Null Byte Features


How To: Hack Your Neighbor with a Post-It Note, Part 2 (Setting Up the Attack)
In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

How To: The Penny Pinchers Guide to Eating Cost Effectively Without Relying on Ramen
If you're on a tight budget for food, whether you're in college, or someone just starting out living on their own, you're probably low on money and sick of ramen noodles. Don't get me wrong, ramen can be tasty and filling, and there is almost nothing cheaper.

Hack Like a Pro: An Introduction to Regular Expressions (Regex)
Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Hacking Windows 10: How to Turn Compromised Windows PCs into Web Proxies
A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

How To: Links to Help You Hacking
This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

Listen In: Live Social Engineering Phone Calls with Professional Social Engineers (Week 2)
Last week's social engineering phone calls were a blast. We made some friends, and even some enemies. We scored cheap food for some buddies, made some phone bills disappear, and even got a few people some free pizzas. So overall, it was a very successful night. In light of its success, I figured we'd all do another one!

How To: Program Your Own Little RAT (Part 2) Getting the Client Working
OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Root Exploit: Memodipper Gets You Root Access to Systems Running Linux Kernel 2.6.39+
Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the
How To: Hack Windows Administrator Password with Out SAM
Hi, I am Robel, I am here to let you know about how to hack windows admin password with out Sam files, this requires physical access and any boot operating system...I used Kali 1.8 , if it doesn't work make sure you have shuted it down properlyor use backtrack.

News: Advanced Cracking Techniques, Part 2: Intelligent Bruteforcing
Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

How To: Keeping Your Hacking Identity Secret - #2
My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

How To: Encrypt Your Notes, Photos & Archives with EncryptPad
For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.
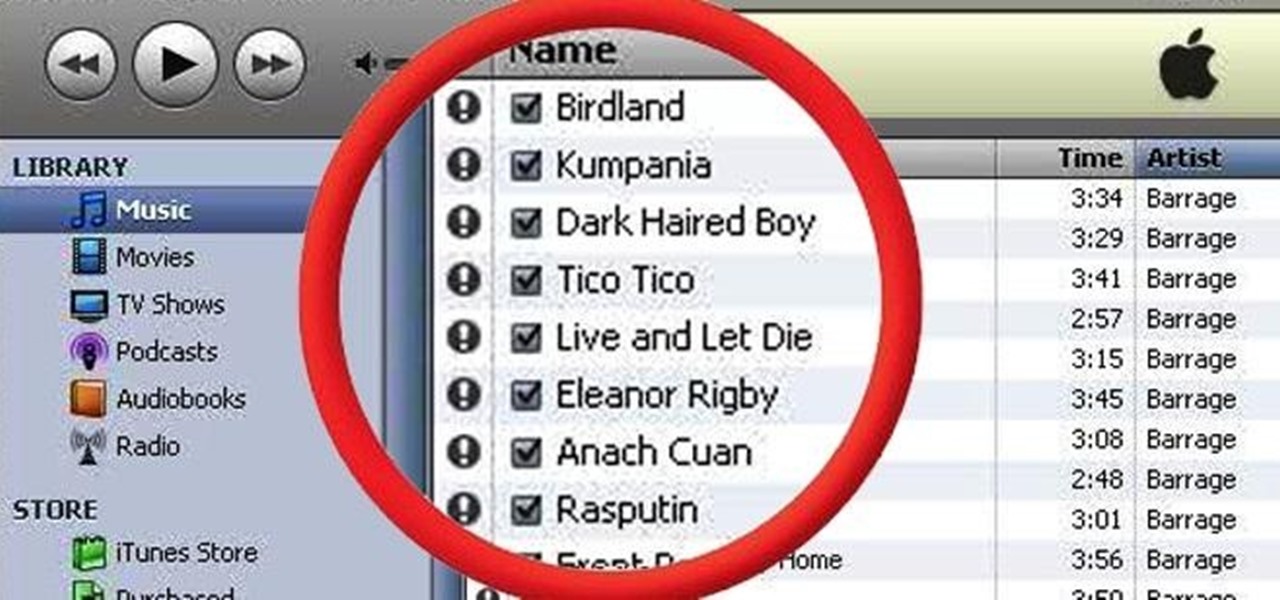
How To: Clear Dead Tracks from Your iTunes Library on Windows Using Only Notepad
If you've ever mistakenly moved your music files around without relinking them in iTunes, you might now be noticing that you have a long list of tracks asking you to relink them. You could go through them one by one, redirect them to the new file location, then delete any copies. Or you could try to track them all down and delete the old references. But come on, who wants to spend that much time when you can clean up your library using this clever method using only Notepad on your Windows com...

How to Meterpreter: Interactive Ruby Shell (A Quick Introduction)
First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

How To: Make a Trojan Appear Legitimate
So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

How To: Quickly Look Up the Valid Subdomains for Any Website
Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

How To: Security-Oriented C Tutorial 0x14 - Format String Vulnerability Part I: Buffer Overflow's Nasty Little Brother
What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Hacking macOS: How to Bypass the LuLu Firewall with Google Chrome Dependencies
Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Zanti: Nmap
In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

WANTED: Hackers for Bug Bounties
In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.
How To: Advanced Penetration Testing - Part 1 (Introduction)
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

How To: Bypass Windows Passwords Part 2
This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I'll test all the ways on Windows 10 and Windows 8/8.1.
News: Many Lookup Engines
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Hack Like a Pro: Capturing Zero-Day Exploits in the Wild with a Dionaea Honeypot, Part 2 (Configuration)
Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.
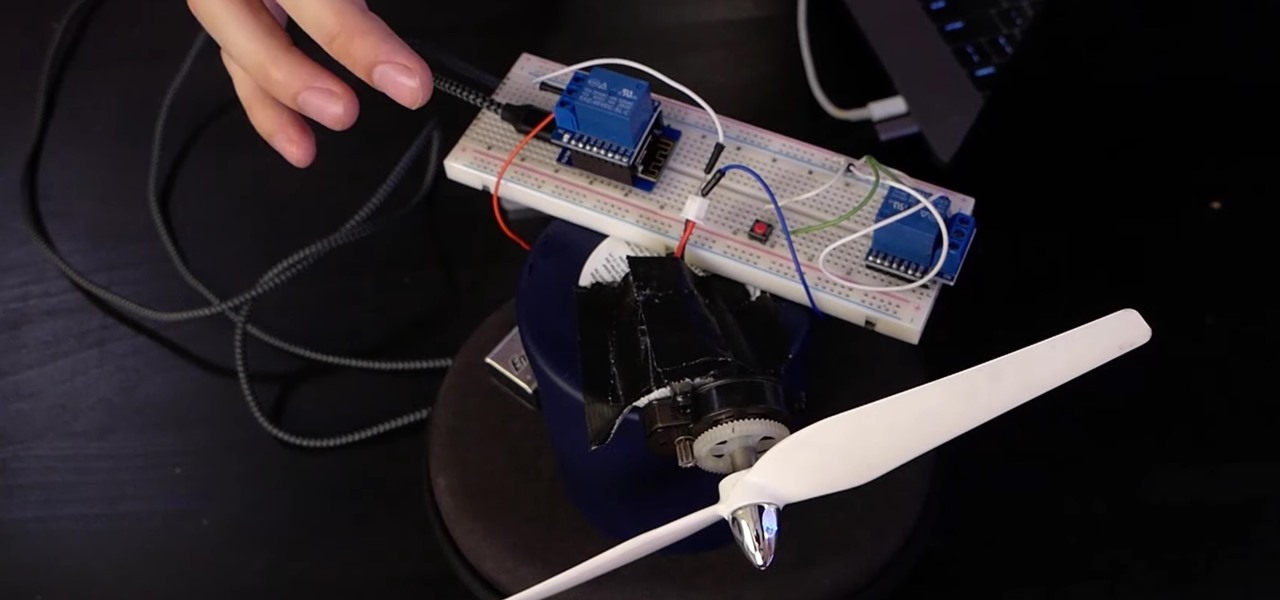
How To: Control Electronics from a Browser Using MicroPython in Jupyter Notebook
If you want to control electronic devices, such as a relay or motor, you can do so using MicroPython with an ESP8266 and web browser. Usually, you'd program an ESP8266 using Arduino, but C++, which Arduino uses, is not always the easiest programming language for beginners to learn.

Hacking macOS: How to Spread Trojans & Pivot to Other Mac Computers
It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

How To: Abuse Session Management with OWASP ZAP
It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

IRC Guide: Making a Bot
Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.
Decrypting [Part 1]: How to Decrypt Caeser Encrypted Texts
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

News: 9 Notorious Hackers
I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

TypoGuy Explaining Anonymity: Who Is Anonymous?
Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

How To: Using BASH for Computer Forensics
Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.
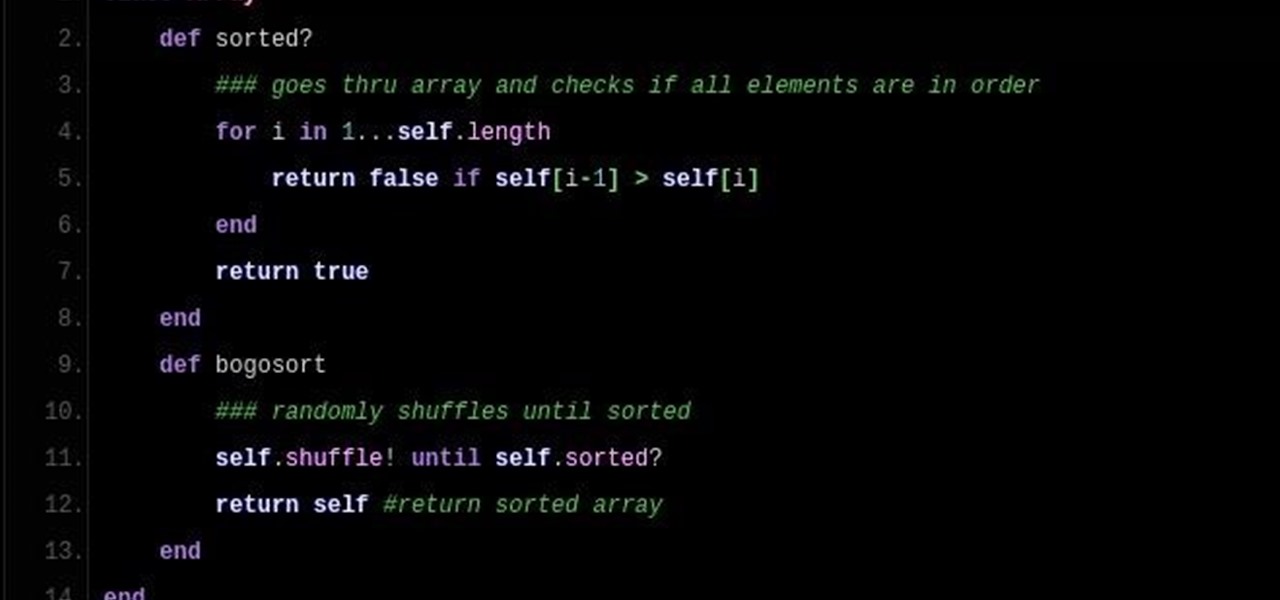
Sorting (Part 4.0): Bogo Sort & Wasting Time
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

How To: RootKits 101 (I). The Basics
removed!

Hugging the Web (Part 1: Introduction)
Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

How To: Security-Oriented C Tutorial 0x12 - Scope
What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

How To: Security-Oriented C Tutorial 0x03 - Bits, Bytes, Broken?
Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

News: Tux the Origami Penguin
Tux the Linux penguin, made from origami sonobe units. Can anybody figure out how to assemble?

How To: Learn How to Play the Market with This Data-Driven Trading Bundle
If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

News: Capture the Flag, Round 1
As many of you know, Standard User proposed that we start a Capture the Flag (CTF) competition. I think this is a great idea! Standard User proposed to set up the server and the flags for this first competition. Since Standard User was new to our community, I asked him to postpone the start of this competition until I had a chance to make certain that this was safe and legitimate for our community. I have good news! With the help of Phoenix750, we have done the necessary due diligence and we ...







