What's ARP Spoofing?
ARP spoofing allows an attacker to intercept data frames on a network, modify the traffic, or stop all traffic. Often the attack is used as an opening for other attacks, such as denial of service, man in the middle, or session hijacking attacks.
Why shARP?
Many of us must have used the ARP Guard or any other similar android app that scans for any malicious activities in the network. But for Linux ordinary non-technical people find it difficult to successfully install and run it. Plus, most of them only disconnects the end user from the network if it suspects any form of malicious activity. Thus the end user remains safe but the network along with other devices still remains vulnerable to the attacks.
This anti- ARP spoofing program, shARP, detects the presence of a third party in a private network actively. It has two modes: defensive and offensive.
Defensive mode protects the end user from the spoofer by disconnecting the user's system from the network. This mode also alerts the user with an audio message as soon as spoofing is detected.
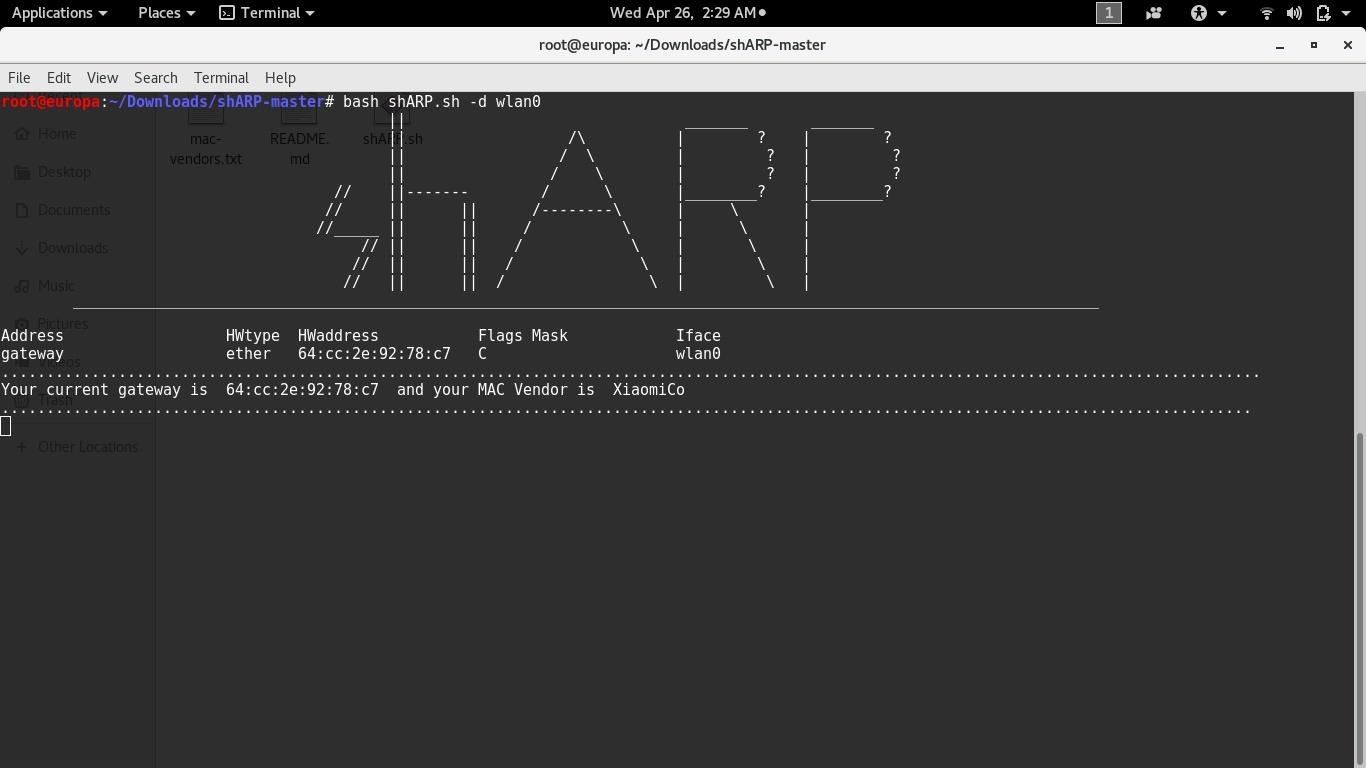
when shARP detects the spoofer it would look like this-
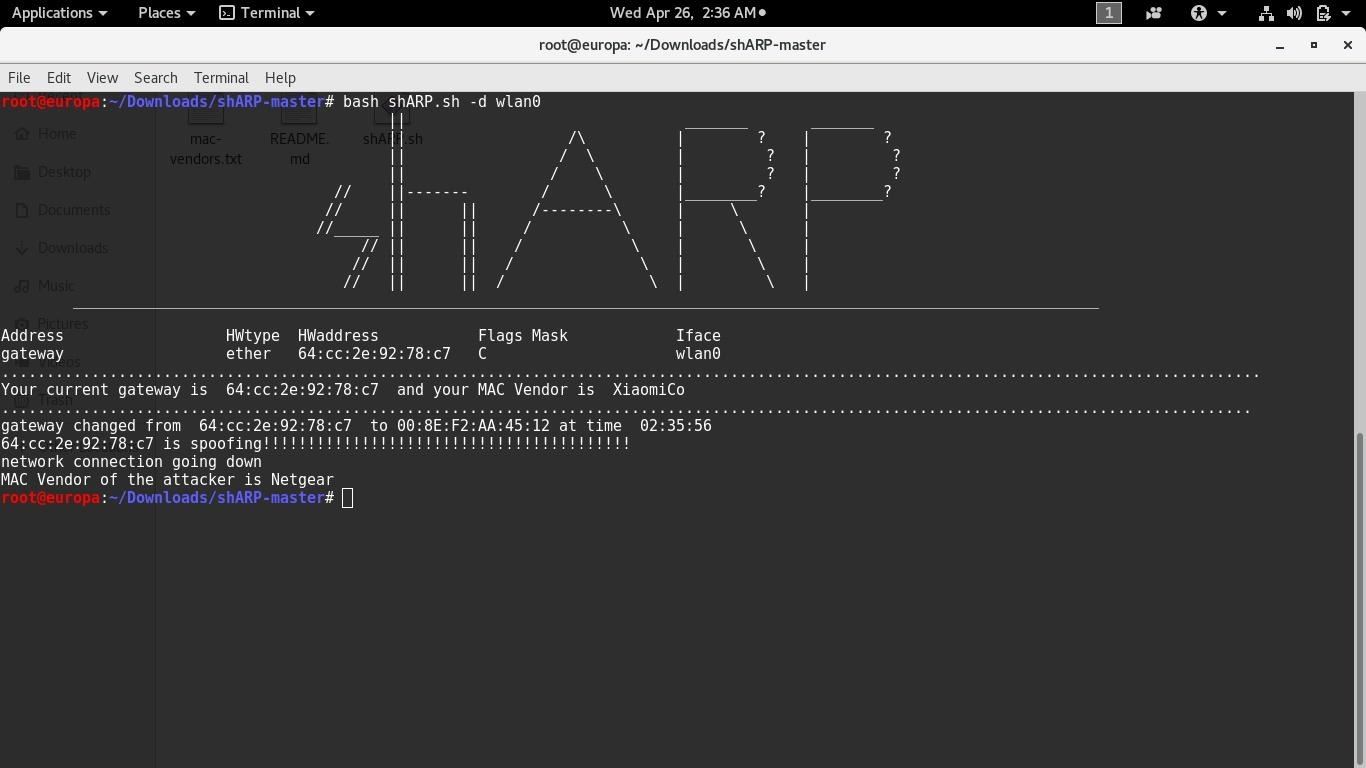
Offensive mode disconnects the user's system from the network and further kicks out the attacker by sending De-authentication packets to his system, this doesn't let him reconnect to the network until the tool is manually reset. For this purpose a third party application Aircrack-ng is required. If it is not present aready in the system, the user is asked to the permission to install the same. The network's bssid and the the spoofer's mac address is passed to the aireplay-ng command which then sends infinite de-authentication packets to the attacker.
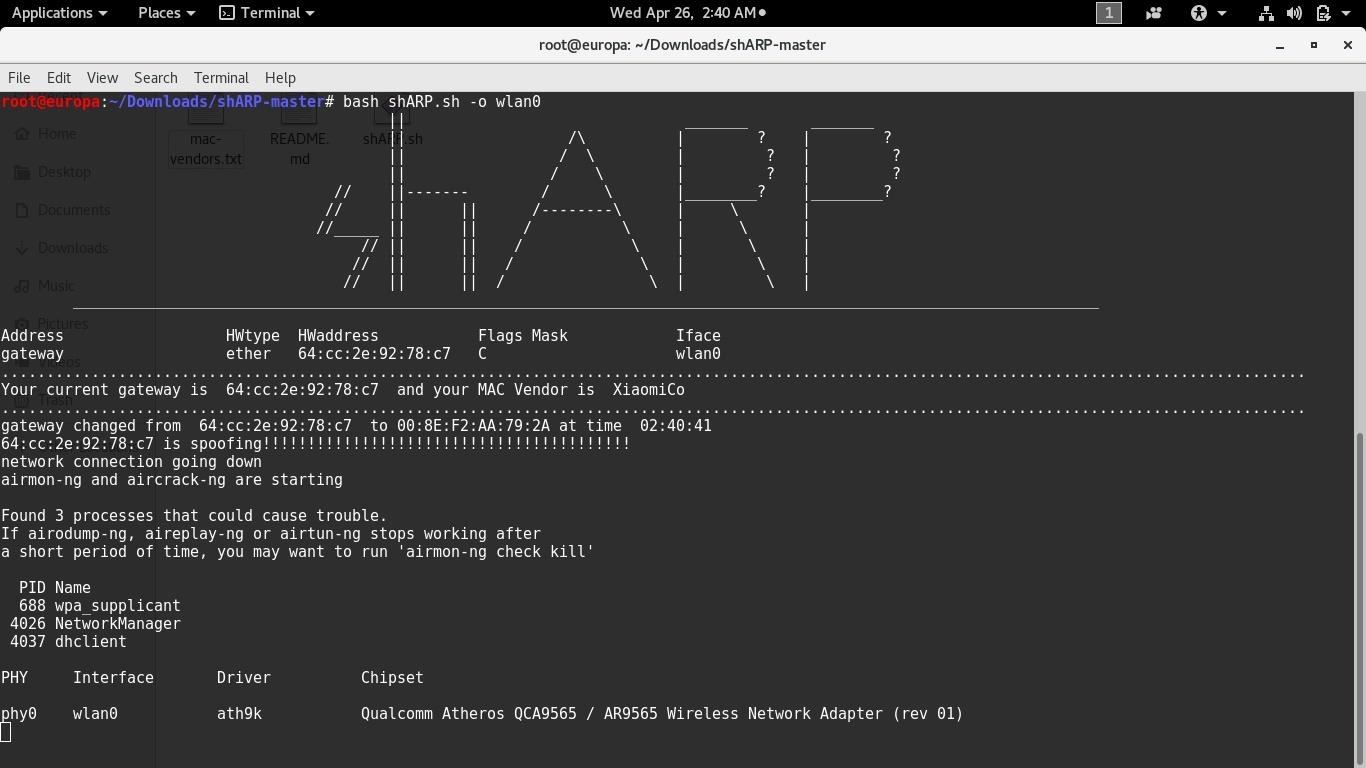
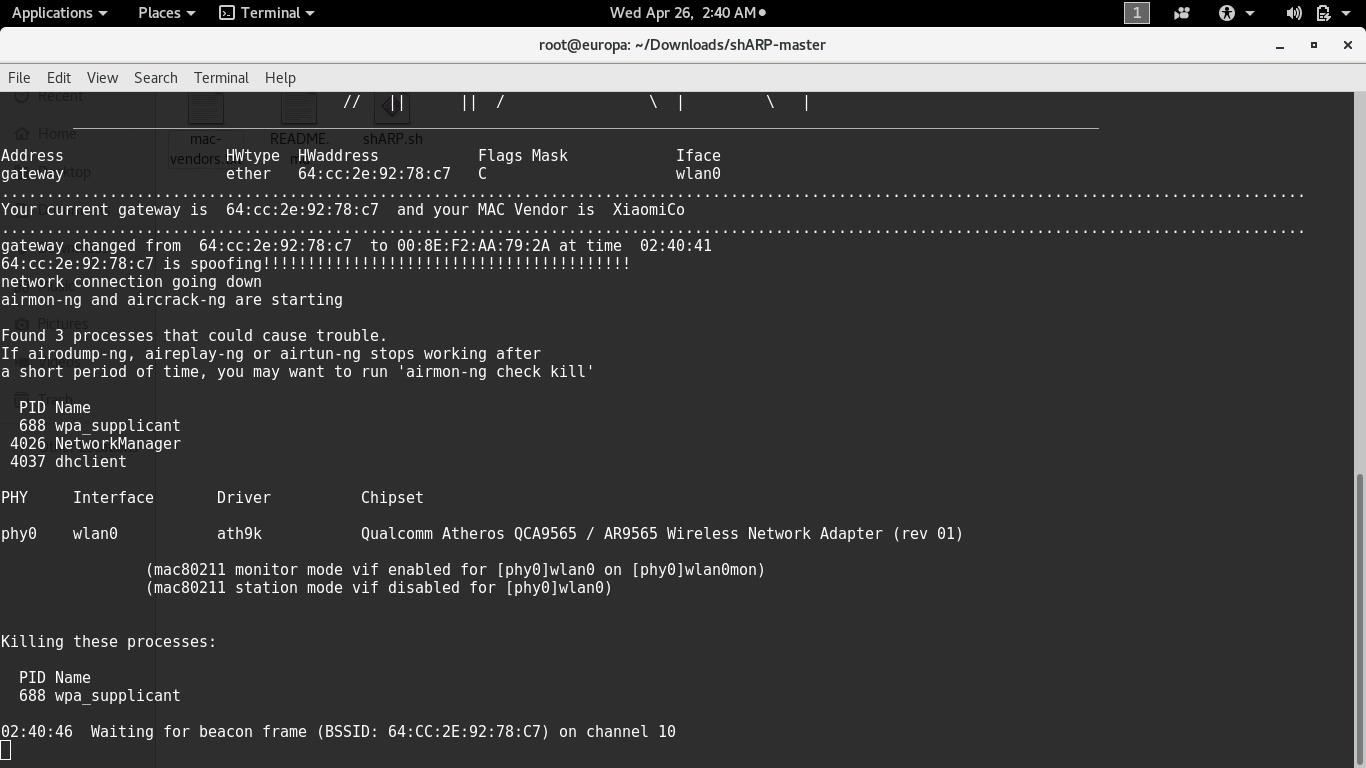
shARP is written completely on shell command. It uses active scanning method to detect any spoofer in the network, meaning that the device on which this software is run constantly refreshes its ARP-table. It then compares the new ARP table value to the original one. This is one of shARP's strongest as well as weakest point.
Whenever a device refreshes its ARP table it consumes a part of the networks bandwidth. Imagine that this process repeats itself after every second consuming the device's bandwidth and CPU cycles. It becomes unaffordable while you are streaming videos or torrents. But the good thing is that it would take action as soon as it detects the intruder/spoofer.
shARP__2.0
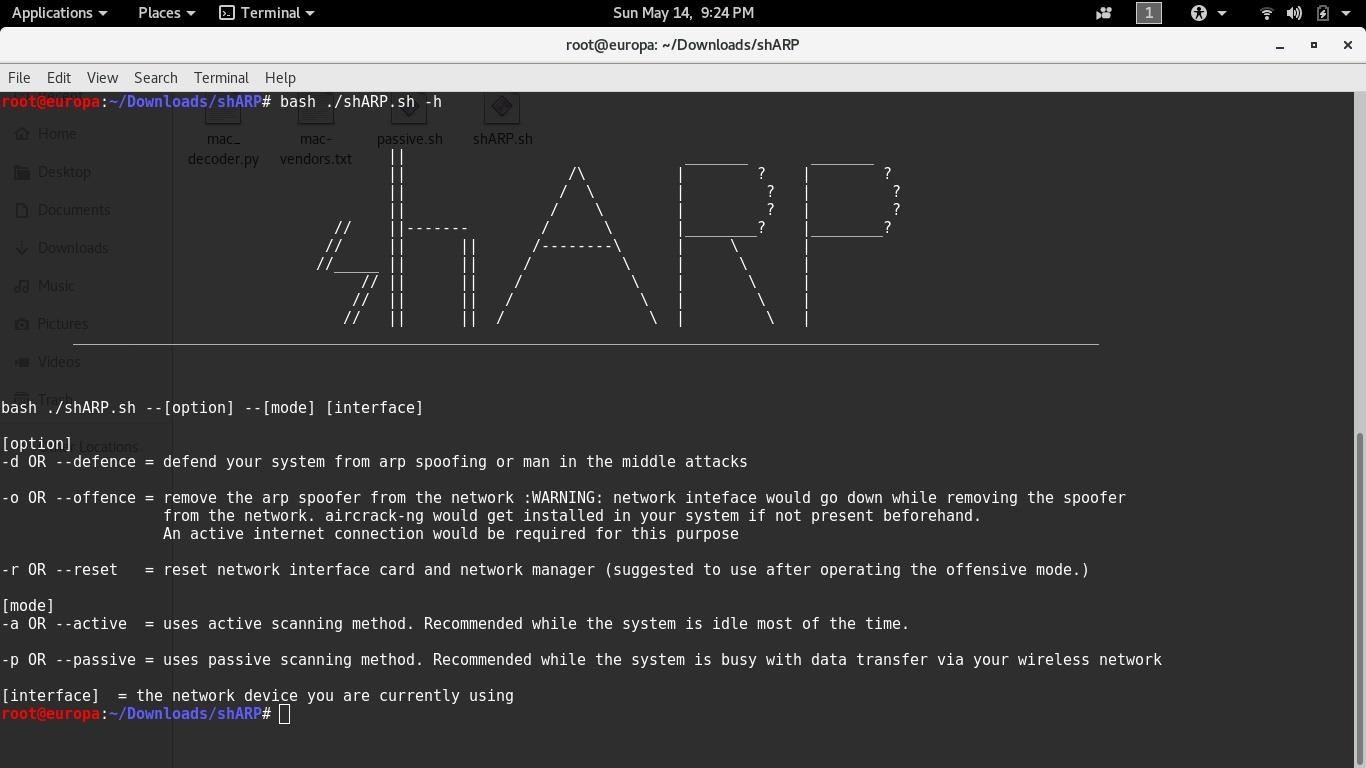
Keeping the cons in mind I released shARP2.0 which provides a passive scanning option, i.e, the device now checks the mac address of the gateway from the packet it receives. Thus, no more extra bandwidth or CPU cycle consumption. Now you can stream videos and torrents without compromising the speed,privacy and security. I would recommend using this option when there is constant packet flow between your device and the gateway. shARP2.0 is partially written on python 2.7 and the rest on bash.
One of the major flaw in this method is that when shARP is running in this mode it wont be able to protect the network and the end-user if there is no packet transfers or if the system is idle.
Records
The program creates a log file in /usr/shARP/ containing the details of the attack such as the attackers mac address, mac vendor, time and date of the attack. We can identify the NIC of the attacker's system with the help of the obtained mac address.
Download Link - https://github.com/europa502/shARP
Updates-
I'm working on the next update for shARP which would have the goodness of active and passive scanning methods. Till now what I have proposed is that the software would basically run on combination mode. Depending on the network traffic shARP would switch between the active and passive modes, thus providing the best experience and security from ARP-spoofers to the end users.
Some of the users also pointed out that I should give an option for automatic end-user disconnection. I'll add them too.
One of the major issue with both of the versions of shARP is that you need to turn it off when you are switching the networks.
Since there are some prerequisites (python 2.7.x , aircrack-ng) I also intent to compile the program.
Please fell free to point out the flaws and bugs in this tool. Open issues on github. And if you feel like it should be more user friendly and easy to use or maybe it lacks functionalities please do comment and let me know. : )
Note :
I won't suggest using this software over wired connections, especially in offensive mode as it might cause network instability.
Use the offensive mode only with the NICs that supports monitor mode.
Offensive mode does DOS attack on the ARP-spoofer. So use Offensive mode only after making sure that you have appropriate right over the network and the devices connected to it and make sure that doing so is legal in your Country/State.








































Be the First to Respond
Share Your Thoughts