A few days ago some stupid Neighbour or so Hacked my AP, changed the Admin Password and deleted every Port-forwarding rule in it.
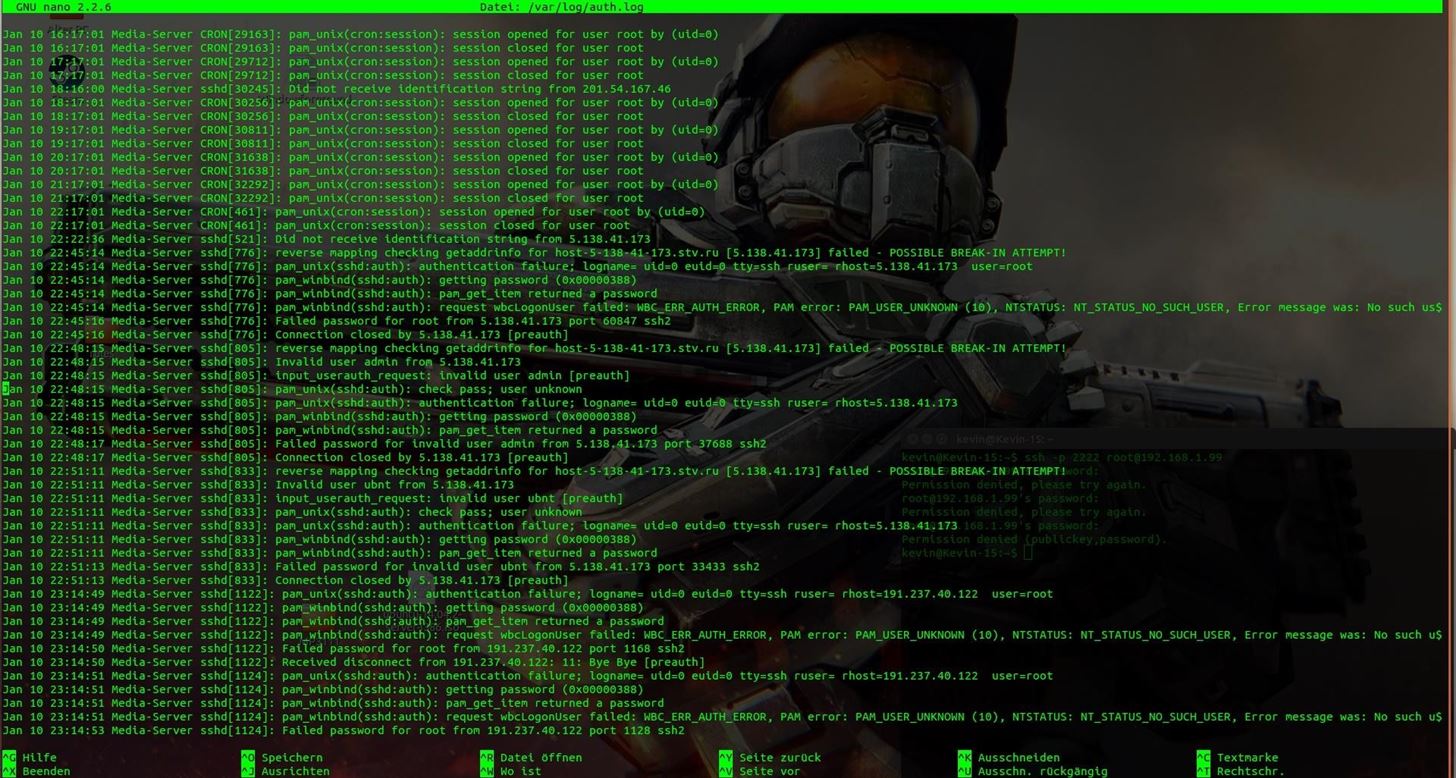
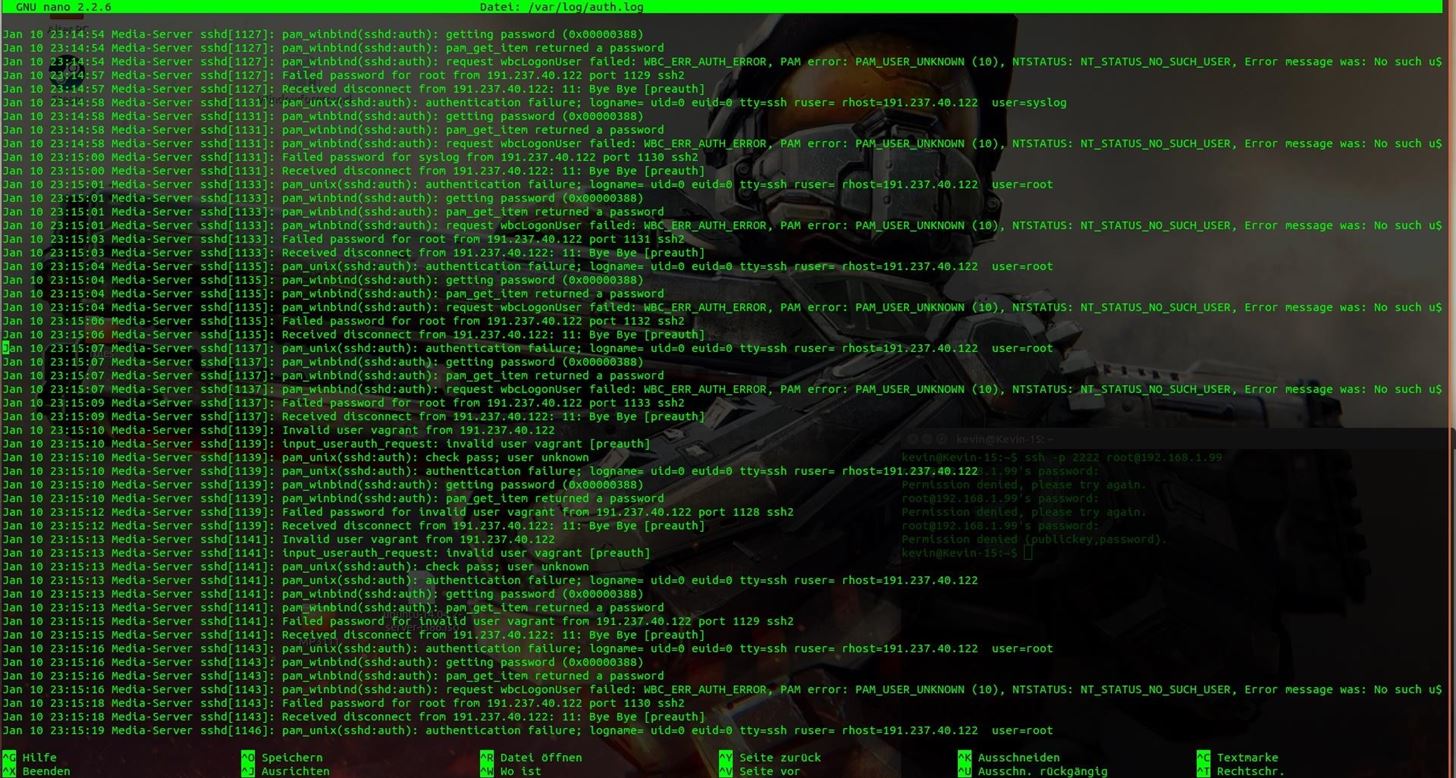
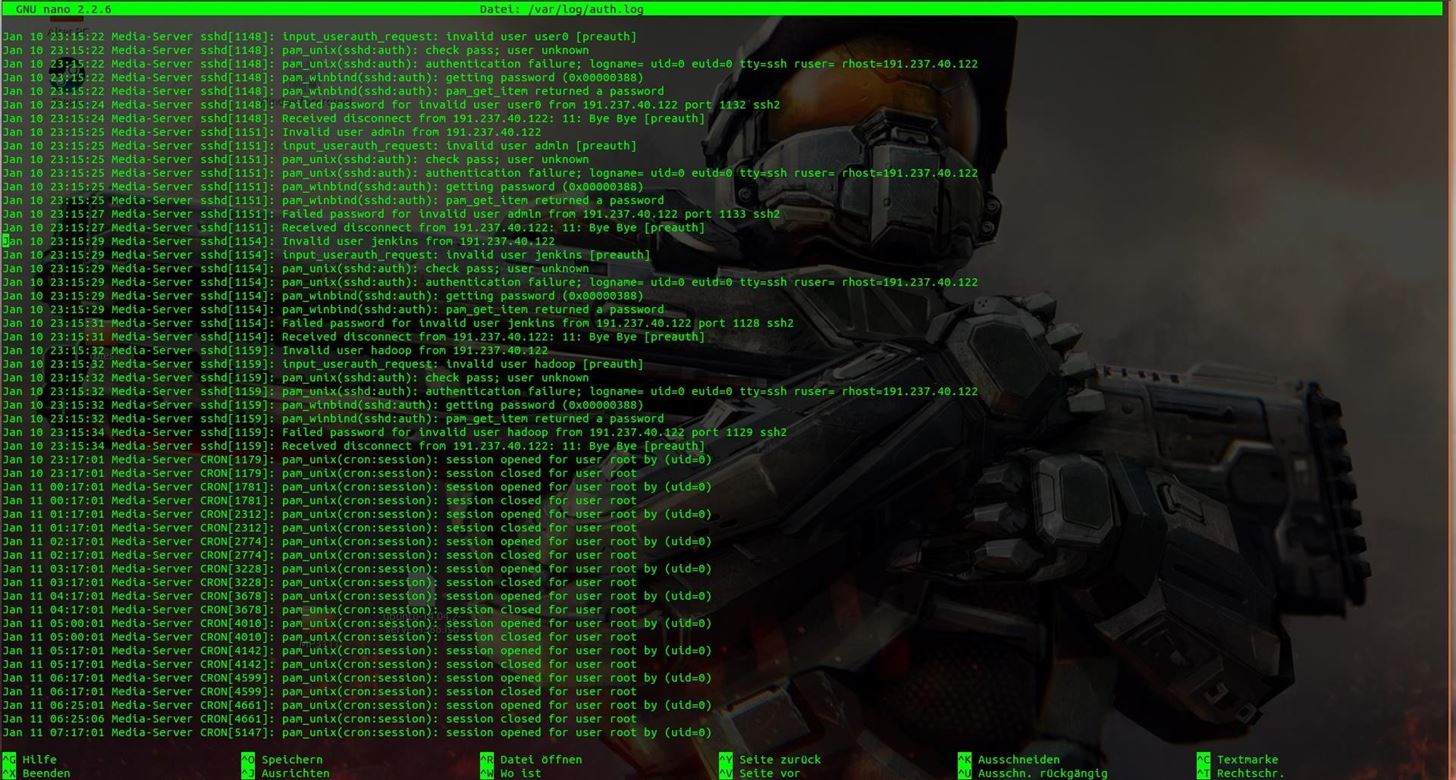
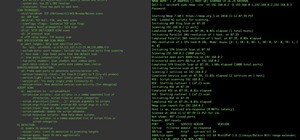
I repaired the Damage and looked at the log file on my Media-Server. This Guy really only Hacked my WiFi but on the Server logs are some Alarming lines. I use an Ubuntu 14.04 Server and I changed after that every standard Port and Password.
My Questions are,
- How can I better secure the Server against Attacks? (specially SSH )
- Can someone tell me please what is going on in my "auth.log"
No IP address in this file is one of mine.
Thanks for any Help!







































5 Responses
First off I would ask if you are sure this was an attack from a neighbor?
Now I would enumerate several steps to protect yourself (yes this is overkill)
Thanks for the great info, BSSID broadcast is already off and I secured the AP so good as I can. This Attacker has never Hacked one of my Server or other Computer (I'm really sure about this).
I know one malicious Name (written in leed or some) in my near (output from airdump-ng)
and I got his MAC-Address but I can not figure out which AP he is using.
I am more afraid of the WAN-Attacks from Russia and elsewhere on my .log.
That's only one Day, the most other days of this log file look very similar and I can not really say if someone made it to Brake in..
This Server is my Media Server and Game Server where Friends should can watch Movies and Play some Games on it (at moment 7 Days to die)
Can you tell me about the Firewall settings with MAC addresses because the most IP-addresses in my Country are dynamic and changes every 24 hours.
Please Ask if you need specific infos.
EDIT: root login and empty passwords are Deactivated for SSH
This is a normal thing, I have a static IP and I regularly watch slow probes on my network. Depending on the time of day it rotates geographic locations. I'm in EST time -5 on GMT and I watch as the day goes by probes from Russia and others. It seems to be the norm that time goes by and locations get switched.
Just know MACs and IPs can be forged. It really comes down to you as the end user at your network. Deny all is a good starting point for all policies, you should always allow only what you know is 'ok'. It is tough providing help with limited knowledge of your network and what you intend to do with your network. But thus is the job of all admins.
Dynamic vs. Static doesn't matter in usual cases, it only comes into play when you have certain use-case scenarios.
there is a LOT of robots that are scanning all the internet and trying to exploit known leaks. The router from your internet provider protect you from all (almost) all of them, but as soon as you start playing with port-forwarding (and weak service listening), you'r also allowing that kind of threat.
I forwarded 3 Ports, one for SSH connection, one for the Media-Server and one for the Game-Server. No port is a standard Port, and every Port I don't need is on the server closed.
I figured out that I can use a public/private key pair instead of the password to get more security for SSH.
Share Your Thoughts