Everything Else


How To: Make a Simple UDP_Flooder in C pt2
Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

How To: Make a Simple UDP_Flooder in C pt1.
Alright, this will be my first tutorial in C. Note that this guide is written for Linux.

How to Java: E5 (For Loops)
Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.
How To: Make Wordlist with Cupp
hey everyone ,im a newbie here at null byte and i want to say thanks for all the tutorials and information people give me here.

How To: Use NMAP 7 to Discover Vulnerabilities, Launch DoS Attacks and More!
NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

How To: Advanced System Attacks - Total Guide
Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

How To: Social Engineering - Total Guide
Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

How To: A Guide on Runtime Crypters
What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

How To: Write Batch!
Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

How To: Advanced Cryptography - Total Guide
Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

How To: Cryptocurrency for the Hacker Extra 1- the Stereotypes
This is not essentially the next part in the series, but an expansion of previous part about why should you not use cryptocurrencies.
How To: A Simple Virus Written...in Bash!
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.
How To: Turn a OSX Backdoor into a .App
Hey its August. I dont know why I post so often but I wanted to add up on a post by Cameron Glass here What we are going to do today is turn that backdoor into a .app file so that we dont even need to touch the victims computer! also thanks to someone who helped me with this. (You know who you are)

How To: Perform an Attack Over WAN (Internet)
So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.
How To: Get Administrator Privileges on Mac
So yeah. Its AugustFackYou and I felt like posting today and being an active member of the community. After reading this please tell me if you have any comments on what I can do better or if this method is bad. Anyway today I will be showing you how to get root on a mac. I managed to become an administrator at my school with this and one other method.

Coding with Typo: Structured Query Language (SQL) Part 1: What Is SQL?
Welcome to the first coding tutorial on SQL here on Null Byte. Typo:
How To: KALI Linux 6 Things You Should Do After Installing
Ok, now lets introduce myself i am also a newbie but conducted many pentests.This is the tutorial for customizing kali linux

Coding with Typo: Structured Query Language (SQL) - Yes/No?
Basically, I have been pondering this a bit. First Off:

Networking Foundations: Dynamic Host Configuration Protocol
Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Dissecting Nmap: Part 1
Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

How To: Hide PHP Code in an Email Image
In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

How To: Bypass UAC Using DLL Hijacking
This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

How To: Scan Websites for Vulnerabilities with Arachni
Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.


How To: Gathering Sensitive Information: Using Advanced Search Queries
continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

Zanti: Nmap
In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

How to Java: E4 (Methods)
Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.
Advice from Typo: Mastering CMD Like a Real Hacker, Part 1 (Colors)
Another series I am now starting, might have to slow down on all of these series, but why tf not. What Is CMD?

How To: Create a Metasploit Exploit in Few Minutes
Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

A Hackers Advice & Tip: Choosing Your Path. Knowing Where to Learn & How to Learn It **Newbies Please Read**
This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

How To: Create a MySQL Server BruteForce Tool with Python
Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

How To: RootKits 101 (I). The Basics
removed!

How To: Hide a Virus Inside of a Fake Picture
In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus
Zanti: Introduction
I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.
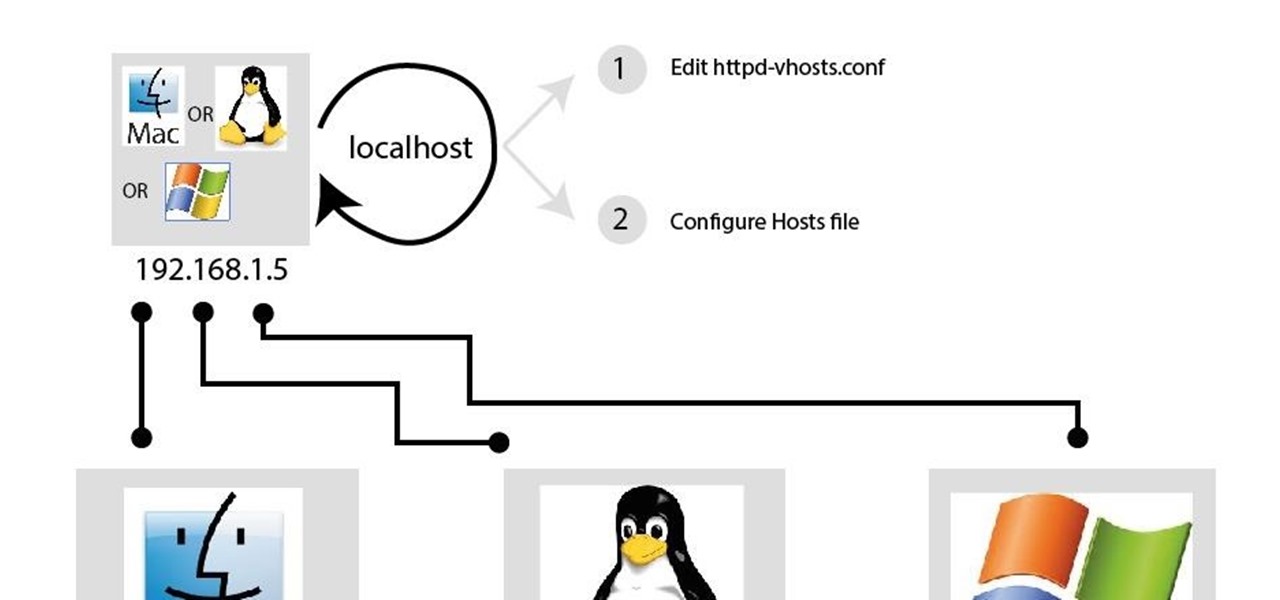
How To: Access Xampp Server Remotely
In my last article, I discussed: How to install xampp

How To: The Ultimate Guide to Upping Tx-Power in Kali Linux 2.0
Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.
How To: Bypassing School Security (White-Hat)
While following a tutorial on python recon tools, I found a new way to access the command prompt on a school network. While there are other ways of bypassing security, it's nice to learn use Python's OS library.

How to Program in C# : Variables and Data Types (Part 2)
Welcome back my friends !! Today we'll go through the second part of this C# series

How to Java: E3 (If/Else Statements)
Hello Java-ers, In the previous two tutorials, we learned about installing the JDK, Installing/CreatingAProject in Eclipse IDE, and data types in Java.







