I tried to get a Meterpreter reverse tcp session in WAN to my own second PC, I used my normal Gateway for the Attack Machine and an mobile W-lan hotspot with an Tablet-PC for the Target Machine.
If i understand it right to write the Payload i took as LHOST my public IP and Port 4444, 53, 443, 25, 80 usw... (i tried many ports). I execute the payload on my target pc and waiting for a response in Metasploit but there is nothing happend. After about 3 Days of Google, Testing and more Google im really sad becouse it doesnt want to work over WAN on LAN there is absolut no problem.
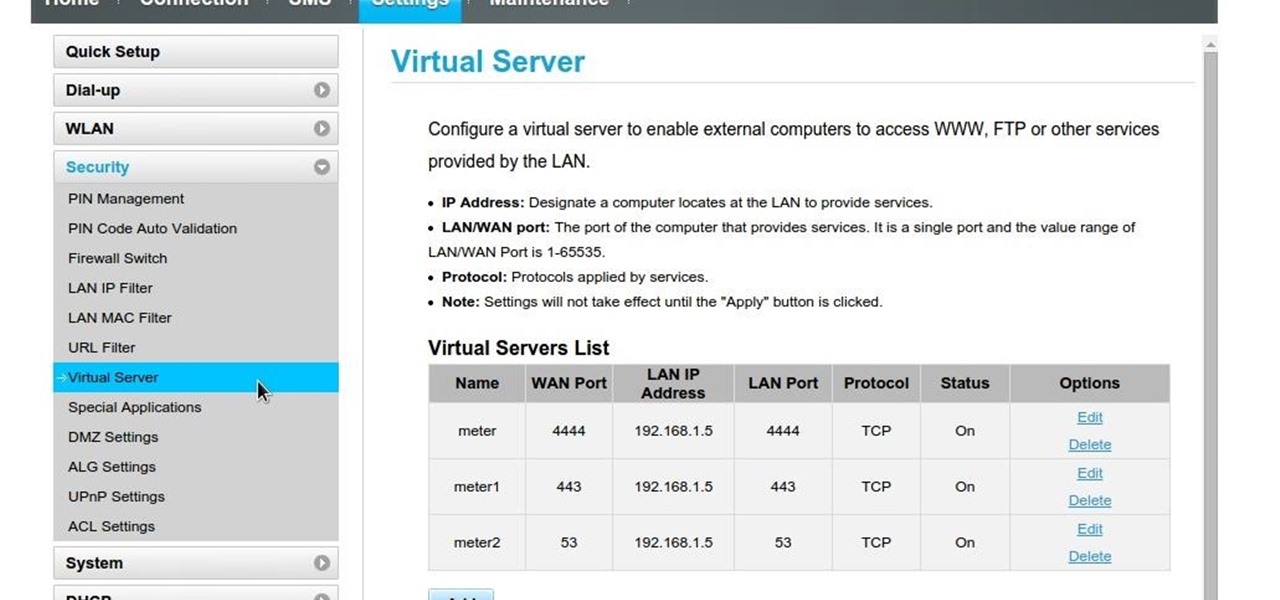
Port forwarding is the key but it wont work, here are few screenshots from my Gateway maybe some of you have a idea. I disabled also the Main switch of the Gateways Firewall to try but nothing changes....
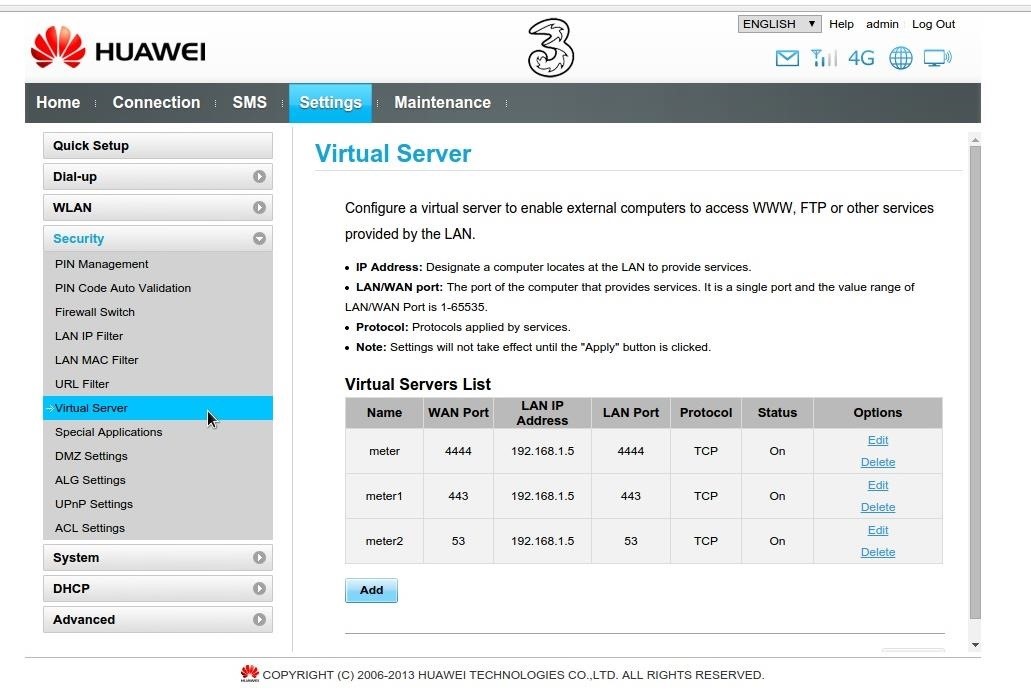
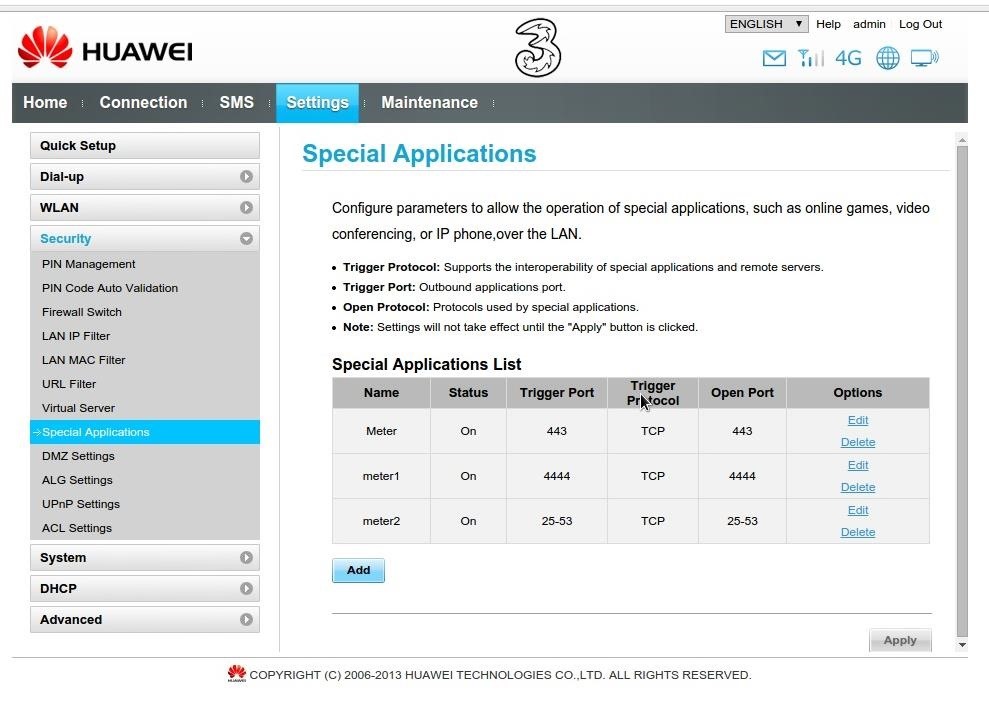
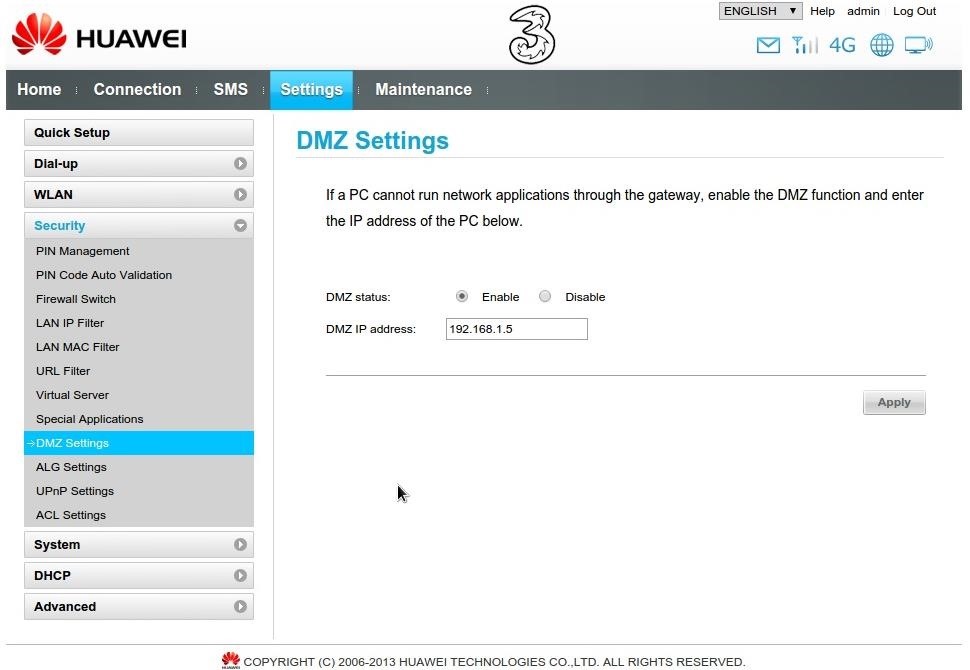
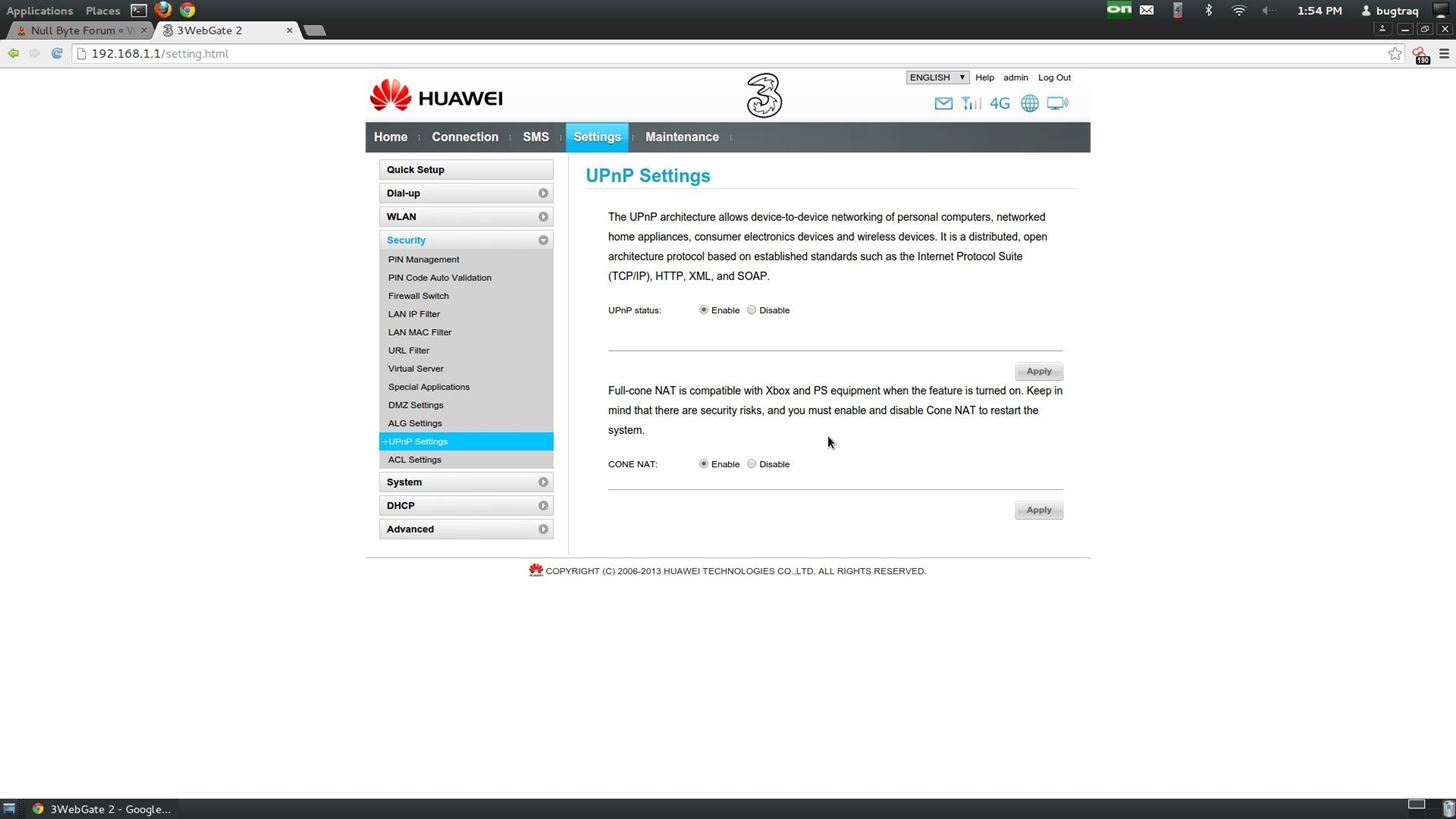
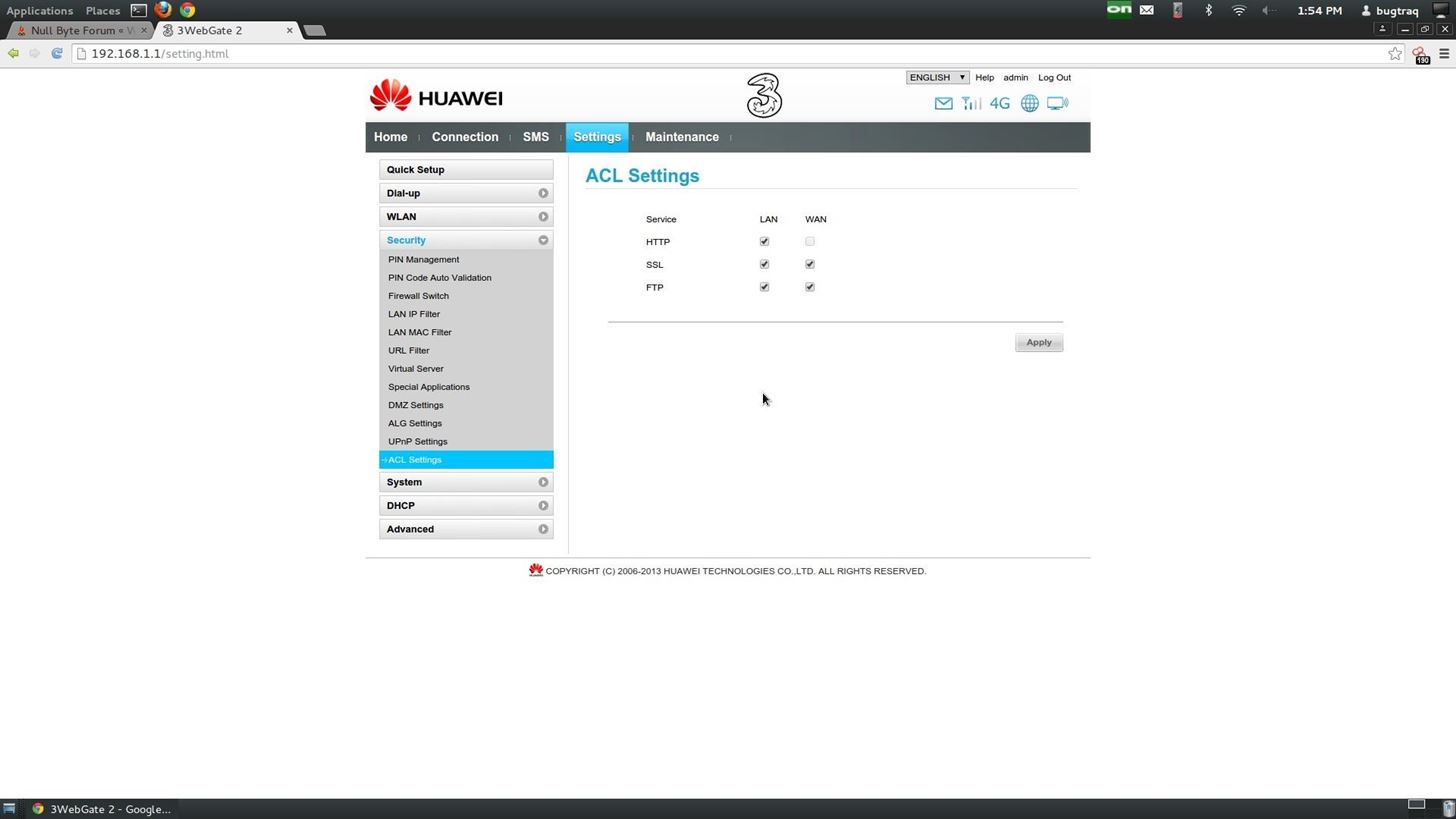
These are my settings and here are a Scan report on my router with nmap the next thing is that also without the enabled firewall on the router i had to set the -Pn option in nmap.
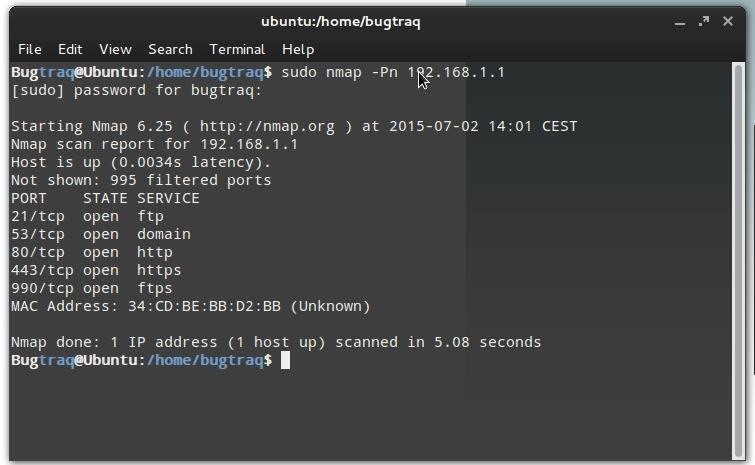
and here a scan of my Attack System
I hope somebody can help me with my problem here are some Details on the Attack i tried:
For the Payload:
windows/meterpreter/reversetcp
LHOST = my public ip
Lport = 443 or 4444 or 53 or 25 or 80
In Metasploit with the multi/handler:
LHOST=192.168.1.5
LPORT= 443 or 4444 or ....usw...
If some of you need another Details only ask but i really need help with this also the port of my Gateway 443 is open but that is new today...
I also configured the MAC address of my Attack system to use a Bridge in the Gateway but really nothing helps.
Thanks for any Reply on my Problem!
Edit:
Other screenshots
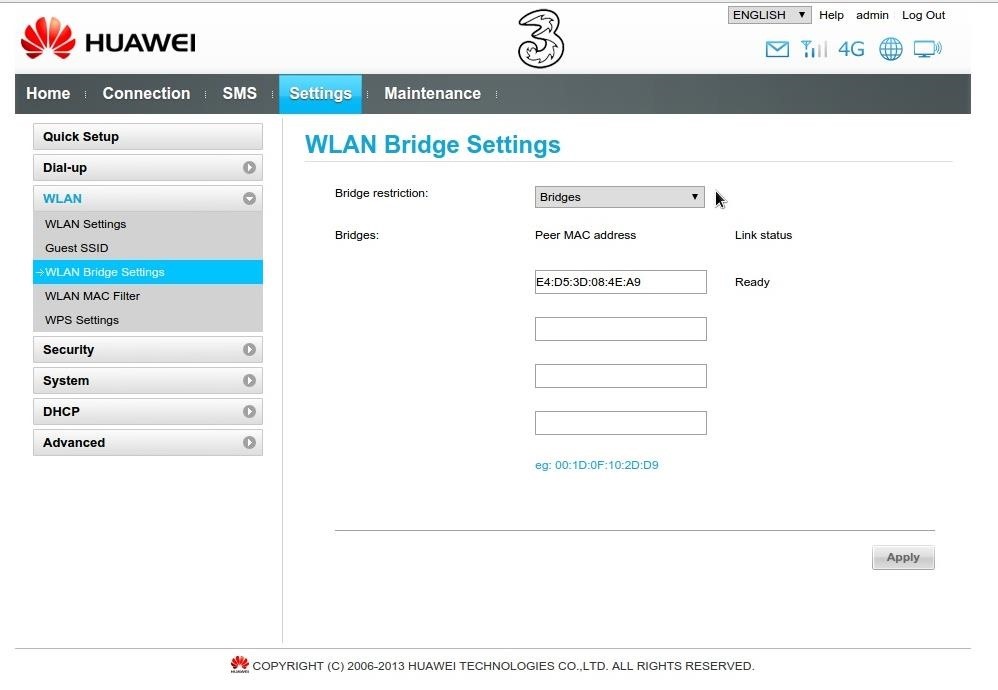








































21 Responses
I had the exact problem like you last year, was also using tab hotspot and also a Huawei router...
Anyway your portforwarding looks correct (like mine), the only thing is suggest is opening the listening port of your attack machine...on the terminal type "sudo gufw" , you might need to install "gufw" via apt-get. It's a graphical firewall interface..
I hope this helps, I'm still new in this field I apologise in advance if i give incorrect information.
Thanks for the Very Fast Help,
I will try it, The Huawei-thing is anoying like hell xD
I got a lot of problems with it since i got it,
and its all only about the ports the first problems was
to open the NAT for the Xbox, i never solved this complete...
I testet it now its a cool Tool and it seems that Port 443 is now open on my Attack system but the payload cannot connect with Metasploit.
So that doesnt work for that problem :(
Is metasploit running on a VM or physical machine?
Is the exploit successful? Meaning can you get a shell across the LAN successfully?
If you run a packet capture during the connection attempt do you see any traffic from the victim to the attacker?
I also don't see a port forward rule in any of your screen shots. What is the model number of your Huawei?
Its a physical machine and yes inside my LAN it works just fine.
I use a Ubuntu 12.04 x64 machine with Bugtraq 2 as Attack machine
and a Win7 x64 SP1 as target.
The modell number is B890-75
I cant find it on portforward.com.
Can you please tell me how i do a packet capture
I couldn't find any exact instructions on that model, but several of the Huawei devices use the virtual server setting for port forward, try that maybe?
Thanks for researching, i also cant find something about it.
I tried it with the virtual server, you can see it on the first screenshot.
I really tried everything I know about networking and got this AP device since 3 years so the screenshots show everything i tried instead of the bridge settings but i can add it.
oh yeah, duh... Sorry.
No Problem xD
Thanks anyway
I can confirm that port forwarding is on the virtual server...
Do this, set up the virtual server to forward to your local IP (lan IP) and lets use port 4455..make sure status says "on"...
Make sure you have port 4455 open via "gufw" and again its status is on(green)..
On terminal type "nc -l localhost -p 4455" and leave it open, go to www.canyouseeme.org and type port 4455, this will confirm you have sucessfully portfowarded and opened the desired port...we can take it on from there
Have you allowed those ports through (Router's) Firewall?
And don't use any port checker tool, they check for open ports Not forwarded. That will be a waste of precious time.
F.E.A.R
Please help me clarify this I'm a bit confused now...
The port checker on this case is on the Internet (wan) and the attack machine is on the lan behind the router..If the port checker sees an open port on the attack machine, wouldn't this mean it would have to go through the public IP to the router then from there to the local IP and see the open port?
Coz if that's the case then can't we say it has also confirmed portforwarding has been done correctly?
Port forwarding and opening ports are two different things: (at least for me)
And we are/were talking about forwarding ports, instead of opening them, but never-mind
If we forward port, it is not detected by any port-checker tool, and hence is far better for security reasons than opening ports.
.
Copy-Paste:
"{Ok some definitions for you.
"Ports" are a 16-bit number that acts like a mailbox / communication channel for your network interface. Every packet received by your system must have a destination port number, and based on this the network stack will know which application to send the packet to.
An "Open Port" is a port that your network device accepts packets on, it may have absolutely nothing to do with the packets and thus the packets may be deleted, but the port still accepted the packet and read its header. A "Closed Port" is a port where your device will either actively refuse (send a response) or completely ignore (no response) packets on. Open Ports can be bad / good depending on your security posture.
Example, Application A is expecting to receive packets on port 3030, your FW / computer is blocking port 3030 and thus Application A will never receive any packets. Conversely malicious code can be hidden inside packets and accepting them on arbitrary ports can cause your system to be hacked and infected. Rule of thumb is to close any ports you don't expect traffic on, only open the ones you know you'll need.
"Port Forwarding" is router speak for NAT Masquerading. What happens is Application A wants to receive packets on 3030 but it's IP address is 192.168.1.10, a private IP address. You Gateway device needs to have an entry put in its table stating that all packets received on port 3030 need to be forwarded to 192.168.1.10 so that Application A can receive them.
Most of this is automatic, but not always.}"
I can only turn on or turn off the Firewall from the router,
So i disabled the Firewall on my Target, on my Attack machine and on my router and it still doesnt work
Can you access internet after turning off that firewall (NAT) from the host?
Yes without a problem,
I have a idea,
so my Attack Gateway and my target Gateway both registered by the same company named "3" on the same Address.
For the Internet Connection my packets getting Routet over an "3" server and there is also an Firewall that indicates this as a uncommon or some malicious connection and blocks the packets?
I tried Traceroute and the Gui-Version of it so when i try to connect with it the Public Ip of my target system it goes over some server and ends everytime by an "3" server in the same City.
Can it that be?
If yes how can i evade it?
which is your country?
in some countries ports are blocked by default and you need to call up your ISP and ublock them
Im from Austria. It works now. My network was behind a Nat and the Firewall from my ISP Blocks every intern connection. There is an Option called open Internet, if you activate it you are alone.
No Firewall and No Nat from your ISP but you can connect from outside to your network.
Also good for everyone who plays multiplayer games becouse the NAT gets deactivatet so it will Display in every game: "NAT Typ: Open"
So you have fixed your problem with port forwarding now?
can you help me please because I'm facing the same problem.
Any help with this issue will be greatly appreciated.. Thanks
null-byte.wonderhowto.com/forum/need-help-with-fatrat-over-wan-0183192/
I have exactly the same issue in 2018 as the Lion. i am using a B315 Huawei Router. I have even changed my ISP AND I am battling to connect.
Share Your Thoughts