Hi guys!
I wondered, if it's possible to infect victim that is visiting our website? Without downloading and running any files, is there any way to install exploit when loading website?

Hi guys!
I wondered, if it's possible to infect victim that is visiting our website? Without downloading and running any files, is there any way to install exploit when loading website?
 Forum Thread:
When My Kali Linux Finishes Installing (It Is Ready to Boot), and When I Try to Boot It All I Get Is a Black Screen.
8
Replies
Forum Thread:
When My Kali Linux Finishes Installing (It Is Ready to Boot), and When I Try to Boot It All I Get Is a Black Screen.
8
Replies Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies
Forum Thread:
HACK ANDROID with KALI USING PORT FORWARDING(portmap.io)
12
Replies Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
2
Replies
Forum Thread:
Hydra Syntax Issue Stops After 16 Attempts
2
Replies Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies
Forum Thread:
Hack Instagram Account Using BruteForce
208
Replies Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies
Forum Thread:
Metasploit reverse_tcp Handler Problem
47
Replies Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies
Forum Thread:
How to Train to Be an IT Security Professional (Ethical Hacker)
22
Replies Metasploit Error:
Handler Failed to Bind
41
Replies
Metasploit Error:
Handler Failed to Bind
41
Replies Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies
Forum Thread:
How to Hack Android Phone Using Same Wifi
21
Replies How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies
How to:
HACK Android Device with TermuX on Android | Part #1 - Over the Internet [Ultimate Guide]
177
Replies How to:
Crack Instagram Passwords Using Instainsane
36
Replies
How to:
Crack Instagram Passwords Using Instainsane
36
Replies Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies
Forum Thread:
How to Hack an Android Device Remotely, to Gain Acces to Gmail, Facebook, Twitter and More
5
Replies Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies
Forum Thread:
How Many Hackers Have Played Watch_Dogs Game Before?
13
Replies Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies
Forum Thread:
How to Hack an Android Device with Only a Ip Adress
55
Replies How to:
Sign the APK File with Embedded Payload (The Ultimate Guide)
10
Replies
How to:
Sign the APK File with Embedded Payload (The Ultimate Guide)
10
Replies Forum Thread:
How to Run and Install Kali Linux on a Chromebook
18
Replies
Forum Thread:
How to Run and Install Kali Linux on a Chromebook
18
Replies Forum Thread:
How to Find Admin Panel Page of a Website?
13
Replies
Forum Thread:
How to Find Admin Panel Page of a Website?
13
Replies Forum Thread:
can i run kali lenux in windows 10 without reboting my computer
4
Replies
Forum Thread:
can i run kali lenux in windows 10 without reboting my computer
4
Replies Forum Thread:
How to Hack School Website
11
Replies
Forum Thread:
How to Hack School Website
11
Replies Forum Thread:
Make a Phishing Page for Harvesting Credentials Yourself
8
Replies
Forum Thread:
Make a Phishing Page for Harvesting Credentials Yourself
8
Replies Forum Thread:
Creating an Completely Undetectable Executable in Under 15 Minutes!
38
Replies
Forum Thread:
Creating an Completely Undetectable Executable in Under 15 Minutes!
38
Replies How To:
Dox Anyone
How To:
Dox Anyone
 How To:
Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
How To:
Use Burp & FoxyProxy to Easily Switch Between Proxy Settings
 How To:
Crack SSH Private Key Passwords with John the Ripper
How To:
Crack SSH Private Key Passwords with John the Ripper
 How To:
Exploit EternalBlue on Windows Server with Metasploit
How To:
Exploit EternalBlue on Windows Server with Metasploit
 How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
How To:
Gain SSH Access to Servers by Brute-Forcing Credentials
 How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
 How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
How To:
Perform Advanced Man-in-the-Middle Attacks with Xerosploit
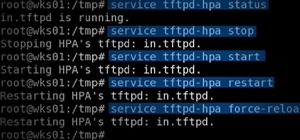 Hack Like a Pro:
Using TFTP to Install Malicious Software on the Target
Hack Like a Pro:
Using TFTP to Install Malicious Software on the Target
 How To:
Scan for Vulnerabilities on Any Website Using Nikto
How To:
Scan for Vulnerabilities on Any Website Using Nikto
 How To:
Find Identifying Information from a Phone Number Using OSINT Tools
How To:
Find Identifying Information from a Phone Number Using OSINT Tools
 How To:
Crack Shadow Hashes After Getting Root on a Linux System
How To:
Crack Shadow Hashes After Getting Root on a Linux System
 How To:
Hack Apache Tomcat via Malicious WAR File Upload
How To:
Hack Apache Tomcat via Malicious WAR File Upload
 How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
How to Hack Wi-Fi:
Stealing Wi-Fi Passwords with an Evil Twin Attack
 How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
How To:
Use Kismet to Watch Wi-Fi User Activity Through Walls
 Hack Like a Pro:
How to Find Directories in Websites Using DirBuster
Hack Like a Pro:
How to Find Directories in Websites Using DirBuster
 How To:
Make Your Own Bad USB
How To:
Make Your Own Bad USB
 How To:
Scan Websites for Interesting Directories & Files with Gobuster
How To:
Scan Websites for Interesting Directories & Files with Gobuster
 How To:
Use Ettercap to Intercept Passwords with ARP Spoofing
How To:
Use Ettercap to Intercept Passwords with ARP Spoofing
 How To:
Bypass File Upload Restrictions on Web Apps to Get a Shell
How To:
Bypass File Upload Restrictions on Web Apps to Get a Shell
 How to Hack Wi-Fi:
Cracking WPA2-PSK Passwords Using Aircrack-Ng
How to Hack Wi-Fi:
Cracking WPA2-PSK Passwords Using Aircrack-Ng
8 Responses
If such thing really existed it would have been quite fearsome!
Thanksfully no (so far I know). All techniques I heard about always involve downloading some exe more or less hidden.
So in short: No.
Umm, exploits do not require an exe. If the visitor of a site has a vulnerable program and you have an exploit for it, you can host it on your own website server or if you can get it on another website through hacking the website or ad network, any visitors with the vulnerability should be compromised. That's how drive by downloading malware and exploit kits work.
Exploit always require something to run them '-' It's may be not a exe if you're using an interpreted language but it's not the point.
In the end you need to send your exploit+reverse-bind on the victim (so you need the user to download it). Modern browsers always ask the user to confirm a download and moreover they're sandboxed to prevent the monkey between behind the screen to compromise its machine just by running a web script (the damage will be limited to the browser).
You can still convince your victim to run your code (Social Engineering is the n°1 weapon of hackers) it's not really hard. But once again it'll require the user to actively download something.
Where ever you learned all that is wrong. Exploiting Flash/Java/Web browsers/any other software that has web access, takes no user interaction to infect. https://blogs.sophos.com/2014/03/26/how-malware-works-anatomy-of-a-drive-by-download-web-attack-infographic/
Dude, I'm not saying you can't exploit. What I say is that you're sandboxed in the browser.
Modern browser such as Firefox and Edge require user interaction for downloading. Most drive-by download happen with the user's consent (through some form of phishing ) and the rest when the user run an deprecated browser.
Now I'm curious how you exploit a web application (let's say a SSH client) hosted on the victim behind his NAT without downloading any file.
You still are not understanding how a exploit kits work. You can't say user interaction is needed, when there's plenty of proof that you are wrong. It doesn't matter if you think a Sandboxed browser stops it. Stop being ignorant and go do some research. Zero interaction is needed to get an infection. I have personally seen it happen and I read articles every day about it continuing to be a problem. A lot of ransomware comes though exploit kits. It doesn't matter if you think I'm wrong as Google has my back. All you need to do is research
https://blog.malwarebytes.com/threats/exploit-kits/
Here, I'll do some research for you.
I understand how exploit kits work (at least the basics). However it's totally different: Exploit kits attack the browser (and associated plug-in) not the host itself (No you can't exploit ANY software that have a web access with exploit kit ONLY those relate to the attacked browser). If the exploit kit manage to break the browser sandbox it's your browser that is at fault. A up-to-date browser is immune to this (maybe you have some 0-days under your feet??)
You just can't access to your potential victim SSH server/client, postgres, tomcat or other services, just like that without breaking the browser in first place (in that case you would already have the control on the box, no need to exploit further vulnerabilities).
Instead of invoking Google as your joker and responding aggressively (almost unrespectfully) to any comment that doesn't go your way. You should learn how works browser sandboxing, the NAT and networking in general
Hope I helped,
That's where are misunderstandings happened. I did not mean, Any software, my mistake. You were saying it wasn't possible at all, which as I proved, is wrong.
Share Your Thoughts