What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

The already robust and ingenious Nmap tool has received a whole slew of new scanning scripts that can be used to do all sorts of naughty endeavors. Notably, the SQLi module, since it is a necessary evil that we must cover here at Null Byte. This major update is going to fuel today's lesson.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.
Looks like someone created a remote exploit using javascript. Pretty scary stuff o.o. Intel Core2Duo cpu cache controller bug PoC | Inj3ct0r - exploit database : vulnerability : 0day : shellcode.

When i went to class today, a good friend asked me a question. He wanted to know what the best hacking software was to basically do everything. What i told him was this: Well there isn't an "Ultimate" tool boot there are a number of tools which deserve a "Medal." So what i'm trying to say here... What are some of the best hacking tools available right now? For starters i created a list with some of the tools.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.
PacketStorm member Ben Schmidt has found dozens of 0day's in Multiple WordPress plugins.

Here's another delicious Byte. Ucha Gobejishvili, a Georgian Security Researcher under the handle of longrifle0x, discovered two cross site scripting (XSS) vulnerabilities on the official website of Forbes. He discovered the hole in two different locations on the site, and has already informed the website of the vulnerability.

BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which was just identified this weekend.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer installed already. If you are young and just starting out, this may be hard for you to manage with your current salary. If you have no washer and dryer, the only alternative is the laundromat.

Hardware hacks are something I feel we don't get enough of at Null Byte, so today I figured I would introduce a fun one. I've always been a curious hardware hacker. Taking things apart and learning how their internals work has always been a part of my nature. Quite some years ago, my father showed me a really cool trick on how to hack normal radios to scan frequencies that are normally non-listenable. This little hack allowed us to scan frequencies belonging to law enforcement, and even frequ...

Friday's Community Byte was weird. The intent was to do a HackThisSite mission, but upon time to begin, everyone in there was programming without my assistance, with the help of Sol Gates. This is great! It's really awesome that everyone enjoys programming that much and will make the effort to learn even when I am not present. So, a tip of my hat to Mr. Sol Gates and the rest of you fine people.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Watch out Macs. Flashback is back. Variations of the trojan have reportedly infected 600,000 Mac computers around the globe, with about 57 percent in the U.S. and another 20 percent in Canada.

Hello to you all I've been reading for a long time now and haven't seen anything about this vulnerability so i thought id post it to make sure it was here

Welcome, my aspiring hackers! In this tutorial I'm gonna be showing you how to hack Wi-Fi using the wps compatibility of a router, in , of course, Kali. First, fire up Kali.

Welcome back Hackers! We have embed a Backdoor in to a PDF file,Android package File.

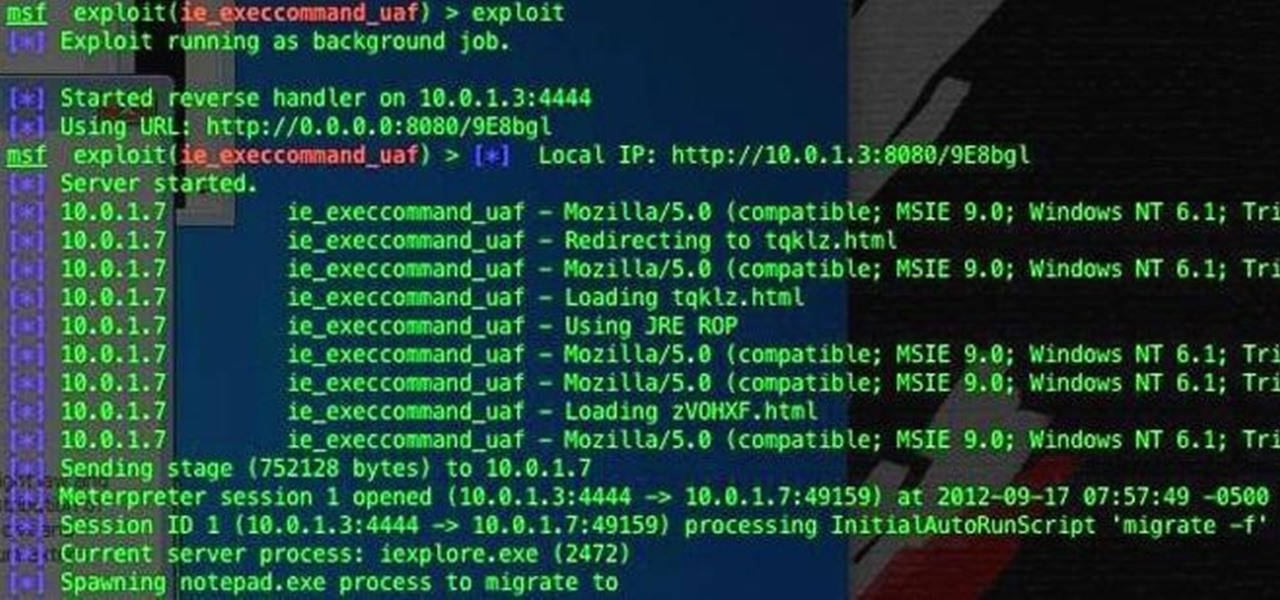
If you're one of the people who make up the nearly 24% of Internet users on Internet Explorer, now is a good time to click on 'Check for updates.' Researchers have found yet another Metasploit Zero-Day exploit that leaves IE 7, 8, and 9 vulnerable for Windows users. Brought to us by the same group as the Java 7 exploit a few weeks ago, this one uses a malicious site to install the Poison Ivy backdoor trojan while unsuspecting users browse. Once installed, it basically gives the attacker the s...

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...

Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, and anything you feel like...

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).