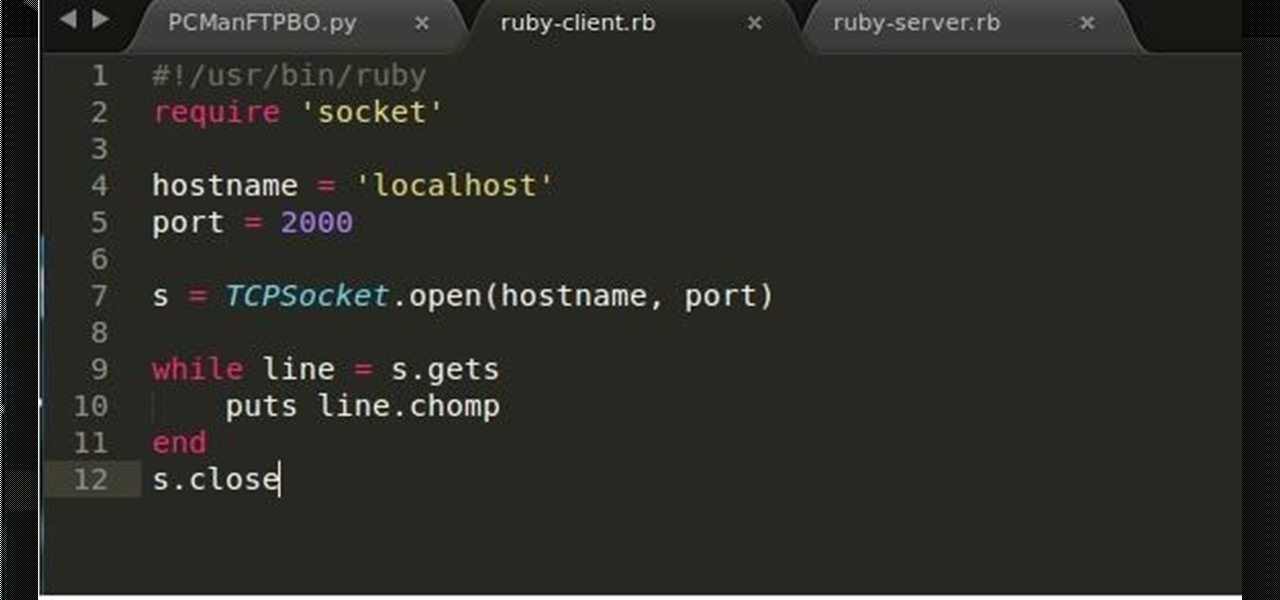
How To: Make a Client/Server Connection in Ruby
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

How To: Make Your Malicious Android App Be More Convincing.
Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)
How To: Hack Metasploitable 2 Part 1
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Hack Like a Pro: How to Hack Web Apps, Part 4 (Hacking Form Authentication with Burp Suite)
Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

How To: Configure a Reverse SSH Shell (Raspberry Pi Hacking Box)
If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

How To: Make Super Hidden Folders
Basically what this tutorial will show you is how to make folders that won't show up in windows even with the show hidden files/folders option on. First thing you need to do is make a folder on your desktop. Then you need top open up command Prompt and type in the following command (Don't forget quotations if file path has any spaces in it):

SPLOIT: How to Find the Exact Location of Any Internet Address ( GUI - Linux )
Greetings My Fellow Aspiring Hackers,
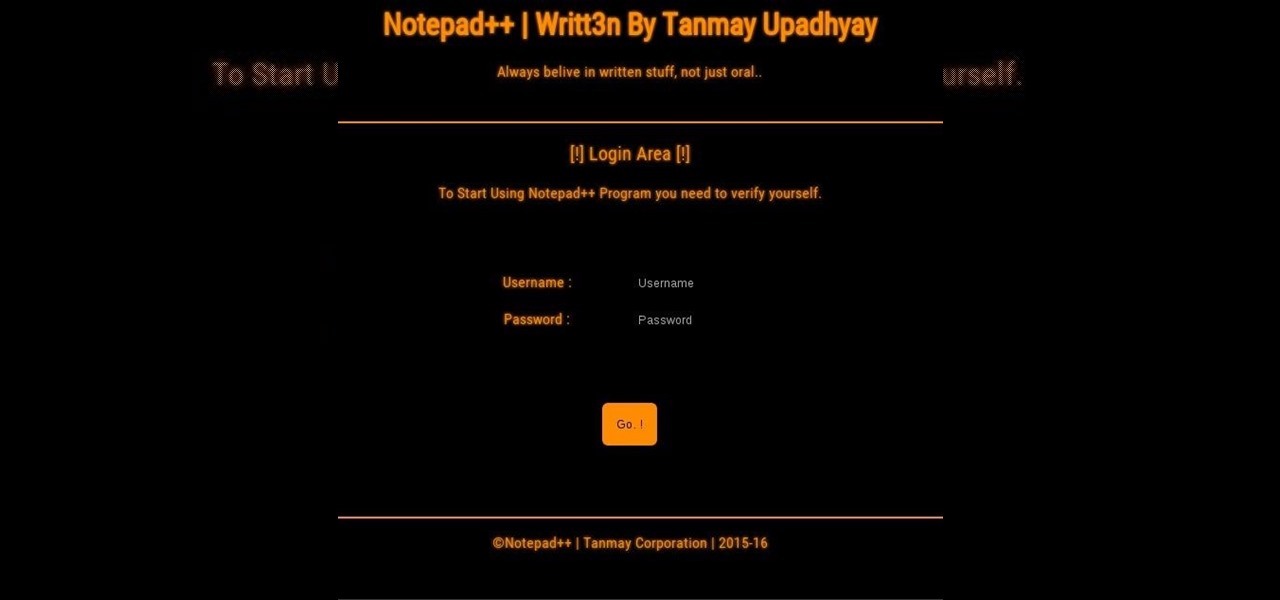
How To: Your Personal Program [ NOTEPAD++] Written in PHP
Hello friends, I'm new in world of web developing. so, i decided to code my own program to save and read my personal notes and which is also secure, so i dont need to worry :) if you have any suggestions please fell free to tell :)
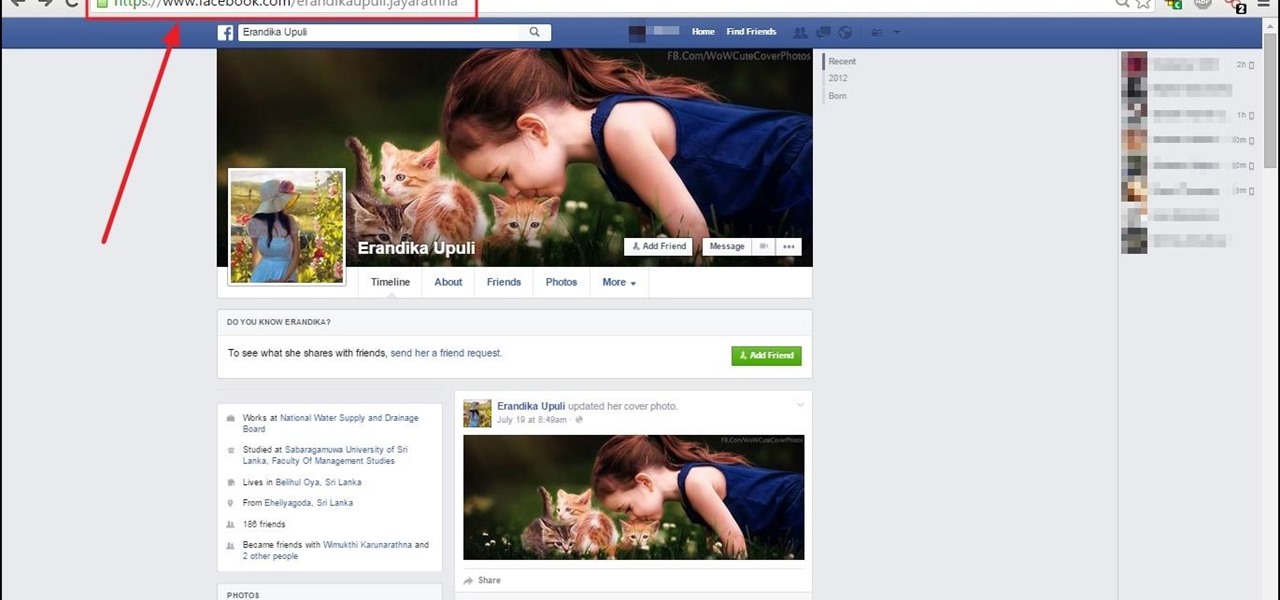
How To: Find Who Is Using Facebook via Mobile
it is helpful to know if you try to hack non of your friend who using facebook via mobile or PC.within this simple trick you will find does your target use or not facebook via mobile .

How To: Grab All the Passwords
This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

How To: Simply Gather Saved Passwords (Quick Tutorial)
Hello you sexy, savage, surreptitiously tech-savvy penetrators (Pun intended)!

How To: Turbo Ping Sweeping with Python
Why did I write this when they're tons of scanning tools available.

Hack Like a Pro: How to Use Hacking Team's Adobe Flash Exploit
Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.
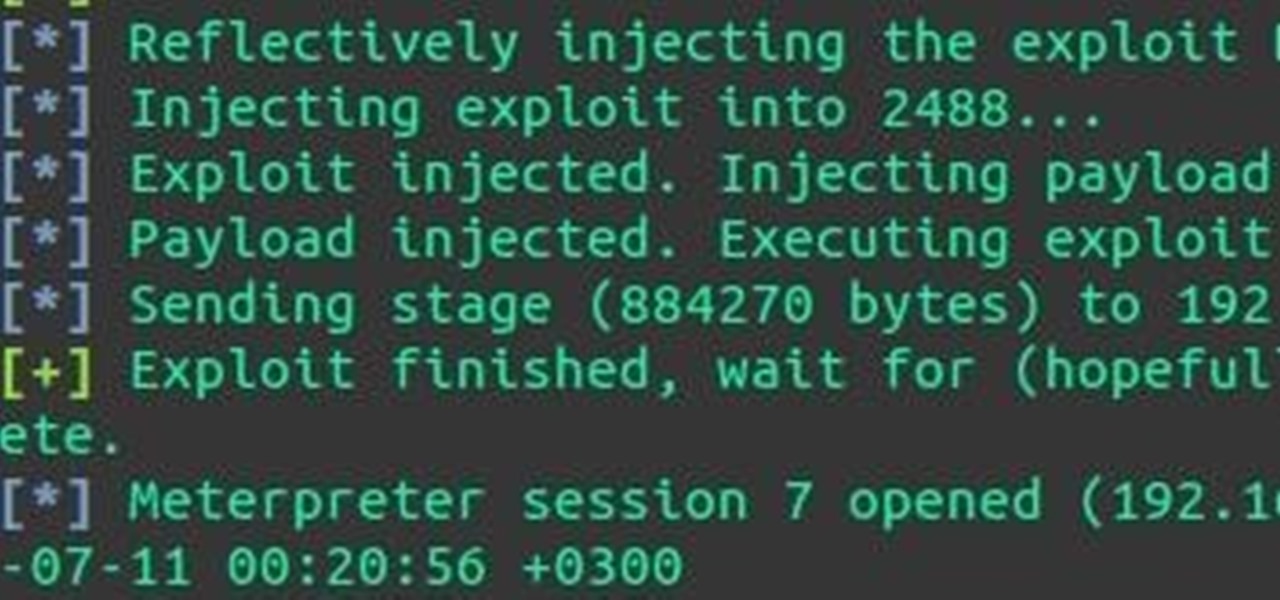
How To: Post-Exploitation Privilege Escalation
Hey everyone, I've been encountering some problems with privilege escalation when the target has an AV installed, so here's a tutorial for when the almighty "getsystem" doesn't cut it and "bypassuac" gets blocked by the AV. The machine is running Windows 7

Oops: Some Security Doors Can Be "Picked" with Canned Air
Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

Hack Like a Pro: How to Hack Web Apps, Part 3 (Web-Based Authentication)
Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

How To: Backdooring on the Fly with MITMf
Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

How To: Make a Locked File Cracker with Python
Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 8 (More Windows Registry Forensics)
Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

How To: Make a Trojan Appear Legitimate
So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

How to Hack Wi-Fi: Selecting a Good Wi-Fi Hacking Strategy
Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.
How To: Make a Secret Language with Python
Sometimes our information important. So important that we have to encode it to keep it away from criminals. What better way to encode information than to make our own encoder with Python?

How To: Fun with OSX Terminal
Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

How To: Inject Payload into Softwares via HTTP
Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Social Engineering: The Most Powerful Hack
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

How To: Look Cool with Notepad with Viruses!
Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool!

How To: Exploit Shellshock-Vulnerable Websites with Just a Web Browser
I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!
How To: Disable Autorun
Hello, Hackers/Viewers, Today's topic is going to be based on how to disable autorun for Removable Disks and Drives. Doing that is very easy, i you read the below!
How To: Make & Study Viruses
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

How To: Create Backdoor on OSX
Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 9 (How to Install New Modules)
Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

How To: Hack a Site Knowing a Bit of HTML (hackthissite.org) Part 3
Hi guys. I'm here to go for level 7 now lets get it start but i apologize u all that i posted this very late but now lets rock:

How To: Defeating HSTS and Bypassing HTTPS with DNS Server Changes and MITMf
It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).
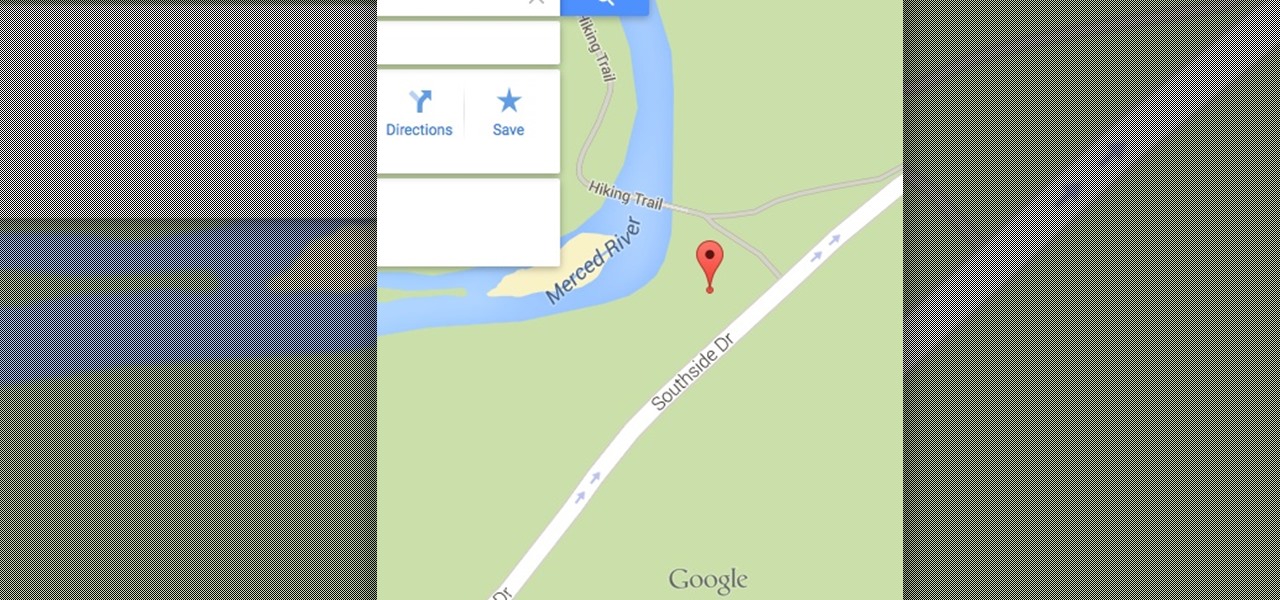
How To: Find Target Location with an iPhone Picture
Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.







