This topic covers cryptography, a topic and body of knowledge that you will encounter over and over again during your career as a ethical hacker(pen tester),black hat hacker(bad guys),IT person or security manager. Having a firm grip of the technology and science is indispensable because cryptography is critical in so many areas.
Cryptography is very specific science - it relates to the protection and immunity of informations, I like it because of complicative structure of each bit. Cryptography provides you with a means of keeping informations away from prying eyes and gives you a way to keep the same information intact.
This science provides a unique set of abilities that have been around as long as human have wanted to share informations with some people, but not with others.This science has evolved dramatically over time, but its underlying goal has never changed, though the tools have.
In the field of cryptography, the topic of encryption gets by far the most attention and can probably be said to be the "SEXY" form of the art :)
- You will encounter cryptography in many forms throghout this topic, it is applied at to many different technologies and situations.
- Before we step on headlines, we must understand and affirm some informations.
- So how does it work?
- Plaintext/Cleartext is the original message, it is not altered; it is usable information
- Ciphertext is the opposite of plaintext, cyphertext is direct derivate of plaintext and crypto key, example: a+123=3a12 ; it is a message or other data that has been transformed into a different format using mechanism know as algoritm. It is also something that can be reversed using an algoritm and key.
- It's good to be familiar with decimals,letters and binarys if you wanna play with encryption and decryption :)
- Encryption is dichotomized in two reons, symteric and asymetric.
Human being or computer(super computer) uses key or one pair of keys to encrypt information.
-Key can be public and private
- Public key can be shared on internet if I use asymteric encryption, because it is safer than symetric, we will take a look on this later, or I can send to my friend key and stay more safer - it's okay to share in public if you use asymetric encryption.
- Private key is a unique symbol, it's essential for asymteric encryption, private key in used just by one person,remeber that.
- Symetric encryptions uses one pair of identical keys for encrypting and decrypting information, we can describe it like green grass on my side of street, and green grass on your side of street. One example:
I use two pair of keys to encrypt info and you will use same pair to decrypt info when it be received to you, logicaly keys have to stay private if you wanna integrity of information. With my experiece I can say - symetric encryption is very fast, but unsafe.
- Asymetric encryption uses one pair of different keys for encryption and decryption, we can share public key on some websites on internet, but private key have to stay private. In this case public key is not enought to decrypt information. For every person private key is different.
- Okay let's take a look on some examples where is cryptography applied:
- PKI - Public key infrastructure
- SSH - Secure Shell protocol
- Authentication
- SHA - Secure hash algoritm
- SSL - Secure sockets layer
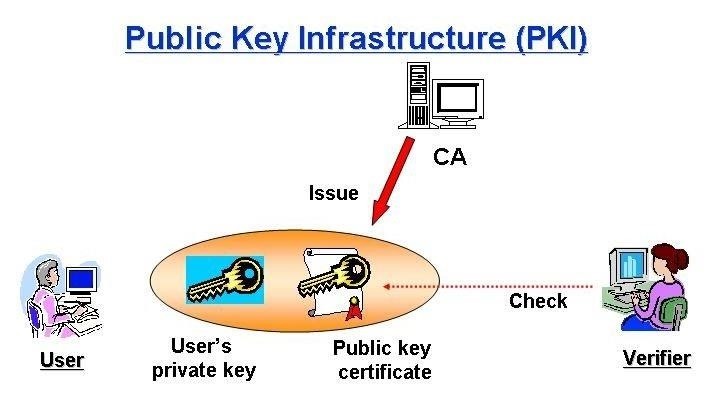
- For the end I will describe one unbeatable algorithm for encryption and decryption of data, but it is not used in computers, you can try it on paper, it is called ONE TIME PAD crypto system.
- If you aren't familiar with mathematics, today I will be good teacher. ASCII presents American standard code for international interchange - letter to numerical record. English alphabet have 26 letter's.
With ASCII letter A = 65 Z = 90 , a= 97 z = 122 , don't lie yourself it's a little trick, how Z presents 90 if aplhabet have 26 letters, it's easy A presents 65 and plus 25 it's 90 - very simple :)
It's time to convert numeric to binary record, if u are familyar with IPv4 and TCP/IP that is very simple, but for kiddies I will present conversion.
Each letter is summary of 2Byte, 1Byte=4bits so A=8bits , each bit is equivalent to his value, here's tabel.
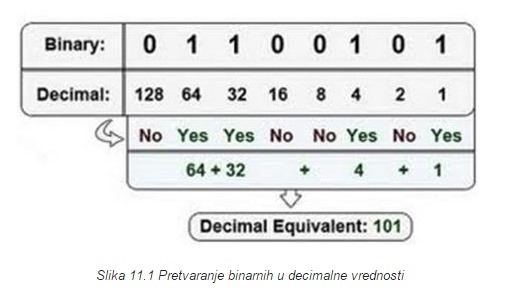
Okay lets convert HELLO to plaintext
With ACSII standard H=72, when we convert 72 to binary it looks like:
72(decimal)=01001000(binary), nice it's very simple :)
Now let's convert all of letters step by step
H=72=01001000
E=69=01000101
L=76=01001100
L=76=01001100
O=79=01001111
Plaintext: 01001000.01000101.01001100.01001100.01001111
Everyone who know rules can transcrypt this to letter, so we need key.
Key can be choosed randomly, but pay attention, if u don't wanna ? character in ciphertext choose the binaryes which summary with plaintext doesn't go bigger than 122 in numeric record.
Key:00001101.00001111.00000011.00010011.00001001
Nice, now it's time for summary this values, but you have to know rules of collecting binarys: 1+1=0 , 0+0=0 , 1+0=1 - now let's get summary(ciphertext).

When we convert Cipher to numeric, than to letter's we will get:
Cipher: EJOOF
Very nice :), you can send to your buddy EJOOF and key, he will decript cipher and key to plaintext with collect both together and get summary.

Thank's for reading.
Best regards ,
Nemanja Jovic










































4 Responses
I was bored one night so I basically just went to YouTube and learned how to convert binary to decimal. It was very interesting... it also explained to me why the numbers 64, 128, 256, 1040, etc. are very common in computing. Math is the foundation of all computation.
I think you meant 256, 512, 1024, 2048, etc.
I was just listing random numbers you often see, not any specific algorithm. But yes, the power of two. ;)
I'm studying Administration and security of networks, conversion is basic..
Share Your Thoughts