I'm experimenting with Metasploit and using it on my own machine.
I'm running Kali Linux on VirtualBox and trying to open a meterpeter session to my host Win 10 OS.
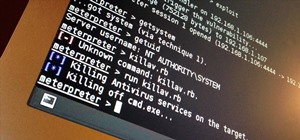
I generate a reverse_tcp payload, execute it on my host OS (Windows 10), and run exploit/multi/handler in Kali.
The session opens but meterpreter doesn't show up and nothing really happens. The metasploit is getting stuck at this point

If I try to cancel the exploit with Ctr+C my whole machine freezes and I have to reboot it.
I think maybe the problems appear because the Kali Linux is a VM and I should somehow configure the VM box?







































Be the First to Respond
Share Your Thoughts