Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

I have to say, the Xbox 360 controller is the best controller ever created. When I first held it back in 2005, I swore that the dudes working at Microsoft came over and took a molding of my hands because of how great it felt. The thing felt like it was born there.

Archiving and compression is a great way to store and prepare files for sending. You can reduce the size of a file, turn a group of files into a single file, and even encrypt and password the contents! Just take a look at this image to see how much it compressed a 28GB text file.

In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a friend pointed out to me, Ubuntu is currently the only distro implementing SHA-2 as the default. With SHA-2, your passwords take an unreasonably larger amount of time to calculate. This will greatly decrease how many password...

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Tux the Linux penguin, made from origami sonobe units. Can anybody figure out how to assemble?

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Just a little desktop comparison. Post your gorgeous desktops too! Any OS :D.
For those who doesn't want their root password on Kali Linux live USB persistent login to be reset to the default 'toor',

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth internet is actually a better solution in most cases.

With the plethora of programming that we promote at Null Byte, I figured a lot of you newbies that stop by IRC will need a big boost in the right direction to make your dive into programming a lot easier. A hot question that has been thrown around in IRC a lot when making the initial dive is, "How do I write code?". People who do not know much about computers can't understand how code is written. Code that we write here is usually scripted and written in Python, so we will use it as our examp...

Back when I was a Windows user, I know I'm not the only one who has experienced password loss—that moment where you just can't remember your password. Sometimes it happens to the best of us. So, how can we get into the system without paying a local geek or geeksquad to do it? First, we have to look into how Windows stores their passwords.

Sharing a laptop's wireless Internet connection with other computers connected to its Ethernet port is a great skill to know. It can be good for a number of reasons; Your computer may not have proper hardware to have a standard setup, or you may have an awkward network topology where sharing your wireless Internet via Ethernet would just be a better option.

If there ever was a time for Null Byte to need people to contribute, it's now. Let's make Null Byte a place where anyone, from novice to master computer user, come and learn. It has been sometime since the last "Call to Arms" for Null Byte, and even longer since the last "Weekend Homework". We all know that this time of year is busy for everyone, but that didn't stop occupytheweb otw from creating a great article in his continuing "Hack Like a Pro" series.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.

Friday's mission was to accomplish solving HackThisSite, basic mission 7, which required us to learn some basic Unix commands. If you have any prior experience using Unix commands, this should be a breeze for you if you sit and think for a second.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

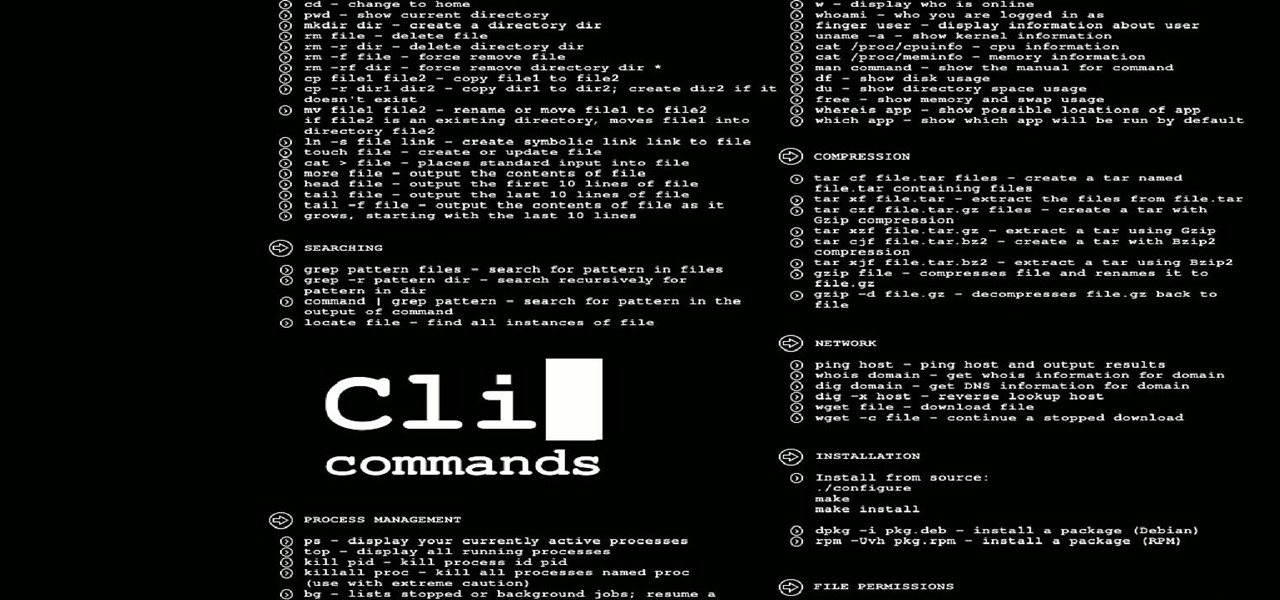
Hello everyone on null byte this is my first tutorial This Tutorial Is on Useful Lesser Known Commands on Linux

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

This Null Byte is a doozey.

As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I am transitioning from C#.

Last week, we had a great contribution from Christopher Voute, who introduced us all on some of the basic moves in Python. Now, who else will share their knowledge and tackle some of the topics below?

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Pygame! And what you can accomplish with it. Another python article... (Blame Alex for getting me hooked on yet another coding language...)

We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials...

We're officially seeking Null Byters interested in teaching others! Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job meant for anyone with the will to share knowledge. There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, and anything you feel like...

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out, such as Gears of War 3 and Dead Island, to name a few.

GRUB, or the GRand Unified Bootloader, is a program that installs to your Master Boot Record and controls what operating system you load at boot time. Normally, it is used for multi-boot systems. Multi-boots allow you to switch between operating systems installed on seperate drives, or partitions at boot time. Linux actually uses it as its default bootloader, even without multiple operating systems.

Alright, since I notcied this article was too advanced for some users, ive decided to revision this!

Welcome, everyone! While Linux distributions are almost always used for exploits, security, pentesting and other stuff covered in Null Byte, knowing the Windows Command Line (or Command Prompt) is a useful skill that can help you in various ways, such as using exploit programs made for Windows or using the command line on someone else's Windows computer.

Hi everyone This is something that I should've done the first day but hey...better later than never right?

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

People have asked: "Here is an IP address. Can you hack this? Can you hack me right now?" Hacking takes time and skill. You can't just get an IP or an email and hack it in ten minutes unless the password is 1234.