Everything Else


How To: Shellcoding Tutorial, Linux x86 Part 1
Alright, since I notcied this article was too advanced for some users, ive decided to revision this!
How To: Fix Kali 2016 Repository/Mirror Error
Recently, I decided to install Kali 2016 as dual boot on my laptop. Everything install perfectly up until the installer gave me the option to set up the package distribution mirror. No matter what setting I provided, no mirror would set up correctly. I was forced to continue the install without setting up the mirror. If you do not know what this means, I will explain it. Basically, you will not be able to update or install any tools onto your Kali distribution.

How To: Setup Practice Ctf's from Vulnhub on Kali Linux
Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,

How To: Bypass Windows Passwords Part 2
This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I'll test all the ways on Windows 10 and Windows 8/8.1.

How To: Place a Virus in a Word Document for Mac OS X
This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

How To: OSX VM Image Install Guide
I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

How To: Bypass Windows Passwords Part 1
This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

How To: Hack Windows Administrator Password with Out SAM
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

Batch Basics: Understanding the Windows Command Line, Part 1 (Echo and Variables)
Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

Networking Foundations: Subnetting Based on Host Requirements
Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.
Batch Basics: Understanding the Windows Command Line, Part 0 (Introduction)
Welcome, everyone! While Linux distributions are almost always used for exploits, security, pentesting and other stuff covered in Null Byte, knowing the Windows Command Line (or Command Prompt) is a useful skill that can help you in various ways, such as using exploit programs made for Windows or using the command line on someone else's Windows computer.
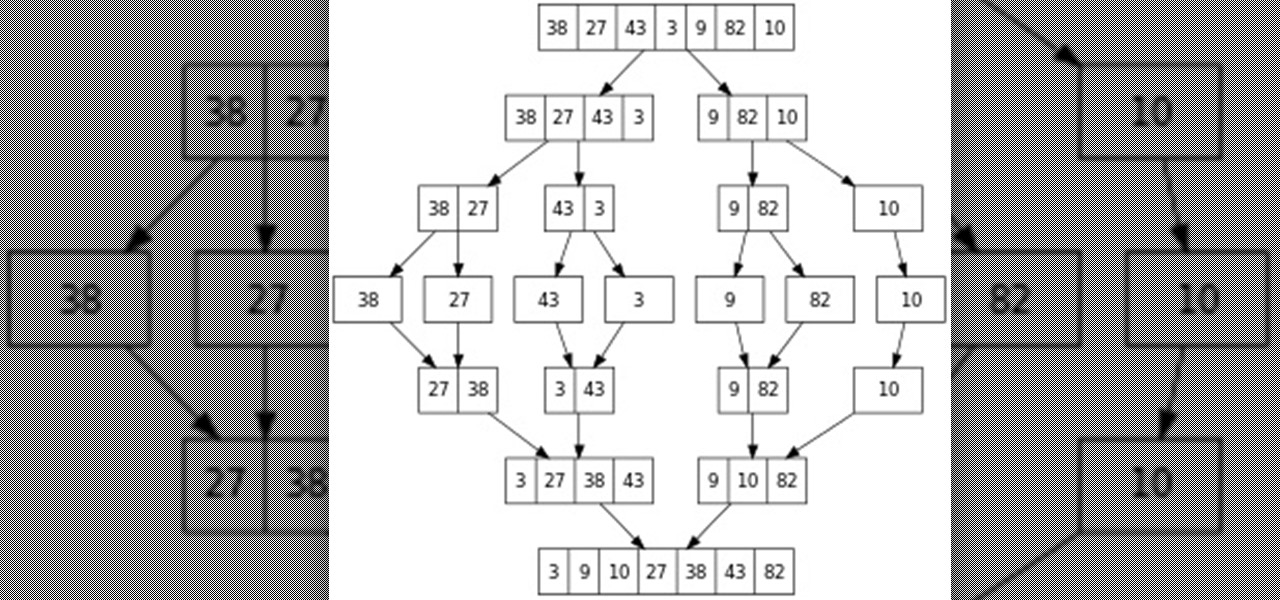
Sorting (Part 7.0): Merge Sort
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!

Networking Foundations: Subnetting Madness
Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

How To: Disable Anti Virus Services After Got Meterpreter Session on Remote PC.
Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

Hack Like a Pro: How to Use PowerSploit, Part 1 (Evading Antivirus Software)
Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Sorting (Part 6.0): Quick Sort [Sorta Efficient]
Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

How To: Build an FTP Password Sniffer with Scapy and Python
Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.
Decrypting [Part 1]: How to Decrypt Caeser Encrypted Texts
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.
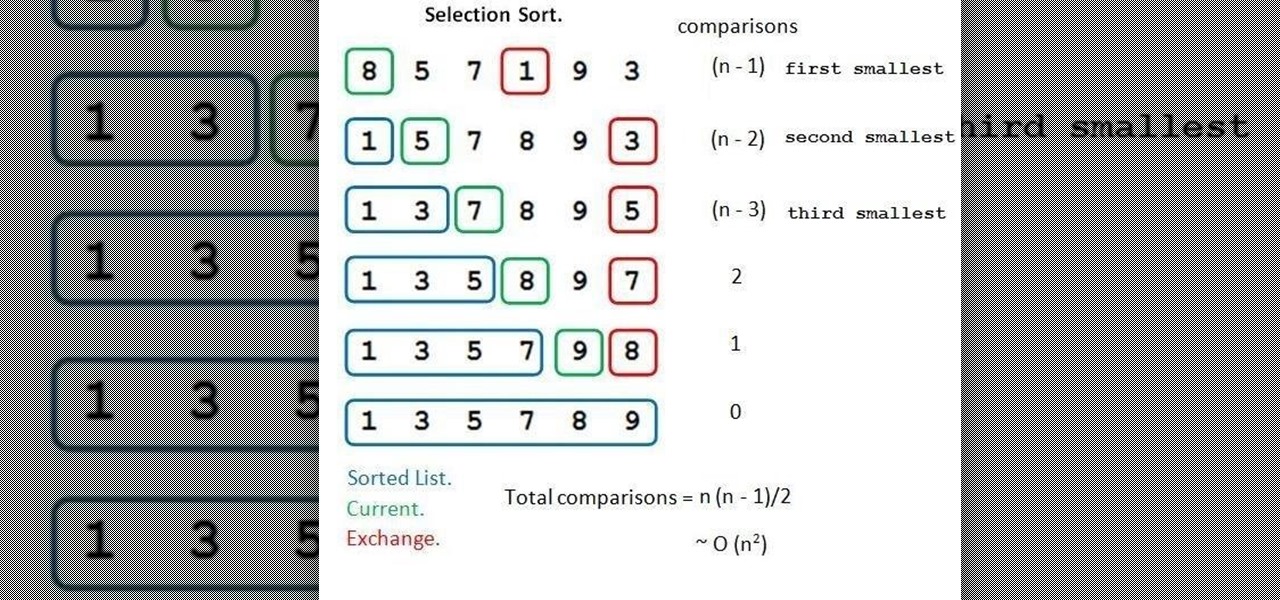
Sorting (Part 5.0): Selection Sort
First and foremost, let me once again apologize for that bug, which I failed to notice in time. Alright, alright... Enough sulking, oaktree. Get to it!

How To: Build Stealth Backdoors
removed!

How To: Reversing and Analyzing a Runtime Crypter
What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

How To: Build a Directory Brute Forcing Tool in Python
While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...
How To: A Simple Udp Flooder Pt 3
in the oncoming tutorials we will post more about forging packets. I originally posted this, but because I found the techniques to be too advanced for this serie, I will post them in a new series which I will be posting in a few months. Sorry guys, but stay tuned!
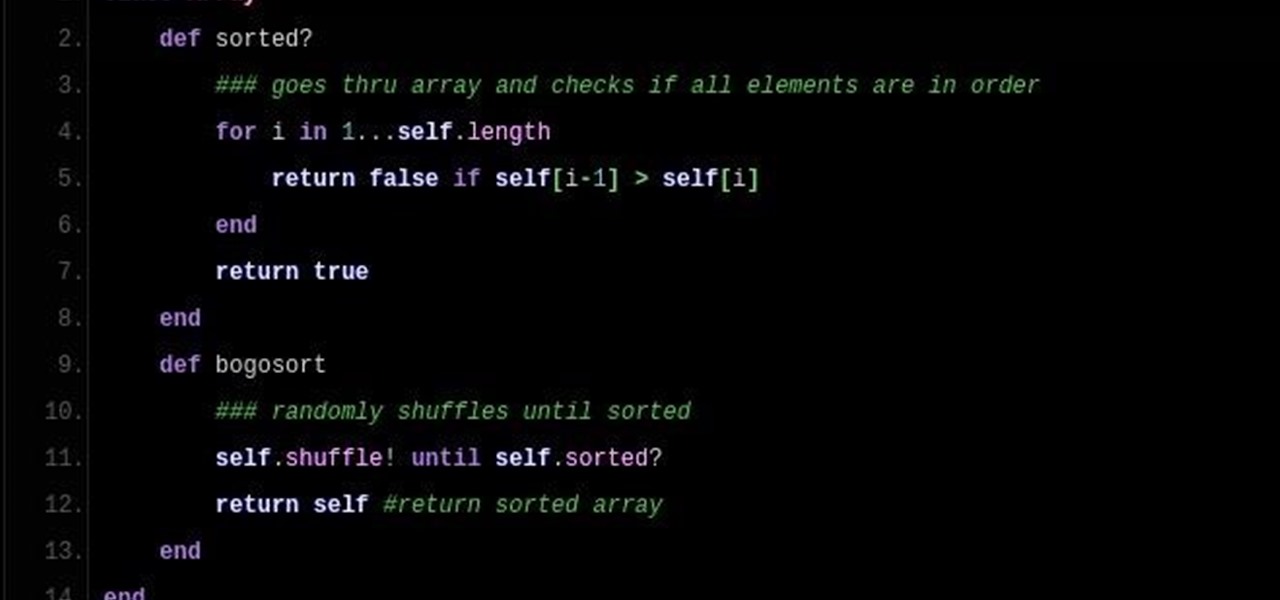
Sorting (Part 4.0): Bogo Sort & Wasting Time
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?
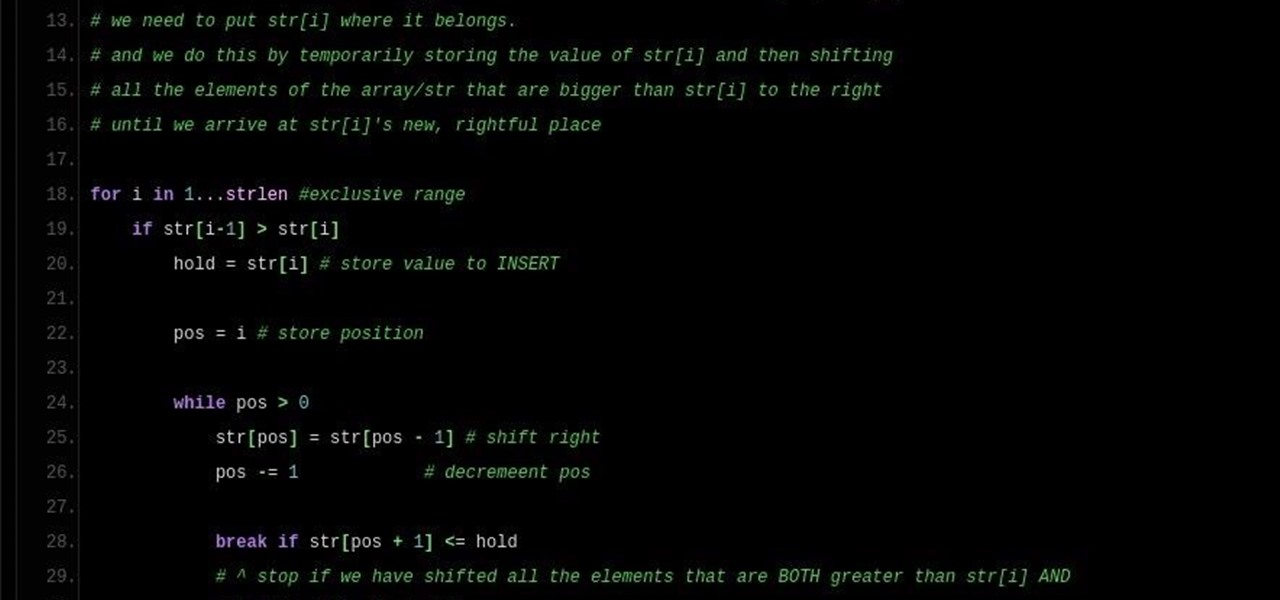
Sorting (Part 3.0): Insertion Sort
Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here.

How To: part1-1:How to Crack a Account or Vps?(Find Proxy List by ProxyFinderEnterprise)
proxyFinderEnterprise is a tools for find proxylist . in this topic you learn how to use this tools for find a proxy list .

How To: Facebook Credentials Revisited
Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.
How To: Bypass Facebook's HSTS
Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

Sorting (Part 2.0): A Tangent to Time Complexity
Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.

How to Java: E6 (While Loops)
I'm back! We're learning Java WhileLoops today.

Sorting (Part 1.0): Bubble Sort
Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

PHP for Hackers: Part 1, Introduction and Setting Up
In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

How To: Write into Another Processes Memory with C++.
Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

How To: Use Your Android as a Hacking Platform:Part 1 Getting Your Android Ready.
Hey guys I am starting this Series because I thought there was a lack of post about Hacking from Android.

Networking Foundations: Exploring UDP via Wireshark(Part 2)
Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

How To: Introduction to the C.H.I.P by Next Thing Co - IoT Hacking Device?
Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Networking Foundations: Exploring UDP via Wireshark(Part 1)
Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

How To: Gathering Sensitive Information: Scouting Media Profiles for Target Information
Here I will show you how to properly dig information on the web that has already been published, you just dont know it.







