
How To: Build a Really Small Hacking
removed!


removed!

If you're looking to train yourself, and see how good at hacking you really are, I'd recommend Hack This Site. You've most likely already heard of it, but it's super fun to use and is also safe. You learn a lot, too, and there's no tutorials or anything. What you do is you pick a challenge and then it gives you a little scenario. For example I started the basic challenges about 10 minutes ago and am on challenge six, it asks for a password and you scramble through the code, editing bits and b...

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

Lock picking is defined by locksmiths as "the art of opening a lock without the key". There's many ways to accomplish this, but I'm specifically interested in using a lock pick set. Since locks vary in shapes and size, it's better to stick with just one kind of lock at first. Most locks are based on fairly similar concepts, so sharing methods across locks is possible.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...
Hi everyone! This is my first How To. Before we start you need to have a Facebook account (of course) and...this only works with your Facebook friends (so if you're looking for someone's mail on Facebook but you're not friends this won't work)

Hello again my fellow hackers. I've come to give you some hope for hacking. As we know there are a lot of exploits out in the world and there are websites you can find them on.

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer installed already. If you are young and just starting out, this may be hard for you to manage with your current salary. If you have no washer and dryer, the only alternative is the laundromat.
The days of entering left, right, left, right, up, down, up, down, a, b to cheat your way through a video game are long gone. With achievements and trophies in existence, game developers have, for the most part, removed cheats from video games.

With the rather large success of the Community Byte activities, both programming and HackThisSite, I have decided to continue to do both activities every session! With that said, when programming sessions occur, they will be lead by Sol Gates in Gobby. Also, the programming mission will no longer be to code a tool, we have changed it to be even more "noob friendly". This means that instead of coding a tool, you will be walked through puzzles and challenges that must be solved by coding a scri...
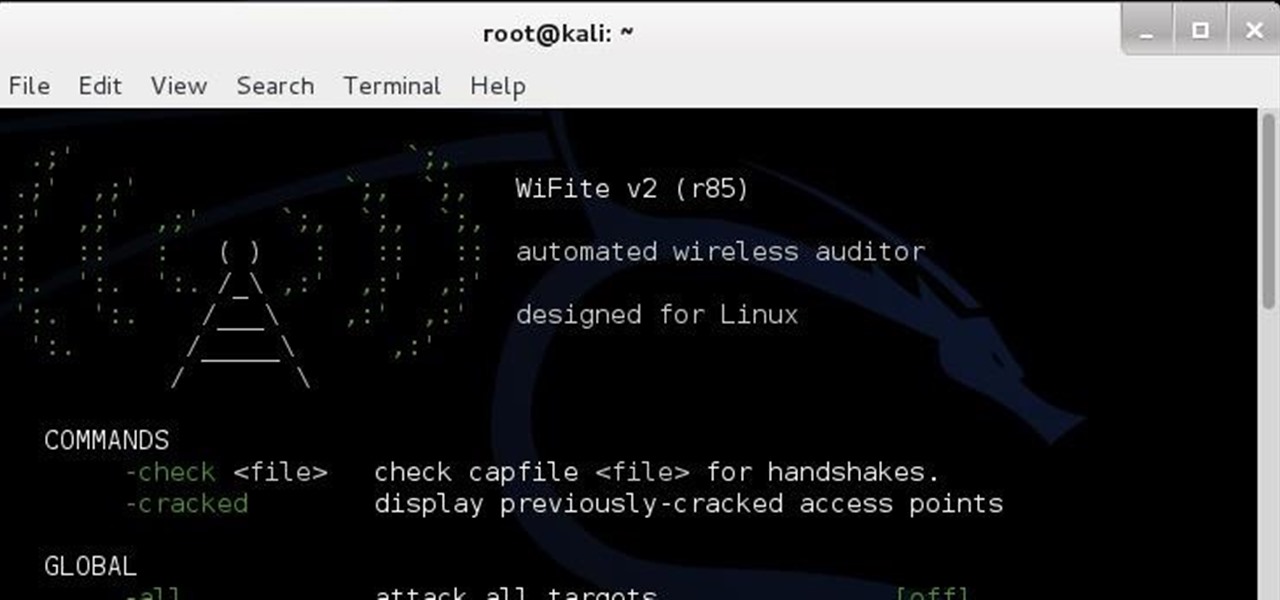
Welcome, my aspiring hackers! In this tutorial I'm gonna be showing you how to hack Wi-Fi using the wps compatibility of a router, in , of course, Kali. First, fire up Kali.
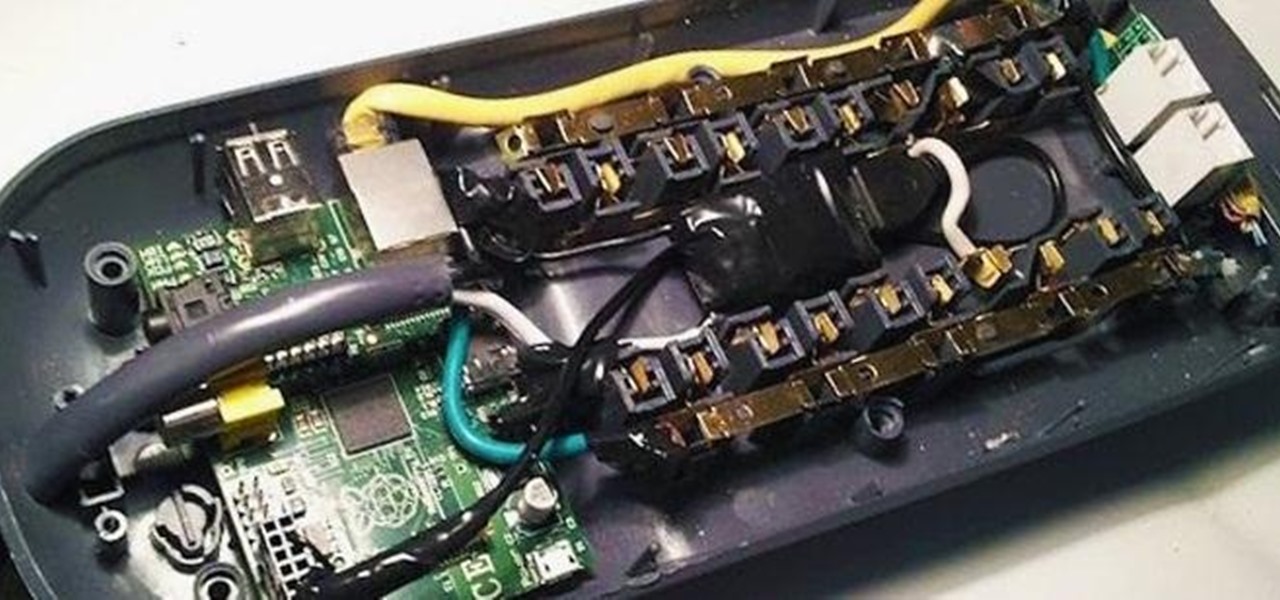
Remember the Power Pwn, the clever little hacking tool disguised as a power strip? It's great in theory, but with a $1,295 price tag, it definitely doesn't fit into most people's budgets.

If there ever was a time for Null Byte to need people to contribute, it's now. Let's make Null Byte a place where anyone, from novice to master computer user, come and learn. It has been sometime since the last "Call to Arms" for Null Byte, and even longer since the last "Weekend Homework". We all know that this time of year is busy for everyone, but that didn't stop occupytheweb otw from creating a great article in his continuing "Hack Like a Pro" series.

Anonymous hacktivists announced via Twitter that they had successfully hacked the website of New York Iron Works, a police-equipment supplier, and replaced the homepage with a tribute of love to arrested hacker and Chicagoan Jeremy Hammond.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...
i am stone taker and currently pursing b.sc computer science. i am from Africa.i want to to master become know programming very well especially c++;

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

Gamers like myself who have switched back and forth between Skyrim on PC and Xbox lack the ability to share game saves. This really sucks. I love playing Skyrim on a console. It's a very comfortable, easy and relaxed gaming experience. You don't have to worry about your frame rate being optimized, or wrist pains from using a keyboard. However, gaming on the PC can allow you to use texture enhancing mods and get an overall smoother experience due to a lack in glitches and bugs that plague the ...

Welcome to another Community Byte announcement from Null Byte! The goal of the Community Bytes is to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you, so that is exactly what we do! In our sessions, we have started to both code and complete HTS missions. This means that there is something for everyone here, so make sure you join us.

Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at HackThisSite one-by-one each week, starting with the basic missions.

Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen.

This Null Byte is a doozey.

Do you need proxy access, but cannot have it for some reason? The most common perpetrator behind the issue is the network you're trying to access the pages from. Some networks will block websites, then go as far as filtering out all of the web queries for terms like "proxy" because it can get around their filter. Quick web proxies can be used for tons of other things, though.

Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about posting peaceful poetry.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Pygame! And what you can accomplish with it. Another python article... (Blame Alex for getting me hooked on yet another coding language...)

Lots of people are going to be getting the latest iOS devices this holiday season. But what good is a portable device if you don't hack it? Jailbreaking on the latest stock iOS, version 4.3.5, is a bit of a trivial endeavor. Not many people know how to downgrade from this firmware to a firmware that can be jailbroken (pre-iOS 5). If you want the added functionality and the complete control over your device that comes with jailbreaking, then read on.
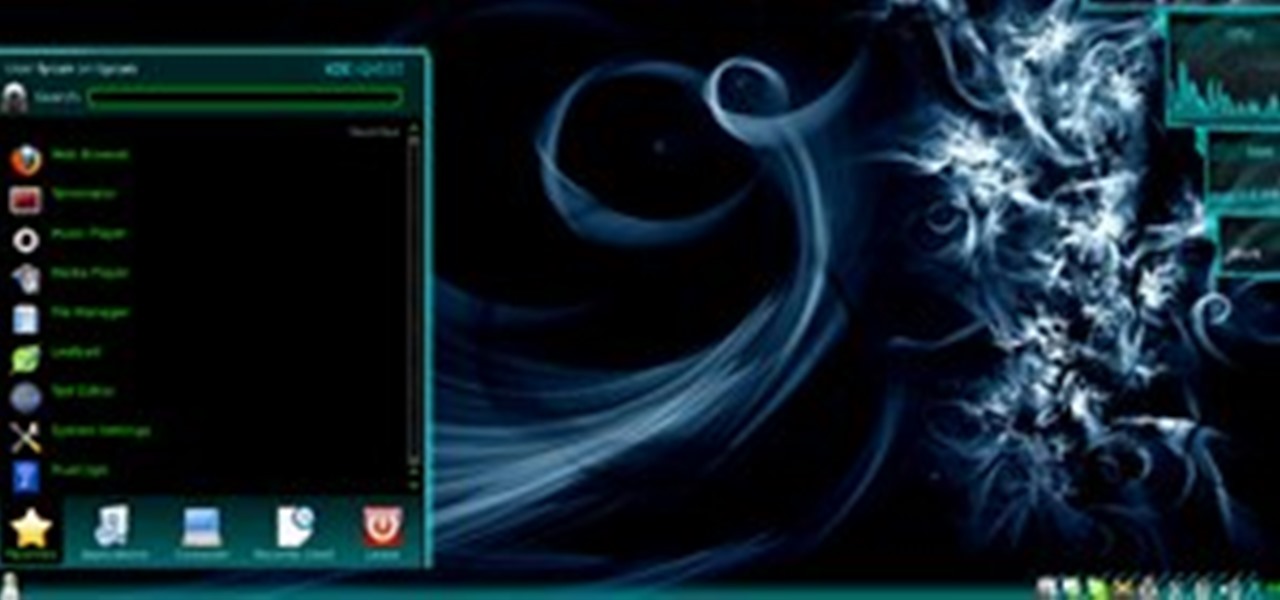
Linux can have the most beautiful interface in the world, because it is simply what you make of it. You can change every little detail with relative ease because that's what Linux is all about: Freedom and OpenSource.

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...