Null Byte News


News: What the Heck Was Stuxnet!?
As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

News: Is Cyber-Warfare Really That Scary?
A post about Cyber war from BBC, want to share. http://www.bbc.com/news/world-32534923

News: White House Hacked by Russian Hackers!
Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Cyberwar: Hacker vs. Hacker
From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

News: Why Is Linux & Other Open-Source Software Free?
Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

News: The Hack of the Century!
Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

News: Finding the Exploits Out in the World (For Beginner Hackers)
Hello again my fellow hackers. I've come to give you some hope for hacking. As we know there are a lot of exploits out in the world and there are websites you can find them on.

News: How Zero-Day Exploits Are Bought & Sold
Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

News: What to Expect from Null Byte in 2015
Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

News: It Would Appear from This Piece of News That We Can All Just Pack in Now and Call It a Day.
Startup promises to catch 100% of network attacks - Techworld.com.

WANTED: Hackers for Bug Bounties
In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

News: An interesting lecture on password psychology.
Lorrie Faith Cranor: What’s wrong with your pa$$w0rd? | Talk Video | TED.com.

News: Is FireChat the Future of the Internet?
As you already know, Hong Hong has been rocked in recent weeks by protests against their Beijing overlords. Promised free and fair elections, Beijing has reneged on this promise and is now telling Hong Kongians (that's what they're called, aren't they?) that they will only be able to vote on Beijing-selected candidates. All that is interesting from a political perspective, but from a technological perspective, the more intriguing story is how the protesters are communicating. Faced with their...

News: Hackers Have 92% Success Rate Hacking Gmail on Android
Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.
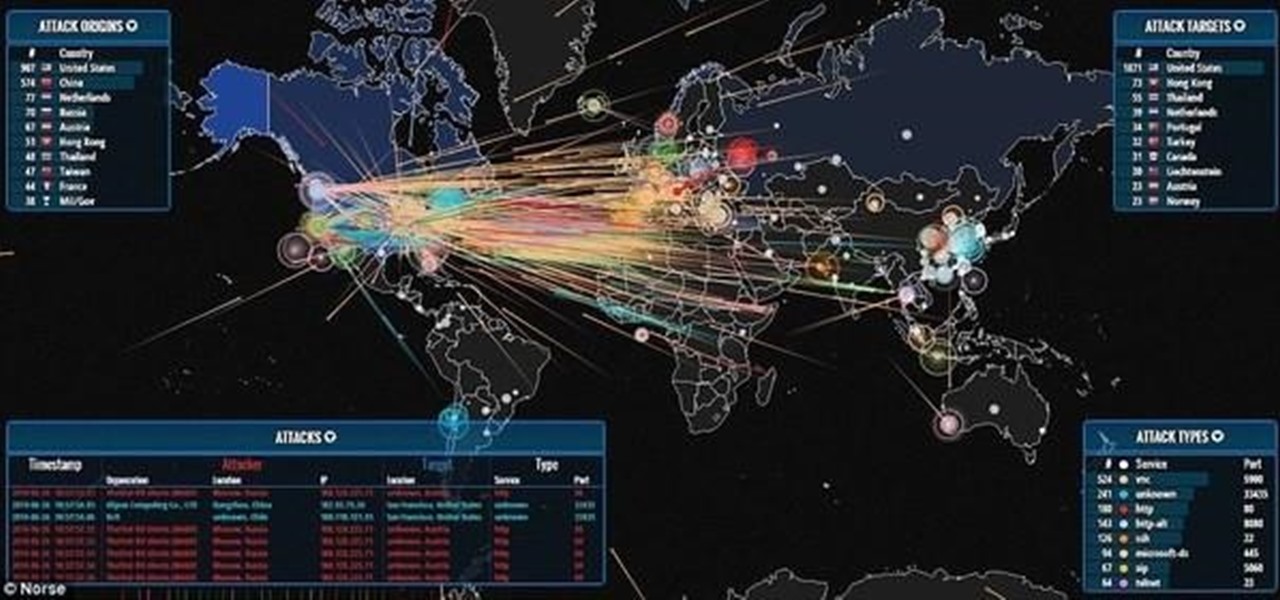
News: View a Live DDoS Map
This is a live map feed to current DDoS Attacks globally. Live DDoS MAP Thought I would post this to give you an idea of the size and scope of DDoS Attacks at any given moment. Plus it looks k00l.

Linux: Where Do I Start?
Greetings, my friend. Welcome to Null Byte. I am Dr. Crashdump. Linux will be talked about a lot in Null Byte. It's used in most tutorials on this site, actually. You should learn how to use Linux as soon as possible, but where do you start? No worries. Let's figure that out.

Social Engineering: The Basics
I felt our community would benefit from this article. Social engineering is a big part of what we do, so it's something you should all become familiar with.

News: Reasons Why You Should Root Your Android Device
First off, Rooting Your Device voids the warranty on the device. If you want to root your device but are afraid of "bricking" said device, rooting it may not be good for you.
News: Use Decentralized Cloud Storage to Keep the NSA from Tracking You
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

News: Best Hacking Software
When i went to class today, a good friend asked me a question. He wanted to know what the best hacking software was to basically do everything. What i told him was this: Well there isn't an "Ultimate" tool boot there are a number of tools which deserve a "Medal." So what i'm trying to say here... What are some of the best hacking tools available right now? For starters i created a list with some of the tools.
News: What Do You Want to See?
I've decided I've not been writing enough and want to get back into writing more often. I have a few ideas for articles based on password cracking and breaking into Windows, and a basic general coding type of articles, but I wanted to know if anyone had anything they wanted to know how to do, a language they wanted to learn the basics of or something like that. Please comment with any ideas.

News: Flawed Laptop Fingerprint Readers Make Your Windows Password Vulnerable to Hackers
Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

News: Hacker Points Out iOS Security Flaw That Allows iPhone Text Spoofing
Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

News: Hackers Can Remotely Set HP Printers on Fire: Is Yours Vulnerable?
Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,000, researchers Salvatore Stolfo and Ang Cui were able to hack into the printers using remote firmware to install malware, and in some cases even cause the printer to catch on fire. The main issue is with the printer's c...

Power Pwn: A Stealthy New Hack Tool Disguised as an Innocent Power Strip
The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

News: Have an NFC-Enable Phone? This Hack Could Hijack It
Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Digital Lock-Picking: This Simple Arduino Hack Opens Millions of Hotel Keycard Doors
It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.
News: Intel Core 2 Duo Remote Exec Exploit in JavaScript
Looks like someone created a remote exploit using javascript. Pretty scary stuff o.o. Intel Core2Duo cpu cache controller bug PoC | Inj3ct0r - exploit database : vulnerability : 0day : shellcode.

News: Interesting Read
Hey guys just found an Interesting article, thought I'd share it. See yourself as the next Assange? Good luck - CNN.com.


News: Basic Math Operations
It was brought up a while back in a Community Call to Arms that *math* is handy for encryption (and let's face it, everything) so let us go over things you just have to know. "In its simplest meaning in mathematics and logic, an operation is an action or procedure which produces a new value from one or more input values."[source]

Windows Security: Software Level
As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end.

Null Byte: Never Let Us Die
If there ever was a time for Null Byte to need people to contribute, it's now. Let's make Null Byte a place where anyone, from novice to master computer user, come and learn. It has been sometime since the last "Call to Arms" for Null Byte, and even longer since the last "Weekend Homework". We all know that this time of year is busy for everyone, but that didn't stop occupytheweb otw from creating a great article in his continuing "Hack Like a Pro" series.
News: found a debit card...
i "found" a debit card that had the sticker on with activating instructions, how can i see if it is activated and if it is not, then how can i activate it and if it is how can i use it with out getting caught...

News: Piratebay - To be blocked in the UK
To those who may not know about this, the UK high court has ruled that all UK based ISP's are to begin blocking Piratebay. This comes in retaliation to Piratebay's action to take down all torrents and provide only magnet links to the pirated content - a move which releases TPB from liability should they be once more accused of hosting the actual content.

News: VMware source code leaked by Anonymous under the banner of The Pirate Bay
@AnonymousIRC released the source code for VMware, mentioning the Pirate Bay.

A Null Byte Call to Arms: Join the Fight Against Ignorance
Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.

Learn Java: Part One
So you want to learn the basics of the fantastic language Java, but you don't want to search the Inter-webs looking for a great tutorial. Well you came to the right place, now may I present to you JAVA.

Editor Picks: The Top 10 Secret Resources Hiding in the Tor Network
We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

News: Packet Capture + Cloud Technology == Awesome
We talk about packet captures often here on Null Byte, but check out this gem. The future of this? what do you all think?







