In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.
For a web browsing proxy and hidden services host, Tor gets the job done well. But if you are looking to expand your options for secure communication, then enter I2P! This article will show you how to obtain and set up I2P, and in the process, we will also configure an IRC client to access the IRC2P network and get you up and running.
Invisible Internet and Onion Routing
I2P initially began in 2003 as a proposed modification to Freenet. To deal with a wide range of attacks, I2P is fully distributed with no centralized resources— hence there are no directory servers keeping statistics regarding the performance and reliability of routers within the network. I2P is not 100% secure, as nothing is 100% secure, but using it will provide you with meaningful security nonetheless.
Content sent over I2P is encrypted through three-layer garlic encryption, used to verify the delivery of the message to the recipient. All messages passing through a tunnel are encrypted by the tunnel gateway to the tunnel endpoint, and undergo inter-router transport layer encryption along the way. You also have the ability to tunnel TCP/IP based applications (IRC, Jabber, steaming music, etc.) through the network. In fact, you can even tunnel your torrent downloads!
Step 1 Download I2P
Let's start with a visit to the download page to grab the Windows binary or source code, if needed. If you are using Debian/Ubuntu or Mint, we can add the repositories by simply typing:
$ sudo apt-add-repository ppa:i2p-maintainers/i2p
$ sudo apt-get update
$ sudo apt-get install i2p
This downloads and installs the I2P router on your computer.
Step 2 Start the I2P Router
Now that we have the packages downloaded and installed, we must start the service. We do this by simply typing:
$ i2prouter start
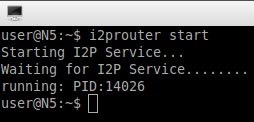
After we type that command, the I2P router will begin to bootstrap itself into the network. It is recommended to give this process some time as it seeks out and adds other nodes for you to route traffic through. After a few seconds, I2P will open a browser with the router console as seen below. You may close this.
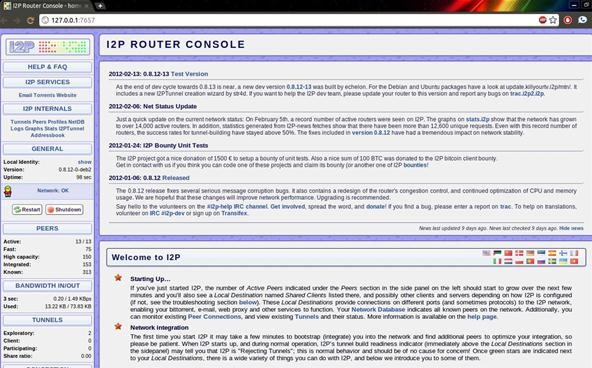
Step 3 Invisible Internet Relay Chat
Some of you might have a preferred IRC client already. I use Irssi myself, but Xchat will work for most people. Normally, when you open the client you have the chance to connect to a server and port number. Because I2P runs as a service connected to your loopback address, we need to connect to it to access the IRC2P network by typing:
/server localhost 6668
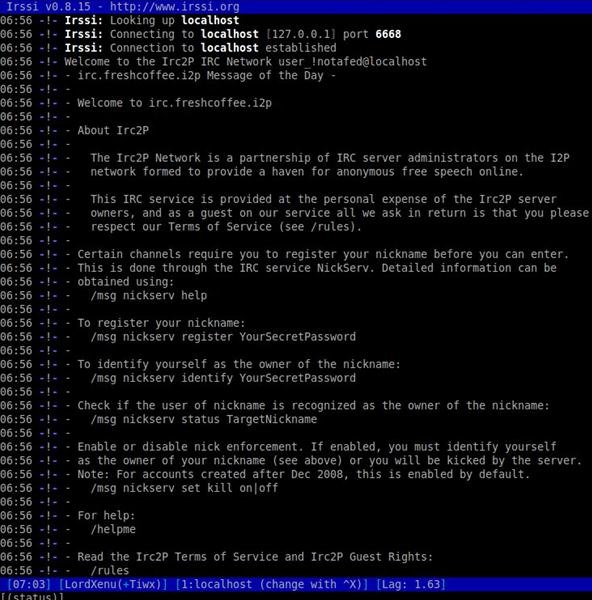
That's it! You are now connected to the IRC2P network. You can use normal IRC commands such as /list to locate channels. Also please feel free to /join #nullbyte and #i2p and say hello!
tl;dr
Just want the commands to get up and running? Look no further.
$ sudo apt-add-repository ppa:i2p-maintainers/i2p
$ sudo apt-get update
$ sudo apt-get install i2p
$ i2prouter start
Then start your IRC client and type:
/server localhost 6668
/join #nullbyte
See you in the Deep Web!
Just updated your iPhone to iOS 18? You'll find a ton of hot new features for some of your most-used Apple apps. Dive in and see for yourself:
























11 Comments
there is a way to mine IP addresses with both I2P and Tor. Since the core of tor is about 2.5 K at most vs about 20K+ with I2P hosting on tor is MUCH more risky. With I2P you can't tell who hosts stuff and who doesn't host stuff. With tor leeching is encouraged more and hence it is generally easier to do ip mining based attacks. I wrote a script that queries an i2p user's local netdb (a database of all peers your router knows of) and looks for entries based on geoip data. Also... it would be great to allow anonymous (moderated) posting.
This is great! I've downloaded tor and i2p and have been browsing. Im also using xchat. I saw that Tor has email services too. Are these anonymous also? Can these be accessed by outside emails (like can I send an email to gmail?). I wouldn't but just want to know how the Tor email works.
I2P does have a clearnet i2p mail system but as for Tor you'd have to ask the people who run that.
I would avoid gmail completely. /0.02
Hey bro can you help?
I tried to install Tor on kali but it says "Tor should not be run as root"
and when i tried to install i2p, there's this msg that display:-
E: dpkg was interrupted, you must manually run 'sudo dpkg --configure -a' to correct the problem.
Can you advice?
Great Article! I actually joined #nullbyte a few times and no one is ever there
Thanks. User base varies still. Sometimes we have a ton of people and great discussion and sometimes it is a ghost town.
allen, real noob here with all this so please be easy on me. so can i use i2p to do my regular browsing or can i only browse on "underground" networks? sorry if this sounds dumb..But im basically becoming more and more antigovernment after finding out more and more invasion of privacy daily and i want something to allow me to browse and email in peace, or relative peace at least, as securely as possible. whats the best way for someone like myself
Is this secure? or will this open my computer up for people to have back door access?
I love the idea and the thought.
lemme no plz
so ikndoit2
Hi everyone!
I am trying to set up i2p, but everytime i try to run the comand:
i2prouter start
I get the warning:
WARNING: I2P Service may have failed to start.
And the console doesn't even appear. I've tried searching for this problem but I didn't find anything that fixed this problem. I also tried reinstalling it, but it gave me the same warning. When doing this I noticed that the i2p router tried to start right after instalation, but it got the error message:
touch: cannot touch '/var/lib/i2p/i2p-config/.perms': No such file or directory
So again i did some research, but to know fruition. So i thought you might have some insight or leads i could follow.
Thanks
What are the risks of adding a i2p node on my network? If someone found my location, do they have complete access/control?
Share Your Thoughts