Hello to anyone and welcome in my first post here I'll try to teach you something here easy and fast.
Hacking social networks is a regular occurrence over the Internet around the world every second. Email, Instagram,Twitter,Youtube,Facebook and other online accounts are being hacked. Even if you are have strong passwords and taken extra security measures, yours accounts are not safe from hackers. In many cases, high security it can be helpful for hackers. You probably read this and wonder what he's talking about Do not worry, continue reading, we'll soon get to that part.
Let's Start from Something Simple and Popular
Good old bruteforce attack.
What really is brute force and how it works.
A brute force attack is a trial and error method in practice Imagine yourself trying to guess a certain password for example E-mail you have a friend and you want to break into his email how are you do it? The only thing you have in mind tries some words, number, characters or combinations like date of birth, street name, some special date, dog or cat name... if your friend password is 3.23.1996 or Michiganavenue127thStreet you will not have the trouble to guess that but if his password 3 .32199.6 or MichiganAvenue_127.thStreet or (dog name) layka - L4{y=K) />I or M!cH1g4nAv3eNuEiz7'7h$tre37 You can have serious problems to break this here comes bruteforce on his mind comes also words numbers characters but faster 100.000 times faster than our brain can also trial-and-error is one million times faster than human.
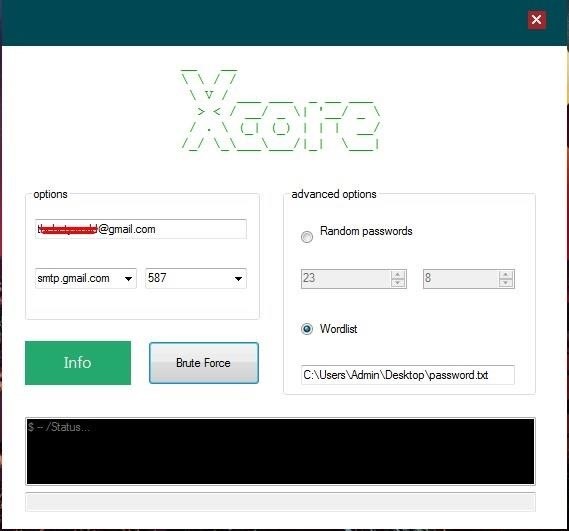
The bad side of this is just like human many of these tools they can not easy bypass the protection yes I'm talking about "trying too many times please come back later and try again" or "Prove you are not a robot select street sign... guess what? there are advanced tools who can bypass this not have many of them I have my favorite that I will recommend So if you're lazy And you do not want to sit in front of your computer spend years of your life to break the password like "L4{y=K) />I" then you need some good brute force tools like Xcore NO i do not motivate you to hacking friends/girlfriend, boyfriend or random people passwords You can use this in a nice way recover your old forgotten password!
Xcore in action
Let's Talk About Protection I'll Be Short
You can not protect yourself from this type of attack .
As I said many social networks have restrictions on using bruteforce attacks but there are also tools that easily bypass this protection
The best you can do is use 227 bit password or more it's not something you can remember
but many social networks have restriction for minimum and maximum bit This will only buy you time not protect you from hackers if they have a good resource like supercomputer think about that supercomputer which you can build for a few thousand can do 41,760,000,000,000,000 keys per second Hackers will not take much time to get your password.
If you are not lazy and do not want the software work for you Go for reading down.
Phishing vs Advanced Phishing
First comes the phishing You probably heard about this many times
What is phishing?
Phishing is a type of social engineering attack often used to steal user data like
login credentials
Phone Numbers
credit card numbers
private keys
etc.
Through the time of IT training many people have learned to recognize and protect themselves from phishing
It is still the most popular method.
Here it shows the example between traditional phishing and advanced.
Let's start with traditional phishing.
How this attack work?
The attacker creates a false page that adjusts to the original one.
Here an example for Facebook
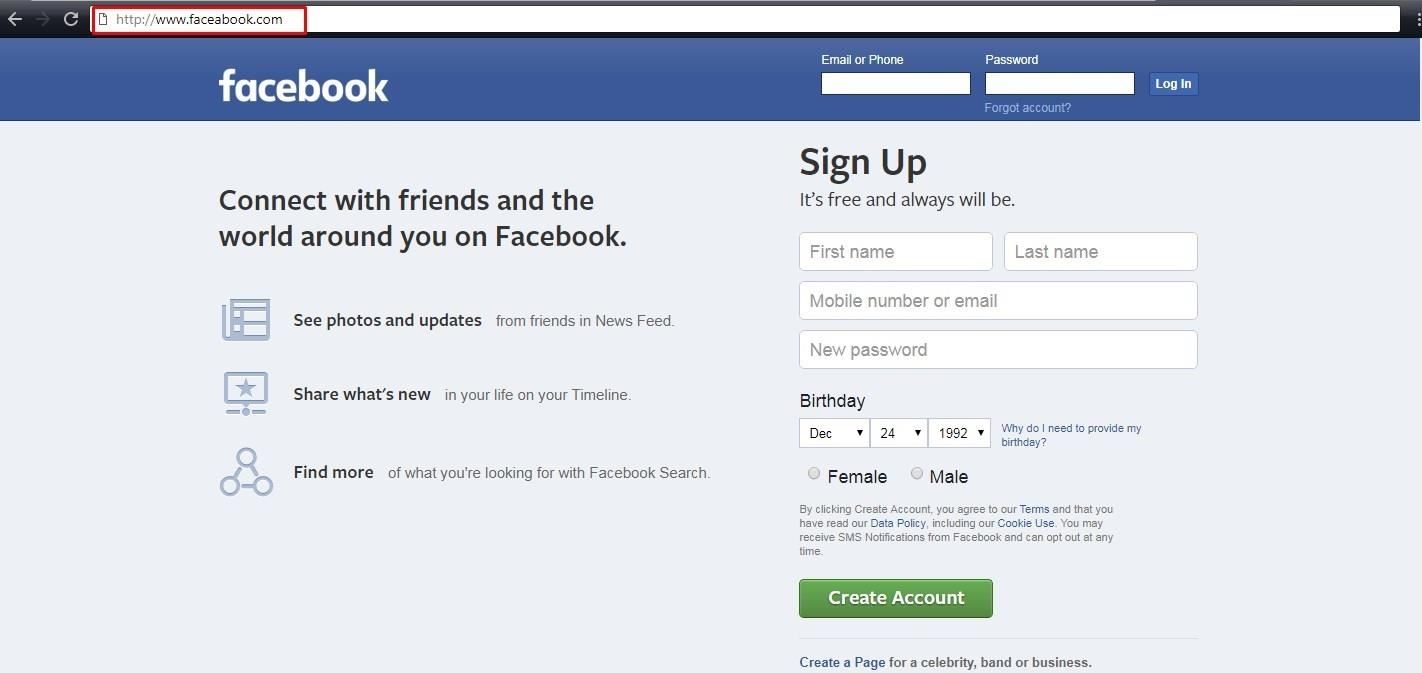
As you can see the page looks identical
we can notice that the address is not the same www.face(a)book.com also missing https
we know that this seems like a real facebook https://www.facebook.com
The attacker sends a fake facebook page to victim frequently via email where he plays the facebook administration and asks for login credentials It's an old technique.
I'll show you here another one much more successful.
There are other ways The attacker also creates a facebook false page.
and make another false page which offers giveaway or a free download
A hacker changes facebook like or a share button with his own phishing site
It would look like this in practice.
You surf the internet and find the page that gives the phone.
to win a new phone
please click below like or share
The next thing that happens is open popup page which looks like this.
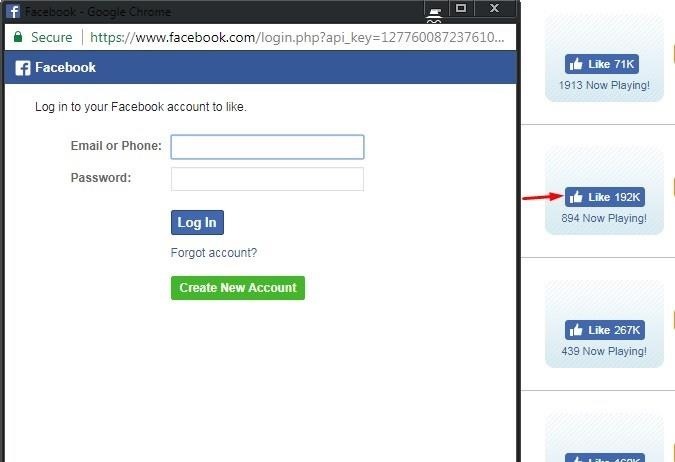
If you are logged in, you will be redirected
You see that this is the original Facebook page and if you are not logged in for continue asking for a login but if the hacker changed the like button You'll get something like this with fake Facebook address http://www.faceabook.com if you are logged in or not it will equally require you to log in
This is a way in which you will not pay too much attention and you will probably become a victim.
Next to the Line Is an Advanced Phishing with the Real Url Address
In this way, I'll show you phishing with real url address with 2FA (Two Factor Authentication) and SSL (Secure Socket Layer)
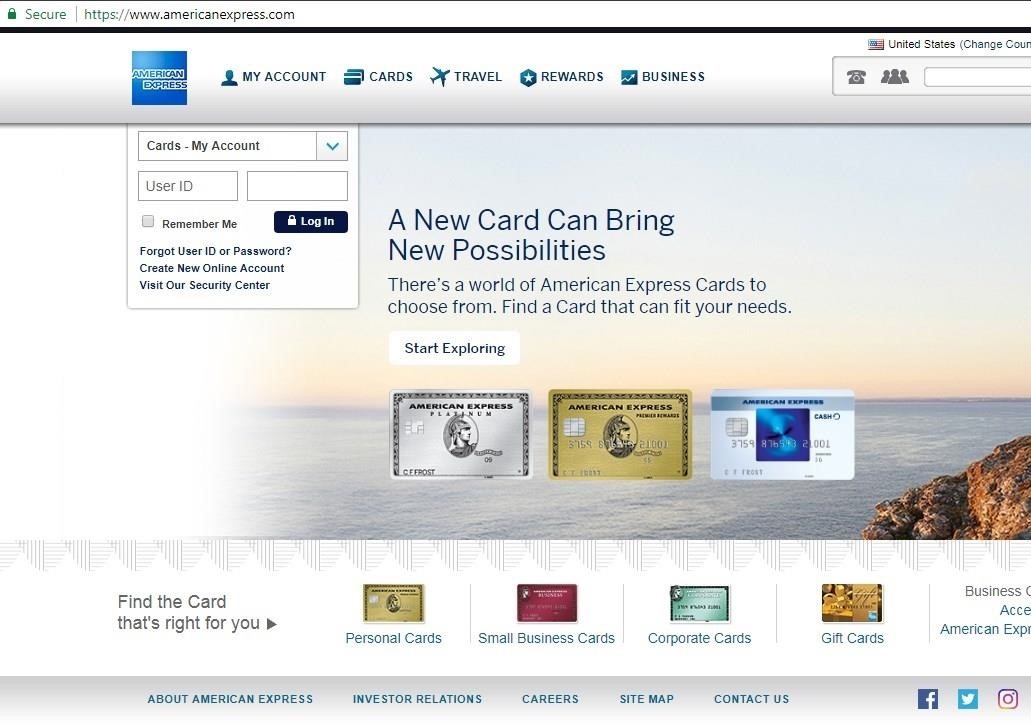
here is a fake American Express site as you see it owns the ssl and the original url address
this type of phishing is impossible to detect.
How we actually did this?
We did this with the help of a simple xn-- prefix Its the result of IDNA encoding The curiously-named system known as punycode is a way of converting words that can't be written in ASCII, such as the Chinese letters into an ASCII encoding here is example
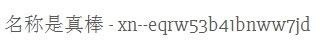
As we can see Punycode makes it possible to register domains with foreign characters.
This makes it possible to encode so-called International Domain Names (IDN) – ones that include non-ASCII characters – using only the Chinese letters for ssl we use Let's Encrypt
this type of attack has been fixed in some versions of Mozilla and Chrome.
2FA Phishing Attack
In this case, not use the original address only use ssl.
Again use the free SSL via Let's Encrypt to make connection look secure
Pishing strategies will look like this
Gmail login > password > two-factor pages then a redirect victim and generate api credentials
phishing vs real page
Gmail E-MAIL
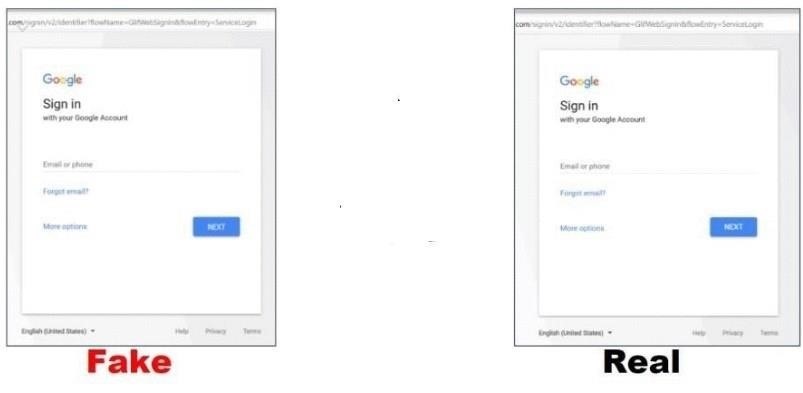
Gmail Password
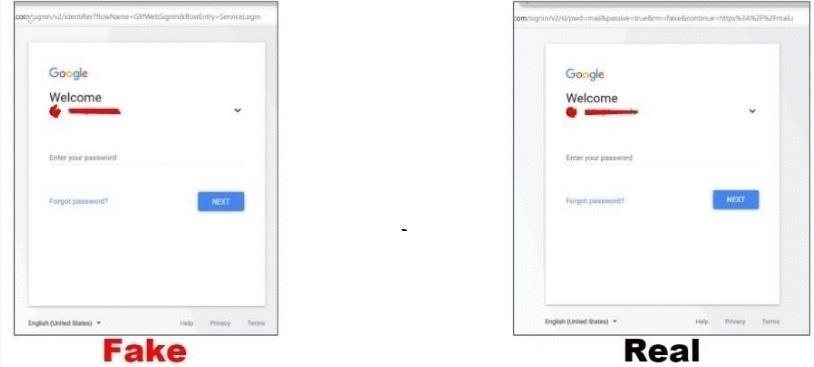
2 Step Verification
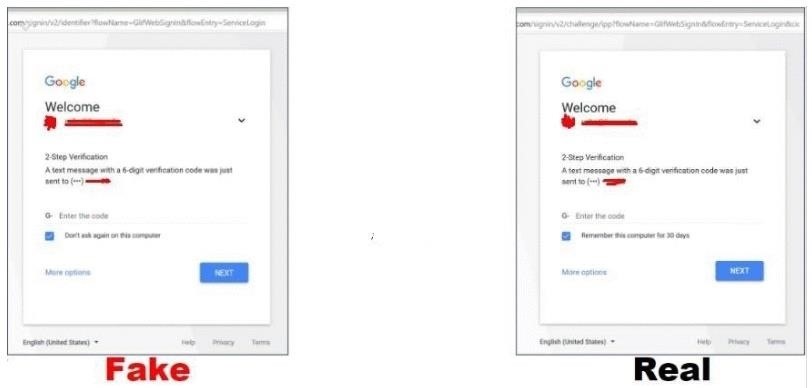
Check your phone
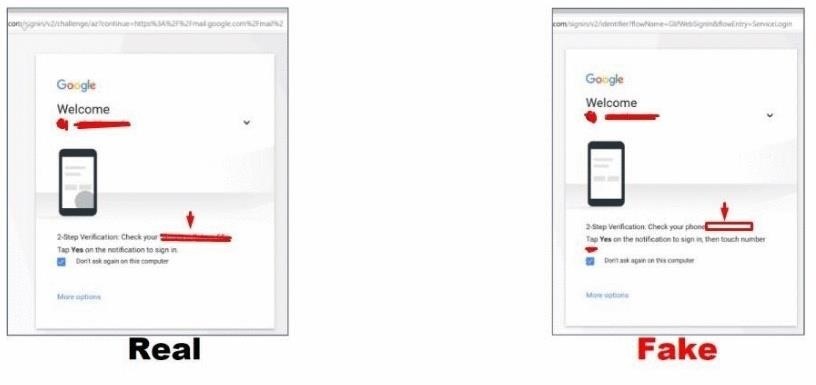
After that, we have everything we need to get to the victim's account.
There are many other phishing techniques like desktop phishing, Spoofing Phishing Attacks, etc.
As in the previous techniques we will not give details about "how to make" to make sure that someone will not abuse it.
How to Protect Yourself from These Attacks
Protection from traditional phishing is simple.
Avoid emails that ask you to log into your Facebook account.
always check the website url even when you click on a social locker.
Advanced phishing protection
As we said this problem is in some versions of Mozilla and Chrome is fixed.
If you have disabled the option automatic update for Chrome or Mozila
Download new versions and install.
2FA protection
in the attack we showed above we used 2FA and SSL to make everything look legitimate.
What we did not do is the original url address
Never look at it only SSL certificate and take it as safe and credible Check also the url address.
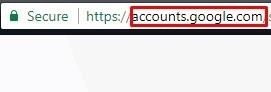
Let's Pay a Little Attention to the Keyloggers
What is keylogger?
Keylogger is a type of surveillance software that once installed on a system, has the capability to record every keystroke made on that system
We have two different types of keyloggers.
Hardware keyloggers and software keyloggers
what is hardware keylogger?
Hardware keylogger is electronic devices used for
capturing the data in between a keyboard
device and I/O port.
Hardware keylogger can be in your keyboard.

No this does not just happen if you take a keyboard from your friend.
They are made in a factory! (true facts)
A recorder can also be connected to your keyboard.
From your friends, boyfriend, girlfriend, parents boss at work and anybody else, one good thing They need a physical access for this type of keylogger.

Here comes something invisible something that does not need a physical approach
software keylogger
most software keyloggers communicate with SMTP AND FTP Send Log by e-Mail, Upload Log by FTP
There are also keyloggers which they use facebook chat, telegram,viber,youtube or Instagram inbox, comments, etc. to send logs These keyloggers are not so popular as smtp or ftp.
Some software keyloggers have a lot of features Here are a few of them.
Keystroke Monitoring
Screen Shot Capturing
Web Logging
Programs Opened
Microphone Logging
Webcam Logging
Captures passwords
Captures button clicks
Logs websites visited.
Invisible mode: that can mean it no show in startup, no show in-service no show in Task Manager no detected by antivirus or keylogger hunter, etc.
Here is video tutorial for one good Ardamax keylogger
How to Protect Against Keylogger
I will offer a few simple ways here how to protect against keylogger.
This will not help if you already have a keylogger on your computer and if it's a keylogger sophisticated written for targeted high-profile.
I will soon do a tutorial based on detailed analysis and protection from advanced keyloggers.
Go back to basic protection.
1 step) Download and install a firewall and choose the highest security setting so that all programs will need admin interaction from you before running.
2 step) Download and install Keystroke Encryption Software.
3 step) Download and install antivirus check for updates and scan your computer.
4 step ) Be careful what you download Any executable file you download can contain a keylogger
download and install Sandboxie and open files with it.
DNS Spoofing
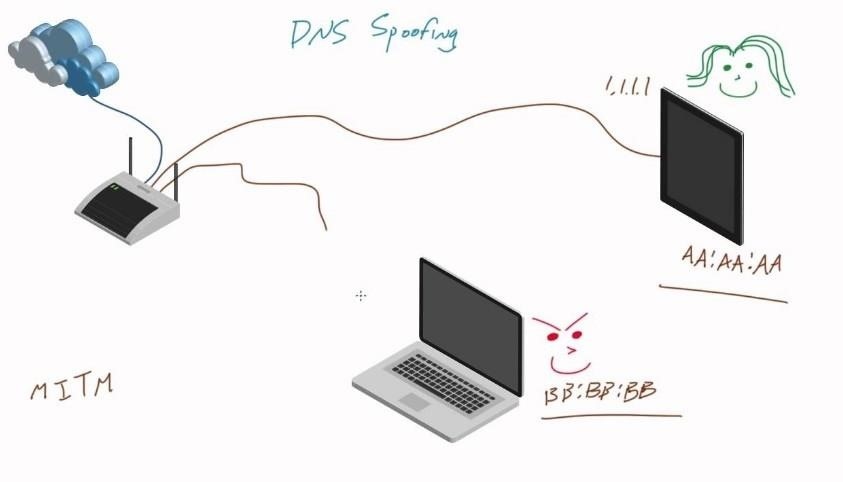
What is DNS Spoofing?
DNS spoofing is another one of the man-in-the-middle attacks that can It allows us to redirect the victim traffic to another website a fake website purporting to be a real one.
User: what is Instagram ip?
DNS Server: here is Instagram ip
real website: www. instagram .com 198.xxx.xxx.xx
attacker: changing 198.xxx.xxx.xx with the 208.xxx.xxx.xx address where he wants to redirect the victim
User: what is Instagram ip?
DNS Server: here is Instagram ip
www. fakeinstagram .com 208.xxx.xxx.xx
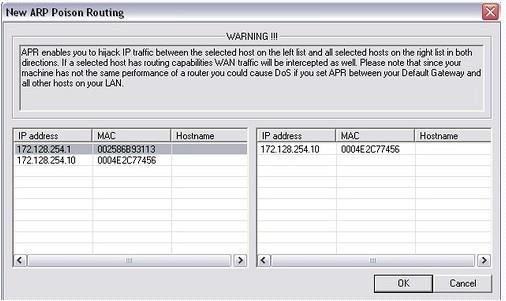
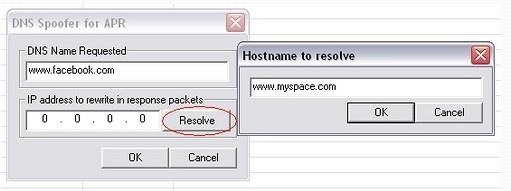
Now when user asking dns for facebook ip dns will redirect it to myspace.
How to Protect from DNS Spoofing
Deploy IDS/IPS: intrusion detection systems and intrusion prevention systems are capable of handling DNS spoofing attacks, so they need to be deployed inside the network as well as on the perimeter of the network.
2 step) in fortifying your DNS security is to deploy Domain Name System Security Extensions is a very secure that can be used to allow only digitally signed DNS records to be published on DNS servers. Through DNSSEC
using a random source port (instead of UDP port 53)
Configure Your DNS Settings
on Windows for DNS-hijacking
Open the control panel.
Under Network and Internet click on Network status and tasks and proceed to the Wireless connection.
Under the Wireless Network Connection Status, click on Properties and select Internet Protocol Version 4 (TCP/IPv4) properties.
Now you can give a DNS address of your choice.
At the bottom of the dialog box, select the Use the following DNS server addresses button and fill out your new DNS server IP information (8.8.4.4 for Google or 103.70.76.86 for DNSResolvers). Click OK and your new DNS will now be active.
For understanding MITM AND MITB
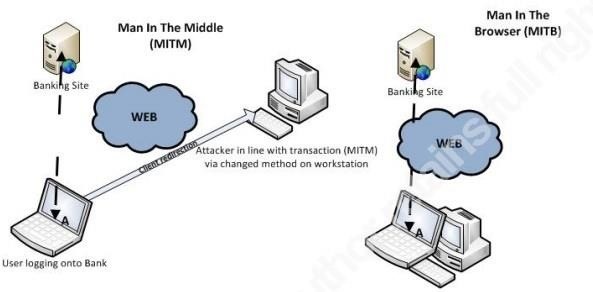
End-to-End Attack
End-to-End Attack what is end-to-end attack?
This type of attack is vulnerability in applications that use end-end encryption for secure communication.
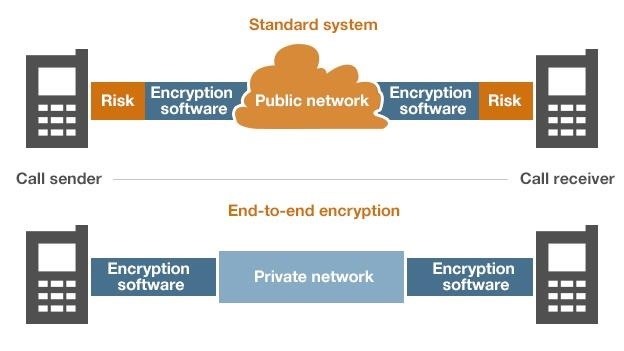
This type of attack allows an attacker to take over victims accounts and access victims
Chat conversations, contact lists, shared files, photos, videos, etc.
How does the attack work?
The attacker creates a malicious script and modifies it with the image for new attacker add new Mime type
to the variable in order to bypass the client restriction and upload a malicious script
After adding the malicious script Mime Type to the client variable client encrypts the file content and then uploads it encrypted as BLOB to server
here is result
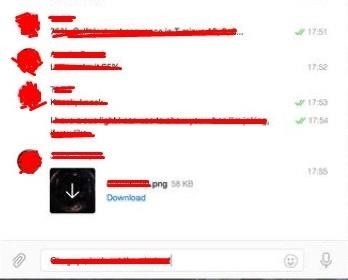
After clicking on the image the victim will be redirected to image under blob object which is an html5 FileReader object under address It gives the attacker access resources in the browser under address victim's data will be sent to the attacker and attacker can take over account and attacker can then send the malicious script to all the victim's contacts for massive spreading
also, the attacker can target the specified ones attacker can send messages with malicious script to your friend, boyfriend or girlfriend, etc. From your account to ensure that the victim will click "example" hey alice look this pic I caught jake cheated on you last night with another girl.
This and other methods of social and emotional manipulation will be effective.
How to Protect from This
Never open images or videos in chat form download it and start it safely (this also can be a bad idea.)
Set only you can use one session from your device.
Block all other sessions
Do not uinstall your chat app and install again it will not help you and the attacker will always give access to your account with certain javascript code you will never be able to log in again in your account.
Cloning Old E-Mail
More than 200 million people just on facebook have old and forgotten email addresses.
How this works?
This technique attempts to clone the email address that used to be In most cases, this email address exists in the database of a social network, but not in the email service can be deleted, lost out of date, etc.
Have you ever tried to log on to a site with your old address and get Something like this "sorry this address does not exist" or "we can not find an account with this email address" To me it happened on my gmail from 2012 year I had somewhere written that email and found it after a few years What I tried right now is to go to facebook he immediately showed me the profile, but I did not know the password After that, I went to gmail and tried to log in I got this..
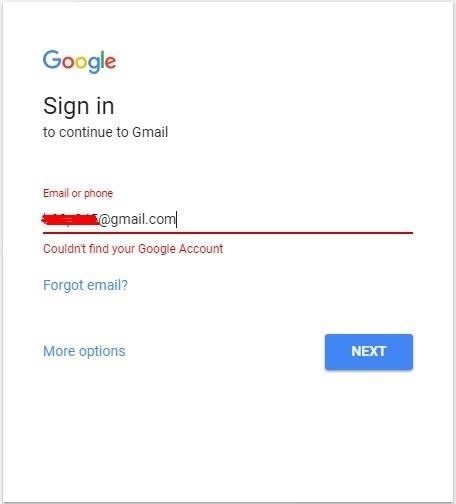
I tried to register the same Gmail and guess I succeeded.
The next thing I just did was go to facebook and ask for password reset.
And a jackpot They just sent me a password reset form.
This is definitely the easiest way to get in someone's account.
How to Protect from This
Check your old mail Are they out of date?
Try to register them again with a new password.
If you can not remember create new one, go to settings on the social network and replace with a new email address.
Click Jacking Attack with Invisible Login Page
What is Click jacking Attack?
Click jacking is a technique of stealing clicks on a website, redirecting to other locations, either using xss vectors to replace link goals (or entire parts of the page) or by placing your page in iframe clickjack is a form of embedded code or script that can be executed without user knowledge in transparent mode.
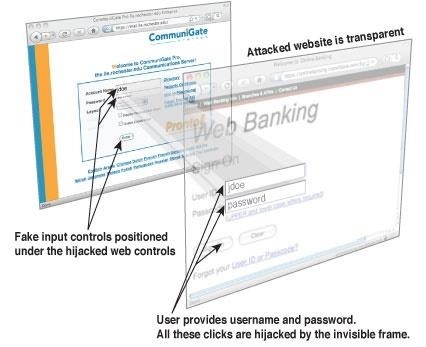
While searches your facebook and visit some site whether you found it facebook wall or received in the message does not matter.
Let's say you read the site with some interesting story or watch a shocking video.
clickbait (shocking scientists cloned the first t-rex dinoasuros PHOTO+VIDEO)
Of course you visit the site, and you become a victim of the attackers For example, an attacker can add a transparent button to install malicious extension and take over control of your account or spread spam You've probably already seen that your friends share strange files and tags all friends or download. exe file and execute etc all you can imagine do not want to click you will do it without your knowledge.
How else an attacker can take your account
also while you are on a site the attacker can make a multiple interaction in one transparent button He can develop a button that will logout you from the social network and also close your original page or redirect to his fake page can also create a transparent login form that will follow your mouse and wherever you log in, the data will be sent to him.
That's not all The possibilities are unlimited can do everything what can we imagine
The attacker can enable something on your computer such as a microphone or camera and stream you on the Internet.
It does not sound so terrible Only those millions of people are watching you and you do not know.
How to Protect Yourself from This Type of Attack
What I always advise is to look where you click and to which sites you open.
install NoScript It can be bypass with little coding and is not 100% protect you but will help.
Updating your browser specially flash.
Checking the social network and in friends or followers, you see people for which you have no idea how they got there this type of click jacking which is called Follow-jacking, subscribe jacking, like jacking, etc.
If you see the people, you follow and you do not know how You are a 99% victim of a click jacking.
PwS + WYSINWYC Attack with Replacement Url
What is PwS attack
Password Stealer (PwS) is a software that is specifically used to steal personal information, such a user names and passwords.
This type of software is exclusively written to steal a user names and passwords There are usually no more features like keylogger.
We will not talk about usb, PwS here.
What is WYSINWYC? What you see is not what you copy.
Paste jacking mode with a special type of rich text
copy where the apparently inncuos payload is pasted in a different one
context able to parse it. Or you copy "I AM THE BEST" paste "YOU ARE NOOB"
You can see that uses by portals and newspaper.
I'm going to show you an example technique with a url replacement of the original file.
Here we will target Linux users.
Example attacker creating a Super Mario Game and upload on git hub
Also, the attacker create stealer and upload on git to another account.
In the section read me can offer #install git clone https github. com/imniceguy/super-mario.git
with this type of attack replacemnet real supermario with github. com/imevilguy/super-stealer.git
when a user copy he copies real url but after he past in the console he got git clone https github. com/imevilguy/super-stealer.git now it can be too late.
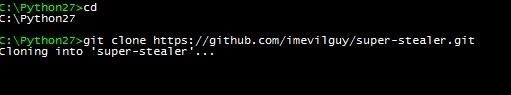
I used a lot of differences between the name but if only one letter changes, it can easily trick users.
How to Protect?
Always check carefully what you paste
There are many other software solutions, but you do not need it.
Social Engineering
What is that?
Is just psychological manipulation of people to give access their account or other confidential information
There are many ways to do but here I will give you one mine.
Note: this story is not real I invented it for this tutorial.
user1) discussing with someone here is no way that you can hack my facebook password.
user2)I can do it. I'm the best hacker.
user1)prove me if you hack me, I'll give you $1,000.
user2)I'll do it tonight.
user1)Well let's see.
user1) found some simple ftp keylogger companies and pay ads on facebook in her country for spy software.
user2) see ads This can be good I will definitely buy and hack him with this.
user2)But how can I do it? I know! I'll make a fake profile and introduce myself as a pretty girl.
user2) Hello, I buy your software for a spy how can I use can I get a technical help?
Spy software company) Hello, sir thank you for purchasing our software to use the software add your email and passwords to which you want send logs check other options and click generate after that send svchost. exe file to victim.
user1)accept a request from a pretty girl.
user2 with fake acc)They talk for a while after that user2 asking send me some nude and you are hot boy
user1) I'm shy and I do not think it's ok so fast I'm sending you pictures.
user2 with fake acc) It's okay, do not worry, I can send you some first.
user2 with fake acc) send pictures binded with keylogger hey here is mine nude:)
user1)Analyze code from keylogger finds email and password.
Here we see how easy user1 gets what he wants.
This is one of the type social engineering attack.
How to Protect from This Attack
Your brain is the best tool to protect against this attack Just use it.
SS7 Attack
Finally, we came to the point where your high security helps the hackers.
What is ss7?
Signalling System No. 7 is a international telecommunications standard which is used to set up and tear down most of the world's public switched telephone network (PSTN) telephone calls. It also performs number translation, local number portability, prepaid billing, Short Message Service (SMS) etc.
How attacker can hack you and what can hack?
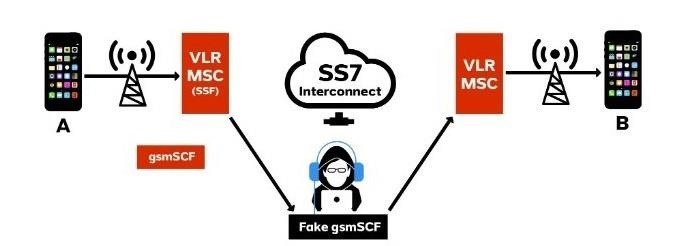
The attacker can hack everything that the uses phone number for security.
All he needs is going to reset the password, and that is It looks so hard is it?
How did he do it?
When we use telephone networks to exchange the information needed to transfer calls and text messages between themselves and to provide proper billing Someone can control it
if you ask google to send you a pin code attacker can use your number that he gets a pin just as shown above in the picture he can also control you to never get a pin or other request.
He can do many other things like.
Track your location yes just like government secret agency or
Listen to your calls, spy on all your messages, Get access to all your communication apps.
Can do everything what police and mobile operators can do.
But do not worry there is no place to care police and mobile operators need legal spy warrant
attackers do not need to.
But the best of all there is no protection ss7 delays to fix the vulnerability or simply you can not do anything to protect yourself.
*If after reading this, you thought that you now know everything and you are safe
I have to tell you this was for complete beginners.
There are still thousands of ways to hack anything we call them vulnerability.
In some of the next posts, I'll show you how to find vulnerability in social networks and report them to Bug Bounty or use for illegal purposes you choose! *









































Be the First to Respond
Share Your Thoughts