Everything Else


How To: Hack Hackademic.RTB1 Machine Part 1
Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

How to Meterpreter: Interactive Ruby Shell (A Quick Introduction)
First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).
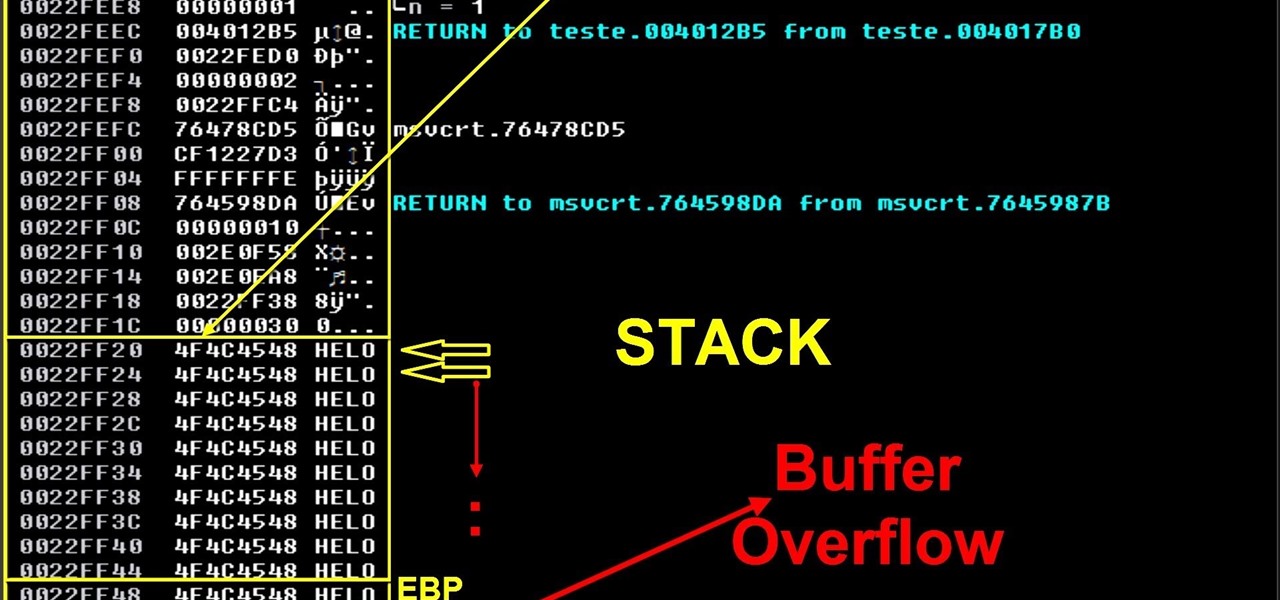
How To: Exploit Development-Stack Base Buffer Overflow/Part 1(VIDEO)
On this video I will demonstrate a simple concept of stack base overflows. This is the first part of my exploit development tutorials and after that I will demonstrate seh buffer overflow, ROP/DEP/ASLR, spraying the heap, search for bugs/think different etc.
How To: Build and Install Kali Nethunter (The New Version) On a Supported Android Device Running Android 6.0.1
Hi guys. Hope you all had a good Christmas , today i have a tutorial for you.
How To: De-Freeze Kali 2.0. ?
Hello, hackies... Today i want to give you a simple but effective step-by-step guide to

How To: Setup Dendroid (Android RAT)
This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

How To: Hack Android's WhatsApp Images with BASH and Social Engineering
Hello friends. This is actually my first how to.
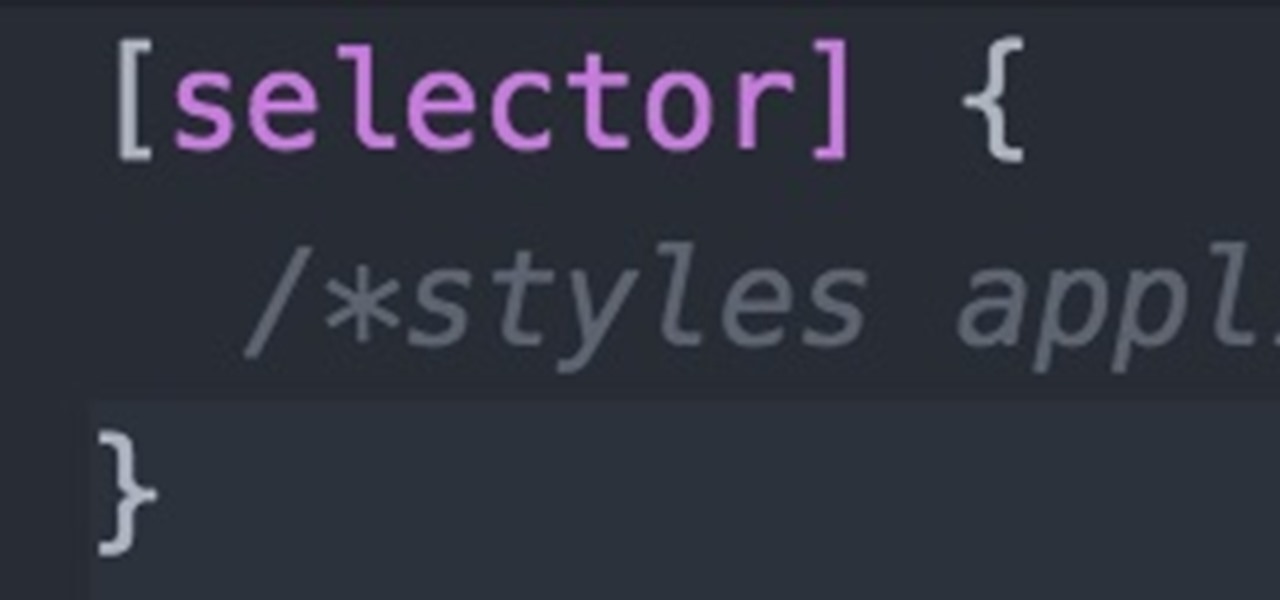
How To: Web Development 04 - Styling Pt 2
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.
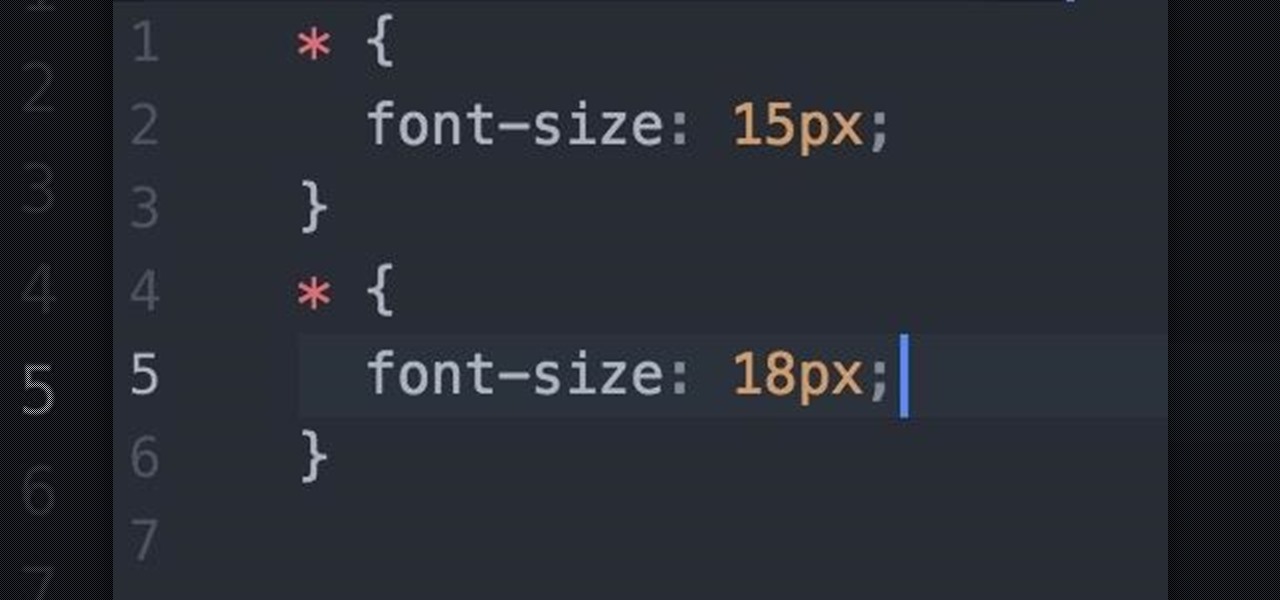
How To: Web Development 03 - Styling Pt 1
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

How To: Become a Hacker
Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.
How To: Web Development 02 - Simple Webpage
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.
How To: Remotely Reset Router P.DG AV4001N
I assume you are on the same network with your router 1 - open a terminal window

TypoGuy Explaining Anonymity: Secure Browsing Habits
to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

How To: Web Development 01 - Setting Everything Up
Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

How To: Protect Yourself from Someone Trying to Hack into Your Mac
If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.
How To: Bypass Two-Way Authentication on Facebook with Android Script
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

How To: SQL Injection! -- Detailed Introduction.
Hello NullByte! This will be my first How To series.

Botnets and RATs : Precautionary Measures and Detection (Part 2)
Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

How To: What is An Arduino? (Part 1)
I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.
How To: Increase TxPower Kali Sana Linux 2.0
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

How To: Hack into a Mac Without the Password
Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:
How To: Fake Captive Portal with an Android Phone
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...
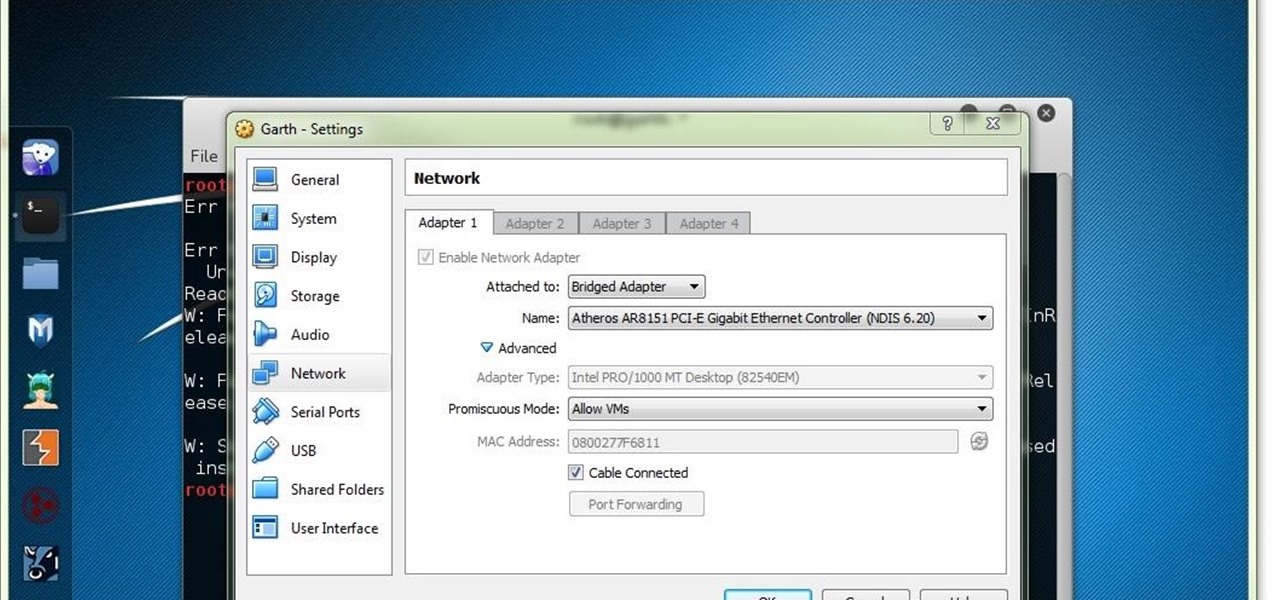
How To: Struggling to Connect to WiFi Network on Kali Linux 2.0 VirtualBox
Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.
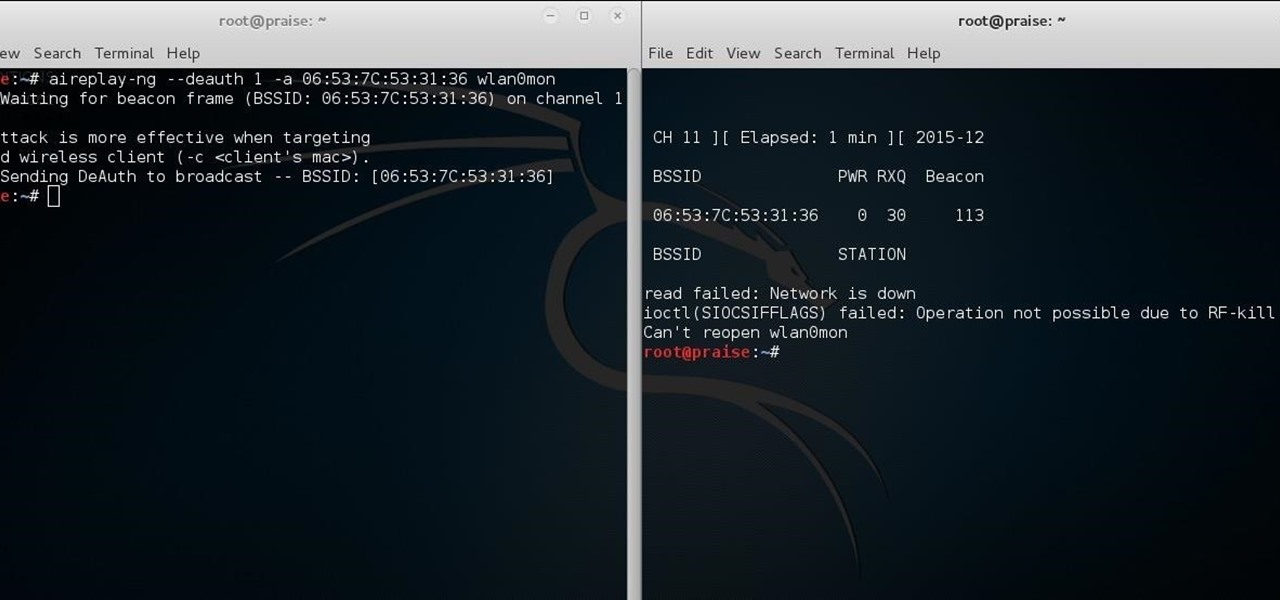
How To: Fix "Network Is Down" on Airodump-Ng
Hello there learners and readers! I figured I'd show you guys my problem and how I solved it, hoping that it would help people who are facing the same issue. Today, we'll be talking about the solution of

How To: Web Development for Hackers 1.1: HTML,CSS,JS
hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.
How To: Install ParrotSec Sealth and Anonsurf Modules on Kali 2.0
First of all, before we start, the modules and some of the tutorials belongs to Und3rf10w, not mine!

Cryptocurrency for the Hacker : Part 3 (Why It May Be a Bad Idea for You)
Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

How To: Displaying Text from a File C++
This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)
How To: Antisocial Engine
A.E Hi again this is my second post on nullbyte. The first one was on how to make a remote screenshot captor, now I will give you a presentation for a project of mine(I have named It Antisocial Engine) that It is not something extraordinary but will help many guys.

How To: Hack Any Windows 7/8/10 User Password Without Logging In
Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

How To: Properly Submit Tools for the Null Byte Suite
Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

How To: Learn How Elliot from Mr. Robot Hacked into His Therapist's New Boyfriend's Email & Bank Accounts (Using Metasploit)
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

How To: Download & Install the Null Byte Suite
Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

How To: C++ Hash Cracker
This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

How To: Introduction to Botnets and RATs : Part 1
Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

How To: Execute Remote Commands on a Disconnected Victim
Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

How To: Make Your Remote Screenshot Captor(Python)
Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

TypoGuy Explaining Anonymity: Choosing a Good VPN
You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

How To: Hack TOR Hidden Services
A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

Don't Be a Script-Kiddie part2: Building an Auto-Exploiter Bash Script
Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.







