Hello fellows, this is my first time I post an article on nullbyte so I hope you like it :)
Today, we will replicate a technique which has been used by recent, sophisticated and hard to trace a Russian malware called Hammertoss, the creators of this malware has abused multiple well known sites like Twitter and Github to defeat modern firewalls and torture whoever tracing their tracks.
In a nutshell, instead of getting a direct reverse connection back to the C&C server similar to what traditional malware does, this smart malware will jump between third party servers to perform its malicious activity, please take two minutes and watch this short explanatory video from Fireeye so you will get a quick overview how the malware works.
Step 1:
All right, so the first stage of Hammertoss was to connect to a Twitter looking for a tweet created by the hackers which contains a URL for an image and hashtag as a part for encryption key. Technically speaking, you don't need to login into Twitter to parse someone's tweet, so in this case, we just need to figure out the account URL to navigate and the HTML tags which contains the actual tweet, Keep in mind you can add other twitter accounts to hide the original one (which belongs to the hacker).
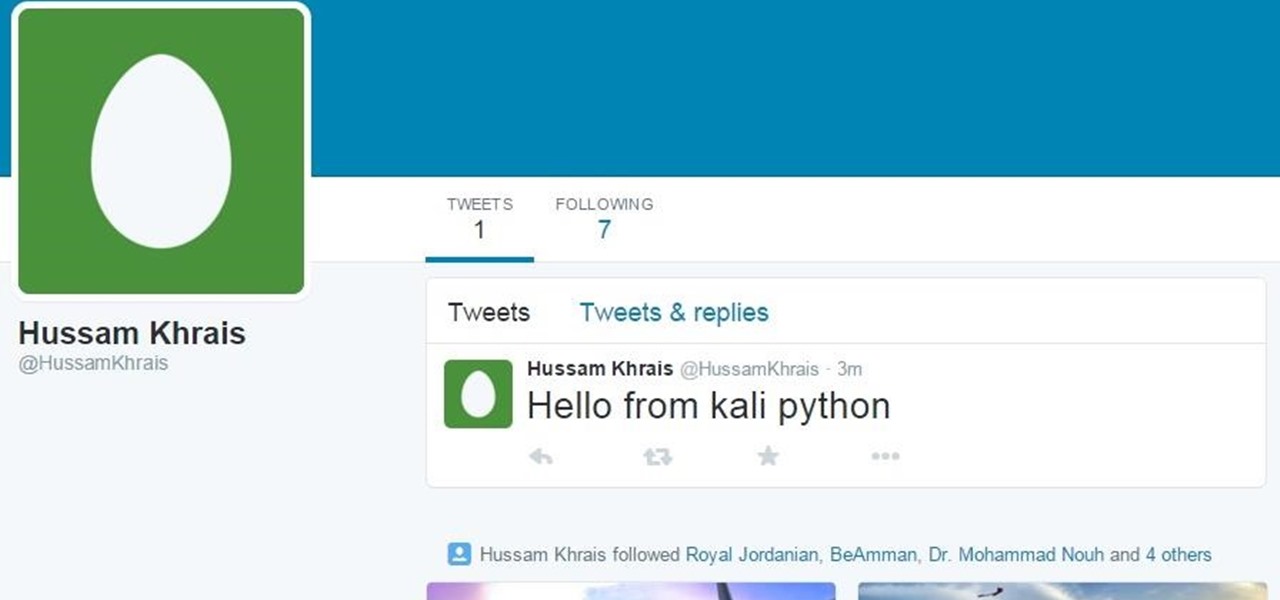
Obviously you should never your personal account while doing similar stuff, that's why I created a new account holding my name and here's is the link for my twitter home page
https://twitter.com/HussamKhrais
Now from my Kali machine, I made a tweet saying "Hello from kali python" then I logged out, at this point once we click on the above URL, we should see something similar to this output
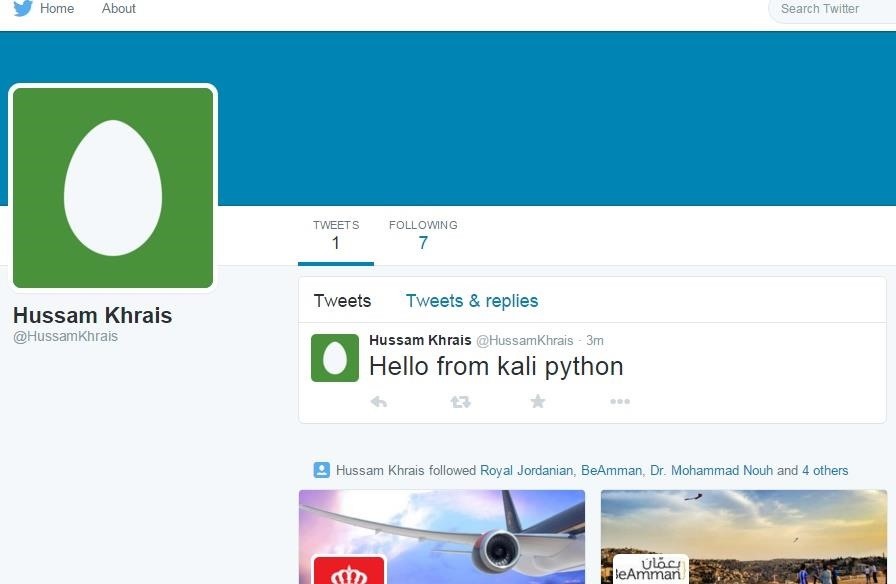
Step 2:
Now using your browser you can view the HTML source code of this page, in Chrome just do a right click anywhere in the page and select "View page source" or Ctrl+U for short, in the HTML if we search for our tweet, we will get the below HTML line:-
<meta name="description" content="The latest Tweets from Hussam Khrais (@HussamKhrais): "Hello from kali python"">
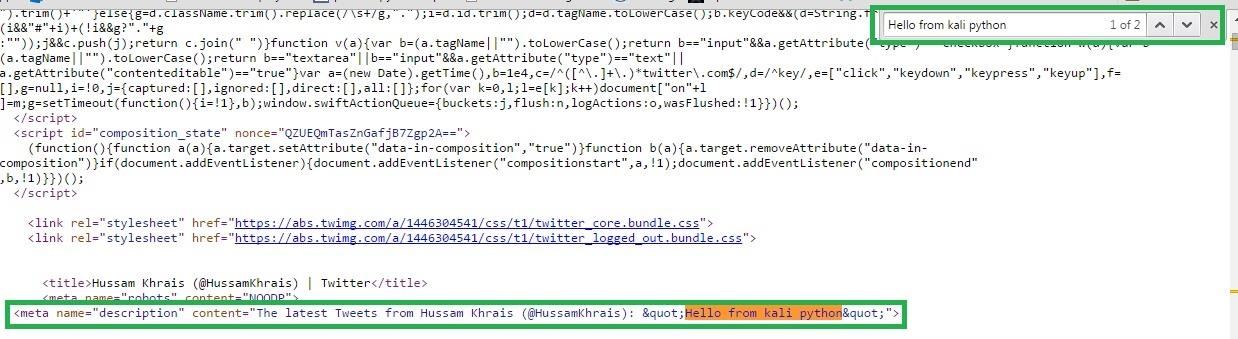
So technically if we code a simple script that will navigate to https://twitter.com/HussamKhrais
And retrieve the HTML page, then inside the HTML if we search for meta tag called name that has a value of description and asked for the value of content, then we should be able to grab our tweet.
Step 3:
Let's translate this action to a code:-
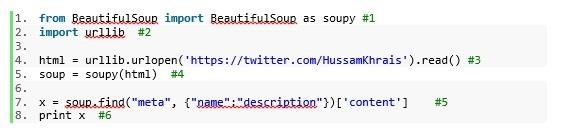
1# Import soupy function from BeautifulSoup library, we will use this function to search for the html tags
2# Import urllib which will be used to navigate to our twitter page and grab the html for us
3# Navigate to my twitter home page HussamKhrais, store the HTML page into html variable
4# Pass it to soupy function so we can parse it
5# Here we search for the HTML meta tags
6# Print the result out
The output for running the script would be
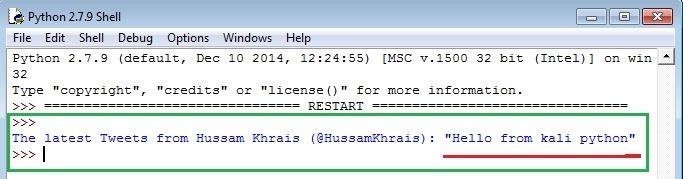
Step 4:
At this point, since we are only interested in having the string between the quotation marks, we can filter it out using regular expression, and that exactly what the below script will do for us
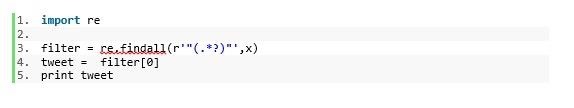
the findall function will grab the string between the " " and store it in a list data type called filter, finally we print the exact tweet.
After putting all the script pieces together, we got the below result
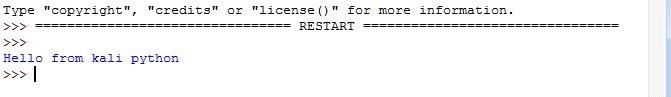
Please feel free to
download the script and give it a try on your own tweet!
Step 5:
Now think about it for a second, can we use twitter to replace DDNS? Well, what will happen if we replace "Hello from kali python" with the attacker public IP, and each time the attacker IP changes, all what he needs to do is to send a tweet with the new IP to get the reverse connection for his victim!
A question for you…
After reading this article, do you think that can you code in Python a complete AV free remote shell and exfiltrate data without even having a single direct connection with your target? Please share your thoughts.








































6 Responses
Very nice article ! Thanks for sharing.
With answering your final question, it is indeed possible to do so. Using http is a very old and effective way to communicate to a C&C to upload and download data.
Almost sure to bypass a network based firewall (not so for an application based one, but meh, who uses them?) and possibly fly under the radar of a IDS. Still, whenever a victims suspects infection, it will have a lot of signatures of consistent timed traffic towards website he never visited (logging http / dns requests is very common). Whenever the attacker adds multiple inncent's handler to ther twitter's list (smokescreen is always good), once the pandora's box is open it's easy to spot the culprit. Twitter has been long known to cooperate by temporary / permanently taking down accounts if they are informed of illegal activity. When I'm sure the malware writers can easy add more accounts to his watchlist, as soon as an APT campaign's cover has been blown, it shall be considered dead on water.
On a side note, using social networks as a C&C is a very good idea, but also consider that most companies would block access, because employes spend just too much time on them, so for some cases that's just a bad idea, depending on who you are targeting. I think that's the reason why the authors also added github, but I might be wrong...
Another funny thing is: at around 1.15 in the vid, you hear that data is uploaded to a cloud drive using credentials that were stegged in the image. This means that researchers can potentially get those credentials either by hijacking the connection or thru malware reversal, whichever has the weakest protection. What could a good guy possibly do when he gets inside the belly of the beast :) ?
Overall, this piece of malware uses some nice concepts, and it would not be too hard to apply those concepts in more homebrew code.
Good luck with your course at Udemy, seems really worth the money (well, after the 83% off... lol). You might want to change the url tho... the CouponCode reports Linkedin campaign while it should be nullbyte campaign :)
Come back with more interesting stories, I'm looking forward it.
Cheers !
Thanks a lot for your comment, i totally agree with your thoughts, i would like to add to your point that many companies are blocking social media site, in response to this, malware are getting more sophisticated in adding multiple attacking vectors, for instance if twitter was blocked, then how about trying google form, and so on ... i remember that i read an article about a malware that uses Microsoft technical forums as C&C lol :)
this is correct, but i think they used an RSA public key in the image to encrypt the data before sending over to the cloud, the private key which is the one who can decrypt the data should never leave the attacker PC, make sense now?
sure i will be back again with other pytho stuff ;)
Cheers
Your course on udemy looks amazing (I would definitely join if I wasn't allergic to spending money) but since this is your first post, you should probably read the rules for community submissions (especially rule number 4). Thanks for discounting us on nullbyte.
thanks for your comment, well, believe it or not i'm allergic as well !
i believe that everyone has the right to learn, that's why i made the price as minimum as i could, anyway thanks for your participation :)
CSRF ? The explanation is very short to understood
no it's not, in few words, technically speaking, you can control your victim ( your target ) remotely over twitter without the need to have a direct IP connectivity between you and your target, all what you need to do is code the malware that installed in the target side to connect to the hacker's twitter account to receive the commands to execute. hope it's clear now.
Share Your Thoughts