Hot Null Byte News Stories


News: Hak5 Just Released the Packet Squirrel
Hak5's products get a lot of attention. Popping up in popular shows like Mr. Robot, their hacking tools are bold proof of concepts with space built into the design for the community to add their own tweaks and modifications. On Friday, Oct. 27, Null Byte attended the Hak5 release event in San Francisco to check out their latest devices, including the new Packet Squirrel.

News: Anonymity, Darknets and Staying Out of Federal Custody, Part One: Deep Web
You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

Goodnight Byte: HackThisSite Walkthrough, Part 7 - Legal Hacker
Last Friday's mission was to accomplish solving HackThisSite, basic mission 8. This meant that we had to learn some more basic Unix commands.

News: How to Study for the White Hat Hacker Associate Certification (CWA)
Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

News: Samy's MagSpoof Hacking Device Was Just Featured on Mr. Robot
Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

News: The Hacking of Blackhat, the Movie
A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

News: Finding Hidden Metadata in Images (Oh, the Possibilities)
Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

News: Wallpapers
I got bored so i wanted to know what each of you got as a wallpaper. Here is mine, post yours in the comment.

News: 20 Things to Do with Kali Linux After Installation
Okay, so first off, I absolutely did not, any any way shape or from, take part in the writing of this article, but I really think that this will be helpful to all of us Kali users. Here is the article made by blackMORE Ops: 20 things to do after installing Kali linux

News: 12 Easy Exploits to Raise Thief Skills in Skyrim
Here is the final part in Null Byte's series on mastering the skills in The Elder Scrolls V: Skyrim. We have already covered the slick and brutal methods to raise our Spellcasting and Combative skills. Skyrim's intelligent new leveling system has trumped the former methods of spamming repeated moves to raise levels quickly. Rather than casting a spell, or jumping up and down constantly, the new system requires that we use our skills in practice to get experience for them. This causes leveling...
News: Remote Chrome Password Stealer
These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine.

News: God's Eye
If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

News: 8 Wireshark Filters Every Wiretapper Uses to Spy on Web Conversations and Surfing Habits
In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

News: Anonymity Networks. Don't use one, use all of them!
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

News: Block Cell Phone Signals on the Carrier of Your Choice by Hacking a Radio Frequency Jammer
Cell phone jammers, a DIY endeavor for the darker crowd. I'm pretty sure we've all considered having one at some point: whether the obnoxiously loud woman next to you is announcing private bedroom stories to a crowd on the subway, or your kids are grounded from using the phone (and consequently snagged a hidden prepaid phone), sometimes having a cell phone jammer comes in handy.


News: A Brief History of Hacking
Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

White Hat Hacking: Hack the Pentagon?
The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

TypoGuy Explaining Anonymity: Who Is Anonymous?
Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

News: Evil Twin(Part 3) - the Full Bash Script
Hello All, So to recap in part 1 I went through setting up the dchp server. Part 2 detailed the bash script. Now in part 3 I will post the entire bash script. I am doing this in its own post because Part 2 is just way to much info on one post IMO.
Mr. Robot: Hacking Sequence Explained
Hi! In case you missed it, on Reddit is pretty good article about attack on

Antivirus Bypass: Friendly Reminder to Never Upload Your Samples to VirusTotal
For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

News: Hack Your Computer's BIOS to Unlock Hidden Settings, Overclocking & More
Your BIOS, or Basic Input Output System, is the firmware on your motherboard responsible for initializing your computer's hardware when it is first powered on. It probes for video adapters, RAM, the whole works. The BIOS provides a small library of basic input/output functions used to operate and control the peripherals such as the keyboard, text display functions and so forth, and these software library functions are callable by external software such as the OS and system software within sai...

News: What the Heck Was Stuxnet!?
As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Digital Lock-Picking: This Simple Arduino Hack Opens Millions of Hotel Keycard Doors
It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

Goodnight Byte: HackThisSite, Realistic 5 - Real Hacking Simulations
Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

News: 'Impossible to Identify' Website Phishing Attack Leaves Chrome & Firefox Users Vulnerable (But You Can Prevent It)
Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.
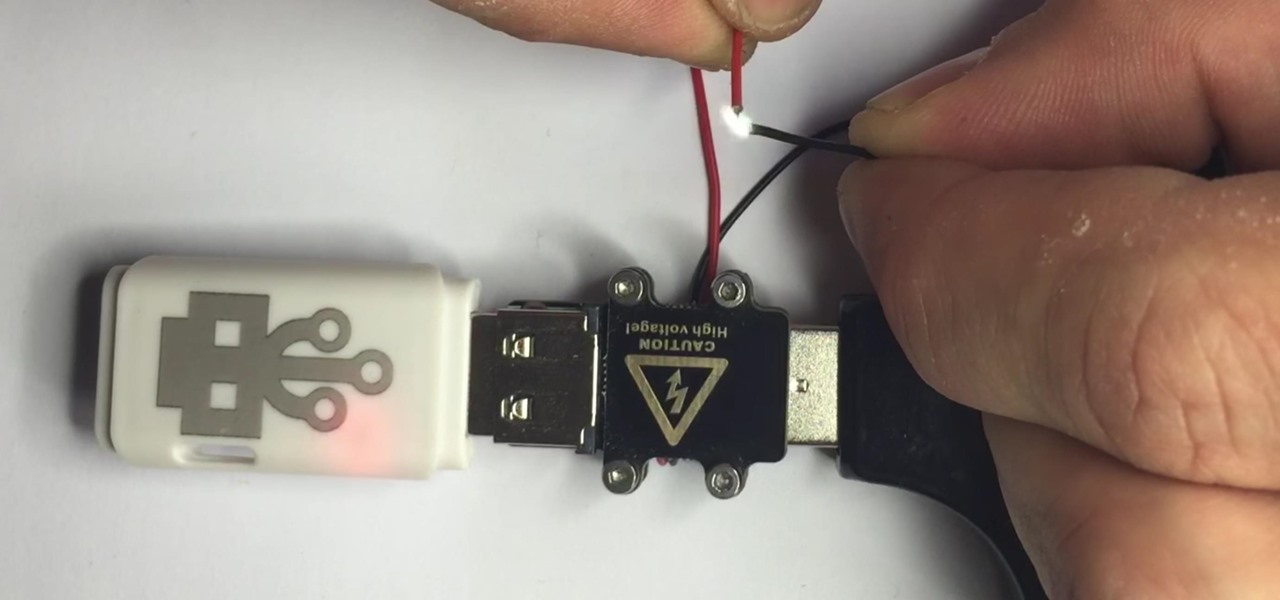
News: The Cheap USB Kill Stick That Destroys Any Computer You Want
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.
News: Social Engineering for the hell of it.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.
Security Tube: Useful Video Tutorials for IT Security.
Hi everyone. I'm relatively new here and I have learned a great deal from many of you already and would like to try and give a little something in return.

Goodnight Byte: HackThisSite, Realistic 4 - Real Hacking Simulations
Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."
News: Change from BASH to zsh
Hello fellow Null-Byters today I will be showing you how to change from the simple but powerful BASH system to a more powerful and faster Z - Shell system. This change can be permanent if you want but doesn't have to be, and it is an extremely simple one to perform.

News: Flaw in Wal-Mart Returns System Allows Major Thefts to Go Unnoticed
We love tearing apart security here at Null Byte. Several years back, upon returning items to Wal-Mart due to a malfunction, I noticed something very peculiar about the way their overall procedure goes. I brought the item up to the desk, and the woman asked if it didn't work, which I responded affirmatively. Without a moment's notice, she takes it right off to the defective items area and asks if I would like cash or store credit.

Secure Your Computer, Part 3: Encrypt Your HDD/SSD to Prevent Data Theft
Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

Buyer's Guide: Top 20 Hacker Holiday Gifts for Christmas 2017
Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

News: 'Beast' Cracks Billions of Passwords in Seconds
Dr. Michael Pound, a computer science researcher and professor at the University of Nottingham, uses hashcat and 4 GPUs in parallel to go through 1o billion hashes a second in this Computerphile video. He calls his deep-learning server the "Beast." If you're new to cracking passwords, he does a great job breaking down the process of what's going on as hashcat does its magic.

News: Capture the Flag, Round 1
As many of you know, Standard User proposed that we start a Capture the Flag (CTF) competition. I think this is a great idea! Standard User proposed to set up the server and the flags for this first competition. Since Standard User was new to our community, I asked him to postpone the start of this competition until I had a chance to make certain that this was safe and legitimate for our community. I have good news! With the help of Phoenix750, we have done the necessary due diligence and we ...

Security Alert: Your Wireless Mouse or Keyboard Can Be Hacked
If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard dongle (receiver).

News: Anyone Else Likes TDoS?
Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

News: Anonymous vs ISIS
As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.







