Hello, today I am going to show you how to crack passwords using a Kali Linux tools.
Remember, almost all my tutorials are based on Kali Linux so be sure to install it.
I am going to show you these :
1. Cracking Linux User Password
2.Cracking Password Protected ZIP/RAR Files
3.Decrypting MD5 Hash
4.Using Wordlists To Crack Passwords
Lets begin.
Cracking Linux User Password
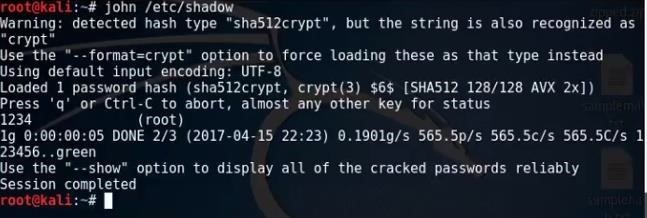
The linux user password is saved in /etc/shadow folder.
So to crack it, we simply type :
john /etc/shadow
It will take a while depending on your system.
Cracking Password Protected ZIP/RAR Files
First, go to the directory of the file.
I will assume that everyone here can do that.
After, use this command :
zip2john zipfile > output.txt
(If it is a RAR file, replace the zip in the front to rar.)
Replace the "zipfile" with the name of the zip file you are trying to crack and replace the "output.txt" with any name that is a .txt format.
After that command, you will see that it would have maked a text file.
The hashes are stored in that file.
To crack the hash, type :
john --format=zip hashfilepath
Again, replace the "hashfilepath" to yours. Mine is just an example.
Now, wait, and you can see it is cracked.
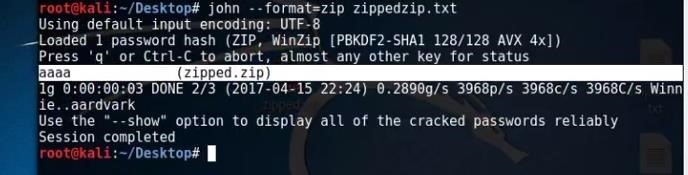
Now go in the zip file and put the password.
Decrypting MD5 Hash
I have my Hash over here :
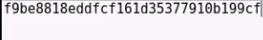
Now, lets use john to decrypt it.
To decrypt it, use this :
john --format=raw-md5 hashfilepath
Again, repl......
I won't say it.
And now enter, and should take a while and it will decrypt it.
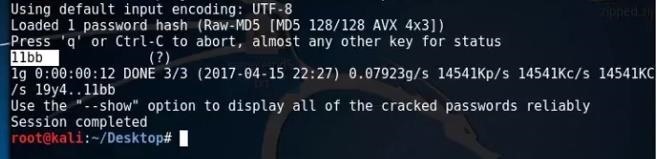
And boom.
Using Wordlists to Crack Passwords
I don't really recommend this one, but there are some peoples out there using this to crack...
I will crack a hash that is inside a text file.
I have a wordlist here, and I named it password.txt.
To use the wordlist and crack the file, do :
john --format=raw-shal --wordlist password.txt THEHASHFILE.txt
You know what you gotta do.
Any Errors?
If you got any errors, comment down and I will try to help you out.
Remember that you need john the ripper to do this.









































14 Responses
Nice! But in the wordlist one, doesn't it take more time to do the process?
No, if it is in the list, it will be more efficient, and if you want to crack lots of hashes at once then make sure your laptop has a fan since that uses 100% CPU, and it might fry.
No, not if you have a targeted list. I tested this on a password protected rar file i had someone create. I extracted the hash & ran john againt it. It ran for a solid 36 hours attempting a bruteforce in iteration mode. John never found it. Using a custom list I cracked the hash in 36 minutes.
sir how to change default threshold.. ans me as soon as possible
Hy all!
I need some more help with john. I used it with aircrack -ng testing on my wifi, my password is picciotto18. Here is the command I use:
sudo john -w=/home/nicola/diznic.txt -rules: --session=attack1 --stdout | aircrack-ng -b E0:CB:EE:7A:CA:DB Pichini*.cap -w -
I use a wordlist diznic.txt, but I still don'understand how to teach john which kind of pw try: if in wordlist I write exactly picciotto18 aircrack obviously got it, but if I add in wordlist only picciotto and some numbers (0-9) john tried some mix as picciotto1, 1picciotto, etc, but it don't mix until picciotto18.
If I know the mask of a password (a-z,A-Z,0-9, length 8 for example), how to teach john to try all mix? How to write a good wordlist to make it start trying?
A step-by-step guide will be appreciated, I- have read many tutorial but still didn't find my exact issue. Thanks in advance.
I will say good but for the beginners they wont understand try to explain more but good job
root@kali:~/Desktop# zip2john test.zip
test.zip:$zip2$030be99d6ab9f06add800000000000000002c26ffffffe4ZFILEtest
.zip052ffffffffffffffffffff$/zip2$:::::test.zip
root@kali:~/Desktop# zip2john test.zip > hash.txt
root@kali:~/Desktop# clear
root@kali:~/Desktop# john --format=zip hash.txt
Created directory: /root/.john
zip-aes file validation failed Not enough data in .zip file test.zip, to read the zip authentication data. Hash is $zip2$030be99d6ab9f06add800000000000000002c26ffffffe4ZFILEtest.zip052ffffffffffffffffffff$/zip2$
Using default input encoding: UTF-8
No password hashes loaded (see FAQ)
root@kali:~/Desktop#
please help me..
i recevied error like this john the ripper
Hello!
I got a problem, the .txt is generated with no hash files... What should I do?
Make sure that you have assigned the correct hashtype whrn using --format='hashtype'
Otherwise john will not recognize the hashes in the file.
How to hack a rar file with John the Ripper in termux
In the section where you show how to use a wordlist the syntax is incorrect.
john --format=rar5 --wordlist=hak5.txt hash.txt
In your example the '=' is missing. The command will run as you typed it, but it will default to john-the-ripper's default wordlist instead of the one you have designated in the command.
Hi, I get this:
$ sudo john 24229_1585779530.hccapx > crackme
2020/04/01 21:07:47.977242 system_key.go:126: cannot determine nfs usage in generateSystemKey: cannot parse /etc/fstab: expected between 3 and 6 fields, found 7
fopen: 24229_1585779530.hccapx: Permission denied
C:\Users\Divu\Desktop\John\run>john --format=zip crack\pass.txt
Using default input encoding: UTF-8
No password hashes loaded (see FAQ)
please help this is the erroe I get when Using --format
when i used --incremental or show command on pass.txt it shows 1 hash to crack
please help me with this problem
Is there a way to do the same with archive created with "zip -e archive.zip file1 file2 file3"
And every file has its own encryption key.
Share Your Thoughts