Welcome to a series I'm working on called I.C.E. - Intrusion Countermeasures, Electronic. To kick things off (pun intended) I'm going to show you how to close another persons SSH connection to your server before they can do much damage.
Phase 1: Target Discovery
In order to remove an attacker, we have to identify them. The best way to do this is to run
who -u
This will tell us all users and their process IDs, or PIDs.
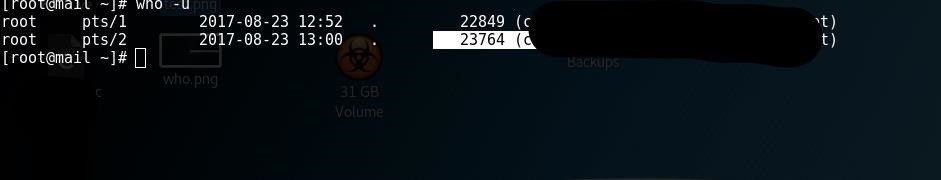
As you can see, I get two users, both root. I've identified pts/2 on PID 23765. But there's also pts/1, on 22849. We need to verify who's who.
Phase 2: Insulting and Identifying (In one fell swoop, no less)
This is very simple on two user systems, which is what you'll generally run into if your small server or computer is hacked.
To determine which user is you, type
echo "Goodbye, skidmeister" | write root pts/2
The echo command can be replaced with the insulting message of choice (I recommend "You cannot escape the clutches of the sysadmin, thou foul hacker scum"), and write is the pts you plan to target followed by the appropriate username.
As you can see, I found myself instead of an attacker. This is actually good news, even though we just cursed ourselves in the mirror. It tells us that in fact, pts/1 is the attacker.
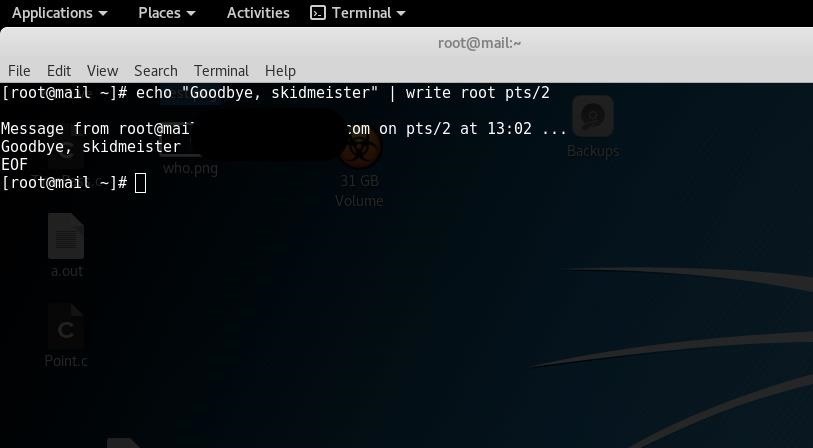
So we do it again, except we use pts/1 instead. Everything else remains the same, even the username, since we're both root. Needless to say, it's easier if one of you isn't. Hopefully the attacker, because if he has root and you don't, you've got bigger problems than insults.
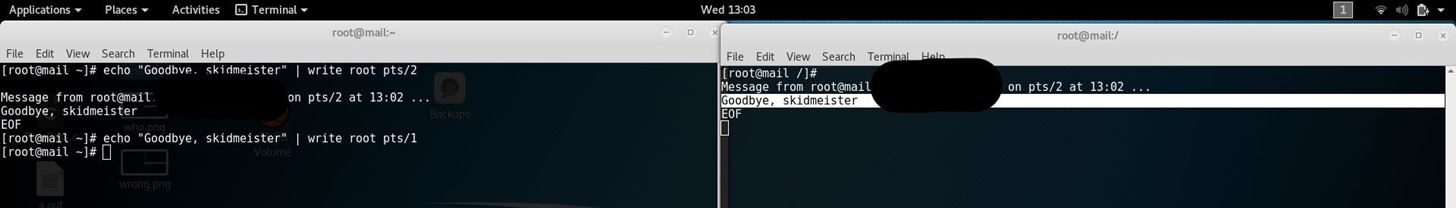
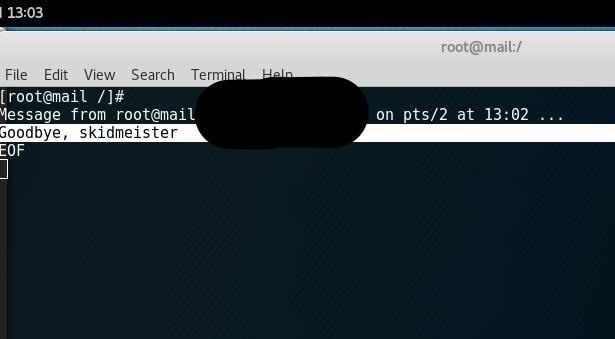
Perfect! My "attacker" terminal lit up with the message we delivered. Now it's time to make good on our promise.
Phase 3: Execution
To remove the attacker is one of the simpler commands we as admins will ever have to use. It's just
kill -9 (attacker PID)
So for me, to kick off pts/1, I had to type:
kill -9 22849
Once we run that, our attacker is disconnected, giving us time to change the compromised password with passwd , and any others he might have gained access to.
This is the aftermath of the removal, as the attacker sees it. (Sorry I don't have a picture, I resized my terminal causing a confusing wash of text, as well as having the attacker terminal obscured by my screenshot program.)
Connection to (server) closed.
Sure to break a hacker's heart.








































Be the First to Respond
Share Your Thoughts