Null Byte Features


News: 'Impossible to Identify' Website Phishing Attack Leaves Chrome & Firefox Users Vulnerable (But You Can Prevent It)
Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

Listen In: Live Social Engineering Phone Calls with Professional Social Engineers (Final Session)
We had a blast during last week's social engineering calls. One of our attending social engineers was so clever that she convinced several people on Craigslist that lost items were hers, even if it seemed she couldn't be trusted. But females are better social engineers, naturally. Some say that females have a special knack for manipulating men, but I think that's preposterous. I can't see why that would be true in a million years (note my sarcasm).

Coding Basics: A Guide to Choosing Your Optimal Text Editor or IDE
When you first become interested in learning how to program, it can be difficult to find a place to start. A lot of questions come up, especially if you're new to the idea of programming entirely. After you pick which language you want to learn, you have to worry about how you're going to write the language.

News: Can We Hack the Hackers?
Welcome back, my rookie hackers!
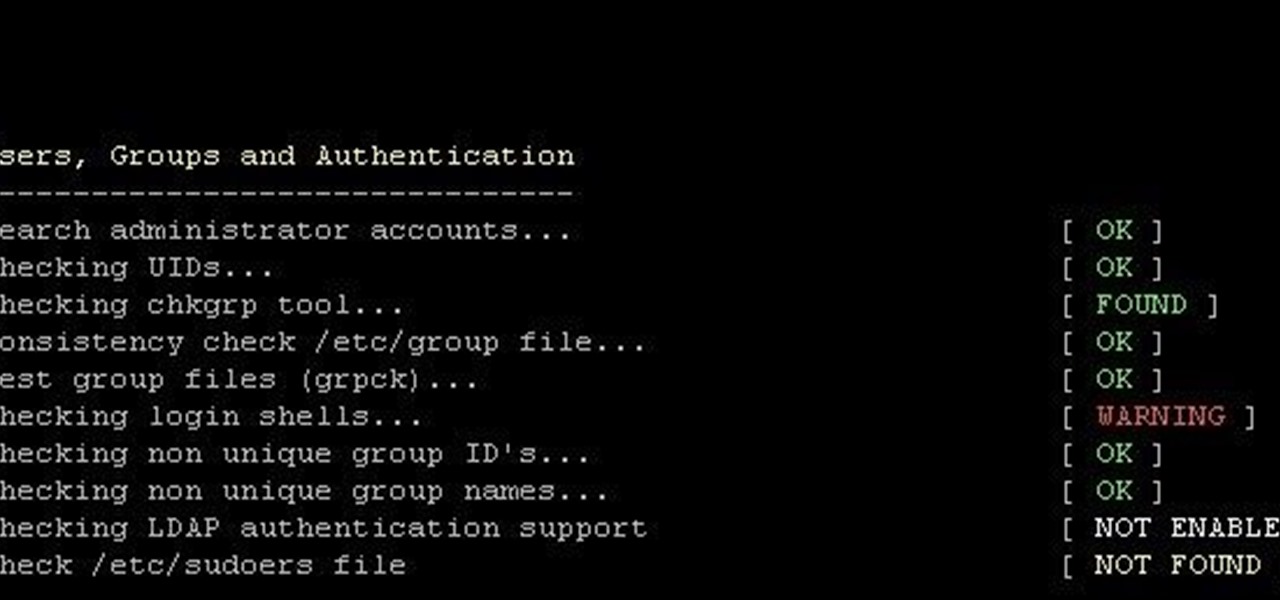
How To: Find Your Computer's Vulnerability Using Lynis
This is finding some of your vulnerability using Lynis. This tool Lynis is used on Unix and Linux type operating systems (sorry windows). So lets get started

How To: Punchabunch Just Made SSH Local Forwarding Stupid Easy
SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.
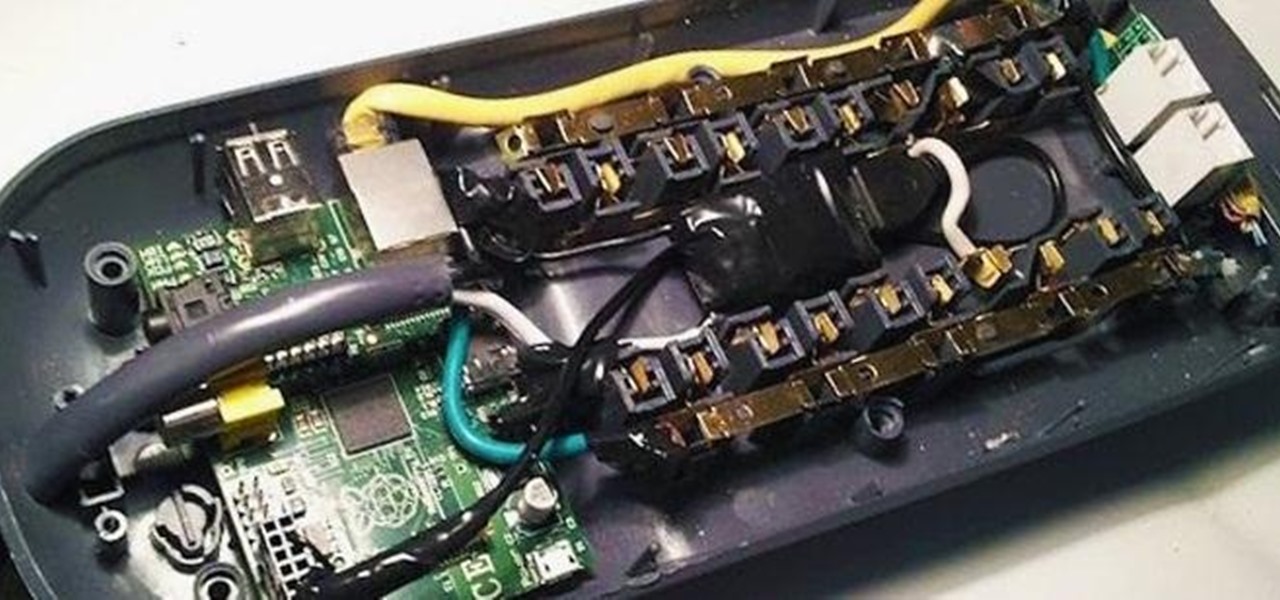
How To: Turn an Ordinary Surge Protector into a Sneaky Hacking Strip
Remember the Power Pwn, the clever little hacking tool disguised as a power strip? It's great in theory, but with a $1,295 price tag, it definitely doesn't fit into most people's budgets.
Hack Like an Elite: Batch Scripting for Malicious Purposes: PART 2 (Some More but Interesting Basics)
And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

How To: Install Linux to a Thumb Drive
Let's face it, CDs and DVDs are a thing of the past. We no longer use them as a storage medium because they are slow, prone to failure in burning, and non-reusable. The future is flash memory. Flash memory is cheap, fast, and efficient. Eventually, flash drives might even replace discs as the preferred prerecorded selling format for movies.

How To: The Easy Way to Use PGP for Encrypting Emails on Windows, Mac & Linux
In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

Uncrackable File Sharing: Securely Transfer Your Secrets with 4096-Bit Encryption
Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

How To: Hack WPA/WPA2-Enterprise Part 2
In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

Hacking macOS: How to Sniff Passwords on a Mac in Real Time, Part 2 (Packet Analysis)
Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

How To: This LastPass Phishing Hack Can Steal All Your Passwords—Here's How to Prevent It
If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

How to Train Your Python: Part 3, Basic String Manipulation
Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

How To: Increase TX-Power in Kali 2.0
Hello, *Note This is my first how to post on here, so please correct anything that I have missed and let me know if anything I explained is unclear and I will try to clearify. Also I am a NOOB when it comes to this art, so I might have missed something, if so please inform me so I can better myself*

News: Why YOU Should Study Digital Forensics
As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Community Byte: HackThisSite, Realistic 4 - Real Hacking Simulations
We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

Advice from a Real Hacker: Why I'm Skeptical That North Korea Hacked Sony
Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

How To: Here's Why You Need to Add Python to Your Hacking & Programming Arsenal
Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

News: My Review on Kali 2.0
Hello guys, its been quite a while since my last post. (sorry for the lack of images)

How To: Abuse Vulnerable Sudo Versions to Get Root
Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

SPLOIT: How to Strip Off MetaData in Images Using Python
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

How To: The Difference Between Http and Https
With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS
How To: Beginners x86 Linux Assembly
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

How To: Attack on Stack [Part 1]; Smash the Stack Visualization: Introduction to Memory, Registers and Assembly.
Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

How To: Use BeEF and JavaScript for Reconnaissance
Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.
How To: Advanced Penetration Testing - Part 1 (Introduction)
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

News: And the Winner of the White Hat Award for Technical Excellence Is...
It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

News: Anonymous vs ISIS
As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.
How To: Make a Secret Language with Python
Sometimes our information important. So important that we have to encode it to keep it away from criminals. What better way to encode information than to make our own encoder with Python?

HIOB: The Ruby Programming Language, Part 1: (Building an FTP Cracker)
Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

News: Art Meets Information Liberation with the Transparency Grenade
Julian Oliver created the Transparency Grenade in January 2012 for the Studio Weise7 exhibition at Labor 8. It's a transparent device with a "payload" built from an ARM Chip, an Arduino Nano, a mic, and a strong Wi-Fi antenna. It taps into wireless networks and logs emails, webpages, images, and voice to a publicly available online map showing its "detonation" location. Apparently, development for an Android version (sans the pretty plastic shell) is under way thanks to interested donors. See...
Security Tube: Useful Video Tutorials for IT Security.
Hi everyone. I'm relatively new here and I have learned a great deal from many of you already and would like to try and give a little something in return.

News: Shadow Brokers Leak Reveals NSA Compromised SWIFT
The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

News: A Brief History of Hacking
Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Weekend Homework: How to Become a Null Byte Contributor (3/2/2012)
Last week, we had a great contribution from Christopher Voute, who introduced us all on some of the basic moves in Python. Now, who else will share their knowledge and tackle some of the topics below?

How To: Security-Oriented C Tutorial 0xF8 - PE File Infection
How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!
News: What Are the Motivation Things You Do or Read to Become a Hacker?
I usually read hackers manifesto. :)

Power Pwn: A Stealthy New Hack Tool Disguised as an Innocent Power Strip
The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...







