In recent months, one of the most innovative and creative hacks in recent years has been wreaking havoc around the world. This hack has come to be known as CryptoLocker. I think it is an example of creative thinking while using some tried and true hacking and security techniques.
In this hack, the victim's precious and valuable files are encrypted and locked from their own access. These can include .doc, .pdf, .jpg, .xls, etc.
For the home user, these can include family pictures, tax returns, and other important files. In a business environment, it can include almost anything necessary to keep a business running, such as financial statements, taxes, and human resource records.
After the attacker encrypts these files, they then ask for a "fee" for access to the files, and in many cases, are getting that fee.
How CryptoLocker Works
Having first appeared in September 2013, it targets just Windows computers. It usually makes its way to the victim via an email attachment. When the user clicks on the attachment, it uses RSA 2048 bit public key cryptography to encrypt all the target files while the attacker holds the private key.
RSA encryption uses two keys that are different, one public and one private that uses very large prime number factorization.
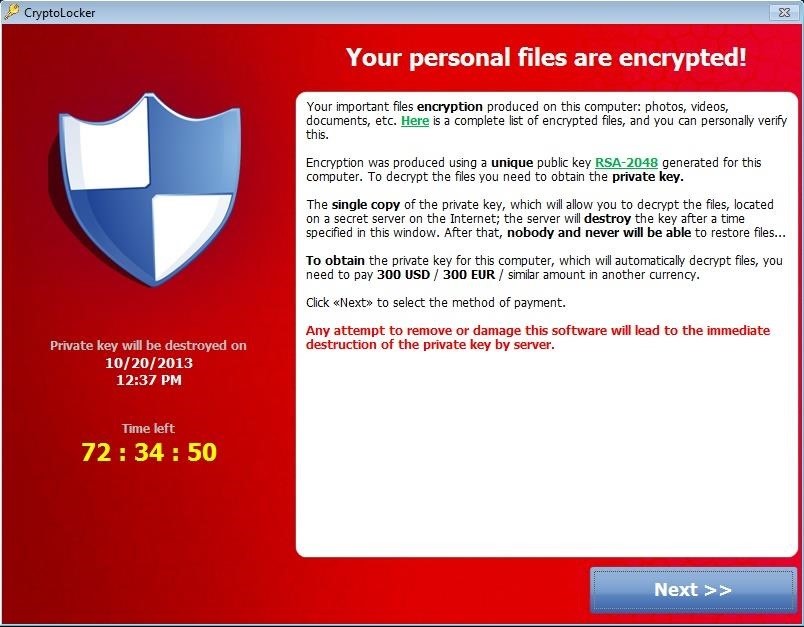
As this image above depicts above, the attacker gives the victim 72 hours to pay the ransom in the amount of $300 or 300 EUR for the private key and access to their files.
When you first become infected by the CryptoLocker payload, it saves itself as a random named file to the root of "%AppData%". It will then create one of the following autostart entries in your registry.
- KEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "CryptoLocker"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce "CryptoLocker"
- KEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "CryptoLocker<version_number>"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce "CryptoLocker<version_number"
Known CryptoLocker Email Subjects
Obviously, CrytoLocker is a social engineering hack. It requires that people click on a link to then infect their computer with the CryptoLocker payload. The creators of CryptoLocker were creative in getting people to believe that the email contained something of value or interest.
Here is a partial list of some of the subjects that creators used to get people to click on their attachment. Note that many of them have a business context.
- USPS - Your package is available for pickup (Parcel 173145820507)
- USPS - Missed package delivery ("USPS Express Services" <service-notification@usps.com>)
- USPS - Missed package delivery
- FW: Invoice <random number>
- ADP payroll: Account Charge Alert ACH Notification ("ADP Payroll" <@adp.com>)
- ADP Reference #09903824430
- Payroll Received by Intuit
- Important - attached form
- FW: Last Month Remit
- McAfee Always On Protection Reactivation
- Scanned Image from a Xerox WorkCentre
- Scan from a Xerox WorkCentre scanned from Xerox
- Annual Form - Authorization to Use Privately Owned Vehicle on State Business
- Fwd: IMG01041_6706015_m.zip
- My resume
- New Voicemail Message
- Voice Message from Unknown (675-685-3476)
- Voice Message from Unknown Caller (344-846-4458)
- Important - New Outlook Settings Scan Data
- FW: Payment Advice - Advice Ref:GB293037313703 / ACH credits / Customer Ref:pay run 14/11/13
- Payment Advice - Advice Ref:GB2198767
- New contract agreement. Important Notice - Incoming Money Transfer
- Notice of under-reported income
- Notice of unreported income
- Last months reports
- Payment Overdue - Please respond
- FW: Check copy
- Payroll Invoice
- USBANK
- Corporate eFax message from "random phone #" - 8 pages (random phone # & number of pages)
- Past due invoices
- FW: Case FH74D23GST58NQS Symantec Endpoint Protection: Important System Update - requires immediate action
The Victims of CryptoLocker
This hack has been successful across the globe, including many small businesses, city and state governments, and even a few police departments in the U.S.
Although security experts advise against paying the ransom for your files, the price is low enough that many businesses and families are willing to pay to get access once again to their precious files. What other option do they have?
I think one of the important aspects of this hack is that the ransom is reasonable low and most families and businesses can afford to pay it. As successful hack doesn't need to go after the one big prize to be successful (see Salami Slicing). In addition, the hackers have appeared to honor their word and unlock the victim's files when they pay.
A survey by researchers at the University of Kent found that 41% of UK respondents who were CryptoLocker victims, claimed to have agreed to pay the ransom. This conflicts with the 3% that Symantec estimated and the 0.4% estimated by Dell SecureWorks.
CryptoLocker's Earnings
As of December 2013, the attackers Bitcoin account had a balance of $27,000,00!
The key takeaway here is that these hackers really didn't invent anything new, they simply used some tried and true social engineering techniques coupled with some knowledge of public key cryptography to garner millions of dollars!








































12 Responses
nice, and if they use bitcoins or litecoins (bitcoins still going down in price) it will be very difficult to track the money, :) nice
how can we send crypto locker to target using email???
Just attach it to an email.
secret if you have to ask that, I wouldn't try it if i were you.
Thanks Jon.
btw I hope everyone has bookmarked this page, The social engineering ideas alone are worth a mint. I know I would fall for most of them.
if our computer is affected with this ransomware thn can we get rid of this by editing our registry values ?????????????
secret, at the beginning it states- it uses RSA 2048 bit public key cryptography to encrypt all the target files while the attacker holds the private key.
RSA encryption uses two keys that are different, one public and one private that uses very large prime number factorization.
right next to the WonderHowTo logo at the top it has a search bar, click on it and type data encrypt. Then read all the topics listed, Also read on Bitcoin as they do a public and private key encryption also and this sounds much like it.
Well, yes you can get rid of it multiple ways, but that won't unlock your files.
My friend was having this worm but it was easy for me to fix it.
I use the rule of SINGLE POINT OF FAILURE.
I already have the hard disk encrypted.
Shadow, partition copied.
And network backed.
The solution was too easy: format (transfer the shadow copy for safety) and restore from network.
sooo basically you restored a backed up copy?
for remove Cryptolocker use this special guide!
Share Your Thoughts