Everything Else


News: The Cruel Crypto Game; How to Beat CryptoLocker Ransomware
It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.
News: Codewars
I've been frequenting this website I recently found out about called Codewars.com. It's pretty neat! In order to sign up, you need to pass a few simple coding tests and then you can start taking on the challenges, which they call kata. Basically, you are given a task and have to write a function that completes the given task and have to test it out on a bunch of test cases they give you. Once you pass the test cases, you can submit it and gain reputation points. It seems like a really good wa...

News: Wallpapers
I got bored so i wanted to know what each of you got as a wallpaper. Here is mine, post yours in the comment.
News: Just A Message
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.
News: Jailbreaking iOS 9
As many of you may have heard, Apple's new iOS 9 is "rootless", which supposedly would make jailbreaking much more difficult. However, it has been shown to be possible. ih8sn0w posted a youtube video of his jailbroken iphone running iOS 9 and even gave some hints about it in the video description section. However, he also stated that he will NOT be releasing it to the public. So it would be quite the feat and adventure to take his hints and comments and use that to figure out how to jailbreak...
News: Xcode Ghost
I just came across an article on Reddit about some iOS malware called XcodeGhost that has affected many apps in Apple's Chinese App Store. After reading more about it, I thought it was pretty incredible how the attackers had pulled this off. As the name might imply, the malware was not loaded onto iOS devices because the iOS devices were directly hacked, but rather it was the Xcode versions used by the developers of legitimate apps that were hacked! Basically, some devs were using hacked Xcod...

News: Is an Unhackable Kernel Really Possible?
In an effort to prevent drones from being hacked, DARPA has been developing an "unhackable system," and seems to think they're almost there. The development team "proved" mathematically that their kernel was unhackable, and they hope to use it for more than just drones (power grids, cars, phones, pacemakers, etc.).

News: The Biometric Authentication Conundrum
Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

News: How to Better Your English (For Foreign Speakers)
Hello! I'm newbie at Null Byte and I want tho share some of my thoughts with you guys, hope you like it. I've been inspired by 3 facts for making this: 1- The post 'How to write better code', 2- A few illegible comments at some posts, 3- I myself have never written such a long text in English, this will be my first one!
News: Interesting TV Show on State Surveillance Powers
A cool show aired in the UK on Channel 4 last night where a number of ordinary subjects (note: we are not citizens!) had to disappear for 28 days whilst being pursued by professional hunters using the powers available to the State. Well worth a watch. http://www.channel4.com/programmes/hunted/on-demand/60136-001
News: The Consequences of Hacking
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.
News: Social Engineering for the hell of it.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

News: God's Eye
If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

News: How to Write Better Code
Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

News: My Review on Kali 2.0
Hello guys, its been quite a while since my last post. (sorry for the lack of images)

News: Banks Around the World Hit with Repeated DDoS Attacks!
In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.
Where Do I Start: Learn How Programmers Think
Common programming blunders can be your best friend when trying to craft your own exploits. If you spend a little time reading what some of these common blunders are, they can uncover potential attack vectors or just show you the weird ways in which computers can store and recall data or access system resources.

News: A Game of Real Hacking
Bad news first: It's not out yet, but it's coming really soon. The premise for the game is this:
Security Tube: Useful Video Tutorials for IT Security.
Hi everyone. I'm relatively new here and I have learned a great deal from many of you already and would like to try and give a little something in return.

Antivirus Bypass: Friendly Reminder to Never Upload Your Samples to VirusTotal
For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Where Do I Start: Learn the Fundamentals
I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

News: Why Newbies Deserve Respect
Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

News: Can We Hack the Hackers?
Welcome back, my rookie hackers!

News: Hack This Site
If you're looking to train yourself, and see how good at hacking you really are, I'd recommend Hack This Site. You've most likely already heard of it, but it's super fun to use and is also safe. You learn a lot, too, and there's no tutorials or anything. What you do is you pick a challenge and then it gives you a little scenario. For example I started the basic challenges about 10 minutes ago and am on challenge six, it asks for a password and you scramble through the code, editing bits and b...

News: Hackers Hijack Jeep, Taking Almost Full Control of the Vehicle
Charlie Miller and Chris Valasek conducted an experiment earlier this month that ended up with a Jeep in a ditch, although the driver didn't drive it there. The two remotely hijacked the car, controlling it through a laptop and a cell phone. FCA says vehicles from the 2013 and 2014 model years with 8.4-inch touchscreen are affected. That includes Ram pickup trucks, the Dodge Durango, the Jeep Grand Cherokee and the Viper. Some 2015 Chrysler 200 sedans are also affected.
Mr. Robot: Hacking Sequence Explained
Hi! In case you missed it, on Reddit is pretty good article about attack on
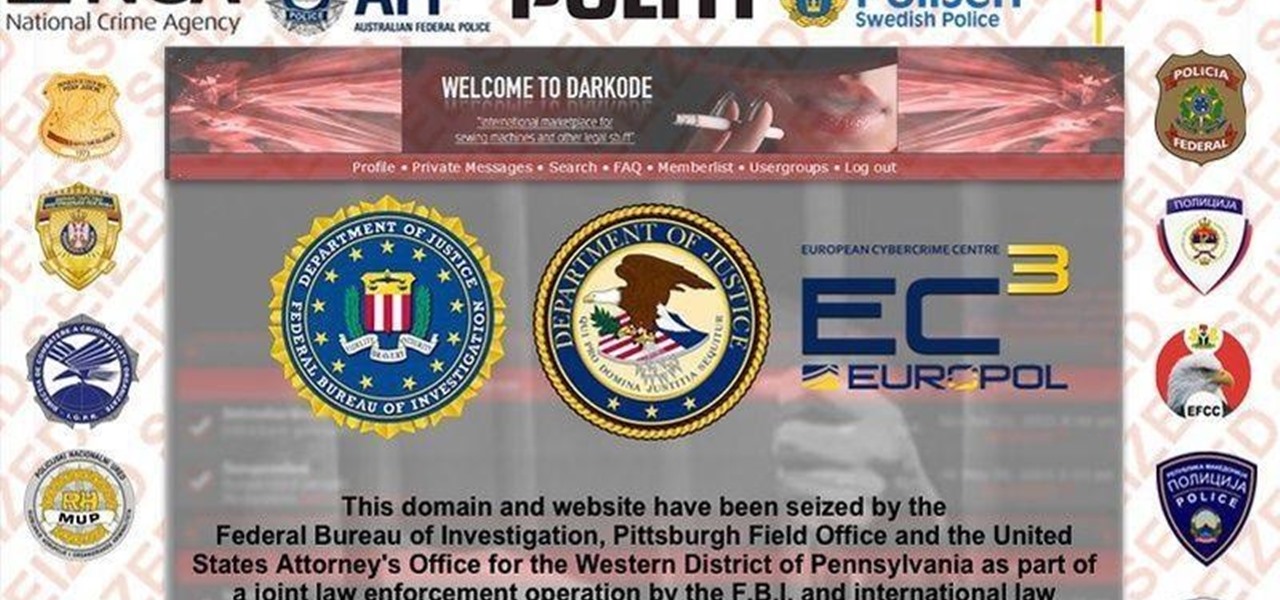
News: FBI Shuts Down One of the Biggest Hacking Forums
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...

News: Airline Offers Frequent Flyer Miles to Hackers
One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

News: 20 Things to Do with Kali Linux After Installation
Okay, so first off, I absolutely did not, any any way shape or from, take part in the writing of this article, but I really think that this will be helpful to all of us Kali users. Here is the article made by blackMORE Ops: 20 things to do after installing Kali linux

News: Some of the World's Most Notorious Hackers Got Hacked
This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

News: The Hacking of Blackhat, the Movie
A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...
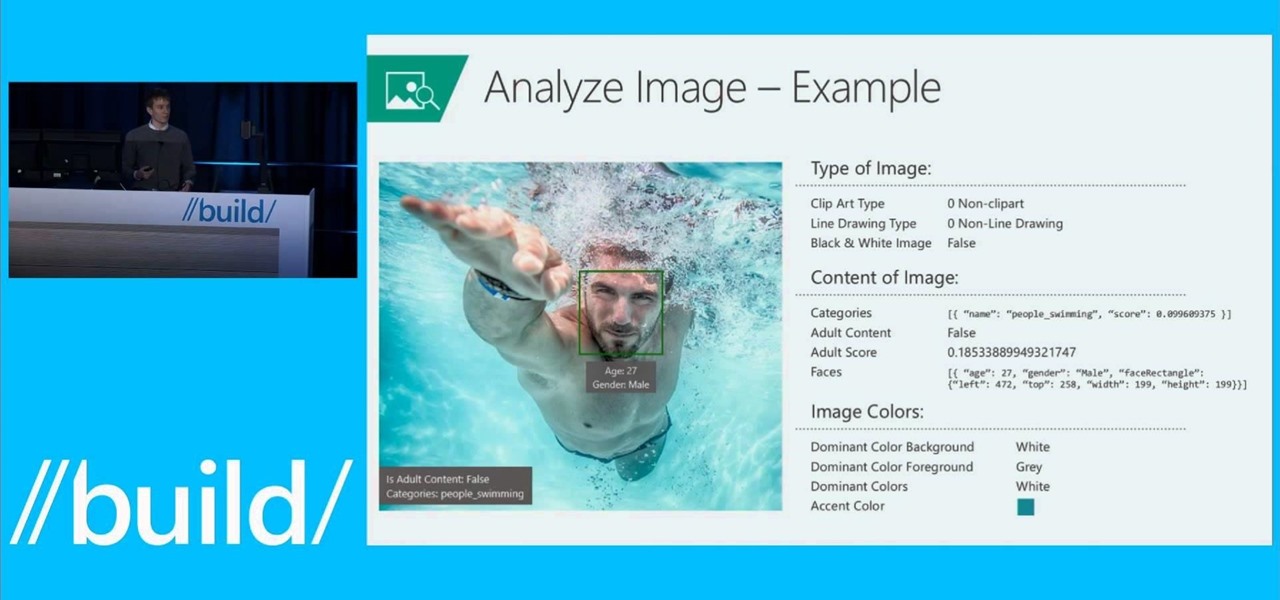
News: Microsoft Project "Oxford"
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)
News: Many Lookup Engines
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.
News: Samsung Keyboard Vulnerability Exposes 600M Mobile Devices!
Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

News: CodinGame (Games for Programmers)
Hi there, nullbytes! Lately I've seen many people posting their codes for many purposes (I've saved most for later use and exploration), and it struck me that maybe some of you find CodinGame fun. Personally, I do, but I couldn't got too far in their games. Still, I find it pretty satisfying when my code finally does what I wanted it to.

News: Funniest Hacks in History
Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...

News: Who Invented the Internet? And Why?
I saw a video that Kurz Gesagt made about the Fermi Paradox, and I liked how the video was made, so I looked up what else they had, and came across this:

News: Chinese Hack of U.S. Employment Records Reveals the Weakness of Signature-Based Defense Systems
With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

News: How to Hack Time
Watched a great guide on hacking things through time by the most powerful hacker on the planet, Hackerman.

News: Hacking SCADA
Welcome back, my hacker novitiates!







