There are different methods to hack wireless devices, likewise drone is the best target to tinker with and develop proper exploit code and injecting them into it.
How to Hack Drone Using Hackrf ONE?
In this world everything is getting wireless for the convenience of people. This is the opportunity for hackers to hack into the system to which data is sending and receiving. Here we will discuss about the vulnerabilities by which a drone can be hacked from any distance.
Most of the drones are working without any encryption and that makes it vulnerable to wireless attack. Here we will learn and understand the attacking methods and its medium.
Step 1: Requirements...
Foremost, you need a basic requirement of radio frequency knowledge, because this is different than web based attack as you won't get walkthrough links. And at times this will make you bored because this is something hard to learn and understand so if you are really interested you are ready to go.
1) Hackrf one (any SDR which is capable to transmit and receive )
2) Any system that can run GQRX, SDR# or GNU radio companion.
3) antenna 500 (which comes inside the pack)
4) For greater range you can depend on parabolic antenna.
Step 2: Scanning the Radio Frequency Range
Before initiating attack on the target we should be aware of the frequency range of the target in which its operating. But we know most of the drones are working on 2.4 ghz.
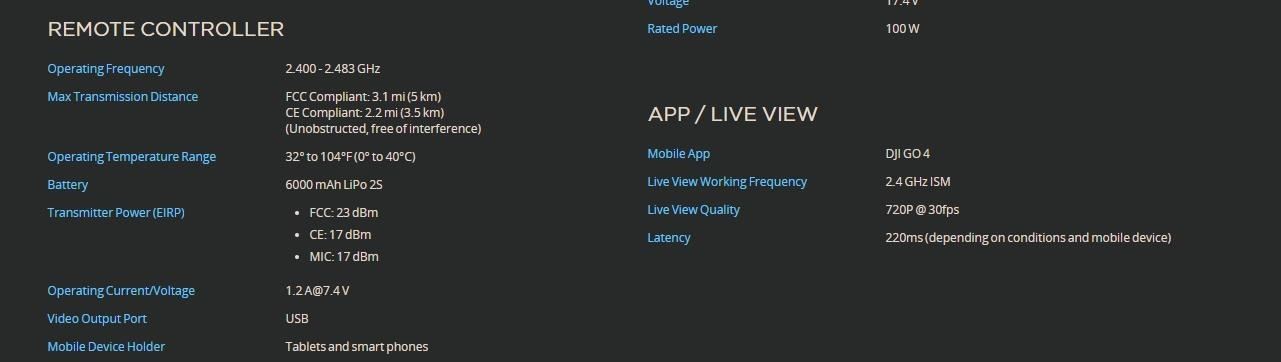
We can see the operating frequency is at 2.4 ghz . Now the frequency is confirmed.
Over here we have taken dji Phantom 4 as target for testing purpose.
Step 3:Capture the Signal
Open GNU radio companion and open new file and follow the below instruction to capture the RF signal from the transmitter.
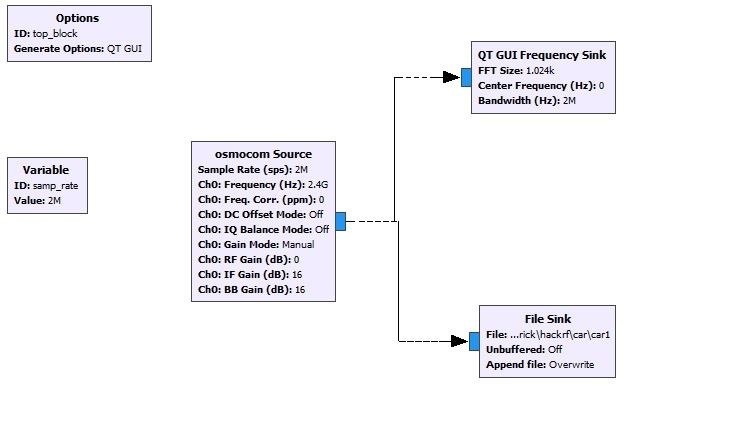
This lets the SDR to hack the radio frequency and the data that is sent over radio spectrum and the transmitted data is capture.
Step 3: Replay Attack
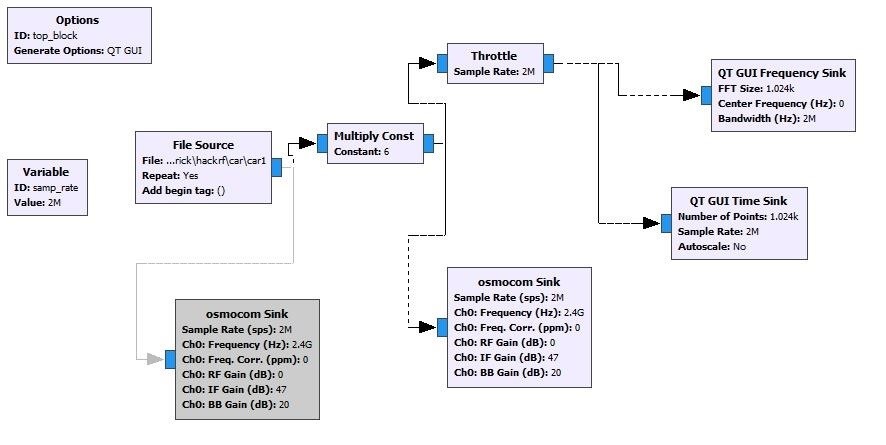
Now the capture data is subjected to replay attack and the capture data can be modified using software like audacity for different purpose.
For example: If the data that transmitted from remote to drone is to move forward, then using audacity the data can be manipulated for implementing different tasks because each and every signal contains different signatures of command to follow.
Step 4: Conclusion
This is the simple method to conduct replay attack against drone as it is operating on 2.4ghz. All drones are not vulnerable to this attack.
This is just one attack explained but there are different methods to hack drones.









































Be the First to Respond
Share Your Thoughts