description = [Searches for exploits in the exploitdb on Backtrack. This archive can also be found at http://www.exploitdb.com]
author = "L10n"
license = "Same as Nmap--See http://nmap.org/book/man-legal.html"
categories = {"safe", "vuln"}
require("stdnse")
portrule = function(host, port)
return port.state == "open"
end
action = function(host, port)
local n = port.version.product
local exploits = ""
for line in io.lines ("/pentest/exploits/exploitdb/files.csv") do
if string.match(line, n) and string.match(line, "remote") then
local items = split(line, ",")
local file = items2
local desc = items3
exploits = exploits..file.." ---> "..desc.."\n"
end
end
if not string.match(exploits, "\n") then
exploits = nil
end
exploits = " \n"..exploits
return exploits
end
function split(str, pat)
local t = {} -- NOTE: use {n = 0} in Lua-5.0
local fpat = "(.-)" .. pat
local lastend = 1
local s, e, cap = str:find(fpat, 1)
while s do
if s ~= 1 or cap ~= "" then
table.insert(t,cap)
end
lastend = e+1
s, e, cap = str:find(fpat, lastend)
end
if lastend <= #str then
cap = str:sub(lastend)
table.insert(t, cap)
end
return t
end
I found that script on exploitdb's papers , already downloaded the files.csv and modified the path but i still cant run that script. If someone can help me with that i would appreciate.
Thank you
























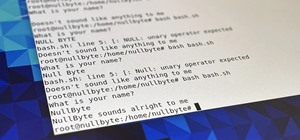














24 Responses
To help, we would need a screenshot or error messages.
NSE: exploitdb against scanme.nmap.org (74.207.244.221:67) threw an error!
usr/bin/../share/nmap/scripts/exploitdb.nse:16: bad argument #2 to 'match' (string expected, got nil)
stack traceback:
c: in function 'match'
usr/bin/../share/nmap/scripts/exploitdb.nse:16: in function usr/bin/../share/nmap/scripts/exploitdb.nse:12
(...tail calls...)
this error was reported when i run this command (nmap --script=exploitdb.nse -sV scanme.nmap.org)
Rui:
It appears that in Line #16, it failed to read in the files.csv file. The error says that the variable was empty (nil).
otw:
But i putted the files.csv on the path above.
"/pentest/exploits/exploitdb/files.csv", im using kali linux, and this tool was made to be used on backtrack.
what could be the problem, maybe the permissions?
At the risk of stating the obvious, Kali and Linux are different.
Did you check to see if that path is correct?
kali
i checked using the cd command from the "/" directory, if it was possible you could test in your machine to see if it works correctly
I did. The path is set incorrectly for Kali.
And
Should something be in the local exploits = "" up there perhaps?
so what is the path for kali, because i downloaded the files.csv from exploitdb manually and tried to set the path but still getting the error
Simply set the path in this script to the location of your files.csv.
but the problem is that i already did that, i created this path /pentest/exploits/exploitdb/files.csv on my kali and it still giving this error, maybe the folder "pentest" is not on the root directory.
i created a pentest folder on the root directory, and inside the pentest folder i created a exploits folder and inside it i created a exploitdb folder and inside it i unzipped the file from exploitdb site. so it was suppose to work i think
Show us the screenshot of the files with the path.
http://imgur.com/XrTN1OL
Rui:
Use the shell, navigate to that location and cat the file.csv and give me a screenshot here on Null Byte.
You are making this exercise SO difficult. Simply find the path to the files.csv in Kali and put it in the path in the script.
I didnt knew that i could upload images from the site, im sorry.
Explain to me your syntax in using this script.
Explain each field and what it is supposed to do.
nmap --script=exploitdb.nse -sV scanme.nmap.org
it is supposed to determine service/version info and the script search on exploitdb website for vulnerabilities/exploits for each service
First, you did not explain your command, only what you expected it to do.
If you are scanning your own system for exploits, why are you targeting your script to scanme.nmap.org?
im not scanning my own system for exploits.
i used this script to make a little easy the part of getting vulnerabilities of the services/versions.
so since im testing the working of this script i decided to target scanme.nmap.org, because i dont get on troubles scanning it
Then you misunderstood what this script is doing. It is looking into Kali to find the vulnerabilities and exploits.
You could use the Linux "find" command to do the same thing, quicker and easier.
otw:
thanks, i didnt knew about find command, im reading your guides of the basics of linux.
thanks for all and have a good day
RUI:
You need to make a little change to the script. The script was written for BackTrack in mind and since you're using Kali, you will need to substitute "/pentest/exploits/exploitdb/files.csv" with "/usr/share/exploitdb/files.csv" to reflect the new directory structure location in Kali. I hope that solves your problem.
Share Your Thoughts