I'm using MITMf to capture passwords and usernames, hence i'm playing around with the MITMf, because i've read that it's the only tool which has SSL+(2) and Dns2proxy, which i'll need to bypass HSTS.
So i've read byt3bl33d3rs blog (Which i find very useful!) and Ciuffys https://null-byte.wonderhowto.com/how-to/defeating-hsts-and-bypassing-https-with-dns-server-changes-and-mitmf-0162322/ post about defeating HSTS and Bypassing HTTPS.
Now i'm stuck. quite stuck actually, since i'm not getting any error codes and it looks like it should work, however it doesn't.
I've ip forwarded; sysctl -w net.ipv4.ipforward=1
and i should've put my card in promisc. mode (Not monitor mode!) ifconfig wlan0 promisc
and mitmf is not "doing anything" - and now i feel quite silly, because i don't know the "next step".
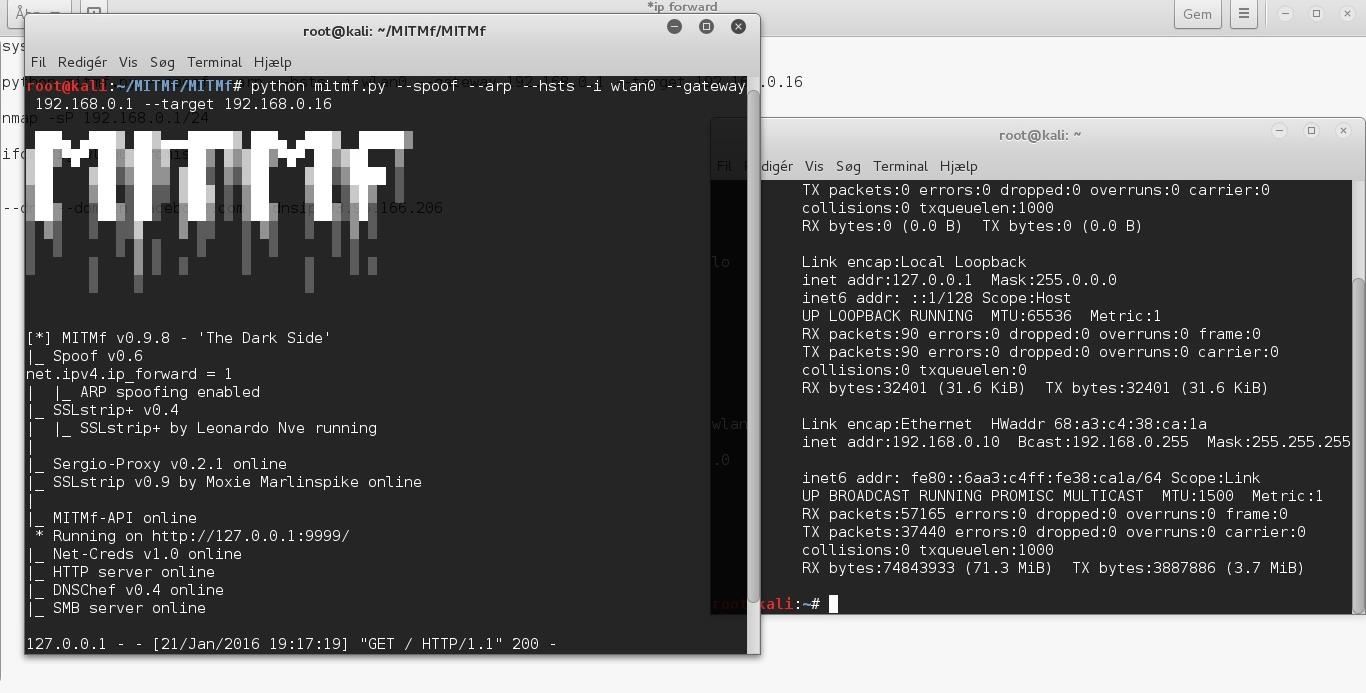
at 127.0.0/9999 it gives me this:
{"ScreenShotter": false, "BrowserProfiler": false, "Upsidedownternet": false, "FilePwn": false, "SMBAuth": false, "BrowserSniper": false, "Responder": false, "SMBTrap": false, "JSKeylogger": false, "Replace": false, "SSLstrip+": true, "Inject": false, "Ferret-NG": false, "HTA Drive-By": false, "Spoof": true, "AppCachePoison": false, "BeEFAutoloader": false}
so SSLstrip+ is true and Spoof is true.
Everything is online, however - nothing is working. Maybe i should specify that the client is a macbook running safari, however even when i go to a non https page, it's not sniffing anything with sslstrip.
Again, i do feel stupid about asking this questing, so any answers are greatly appreciated! Thank you in advance.








































38 Responses
"at 127.0.0/9999 it gives me..."
Do you mean 127.0.0.1 (localhost)?
Yes, sorry - I forgot the .1 :-)
It says that the MitmF-API online is running on HTTP://127.0.0.1:9999
Did you install it with byt3bl33d3rs instruction? If not try do install itliek the says.
Cheers,
Washu
Yes, I've actually installed the one Ciuffy fixed, and everything is up to date.
Do what these two people suggested. You also seem really knowledgeable and I haven't seen you before. Welcome!
Thank you!
This is how questions should be asked. I can't help you with this one though.
Exactly! I was thinking having OTW use this a real life example.
Then examples of what not to post: https://null-byte.wonderhowto.com/how-to/crack-password-0168032/
Haha, well it IS 7 years old ;-)
Wouldn't mind OTW using this as a real life example, i've tried it with Safari on a macbook and a system running windows 8 with Chrome.
It's frustrating when it's just sitting there. Doing absolutely nothing. Would be "easier" if it would just give me some kind of error!
The post I linked was removed. Magically it takes you to a link with a similar title.
The one with the id of 0168032 was someone who posted "How crack passwords" and a body of something like "hack please".
Have you tried using less parameters? Try to run MITMf without spoof and arp, only the extremely basic. Since you can access the API page we know that the core of MITMf is working.
When accessing a page make sure that you haven't accessed that page before since it may be cached on your computer and obviously make sure that its only HTTP.
I think that MITMf is actually working and the issue dont have anything to do with it. Do you have a different device/browser you can try?
Cheers,
Washu
I've tried it again today on a windows 8 systen, running chrome. Again - nothing happened, and i did try it without the spoof and arp. Nothing.
I tried with the "regular" MITMf, and got this response: 2016-01-22 19:09:39 ARPpoisoner Unable to resolve MAC address of 192.168.0.16
2016-01-22 19:09:42 ARPpoisoner Exception occurred while poisoning 192.168.0.16: (4, 'Interrupted system call')
I tried yesterday with ettercap, and it did the arp poisoning, and tried to do the DNS spoofing, but couldn't bypass the https. - So my network card should be working.
Try it on a HTTP site that you haven't visited before so that it isn't cached. Also can the target still access webpages when they're spoofed? Or is the internet completely blocked off from them? Also what is "regular" MITMf?
Cheers,
Washu
And i really do appreciate you trying to help, thank you for all your suggestions, they are most welcome!
Sorry, when i wrote the regular MITMf, it's because i'm using the mitmf.py, so i tried with just mitmf.
I tried it with an http site that i hadn't visited before, like you suggested, still nothing. It's not sniffing or anything. There's litterally nothing.
The internet is not blocked off.
I think i'll uninstall it, and try installing it once more.
I just deleted all MITMf.
Installed the fixed one from:
git clone https: //github.com/CiuffysHub/MITMf
Tried it again. Still nothing.
Maybe it's an issue with Ciuffy's install? Try following these instructions. They are the official ones from the author.
Once that's done try to run Wireshark and monitor the ips that are targeted, do you see your fake are packets? Do you see any traffic that comes from mitmf?
Also make sure that your entering the right ips, I know it a stretch but I've seen worse ;)
Cheers,
Washu
Could be that's its an issue with ciuffys install! I'll give it a go with the one from byt3bl33d3r, and try running wireshark as you've proposed!
The installation from byt3bl33d3r had a lot of issues when installing, however, at the end it did seem to install everything correctly.
BUT! It's the same issue, nothing is happening, which makes me think - i'm definitely doing something wrong, i've installed something wrong, or just using it incorrectly. Nothing was happening in wireshark.
Afterwards i tried with ettercap - something did happen in wireshark (i'm not very familiar with wireshark, hence I can't be sure what it did capture, but it did capture something, however it seemed encoded or restricted), and safari detects that i'm trying to DNS spoof, when using ettercap.
I'm now at the conclusion - I'M doing something wrong or have installed something wrong - because nothing is really starting up, even though the program says it is open and online.
Maybe it has to do with your network card mode? Try 3 things; first running it and using airmon-ng to put the card in monitor mode. Then try in promiscuous mode. Finally, try running without any special modes. I don't know if it will make a difference but maybe it will reveal something we missed. Also make sure that your running Wireshark during these test so that you can see what is happening.
Cheers,
Washu
I'll give that a shot tomorrow!
hmm I could try doing what you are to test things. I am not super familiar with MitMf. Give me a bit :D
Haha, that would be super ;)
I'm not to familiar with it either.. Since I can't get I working ;P
you have forwarded it to true in your primary PCMCIA device. Just create a monitor and forward it instead.
Im not entirely sure what you are suggesting, would you mind elaborating?
Firstly i tried with putting my Wlan1(network adapter) in promisc mode - nothing happened. Same with Wlan0, nothing happened.
I then tried putting Wlan1 in monitor mode and then this happened:
Message from syslogd@kali at Jan 23 14:42:33 ...
kernel: 2369.550621 unregisternetdevice: waiting for wlan1 to become free. Usage count = 52
2016-01-23 14:42:33 ARPpoisoner Exception occurred while poisoning 192.168.0.23: Errno 19 No such device
2016-01-23 14:42:34 127.0.0.1 DNS Could not proxy request: Errno 101 Network is unreachable
2016-01-23 14:42:34 127.0.0.1 DNS Could not proxy request: Errno 101 Network is unreachable
The info was this:
wlan1mon IEEE 802.11bgn Mode:Monitor Frequency:2.457 GHz Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:off
and it puts my wlan in
wlan0 IEEE 802.11bgn ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=15 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Encryption key:off
Power Management:off
it disconnect me from the internet, it shows that's it connected, but it's not (Which it does when it's in monitormode, right?)
Then i tried putting my Wlan0 in monitormode - and then this stuff happened in MITMf:
2016-01-23 14:52:14 ARPpoisoner Exception occurred while poisoning 192.168.0.23: Errno 100 Network is down
Exception in thread NetCreds:
Traceback (most recent call last):
File "/usr/lib/python2.7/threading.py", line 810, in _bootstrapinner
self.run()
File "/usr/lib/python2.7/threading.py", line 763, in run
self._target(self._args, *self._kwargs)
File "/root/MITMf/core/netcreds.py", line 49, in sniffer
sniff(iface=interface, prn=pktparser, filter="not host {}".format(ip), store=0)
File "/usr/lib/python2.7/dist-packages/scapy/sendrecv.py", line 577, in sniff
p = s.recv(MTU)
File "/usr/lib/python2.7/dist-packages/scapy/arch/linux.py", line 485, in recv
pkt, sall = self.ins.recvfrom(x)
error: Errno 100 Network is down
ERROR: --- Error in child 1760
Traceback (most recent call last):
File "/usr/lib/python2.7/dist-packages/scapy/sendrecv.py", line 89, in sndrcv
pks.send(p)
File "/usr/lib/python2.7/dist-packages/scapy/supersocket.py", line 34, in send
return self.outs.send(sx)
error: Errno 100 Network is down
ERROR: --- Error in child 1761
Traceback (most recent call last):
File "/usr/lib/python2.7/dist-packages/scapy/sendrecv.py", line 89, in sndrcv
pks.send(p)
File "/usr/lib/python2.7/dist-packages/scapy/supersocket.py", line 34, in send
return self.outs.send(sx)
error: Errno 100 Network is down
2016-01-23 14:52:22 127.0.0.1 DNS Could not proxy request: Errno 101 Network is unreachable
And it keeps going like that.
In wireshark with Wlan0mon it's only getting proberequests, when it's in monitormode.
I've tried on two different devices, the second device i got this:
Message from syslogd@kali at Jan 23 16:31:35 ...
kernel: 1335.211518 unregisternetdevice: waiting for wlan0 to become free. Usage count = 78
2016-01-23 16:31:37 ARPpoisoner Exception occurred while poisoning 192.168.0.17: Errno 19 No such device
2016-01-23 16:31:39 127.0.0.1 DNS Could not proxy request: Errno 101 Network is unreachable
However no child error.
I ran tests to make sure that my wireless card supports monitormode, and it should!
24:00.0 Network controller: Qualcomm Atheros AR9285 Wireless Network Adapter (PCI-Express) (rev 01)
I've just ran the latest update for my kali system, i'll give it a reboot and try again tomorrow.
What is wlan0 and wlan1? Which one supports monitor mode? Is one of them a wifi usb dongle? What command did you use to put them in monitor mode? What are their names after the go into monitor mode? Did you try running MITMf without changing the wlan mode?
Cheers,
Washu
Washu what you asking is like a toddler barely walking asking how to fly a Airbus . Start with basics using ifconfig iwconfig airmon-ng etc and then you realize you dont need to ask silly questions . Someone asking about MITMf knowing practically nothing about basics is a bit too much ! Have a good one
if you just google your question "what is wlan0" you would avoid embarrassment and actually learn something . Instead all you show is LAZINESS ...
Hahahaha Padma
shut up already, you didn't even understand Washu's question
You seem to have misread the comment- Washu is asking what is wlan0 configured for, not what a wlan0 is. Ironic that you call them lazy but haven't read their comment yourself. Remember, people in glass houses shouldn't throw stones...
Thank god someone realised... Washu clearly knows what he's talking about.
Anyway... a lot of things can go wrong with MitMF. Try doing it with two different systems connected on the same network, ensure that you're typing in the gateway and target IP correctly. (Make sure the target IP is the local IP and not the public one). Also, MiTMF doesn't work on Internet Explorer. Make note of that. Ensure you're deleting your history and clearing your cache (cookies have an annoying way of storing websites you've previously been to!) Also, MitMF doesn't work on HSTS websites (eg. google, facebook, etc.) Hope this helped! Sorry if I've repeated stuff from other people; I didn't have the time to read everything.
The network is set to not be able to view other clients. Thats what I think is the problem. I could be wrong though, but that is how i set up my network at home and i am no longer able to successfully do mitm
Double check your port is working which was forwarded.
And why are you forwarding a port?(To wan?).MITM attacks are conducted over lan.use ettercap or bettercap it's easy and fast.
I am also going through the same problem and also found out that this problem is occuring with newer versions of chrome(chrome 63) firefox , safari amd many more may be these browsers have become enough smart to detect MITM attacks
it.slashdot.org/story/17/09/10/1928232/google-chrome-will-soon-detect-man-in-the-middle-attacks .
correct me if I am Wrong
Share Your Thoughts